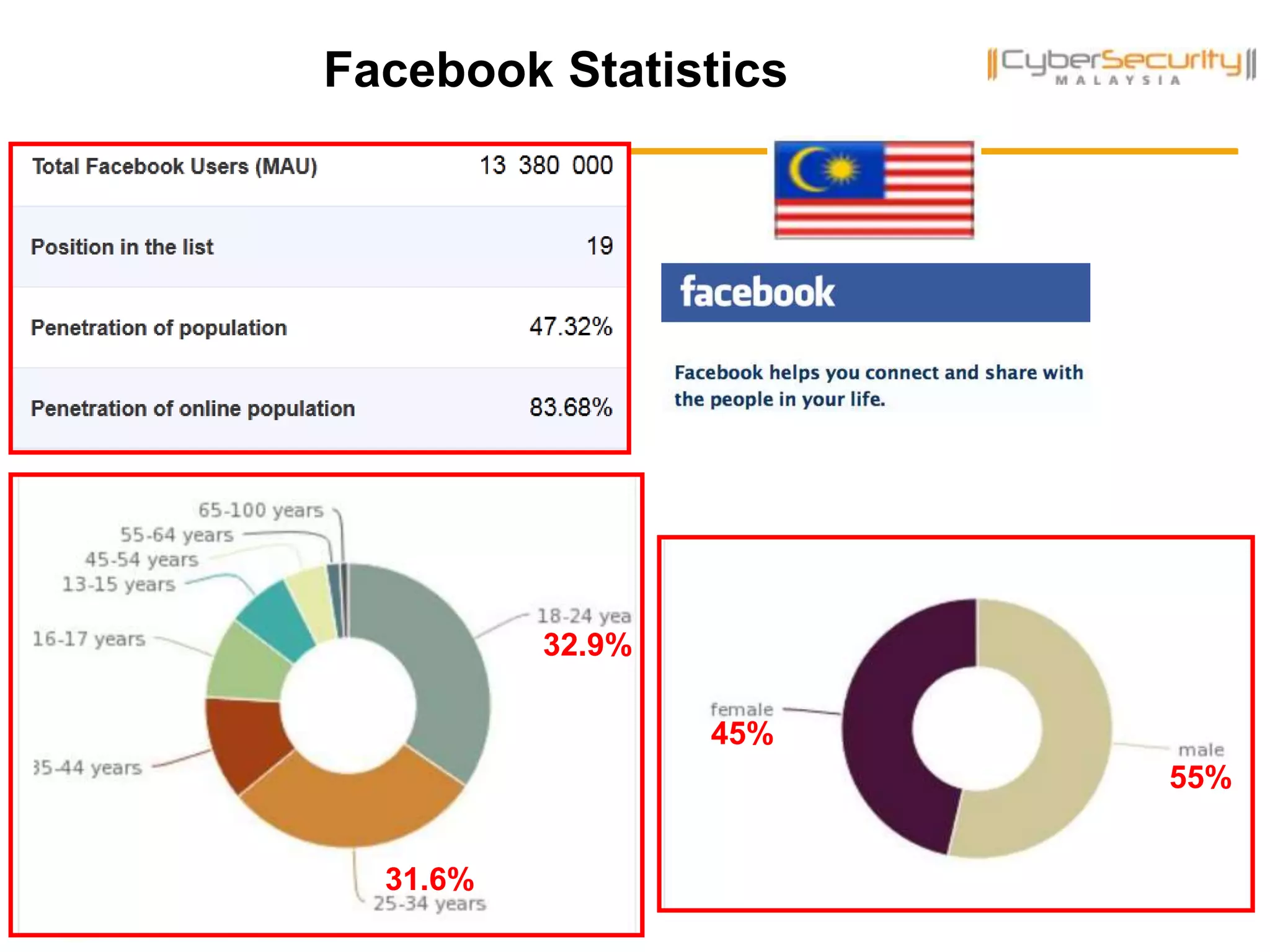
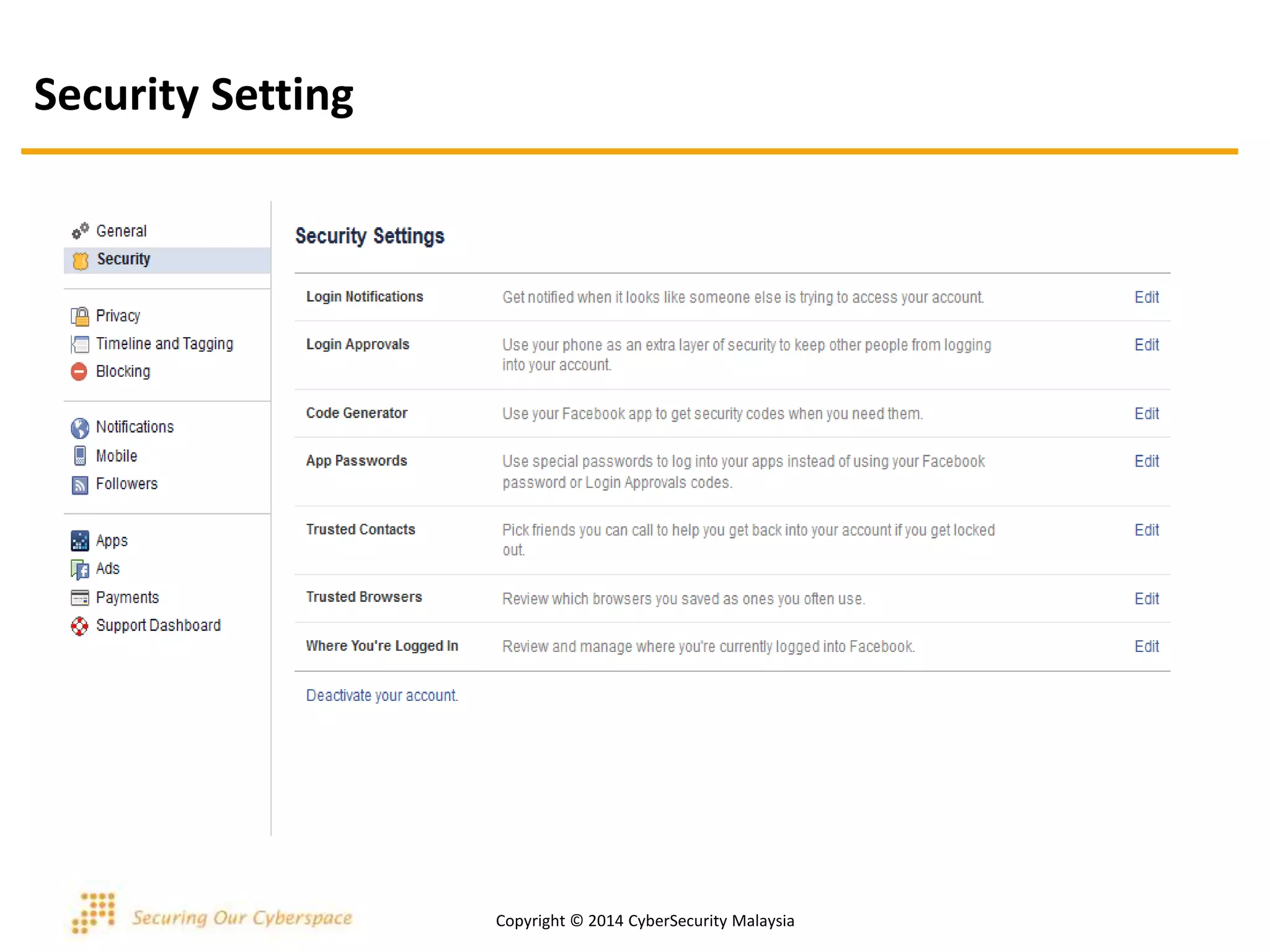
