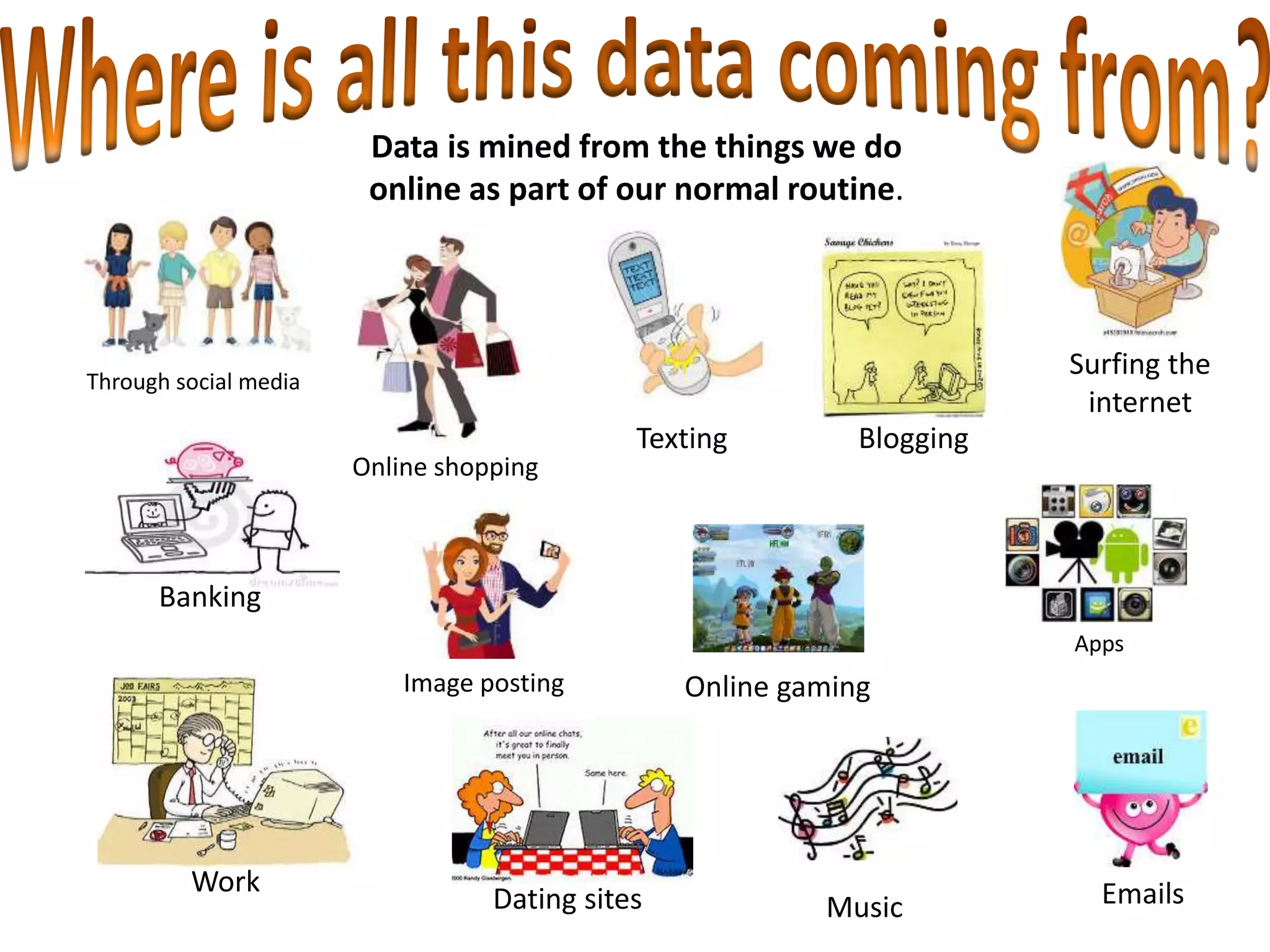
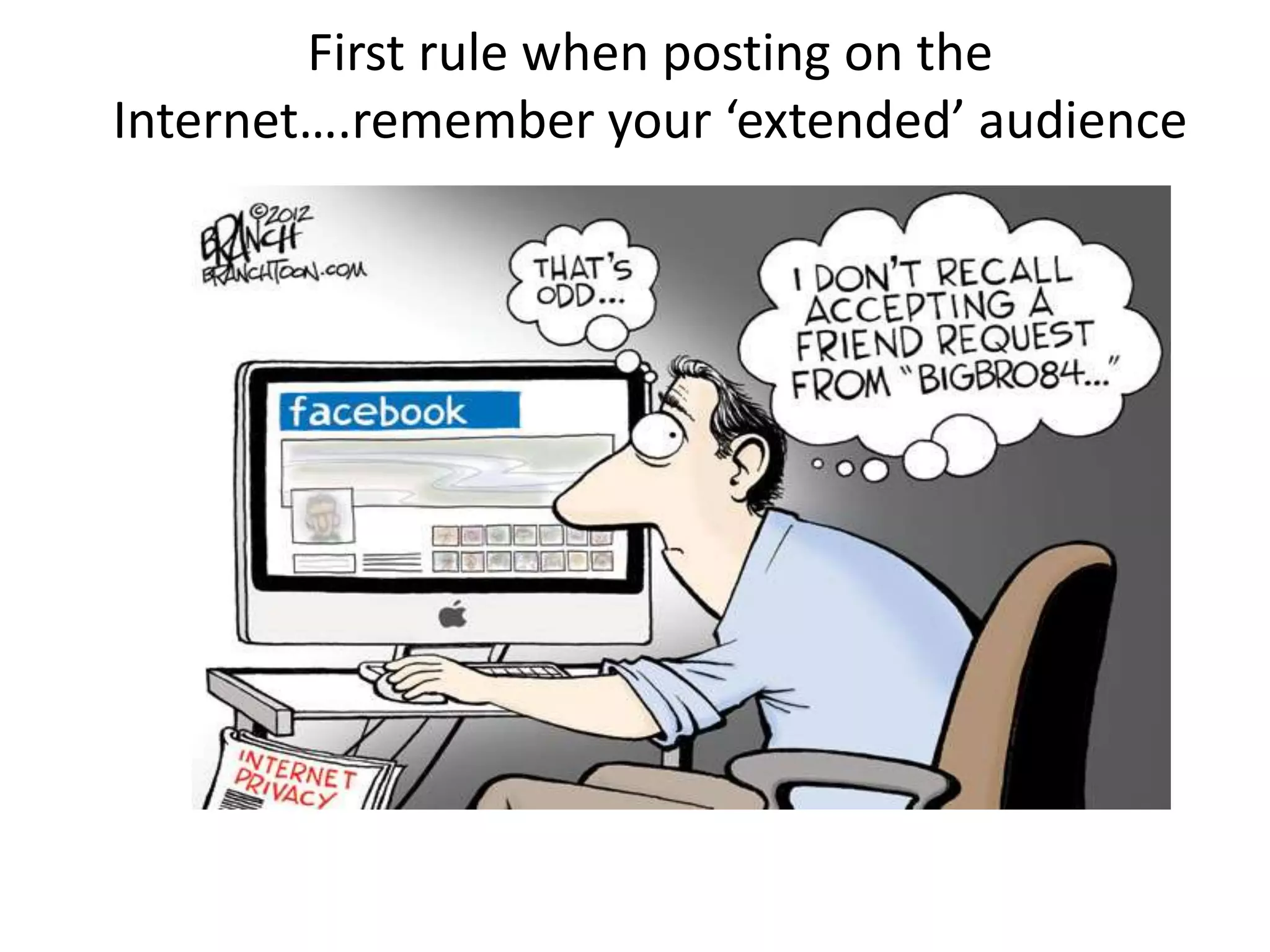
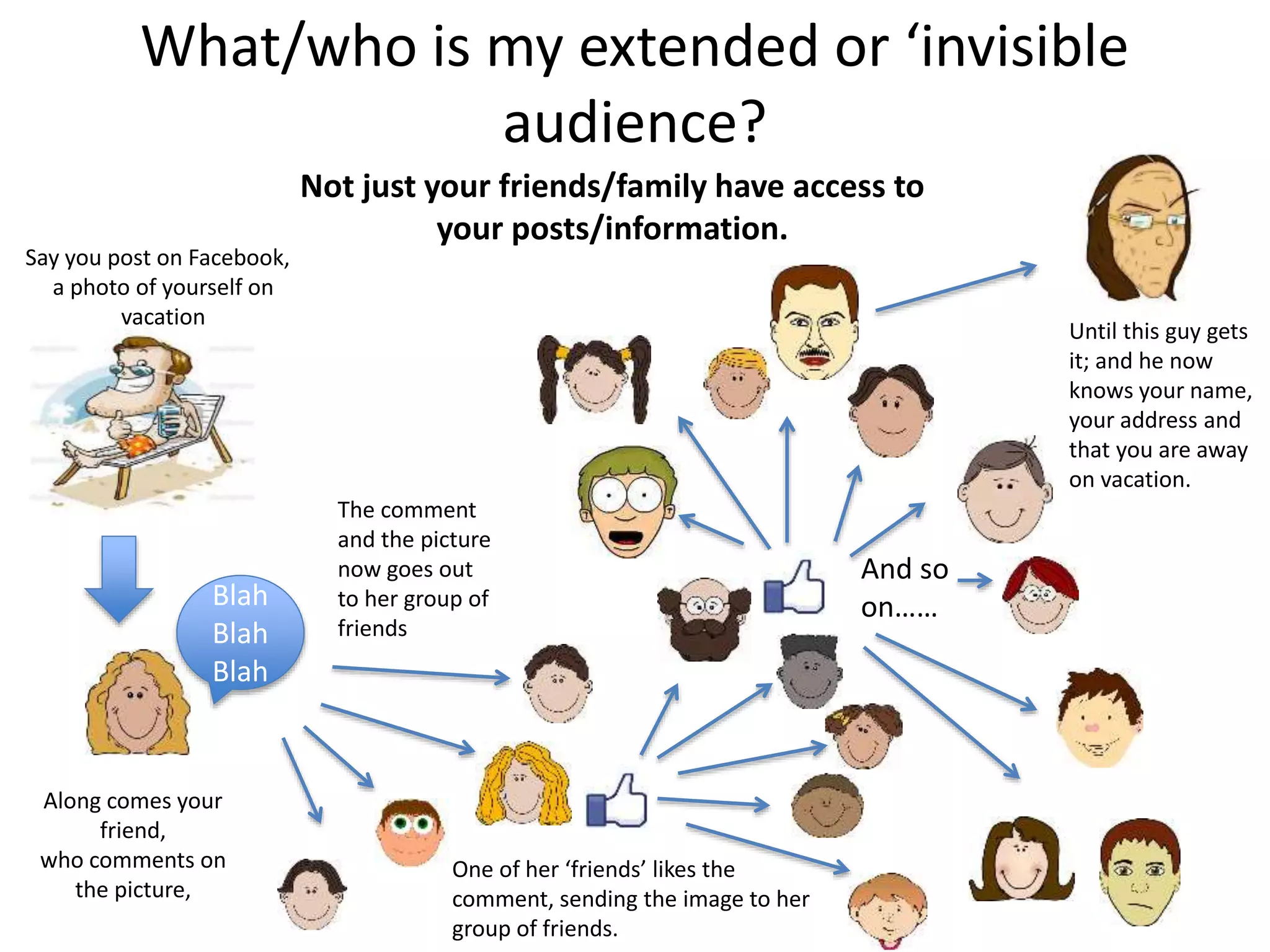
