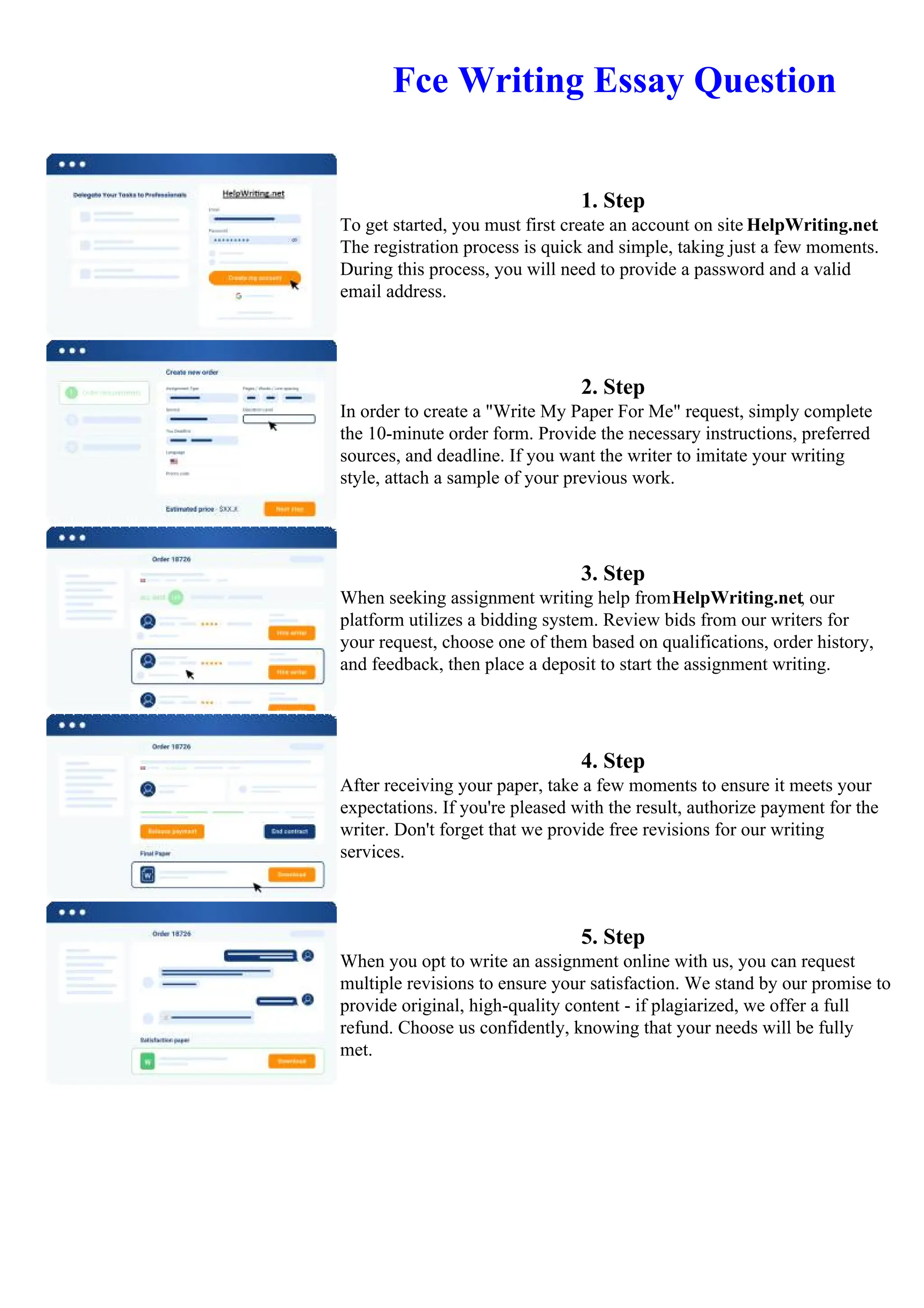
1. Identify potential risks and threats through vulnerability assessments and by considering likely malicious actors and their motivations.
2. Develop an incident response plan to quickly respond to security incidents with defined roles and procedures to contain damage.
3. Create a disaster recovery plan to restore systems and access to data through backups, alternative sites, and procedures for recovering from outages.