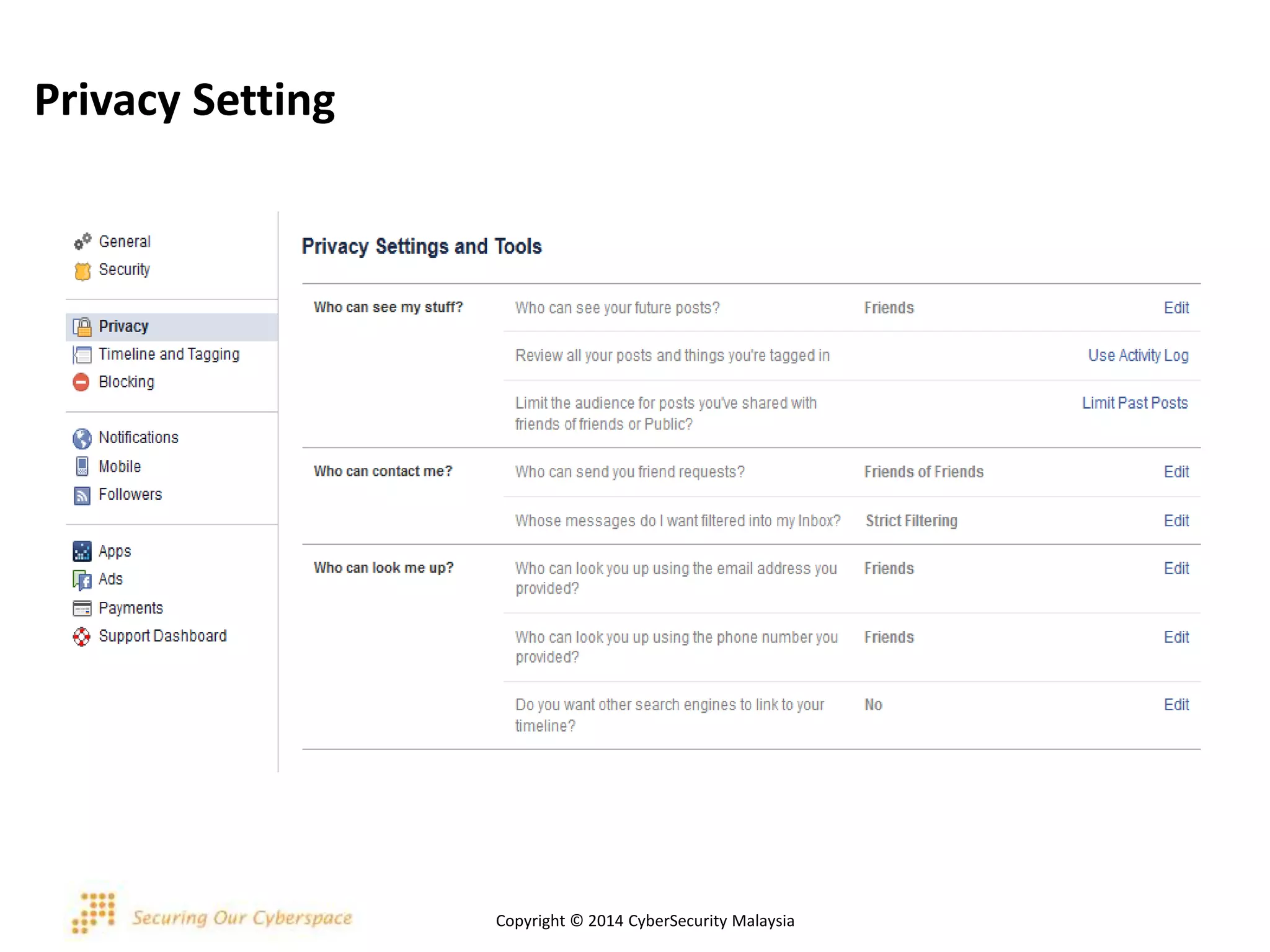
