Managing Security Policies Across Hybrid Cloud Environments
•
1 like•284 views
Managing Security Policies Across Hybrid Cloud Environments: Visibility is Obscured by Clouds
Report
Share
Report
Share
Download to read offline
Recommended
Transform Your Security Operations with Security Automation and Orchestration

Transform Your Security Operations with Security Automation and OrchestrationEnterprise Management Associates
More Related Content
What's hot
Transform Your Security Operations with Security Automation and Orchestration

Transform Your Security Operations with Security Automation and OrchestrationEnterprise Management Associates
What's hot (20)
To Catch a Phish, or: Why You Must Automate Email Security 

To Catch a Phish, or: Why You Must Automate Email Security
Outside the (Black) Box: Protecting Core Operations in Energy

Outside the (Black) Box: Protecting Core Operations in Energy
High Performance Security Report - High Technology

High Performance Security Report - High Technology
Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...

Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...
Transform Your Security Operations with Security Automation and Orchestration

Transform Your Security Operations with Security Automation and Orchestration
Security from Compliance or Compliance from Security?--Metrics are the key

Security from Compliance or Compliance from Security?--Metrics are the key
Infographic: Bringing Your Cloud Visibility Back Into Focus

Infographic: Bringing Your Cloud Visibility Back Into Focus
The Razor's Edge: Enabling Cloud While Mitigating the Risk of a Cloud Data Br...

The Razor's Edge: Enabling Cloud While Mitigating the Risk of a Cloud Data Br...
Viewers also liked
Viewers also liked (12)
Security is from Mars, Application Delivery is from Venus

Security is from Mars, Application Delivery is from Venus
Examining the Impact of Security Management on the Business (Infographic)

Examining the Impact of Security Management on the Business (Infographic)
Migrating Application Connectivity and Network Security to AWS

Migrating Application Connectivity and Network Security to AWS
Avoid outages-from-misconfigured-devices-webinar-slides

Avoid outages-from-misconfigured-devices-webinar-slides
Dos and Don’ts for Managing External Connectivity to/from Your Network

Dos and Don’ts for Managing External Connectivity to/from Your Network
Shift Happens: Eliminating the Risks of Network Security Policy Changes

Shift Happens: Eliminating the Risks of Network Security Policy Changes
A Pragmatic Approach to Network Security Across Your Hybrid Cloud Environment

A Pragmatic Approach to Network Security Across Your Hybrid Cloud Environment
5 Steps to a Zero Trust Network - From Theory to Practice

5 Steps to a Zero Trust Network - From Theory to Practice
Top PCI Pitfalls and How to Avoid Them: The QSA’s Perspective

Top PCI Pitfalls and How to Avoid Them: The QSA’s Perspective
A business driven approach to security policy management a technical perspec...

A business driven approach to security policy management a technical perspec...
Reaching PCI Nirvana: Ensure a Successful Audit & Maintain Continuous Compliance

Reaching PCI Nirvana: Ensure a Successful Audit & Maintain Continuous Compliance
Similar to Managing Security Policies Across Hybrid Cloud Environments
Similar to Managing Security Policies Across Hybrid Cloud Environments (20)
Moving up the Value Chain: What we can Learn from Experienced Cloud Users

Moving up the Value Chain: What we can Learn from Experienced Cloud Users
RightScale Webinar: Benchmark your Cloud Adoption: 2014 State of the Cloud Re...

RightScale Webinar: Benchmark your Cloud Adoption: 2014 State of the Cloud Re...
Cloud Security - What you Should Be Concerned About

Cloud Security - What you Should Be Concerned About
Why is hybrid cloud still so hard? 4 keys to unlock the future of IT

Why is hybrid cloud still so hard? 4 keys to unlock the future of IT
More from AlgoSec
More from AlgoSec (20)
best practices-managing_security_in_the hybrid cloud

best practices-managing_security_in_the hybrid cloud
compliance made easy. pass your audits stress-free webinar

compliance made easy. pass your audits stress-free webinar
2021 02-17 v mware-algo-sec securely accelerate your digital transformation w...

2021 02-17 v mware-algo-sec securely accelerate your digital transformation w...
Compliance made easy. Pass your audits stress-free.

Compliance made easy. Pass your audits stress-free.
Cloud migrations made simpler safe secure and successful migrations

Cloud migrations made simpler safe secure and successful migrations
Build and enforce defense in depth - an algo sec-cisco tetration webinar

Build and enforce defense in depth - an algo sec-cisco tetration webinar
Radically reduce firewall rules with application-driven rule recertification

Radically reduce firewall rules with application-driven rule recertification
2020 09-30 overcoming the challenges of managing a hybrid environment - aws a...