![Disadvantages Of Biometric System
1. Introduction
Biometric technology provides several advantages over conventional security methods like pin,
password, key, card etc. The Biometric system grants authentication by different physiological and
behavioral traits of a person.
Biometric systems are basically of two types based on the use of a biometric trait for identification
and verification. The types of biometric system are
Unimodal biometric system
Multimodal biometric system
The Unimodal system has an only single source of information for authorization of a valid user.
But sometimes single trait do not provide good quality of sample due to deformations problem in a
biometric trait such as the same sample of hand geometry do not capture after swelling, face images
changes ... Show more content on Helpwriting.net ...
Problems which occur in unimodal biometric systems are alleviated by a new approach i.e.
multibiometric. Multimodal systems are the combination of more than one unimodal biometric
traits. It includes more than one modalities of a single user for providing better acceptability,
accuracy, performance and reliable authentication [2]. Fig 1 Different category of Multi Biometrics
The level of Security is also increased by this technique as compared to unimodal. Multimodal
Vivechana: National Conference on Advances in Computer Science and Engineering (ACSE 2016),
Department of Computer Science and Applications, Kurukshetra University Kurukshetra
2
biometric is one of the types of five categories of the multibiometric system as shown in Fig 1.
1.1 Classifications of Multibiometric System
1.1.1 Multiple sensor systems
Multiple sensor systems capture single biometric trait by using two or more different sensors. For
authentication, fingerprint samples taken by optical and solid state sensor [3].
1.1.2 Multiple representation systems
In this type multiple representation methods are used for storing template. Template is
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/fcewritingessayquestion-240130011549-d7916cb6/75/Fce-Writing-Essay-Question-12-2048.jpg)





![1950s Music Timeline
1. Timeline: Trace the history of American popular music in the 1950s. Include dates, major styles,
By Angelika Lowder
1950 had cassette tapes.
The period of Roll n Roll and Elvis Presley The spectacular fifties.
They were light songs with sweet verses sung by the best craftsmen ever. The tunes were guiltless
and tame suited for the state of mind of the world Post Second World War.
As a consequence of the advancements in music in the late 40 s music of the 50s thrived and
caught the heart of millions. The 1950s were considered as a period of progress and saw the
introduction of another music sort which reclassified the music business.
The greatest commitment of the Early 50s towards the universe of music is Rock and Roll. It ...
Show more content on Helpwriting.net ...
Johnny Ray s Cry is the primary melody by a white cadence and soul artist to beat both the pop
and R B outlines
1953
The Dixie Hummingbirds How about we Go Out to the Programs turns into a noteworthy hit, their
mark melody and an exemplary bit of gospel.
Elvis Presley records his first tunes, My Happiness and That is When Your Heartaches Begin .
These records would acquaint Presley with Sam Phillips, who worked for Sun Records.
1954
Elvis Presley records That is All Right (Mama) and Blue Moon of Kentucky , both leap forward
recordings that propelled his vocation and conveyed African American musical methods to white
groups of onlookers
Mahalia Jackson turns into the main gospel entertainer with her own network show, the Mahalia
Jackson Show, on CBS
1955
Elvis Presley s I Forgot to Remember to Forget is a noteworthy hit that builds up Presley as a
nation star.
Throw Berry records Maybellene with Jerome Green and Willie Dixon.[103] This melody,
alongside Bo Diddley s Bo Diddley and Pretty Thing , promote the utilization of the guitar as the
central instrument of beat and soul.](https://image.slidesharecdn.com/fcewritingessayquestion-240130011549-d7916cb6/75/Fce-Writing-Essay-Question-18-2048.jpg)







































![Science, Technology and America’s Military Essay
Science, Technology and America s Military When it comes to the latest and fastest computers
there is one place that all that technology can be found, the United States Military. There is no
doubt that the U.S. Military is one of, if not the most technologically advanced armed forces in the
world. Over our countries development we have changed from a grind it out fighting machine, to a
more advanced, rapid tactical corps to meet the different battle situations found in today s world. [1]
This transformation has taken place largely in the last century with the advancement of computer
technology helping to reshape the battle field to our advantage. Our nation is constantly looking for
the advantage during conflict, and for... Show more content on Helpwriting.net ...
The simulators used today are extremely accurate as to the limitations of people and equipment,
and as advances in technology improve so do the simulators, as they become more and more
realistic. Computer game technology is also responsible for these improvements; today s video
game consoles have many times the computing power than the military s simulators a few years
ago.2 The army has even developed its own video game based on the simulators it uses for
combat training. Americas Army is more than just a shoot em up game; it is built to portray a
real soldiers life, everything from basic training to choosing a career. According to one of the
games designers, Lt. Col. Casey Wardynski, the game took over two years and around $8 million
dollars (USD) to develop, but the main point of the game is education of real Army life, and is
said to be the most realistic game ever developed. Simulators cannot however depict every aspect
of military life, dealing with other team members, salty commanders, and there is nothing to
simulate being cold, tired and hungry at the end of the day. All in all however, simulators are a
vital part of today s military training and operations. In the near future, if it is not already possible,
I would not be surprised if a simulator can be developed for any situation by simply inputting a
given situation, and the soldiers will be able to use the simulator before going into the actual
combat situation.
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/fcewritingessayquestion-240130011549-d7916cb6/75/Fce-Writing-Essay-Question-58-2048.jpg)


