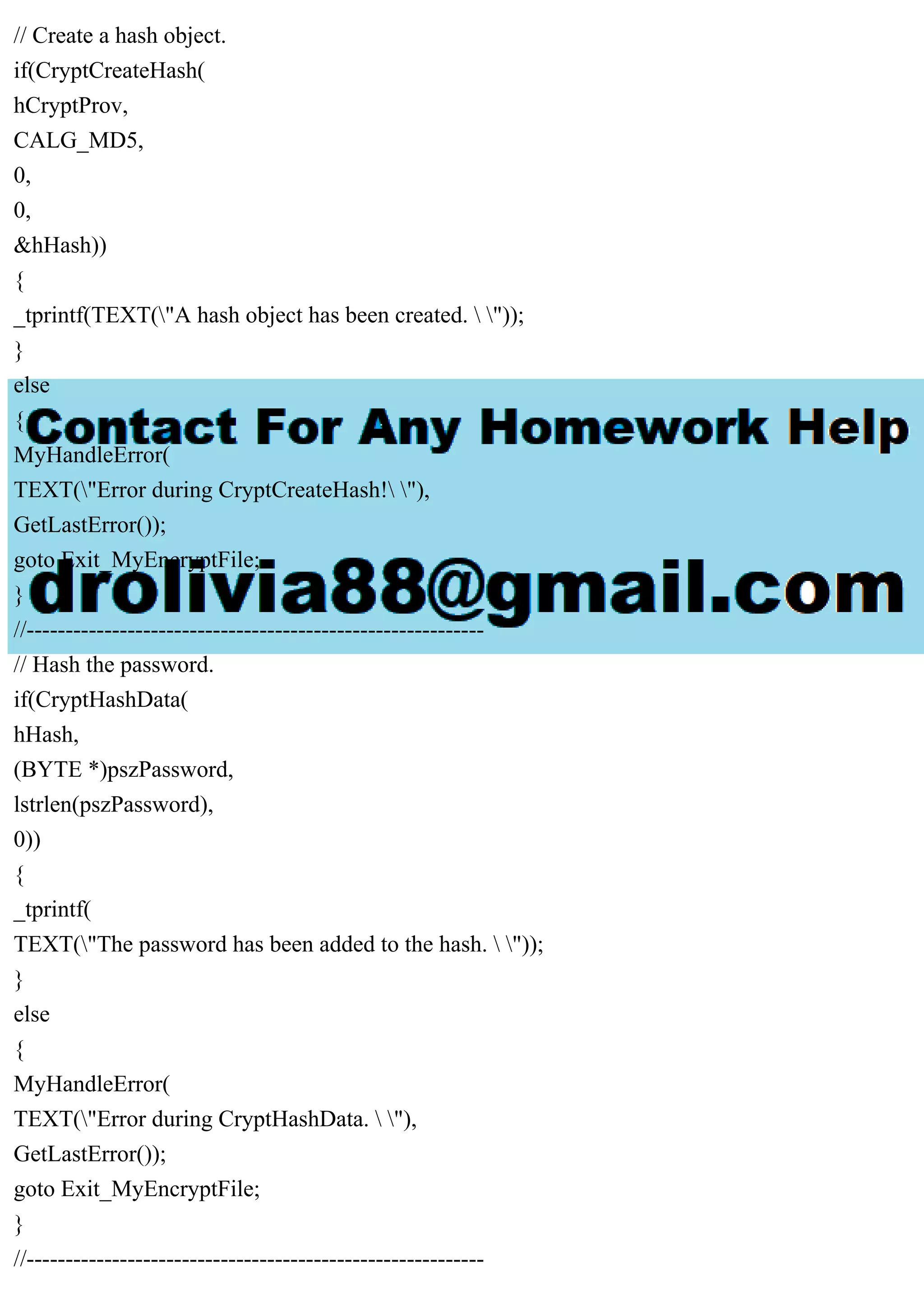
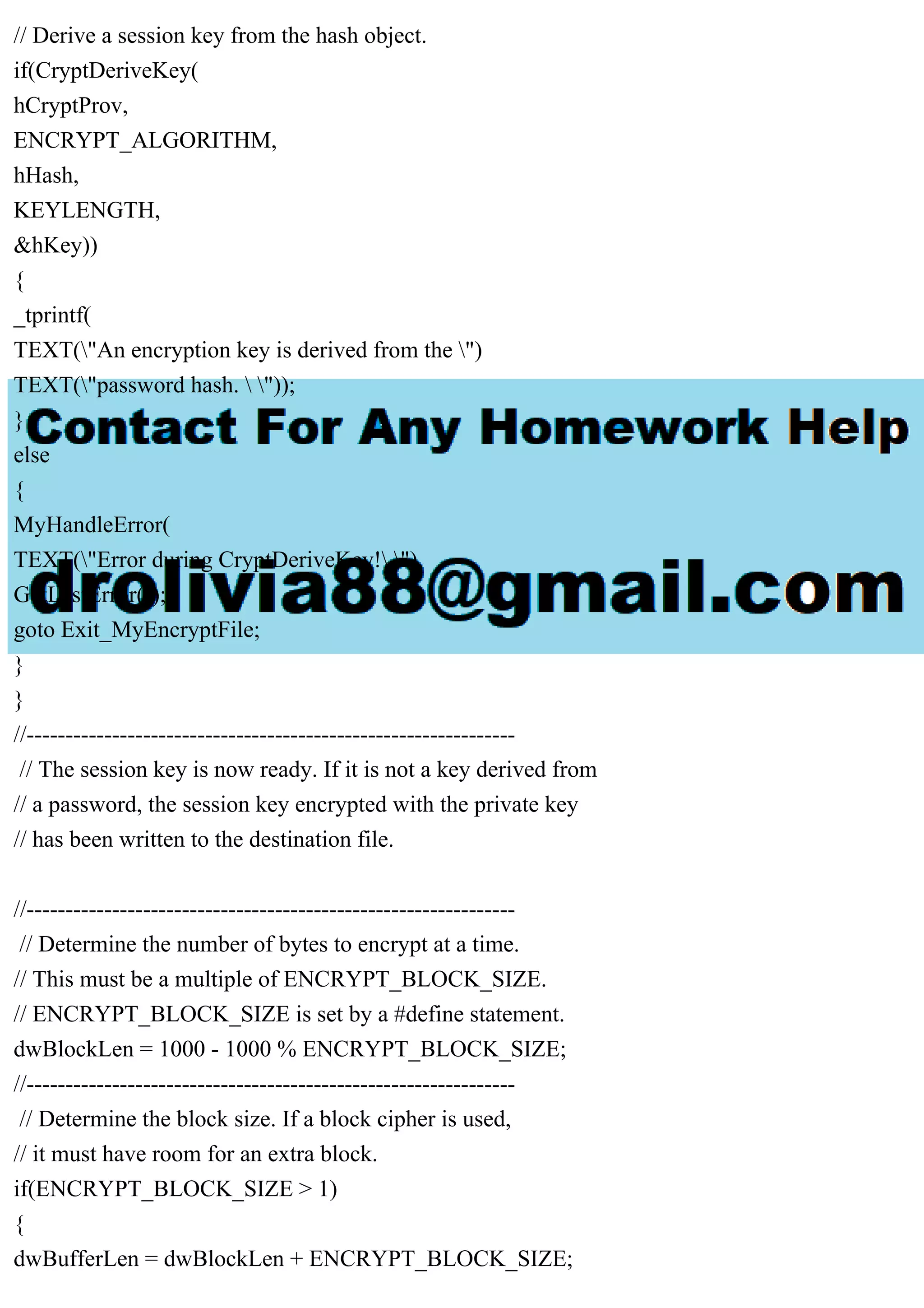
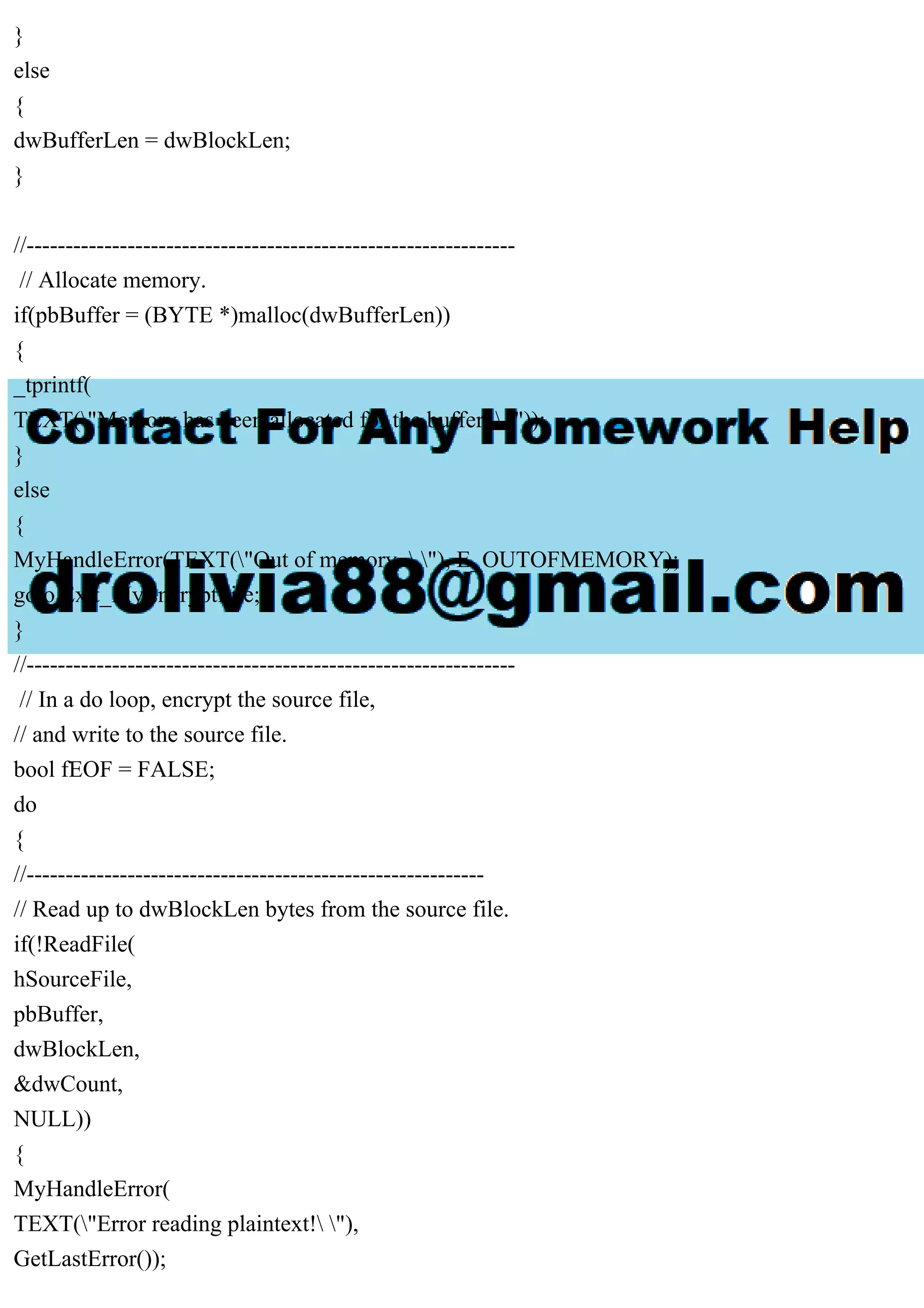
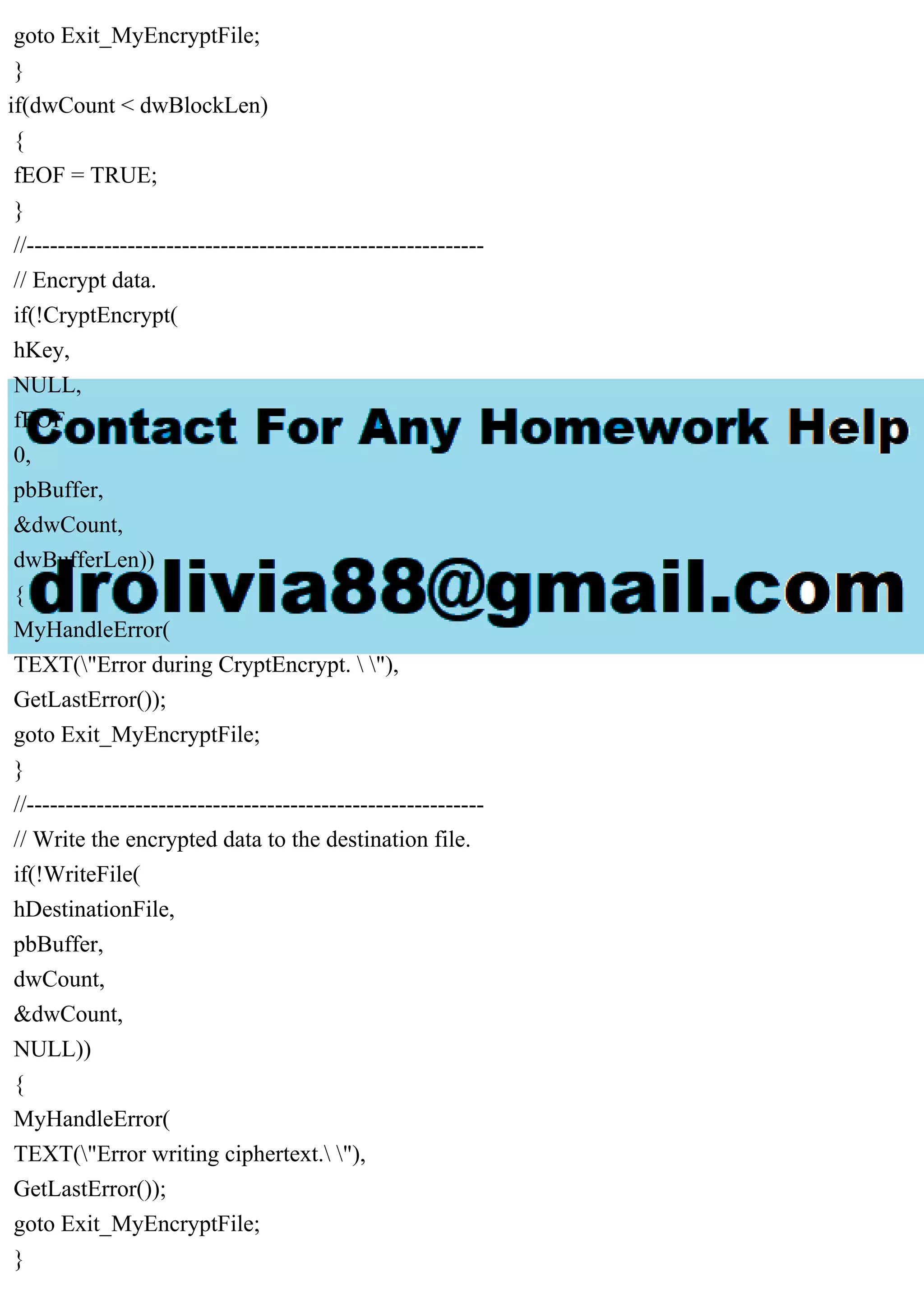
The document outlines a program named encrypt.cpp that encrypts and decrypts files based on user-input passwords. It describes the use of a block-cipher algorithm for file encryption and details the steps for handling both encrypted and plain files, ensuring that multiple encryptions do not occur on the same file. Technical specifics include functions for managing cryptographic keys and error handling.
![File encryption. [32] Write a program which accepts a filename as a command-line argument [-
32]. It should then ask for a password via stdin (but it should not visible when entered; use