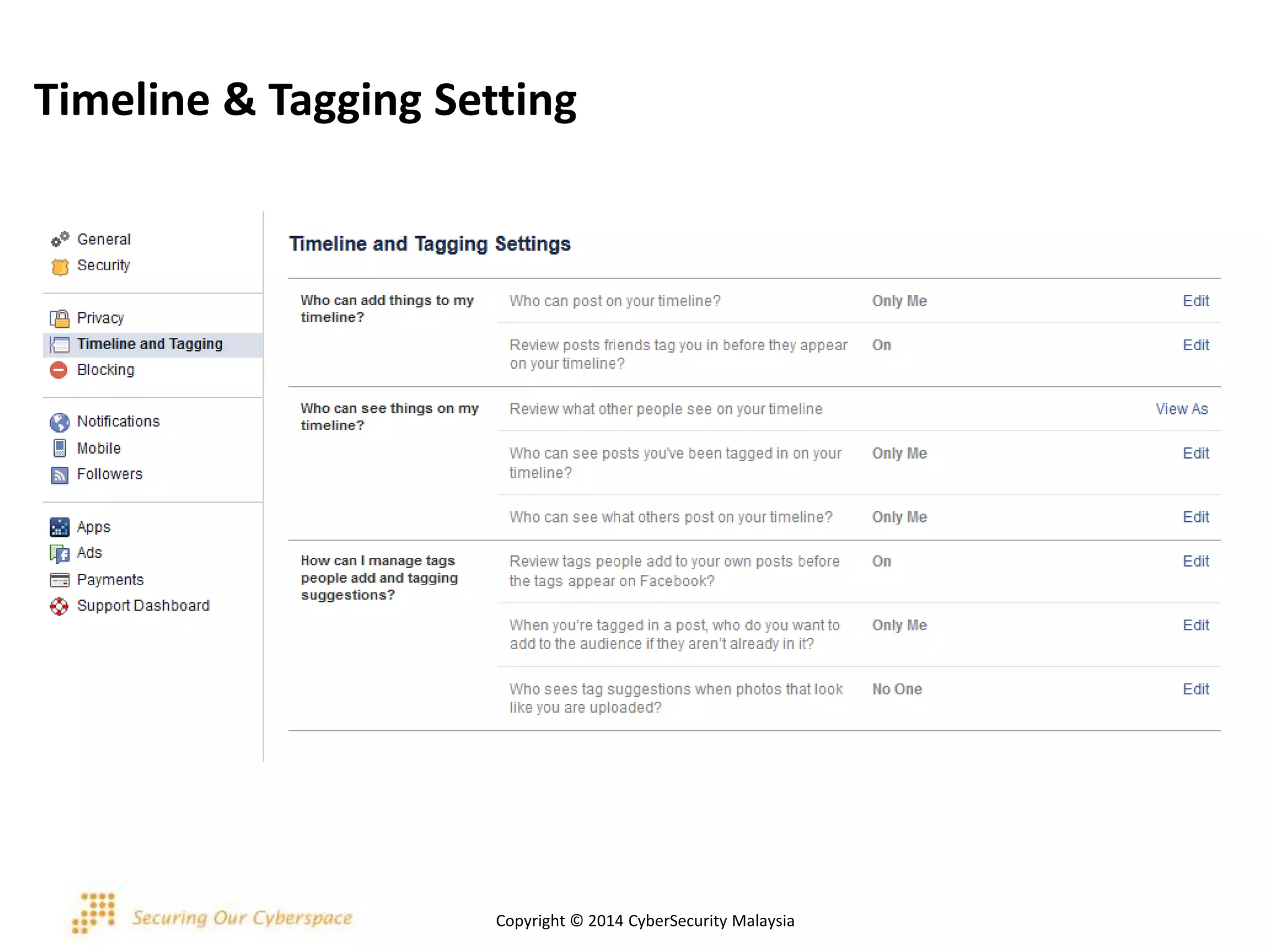
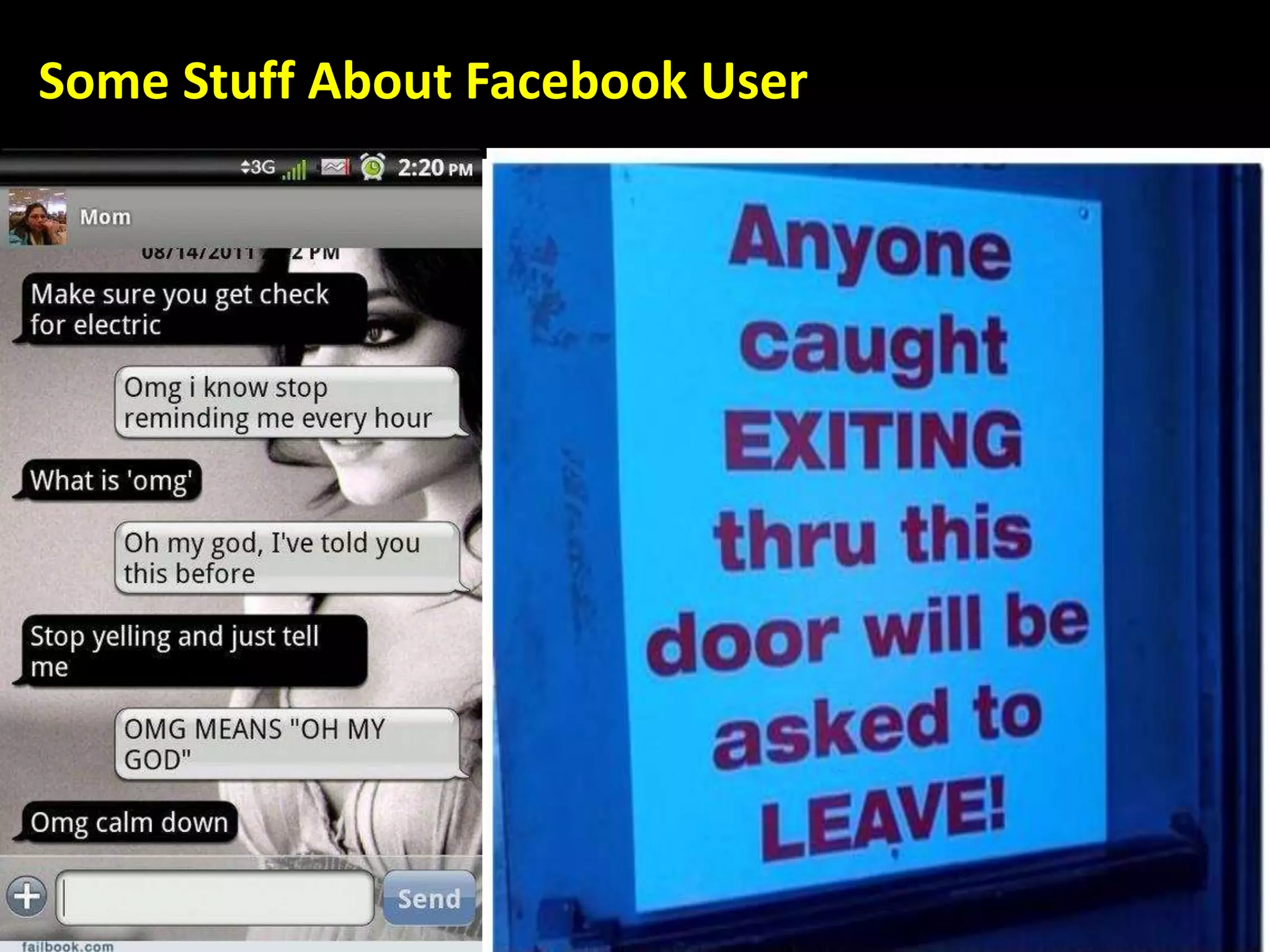