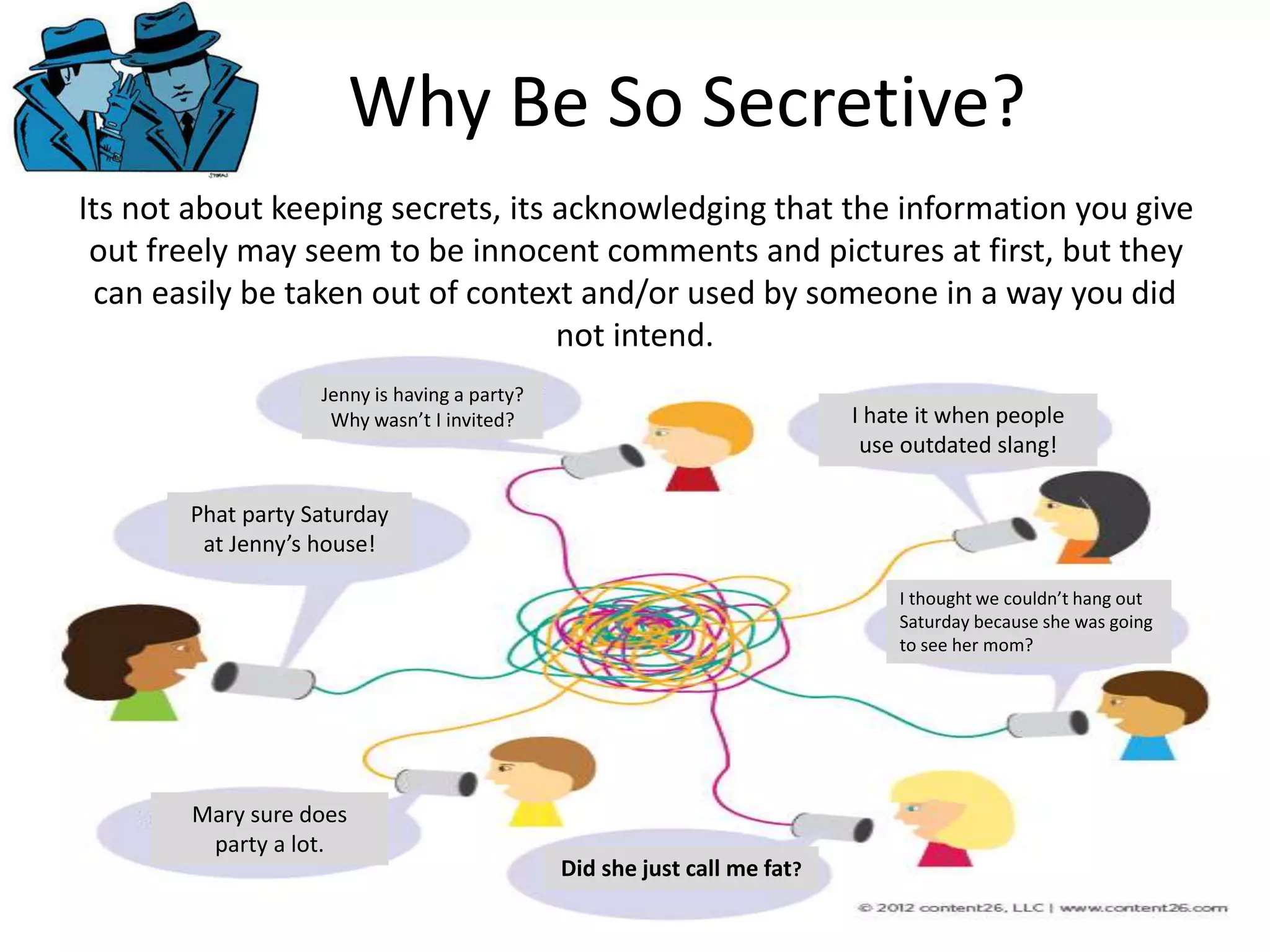
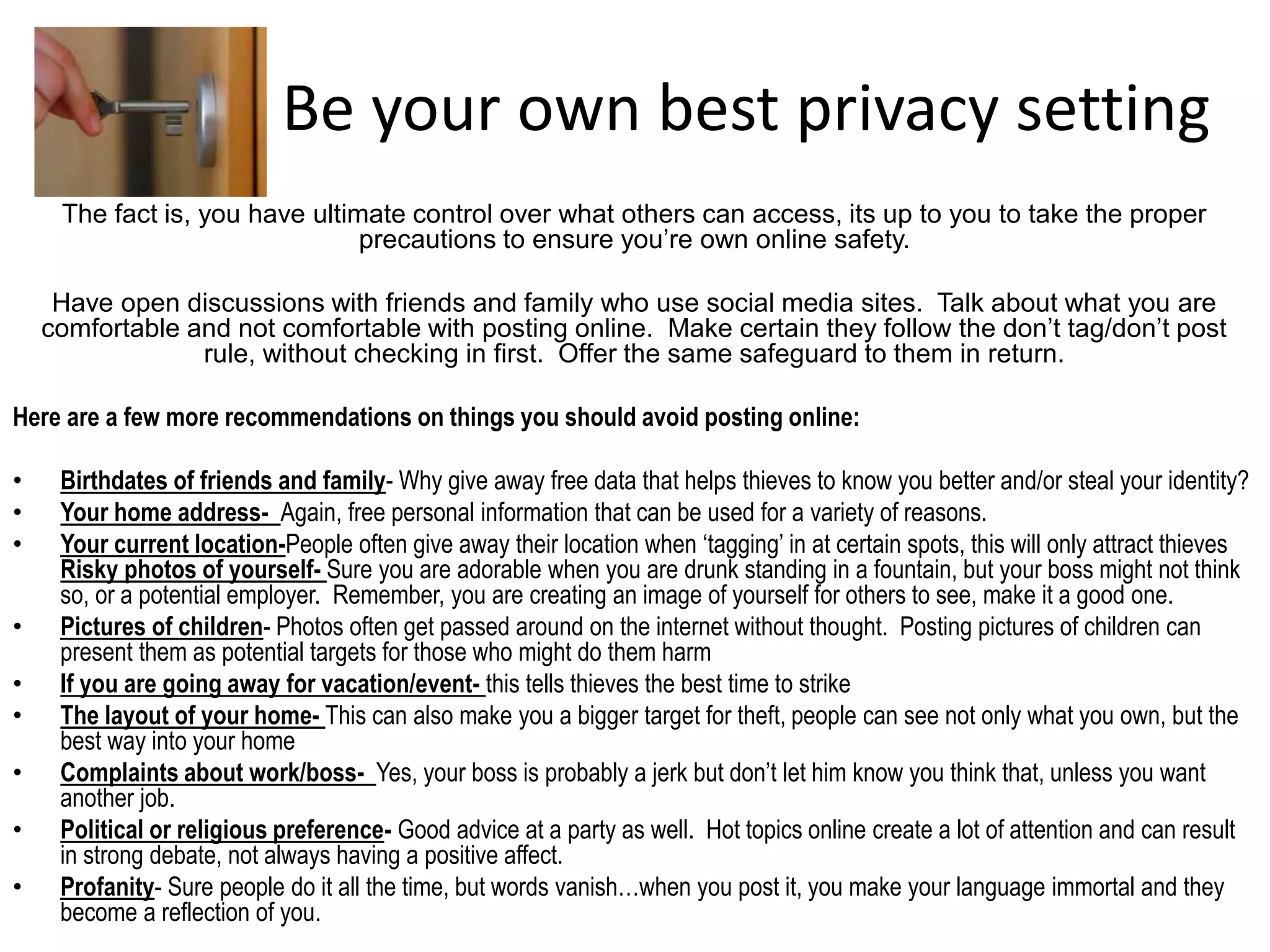
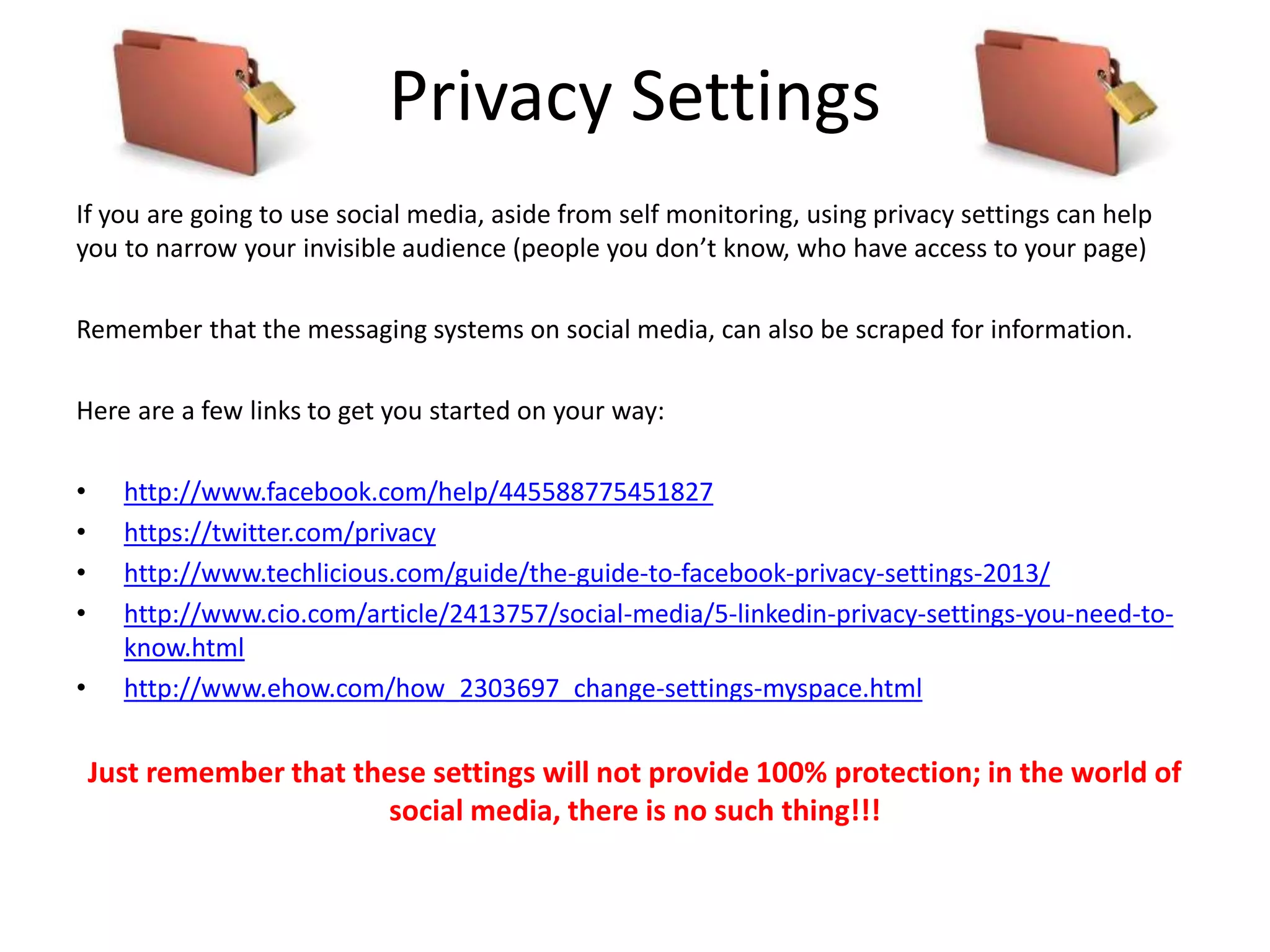