getpass for this) [4]. The program should encrypt the file using a block-cipher algorithm (see
encryption.rst for details) [12] if it was not already encrypted by the program, and rename it with
a .enc extension. If it was already encrypted, it should decrypt the file and remove the .enc
extension [12]. Under no circumstance should the program multiply encrypt the file [4]. Call the
program encrypt.cpp. here is encrypt.rst Suppose I have an input file to encrypt: .. raw: The only
true wisdom is in knowing you know nothing. (A quote by Socrates.) What I can do then is ask
the user for a password. Suppose the user enters kitties. Then what I may do is pre-pend the
password to an output file, and add kitties in rounds to the file: .. raw: kittiesThe only true
wisdom is in knowing you know nothing. + kittieskittieskittieskittieskittieskittieskittieskittieskit -
---------------------------------------------------------- =
fhdkalhfioepwahfkdsanklvcxznkjvpwipqnkxlkdlajsflkjkljkljlkd When I add the characters in the
string kitties, I get what appears to be jumbled garbage. Without the password, it is hard to
decrypt the file. To decrypt the file, I ask the user for the password. Suppose they enter bubbles
(the wrong password). .. raw: fhdkalhfioepwah... - bubbles ------------------ = ueiaqnv I see that
by subtracting bubbles off the encrypted text, I do not get the string bubbles back, so bubbles is
not the password. If the user enters kitties (the correct password): .. raw: fhdkalhfioepwah... -
kitties ------------------ = kitties Then I see that what I get back is kitties, and since it matches the
user password entered, I may proceed to decrypt the rest of the file simply by subtracting kitties
off it in rounds. .. raw: = fhdkalhfioepwahfkdsanklvcxznkjvpwipqnkxlkdlajsflkjkljkljlkd -
kittieskittieskittieskittieskittieskittieskittieskittieskit ------------------------------------------------------
----- kittiesThe only true wisdom is in knowing you know nothing. Thus I obtain the original
message. Notice the user-supplied password itself is a necessary element of the decryption. This
type of algorithm is called a block cipher algorithm.