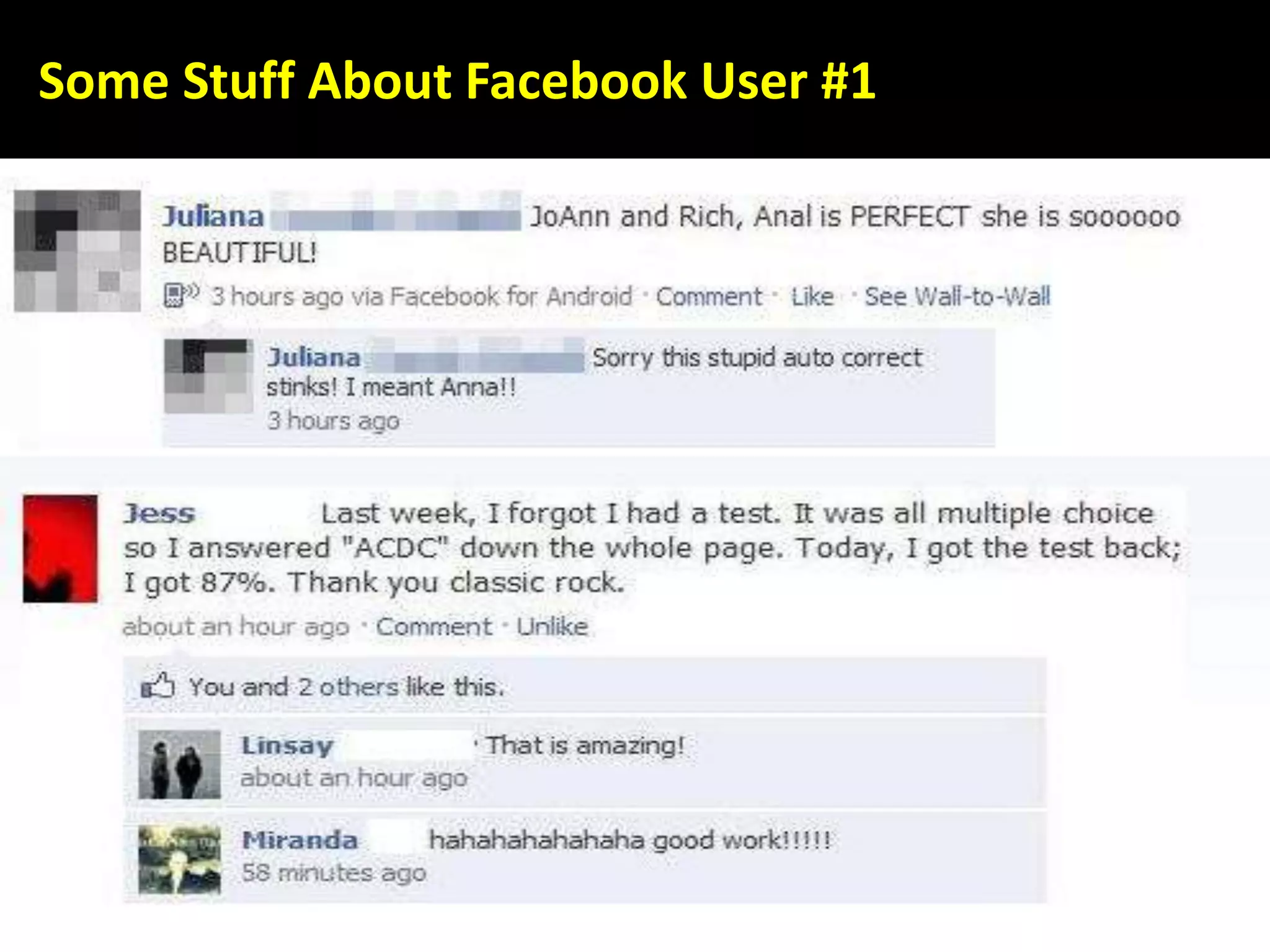
