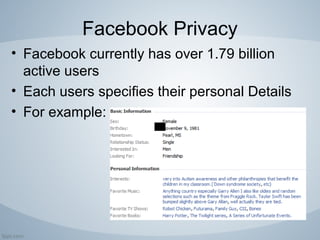
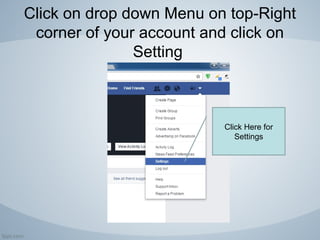
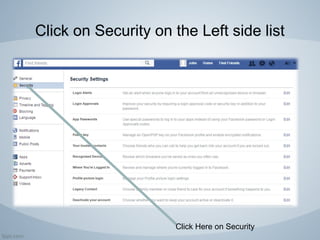
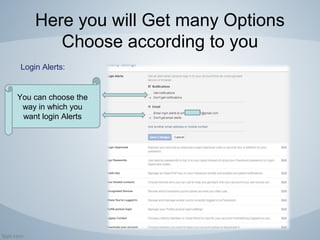
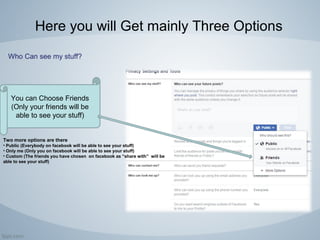
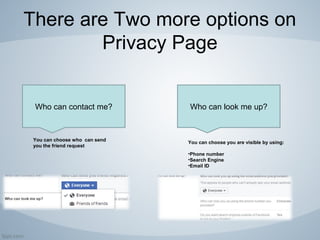
Facebook is a popular social networking platform with over 1.79 billion active users, emphasizing privacy and security for its users. It offers various settings to control who can see personal information and how one's account is secured, including login alerts and trusted contacts. The document also outlines steps to enhance account privacy and provides customer support contacts for further assistance.