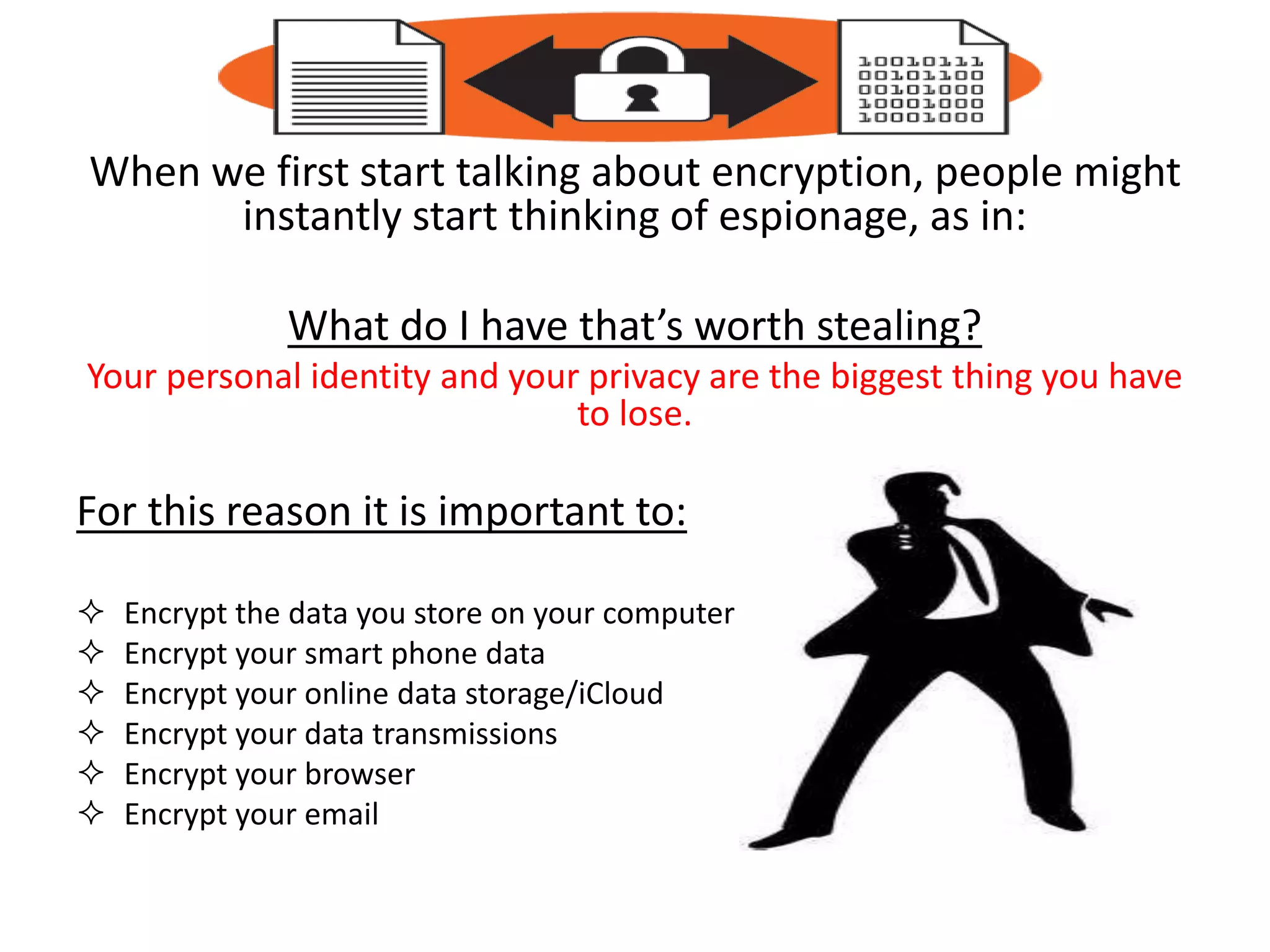
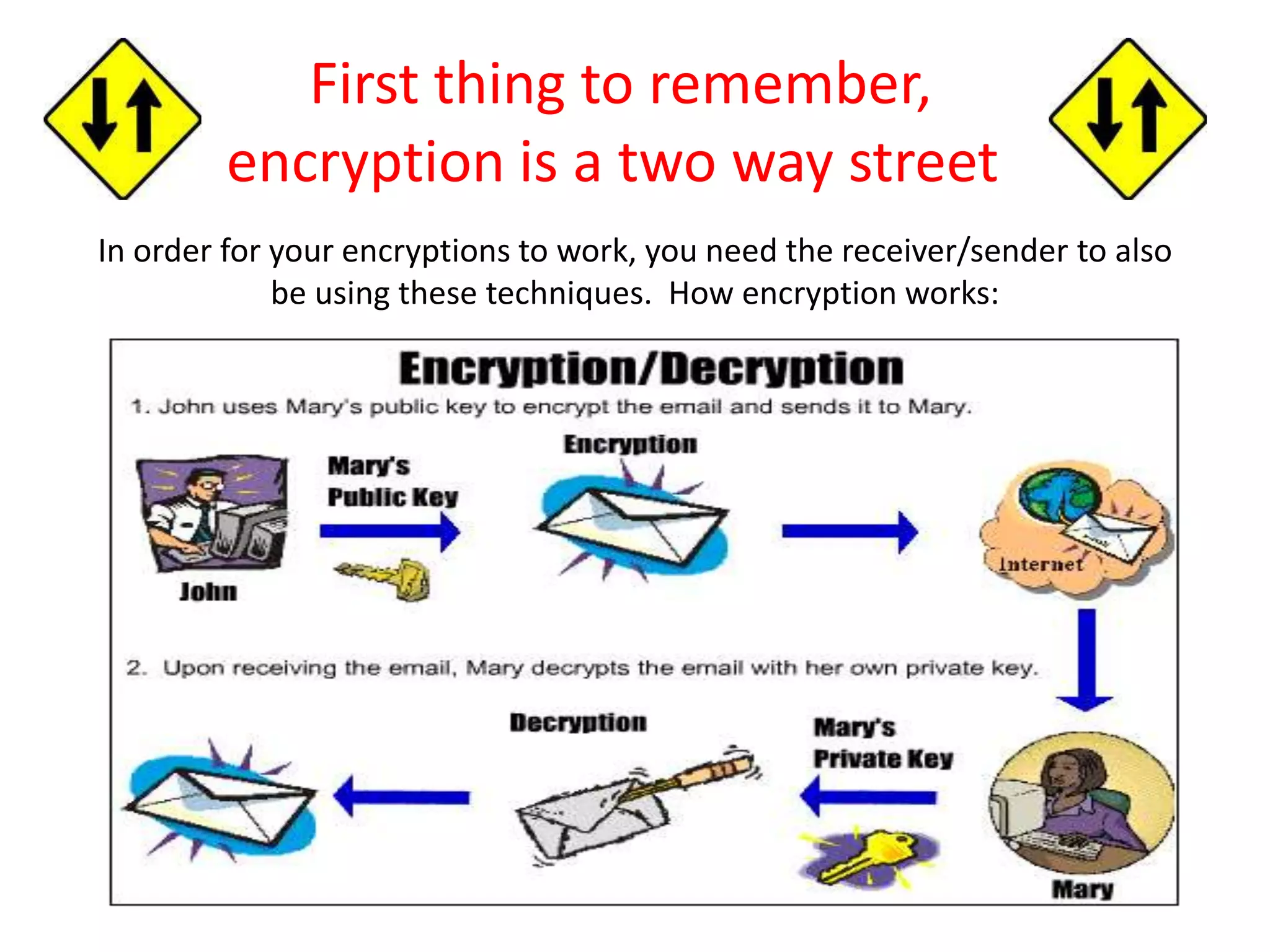
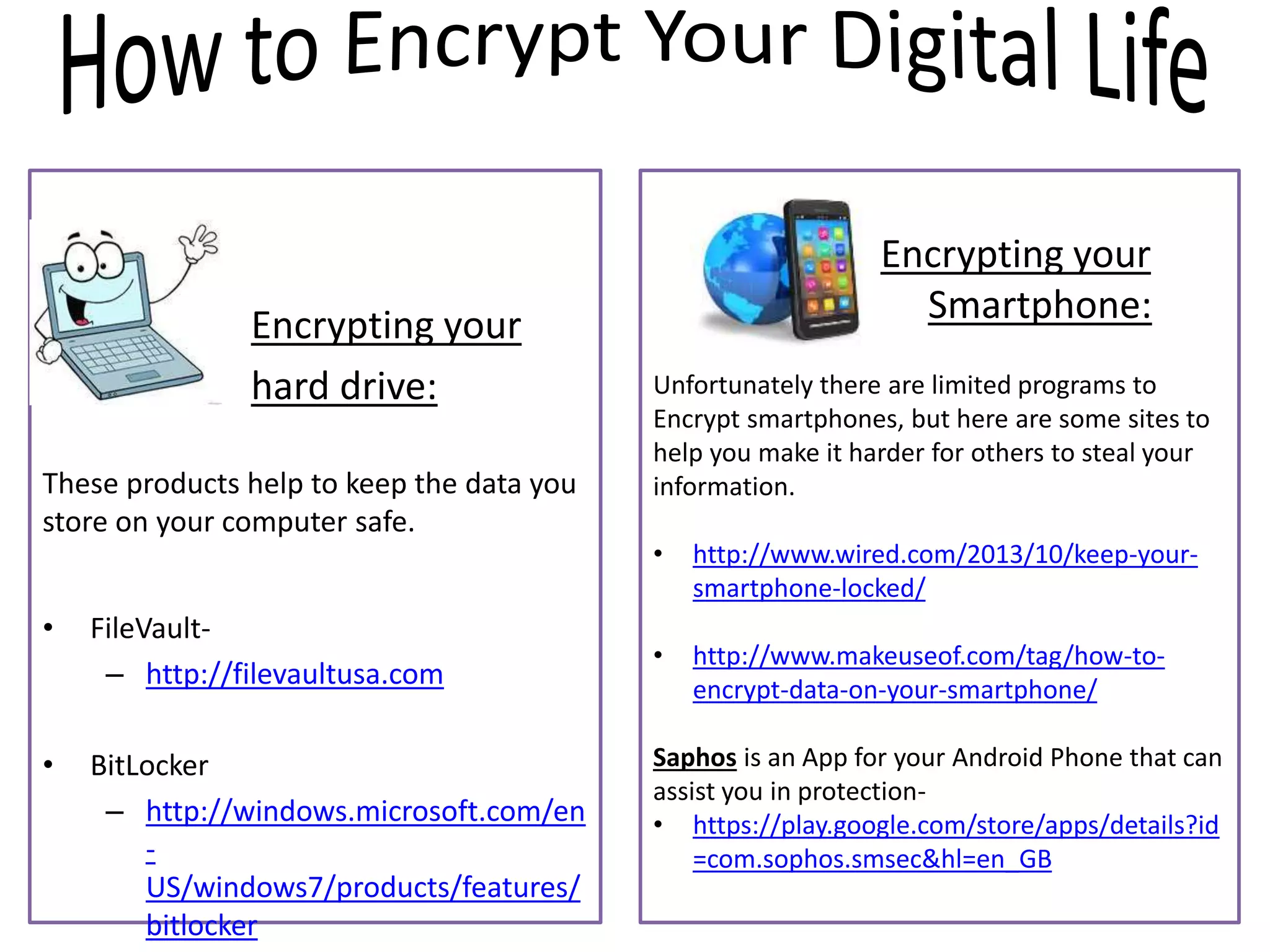