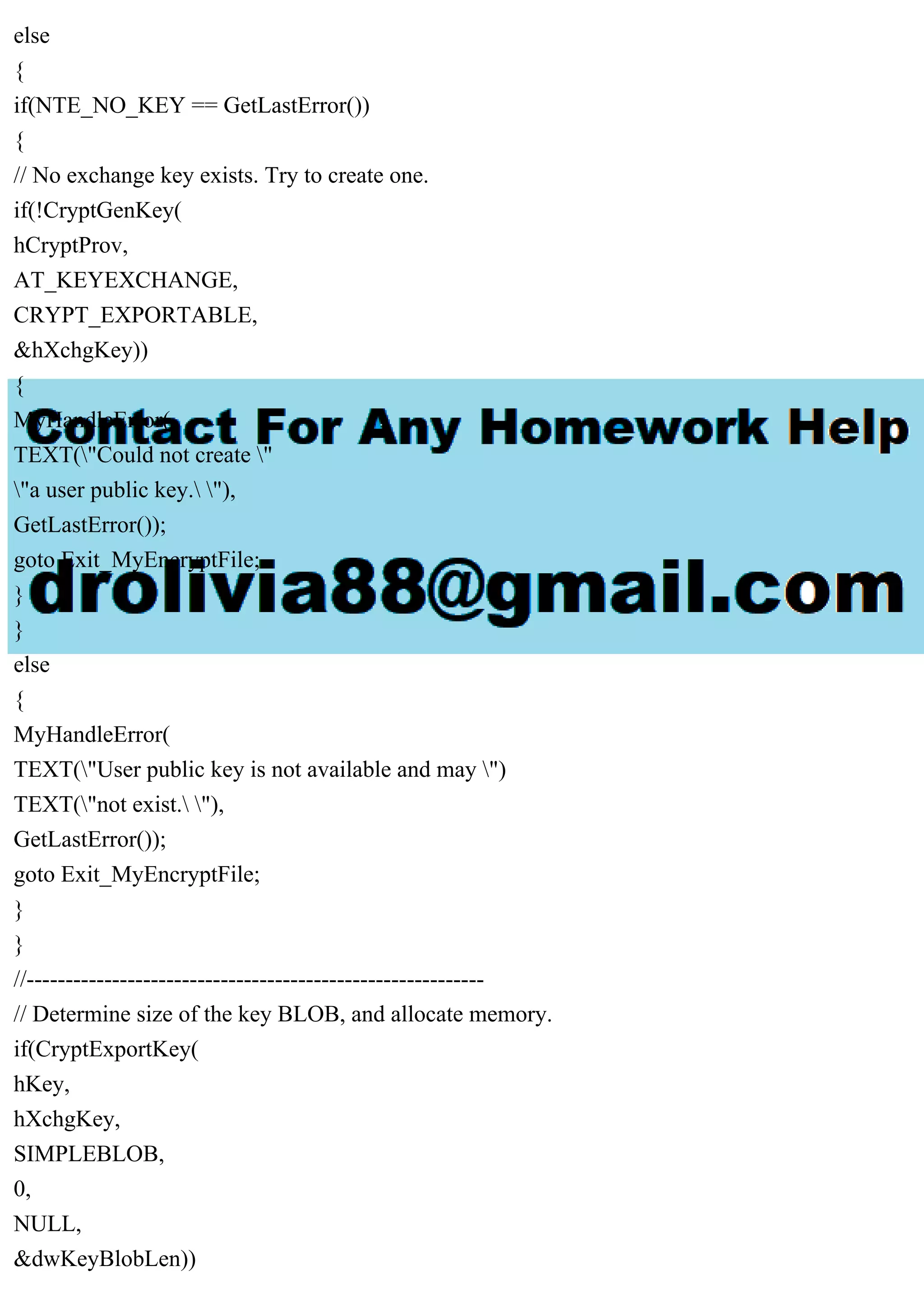
Solution
// Encrypting_a_File.cpp : Defines the entry point for the console
// application.
