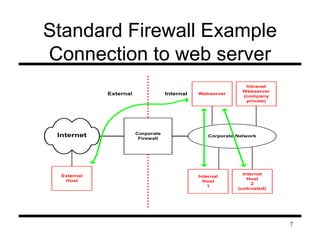
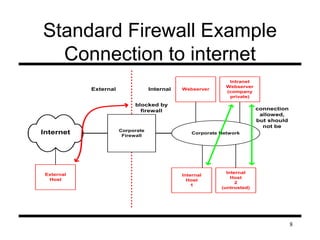
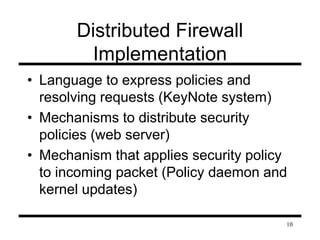
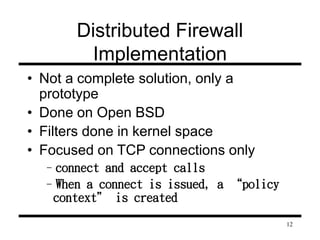
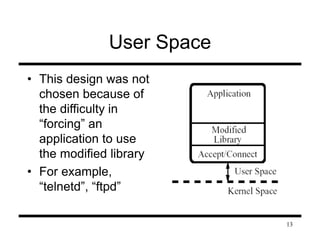
This document presents information on firewalls and proposes a distributed firewall concept. It discusses drawbacks of traditional firewalls, such as difficulties handling certain protocols and assuming inside users are trusted. The distributed firewall concept defines security policies centrally and enforces them using network endpoints. It then describes a prototype implementation using KeyNote policies to define rules and a policy daemon in the kernel to apply rules to incoming packets. Future work areas are identified like improved administration tools and per-packet scanning.