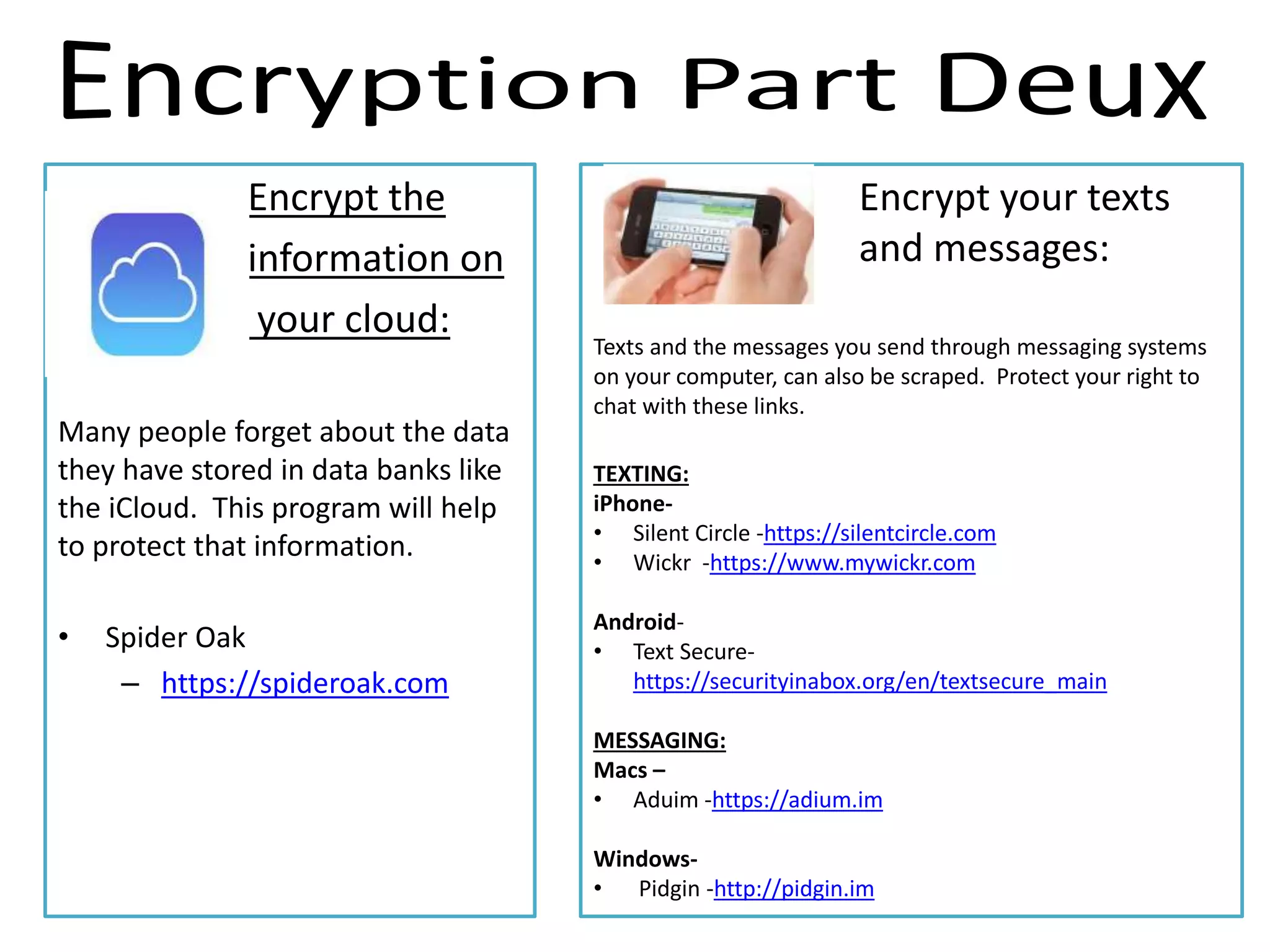
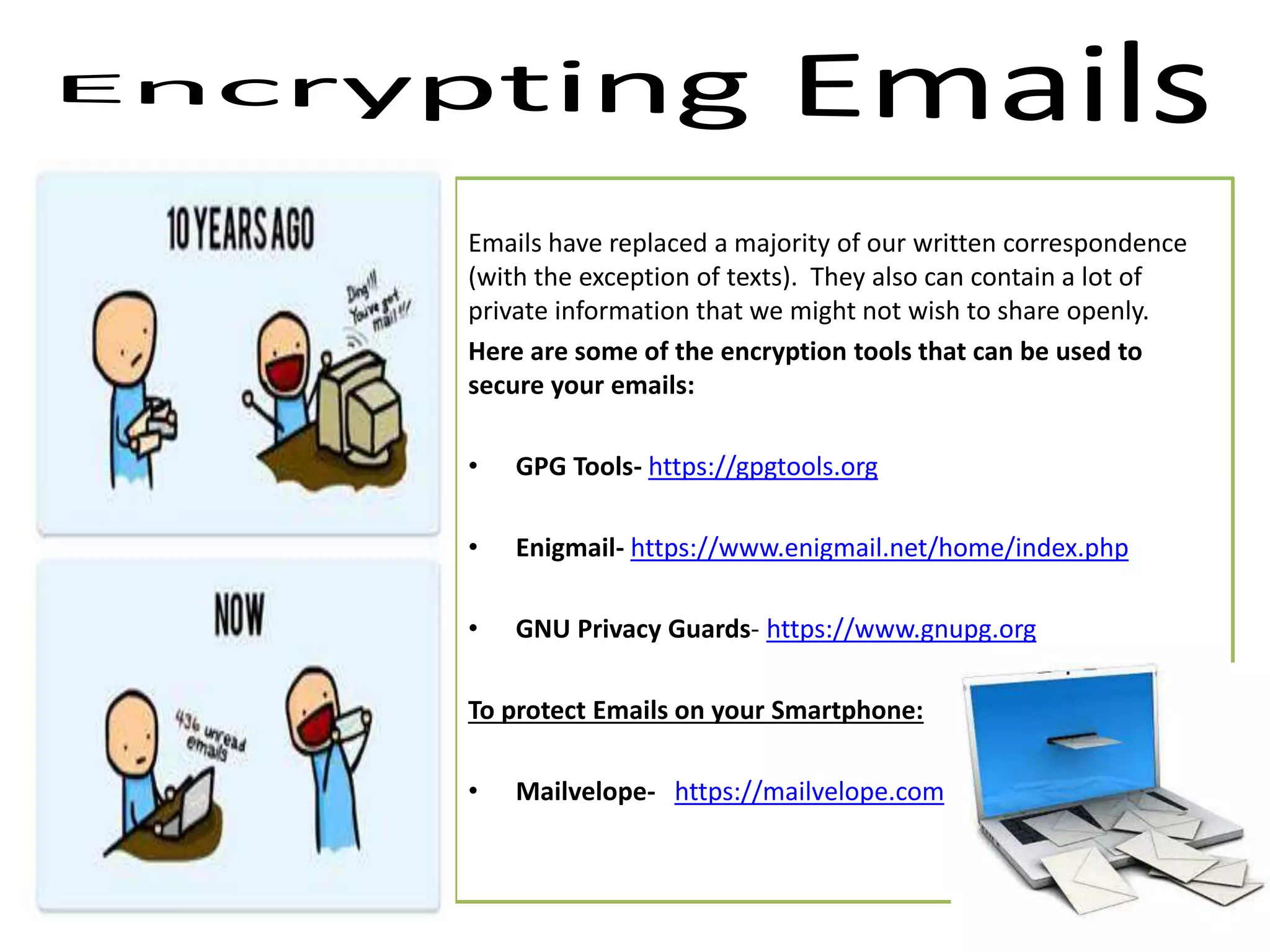
The document provides tips on how to safely manage personal information and privacy online. It discusses how personal data is collected from online activities like social media, emails, and web browsing. It notes that privacy settings don't guarantee absolute privacy and information can be shared beyond intended audiences. The document then offers recommendations to strengthen online privacy through practices like limiting personal details shared, using privacy settings, encrypting data and communications, and educating friends and family.