//
#include
#include
#include
#include](https://image.slidesharecdn.com/fileencryption-230708163619-7cb5c489/75/File-encryption-32-Write-a-program-which-accepts-a-filename-as-a-pdf-1-2048.jpg)
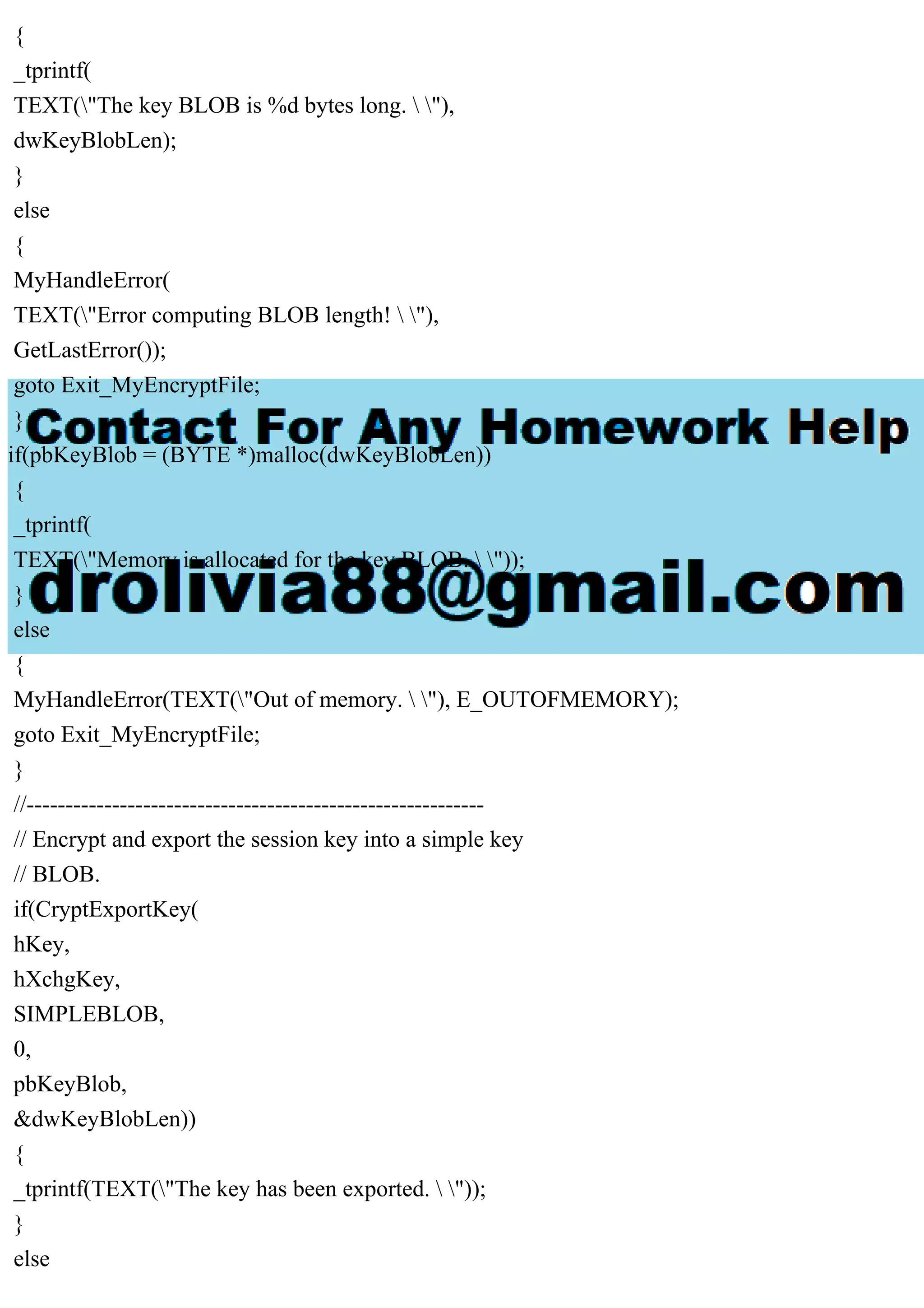
![#include
// Link with the Advapi32.lib file.
#pragma comment (lib, "advapi32")
#define KEYLENGTH 0x00800000
#define ENCRYPT_ALGORITHM CALG_RC4
#define ENCRYPT_BLOCK_SIZE 8
bool MyEncryptFile(
LPTSTR szSource,
LPTSTR szDestination,
LPTSTR szPassword);
void MyHandleError(
LPTSTR psz,
int nErrorNumber);
int _tmain(int argc, _TCHAR* argv[])
{
if(argc < 3)
{
_tprintf(TEXT("Usage: ")
TEXT(" | "));
_tprintf(TEXT(" is optional. "));
_tprintf(TEXT("Press any key to exit."));
_gettch();
return 1;
}
LPTSTR pszSource = argv[1];
LPTSTR pszDestination = argv[2];
LPTSTR pszPassword = NULL;
if(argc >= 4)
{
pszPassword = argv[3];
}
//---------------------------------------------------------------
// Call EncryptFile to do the actual encryption.