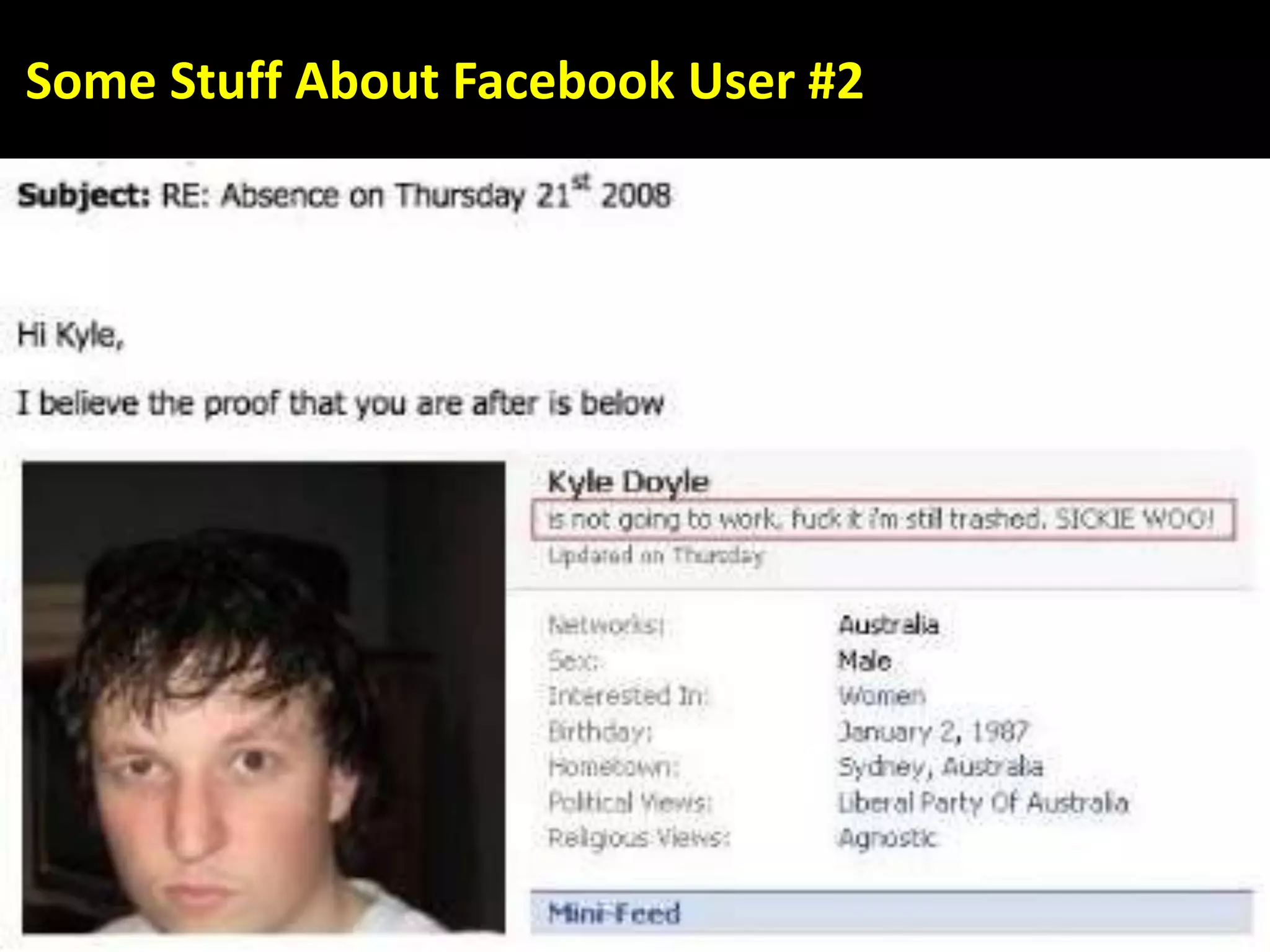
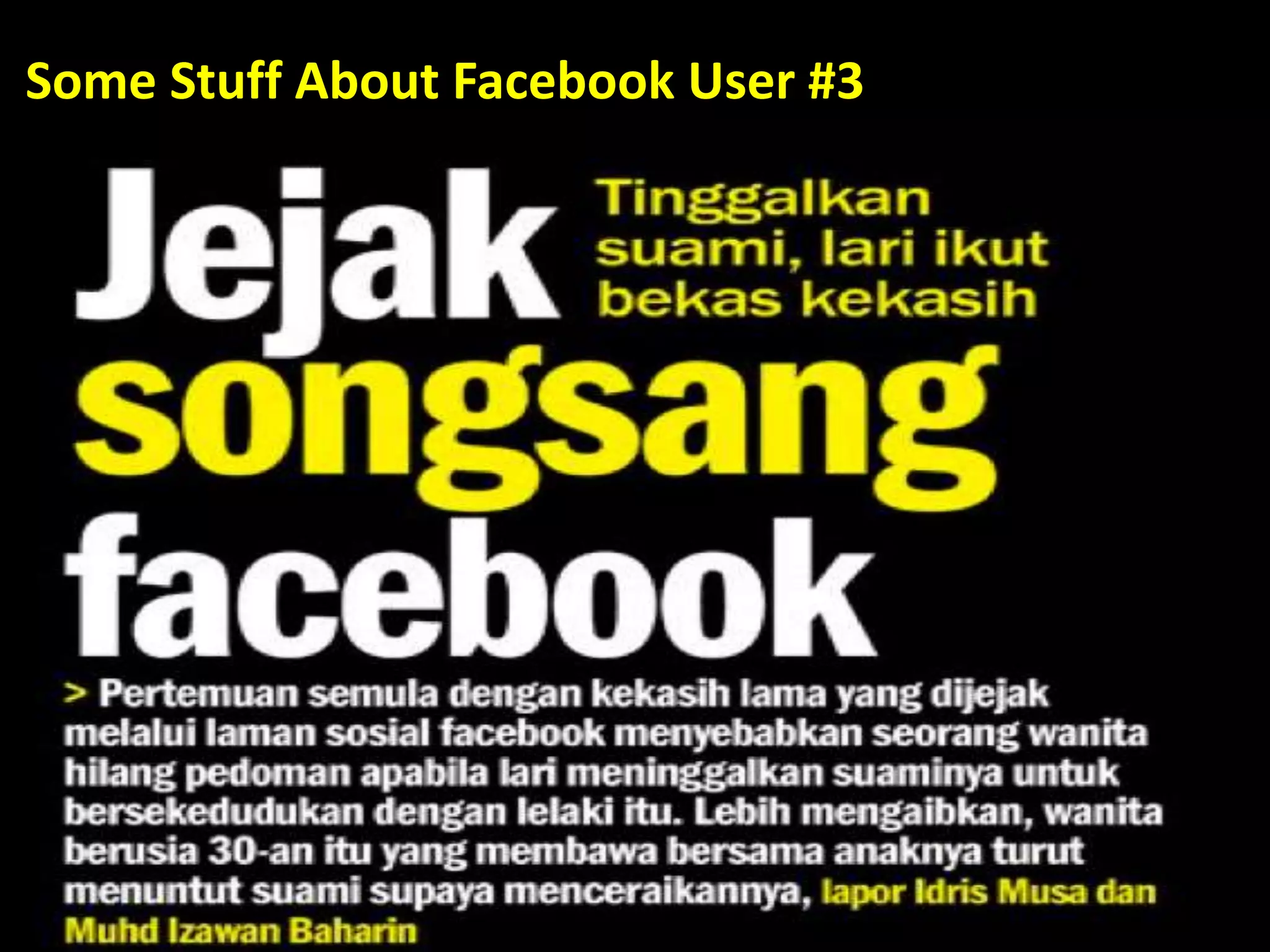
