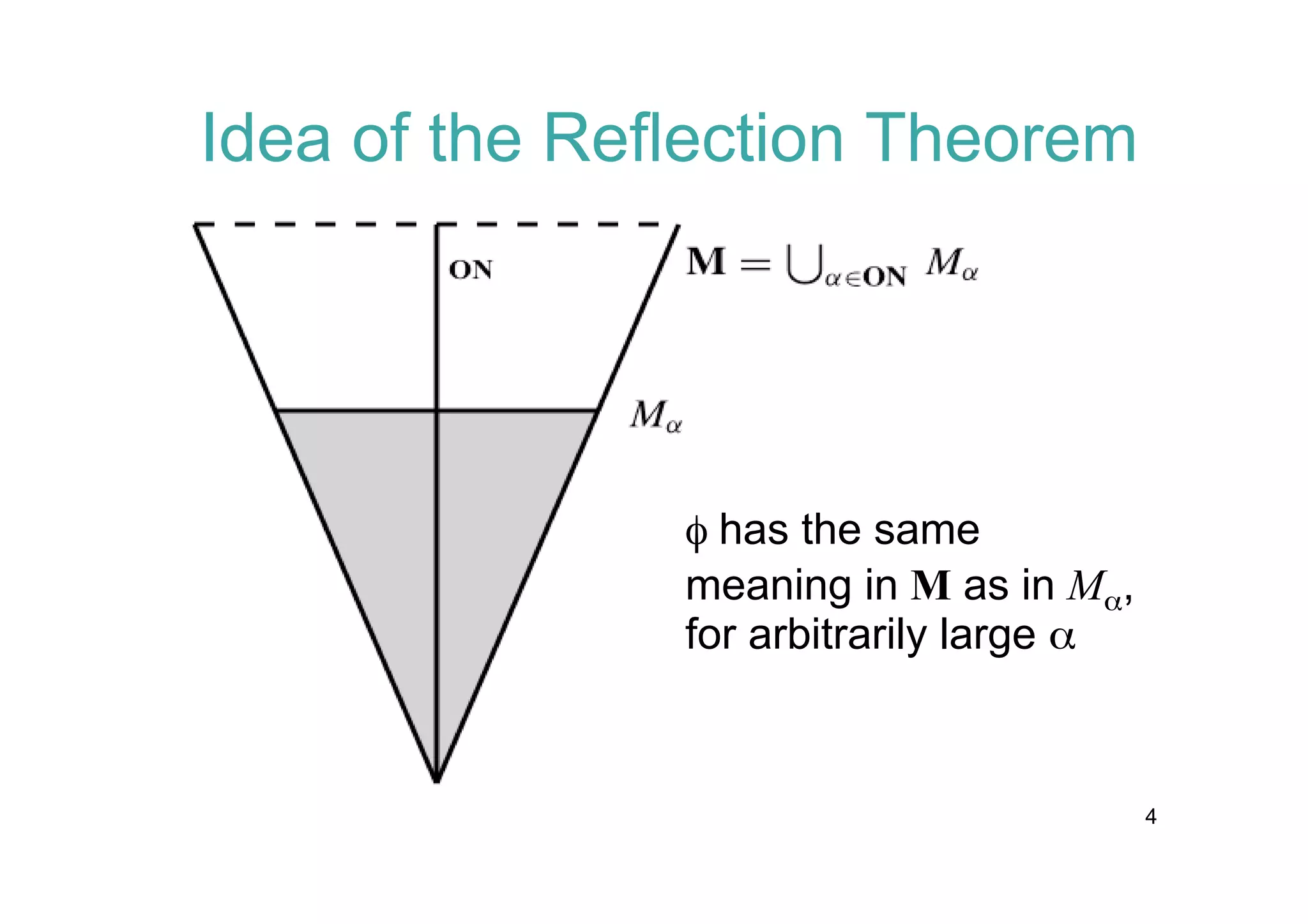
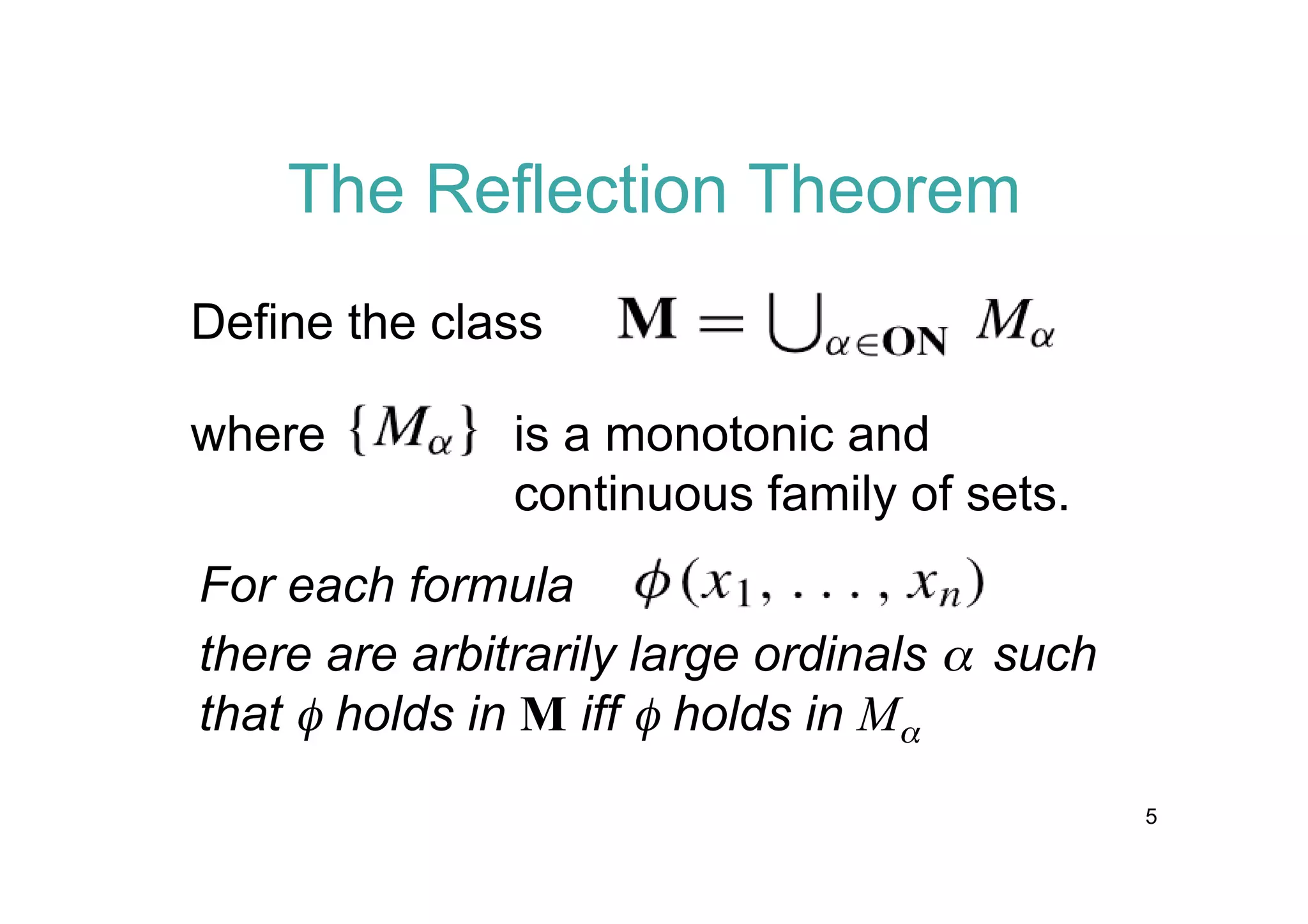
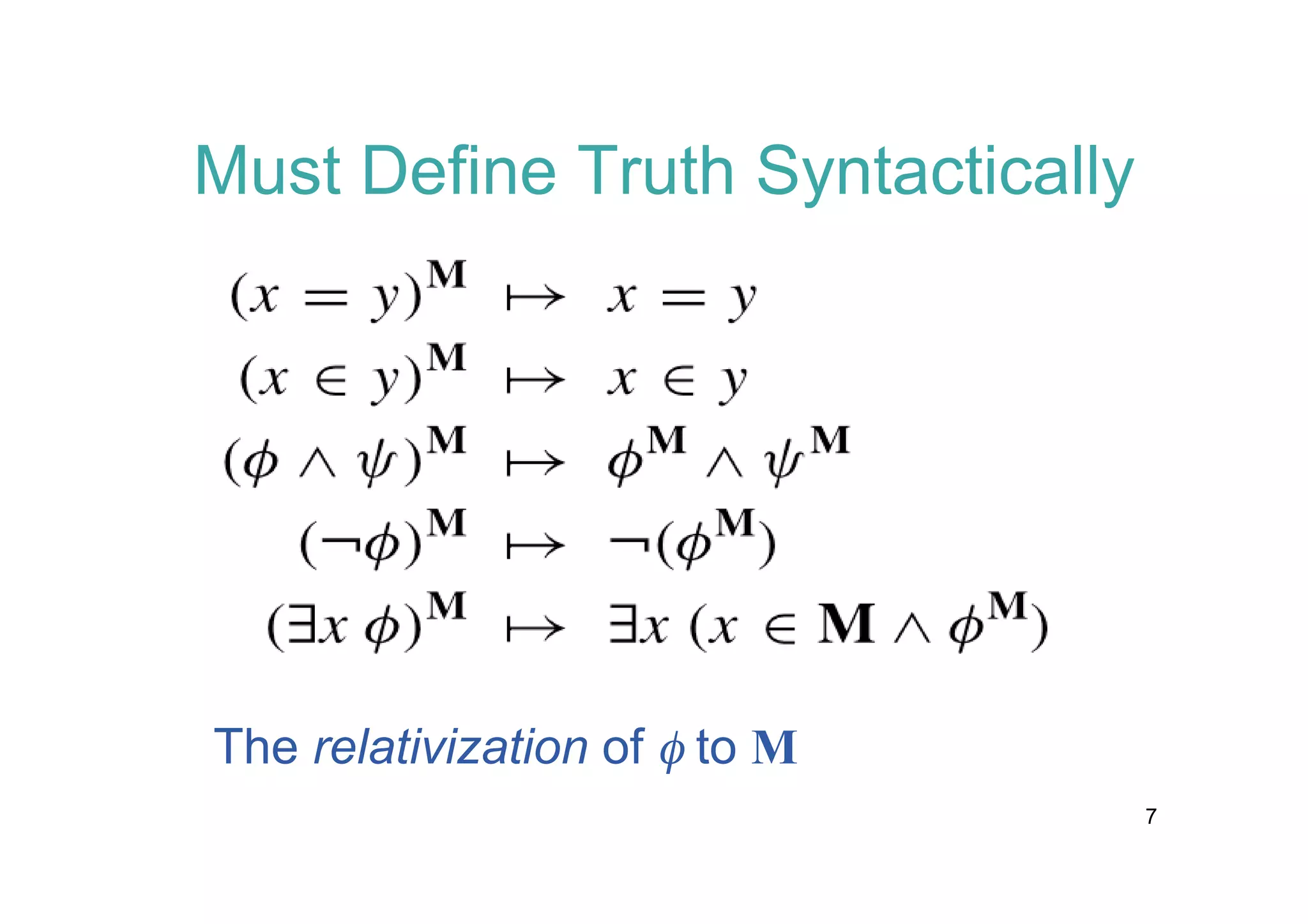
The document discusses the Reflection Theorem, which formalizes meta-theoretic reasoning. It motivates the theorem by explaining that algebraic structures and meta-level reasoning are difficult to formalize. It then outlines proving the theorem in Isabelle/ZF set theory, using a proof from Mostowski involving closed unbounded classes of ordinals and normal functions. The theorem is applied to provide a modern treatment of Gödel's proof that ZF set theory with the axiom of choice and generalized continuum hypothesis is consistent.