if(MyEncryptFile(pszSource, pszDestination, pszPassword))
{
_tprintf(](https://image.slidesharecdn.com/fileencryption-230708163619-7cb5c489/75/File-encryption-32-Write-a-program-which-accepts-a-filename-as-a-pdf-2-2048.jpg)
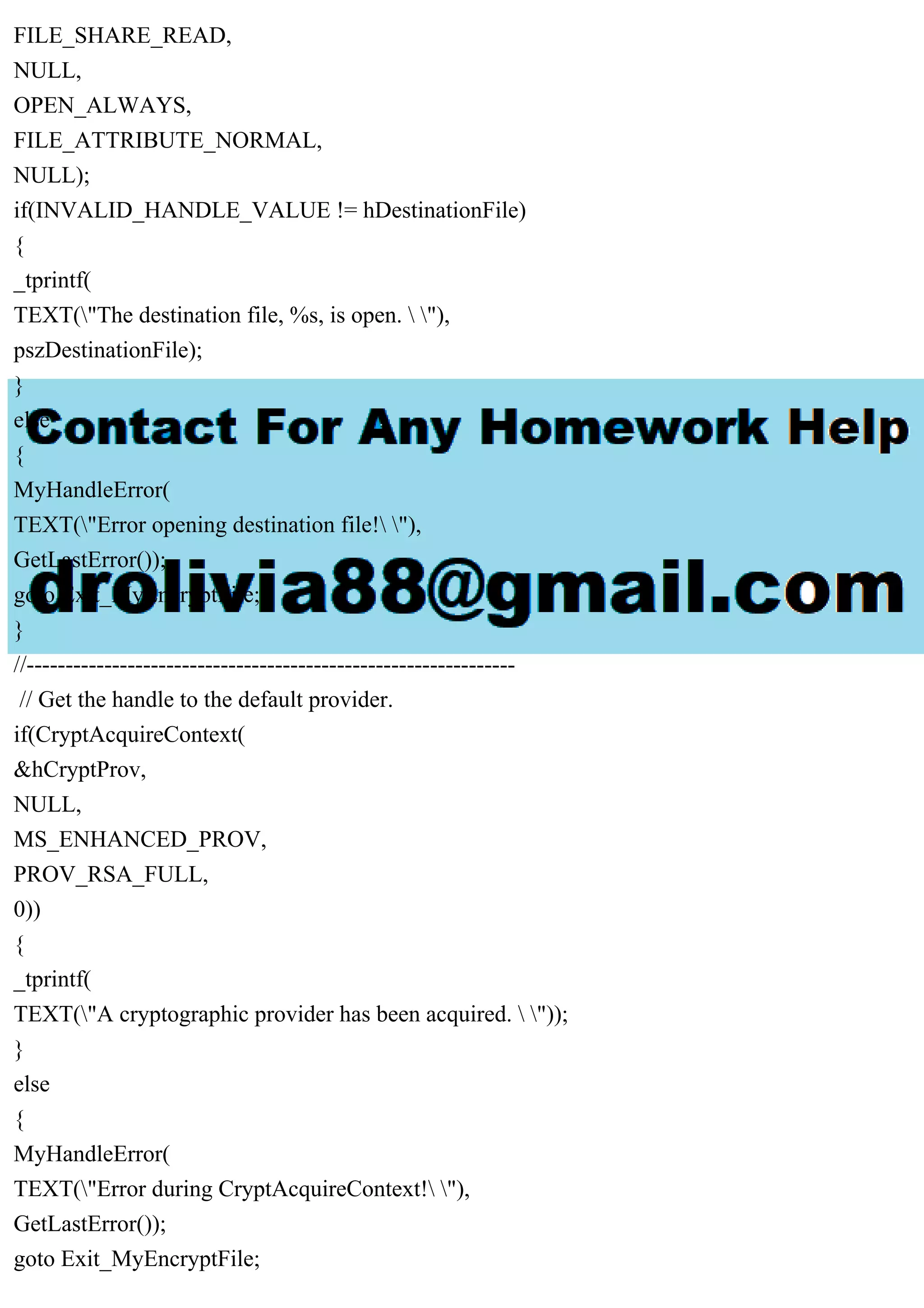
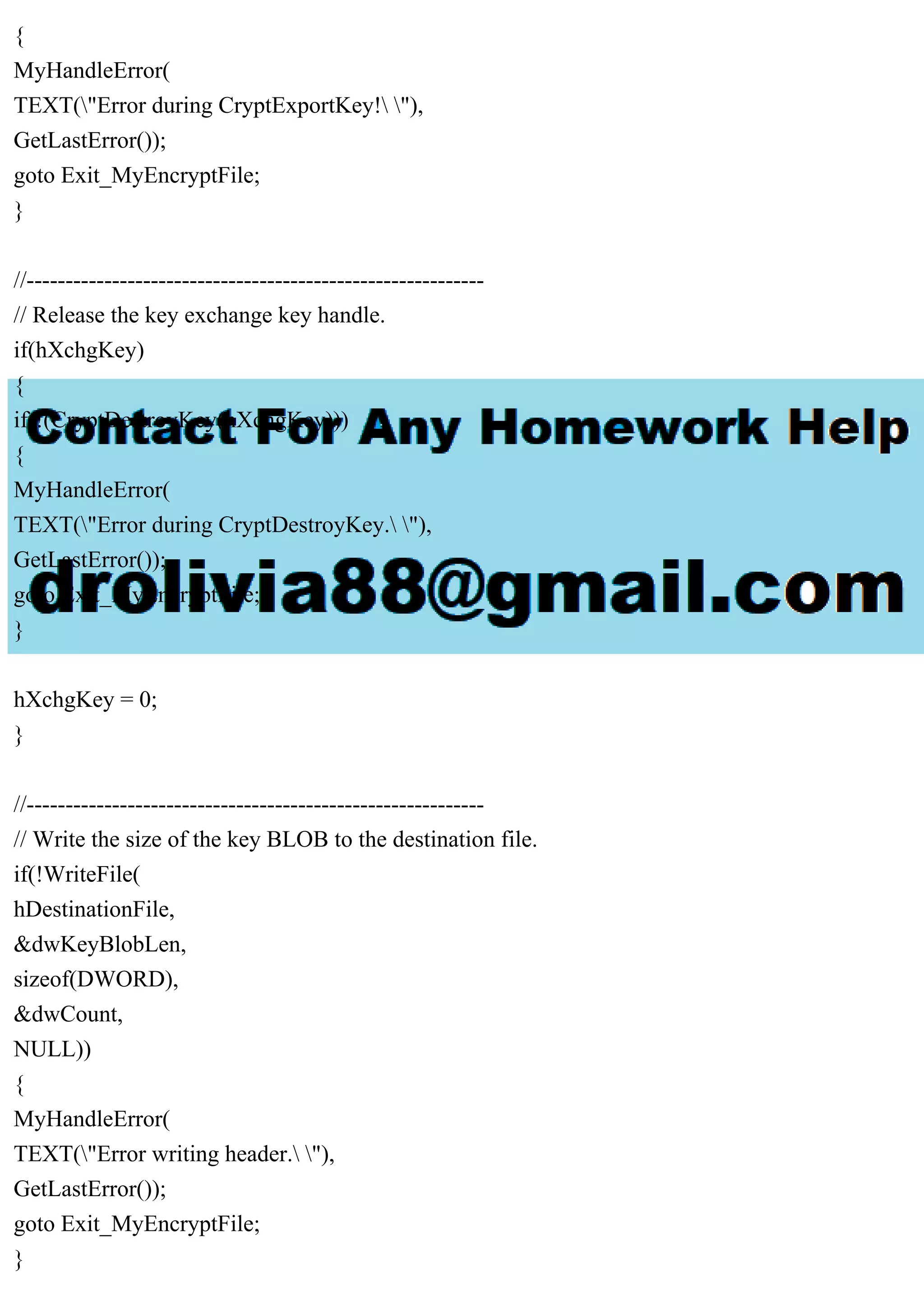
![}
//---------------------------------------------------------------
// Create the session key.
if(!pszPassword || !pszPassword[0])
{
//-----------------------------------------------------------
// No password was passed.
// Encrypt the file with a random session key, and write the
// key to a file.
//-----------------------------------------------------------
// Create a random session key.
if(CryptGenKey(
hCryptProv,
ENCRYPT_ALGORITHM,
KEYLENGTH | CRYPT_EXPORTABLE,
&hKey))
{
_tprintf(TEXT("A session key has been created. "));
}
else
{
MyHandleError(
TEXT("Error during CryptGenKey. "),
GetLastError());
goto Exit_MyEncryptFile;
}
//-----------------------------------------------------------
// Get the handle to the exchange public key.
if(CryptGetUserKey(
hCryptProv,
AT_KEYEXCHANGE,
&hXchgKey))
{
_tprintf(
TEXT("The user public key has been retrieved. "));
}](https://image.slidesharecdn.com/fileencryption-230708163619-7cb5c489/75/File-encryption-32-Write-a-program-which-accepts-a-filename-as-a-pdf-6-2048.jpg)