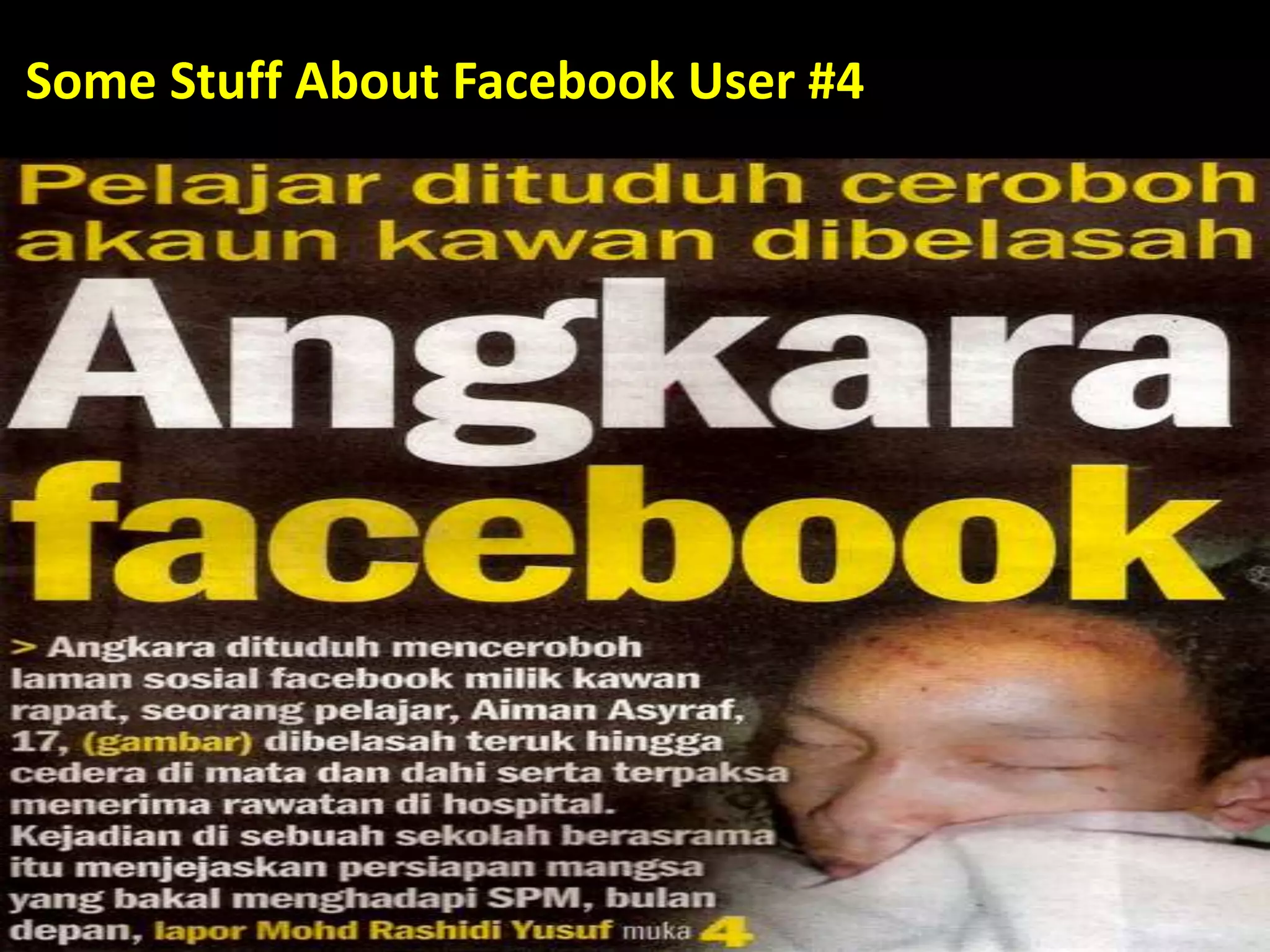
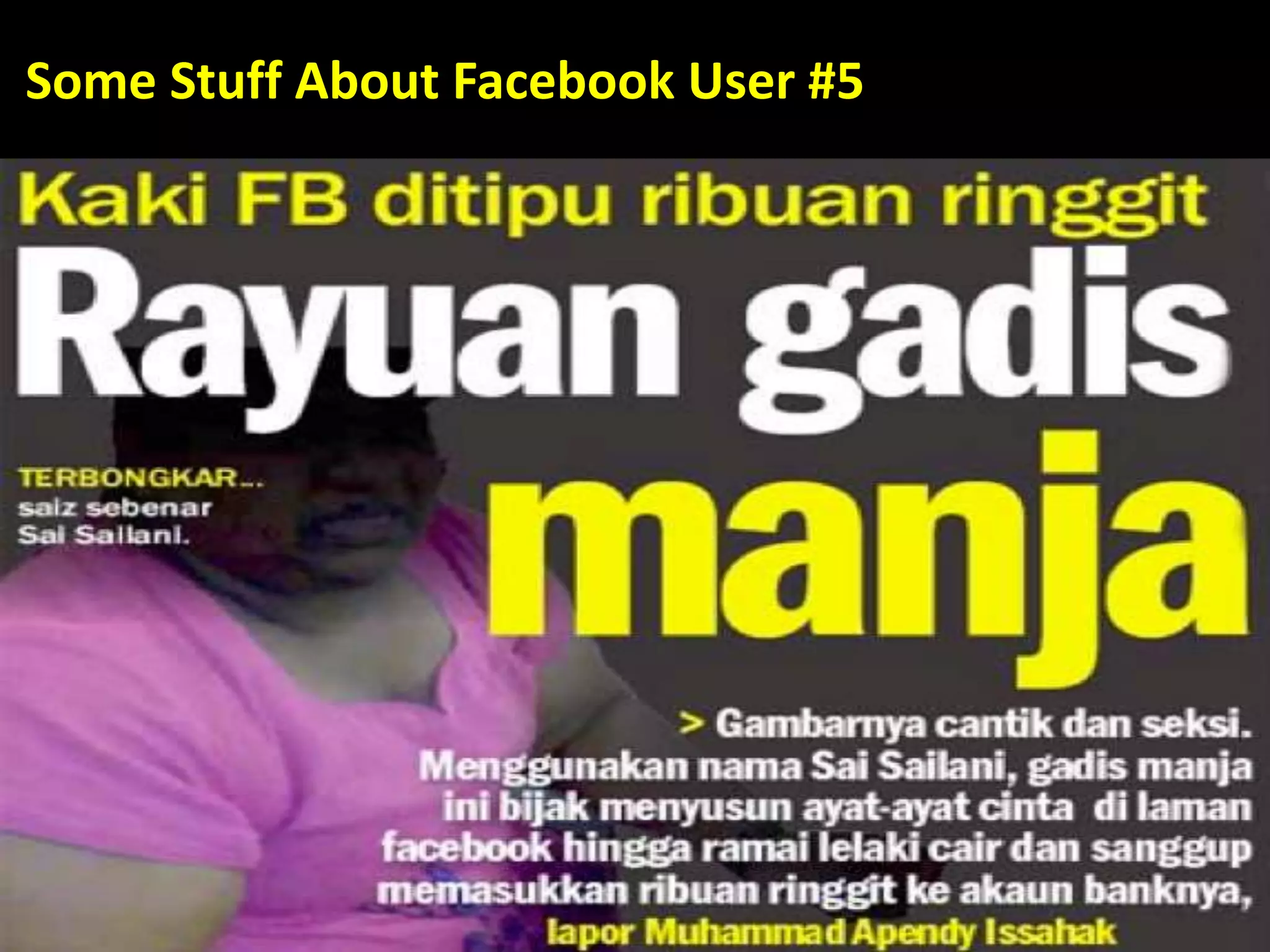