2020 09-30 overcoming the challenges of managing a hybrid environment - aws a...
2020 04-07 webinar slides -turning network security alerts into action change...

2020 04-07 webinar slides -turning network security alerts into action change...
Cessation of Misconfigurations: Common Network Misconfiguration Risks & How t...

Cessation of Misconfigurations: Common Network Misconfiguration Risks & How t...
Put out audit security fires, pass audits -every time 

Put out audit security fires, pass audits -every time
Cisco ACI & Hybrid Networks - Breaking Down Silos with Central Policy Management

Cisco ACI & Hybrid Networks - Breaking Down Silos with Central Policy Management
2019 08-13 selecting the right security policy management solution

2019 08-13 selecting the right security policy management solution
2019 06-26 effective multi-vendor management -fortinet algo sec webinar final

2019 06-26 effective multi-vendor management -fortinet algo sec webinar final
Cisco Firepower Migration | Cisco and AlgoSec Joint Webinar

Cisco Firepower Migration | Cisco and AlgoSec Joint Webinar
2019 02-20 micro-segmentation based network security strategies (yoni geva)

2019 02-20 micro-segmentation based network security strategies (yoni geva)
Recently uploaded
Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service

Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Recently uploaded (20)
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service

Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
Managing Security Policies Across Hybrid Cloud Environments
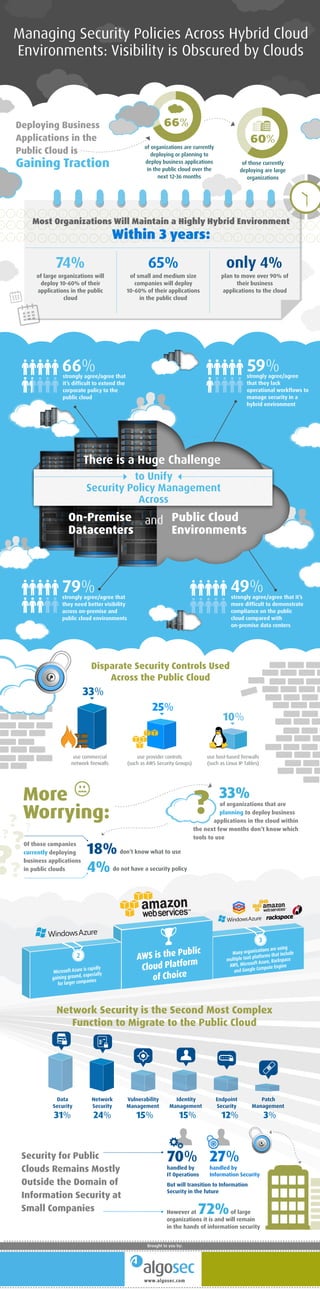
- 1. strongly agree/agree that they need better visibility across on-premise and public cloud environments Deploying Business Applications in the Public Cloud is Disparate Security Controls Used Across the Public Cloud Security for Public Clouds Remains Mostly Outside the Domain of Information Security at Small Companies Of those companies currently deploying business applications in public clouds Gaining Traction of those currently deploying are large organizations There is a Huge Challenge On-Premise Datacenters Public Cloud Environments to Unify Security Policy Management Across and plan to move over 90% of their business applications to the cloud only 4% of large organizations will deploy 10-60% of their applications in the public cloud 74% of small and medium size companies will deploy 10-60% of their applications in the public cloud 65% strongly agree/agree that it’s more difficult to demonstrate compliance on the public cloud compared with on-premise data centers strongly agree/agree that it’s difficult to extend the corporate policy to the public cloud 66% Most Organizations Will Maintain a Highly Hybrid Environment Within 3 years: use host-based firewalls (such as Linux IP Tables) don’t know what to use18% do not have a security policy handled by IT Operations Data Security Network Security Vulnerability Management Identity Management Endpoint Security Patch Management handled by Information Security But will transition to Information Security in the future However at 72%of large organizations it is and will remain in the hands of information security 4% of organizations that are planning to deploy business applications in the cloud within the next few months don’t know which tools to use 33% use provider controls (such as AWS Security Groups) strongly agree/agree that they lack operational workflows to manage security in a hybrid environment Network Security is the Second Most Complex Function to Migrate to the Public Cloud of organizations are currently deploying or planning to deploy business applications in the public cloud over the next 12-36 months 66% 60% 79% 59% 49% ? use commercial network firewalls 33% 70% 27% 31% 24% 15% 15% 12% 3% More Worrying: 10% www.algosec.com Brought to you by: 3 2 25% Managing Security Policies Across Hybrid Cloud Environments: Visibility is Obscured by Clouds
