This document discusses a new approach to cybersecurity as perimeter security becomes less effective. It summarizes that:
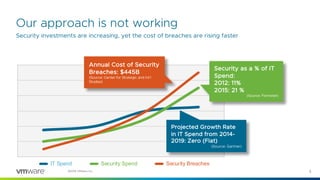
1) While security investments are increasing, the costs of breaches are rising faster.
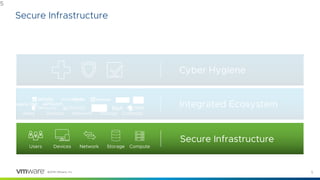
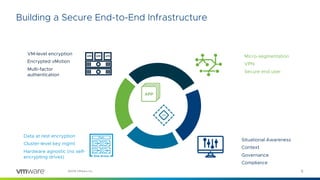
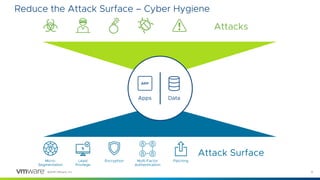
2) The document proposes integrating cyber hygiene practices like patching and encryption across secure infrastructure, devices, networks, and storage to reduce the attack surface and build situational awareness.
3) It also suggests rationalizing the crowded cybersecurity solution ecosystem and using the hypervisor to enforce the intended secure state of workloads through learning, locking, and adapting techniques.



![12©2018 VMware, Inc.
Using Hypervisor to Enforce the Intended State – Learn, Lock and Adapt
Learn
VM Manifest
VM Manifest
VM Manifest
Intended
State Engine
vCenter ESX
App
Scope
Off-the-shelf apps
OTS
Software
Database
Custom apps
CI/CD pipeline
[Provisioning systems]
[Automation frameworks]Machine Learning
Capture & Analyze
Protect
Processes
Processes
Processes
OS
AppDefense
Monitor
Protected Zone
VM Manifest
Detect
Snapshot Suspend
Block/Alarm
Quarantine Network Blocking
Service Insertion
Respond&
Compute Network](https://image.slidesharecdn.com/cybertalksrobertamesflippingthescriptchangingthegameincyber-181022203506/85/Flipping-the-Script-Changing-the-Game-in-Cyber-12-320.jpg)