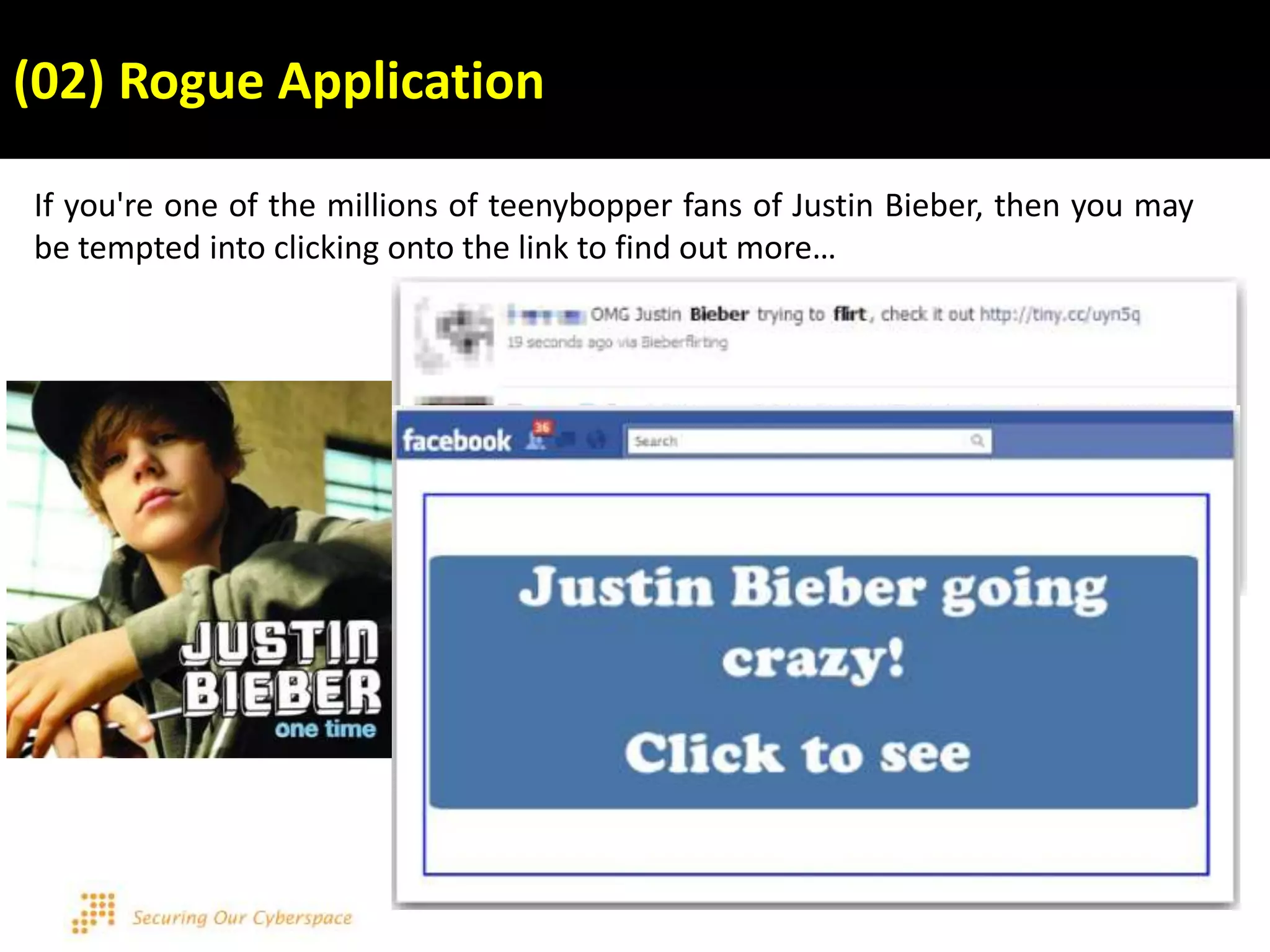
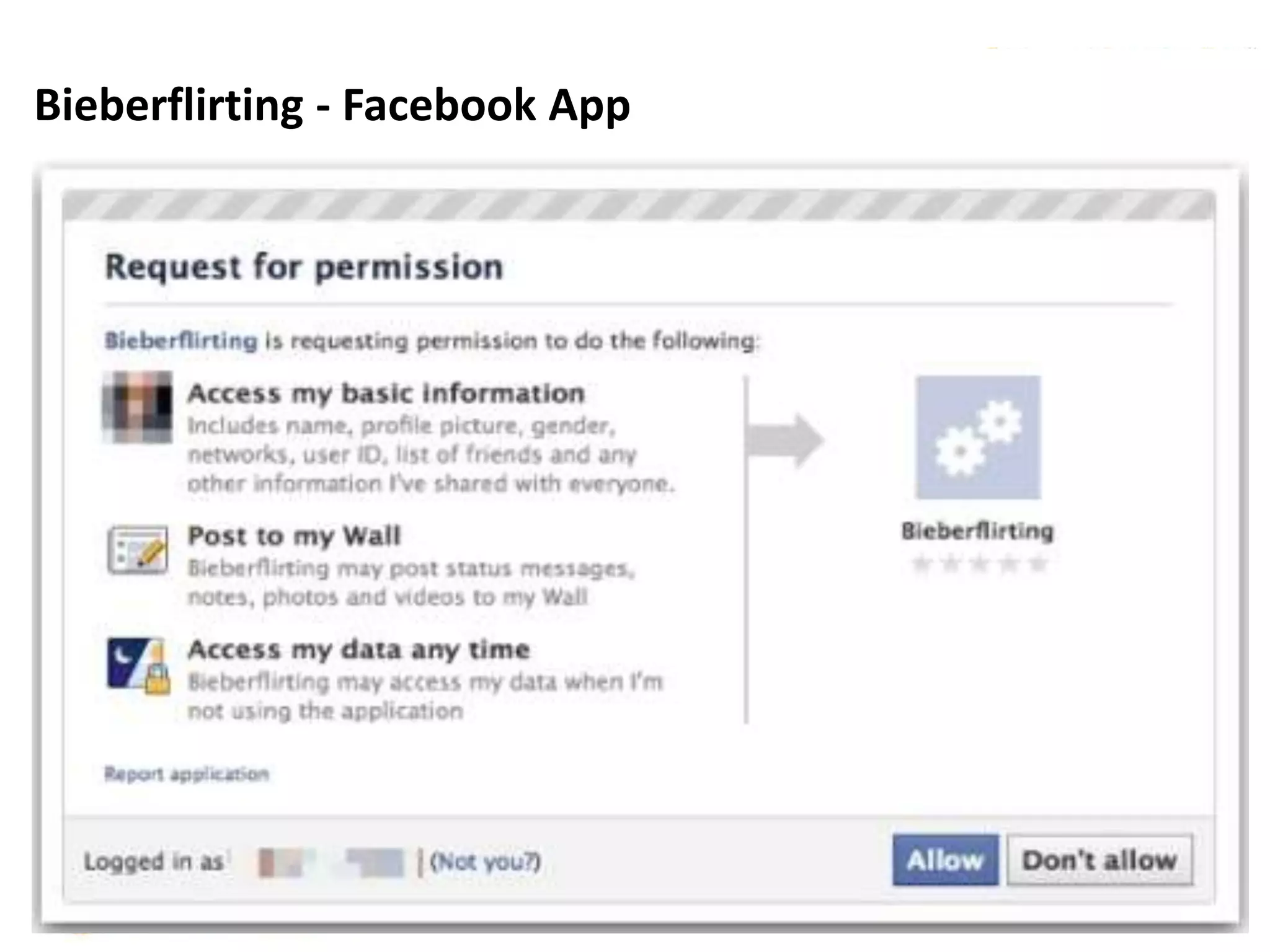
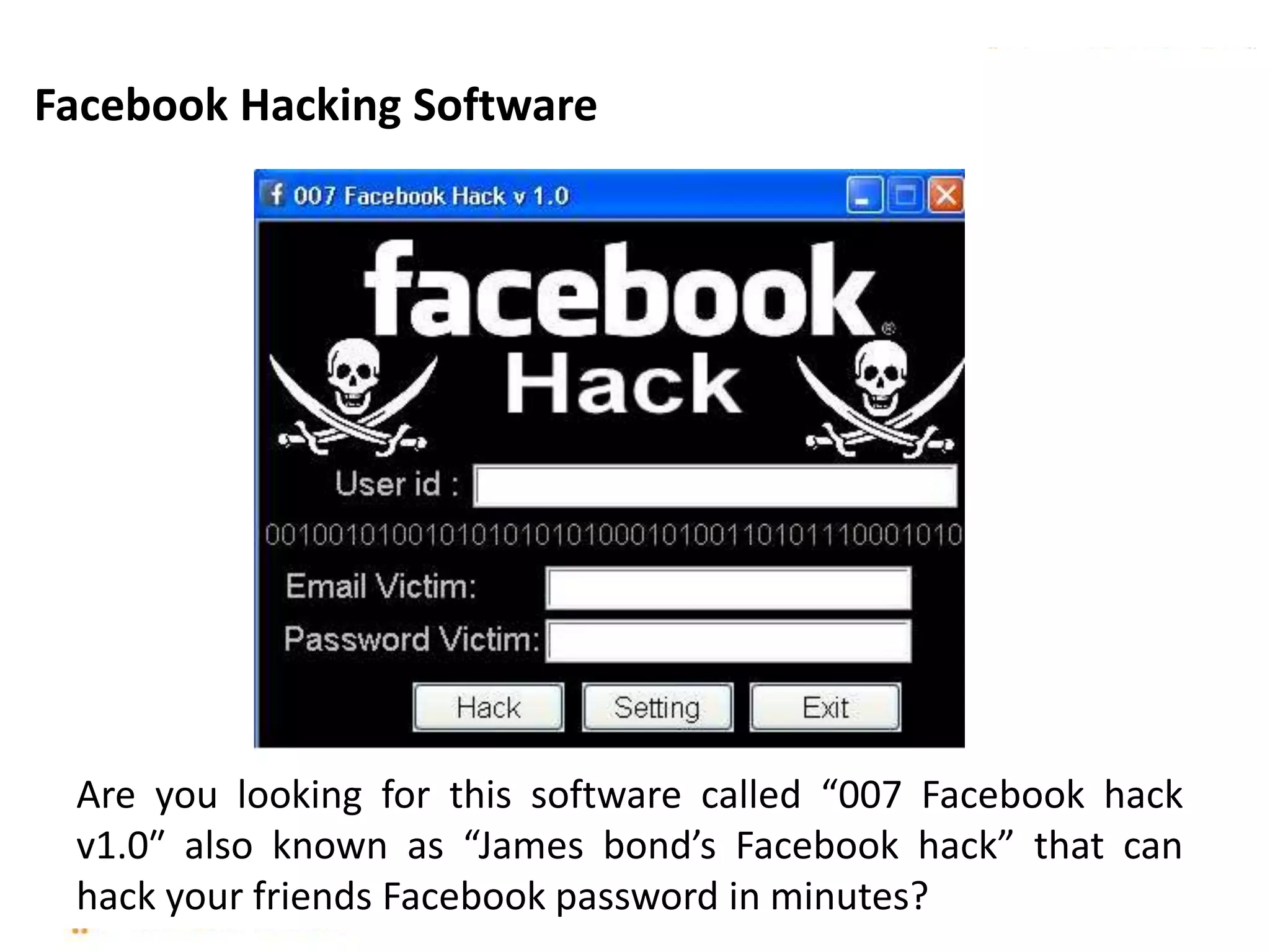
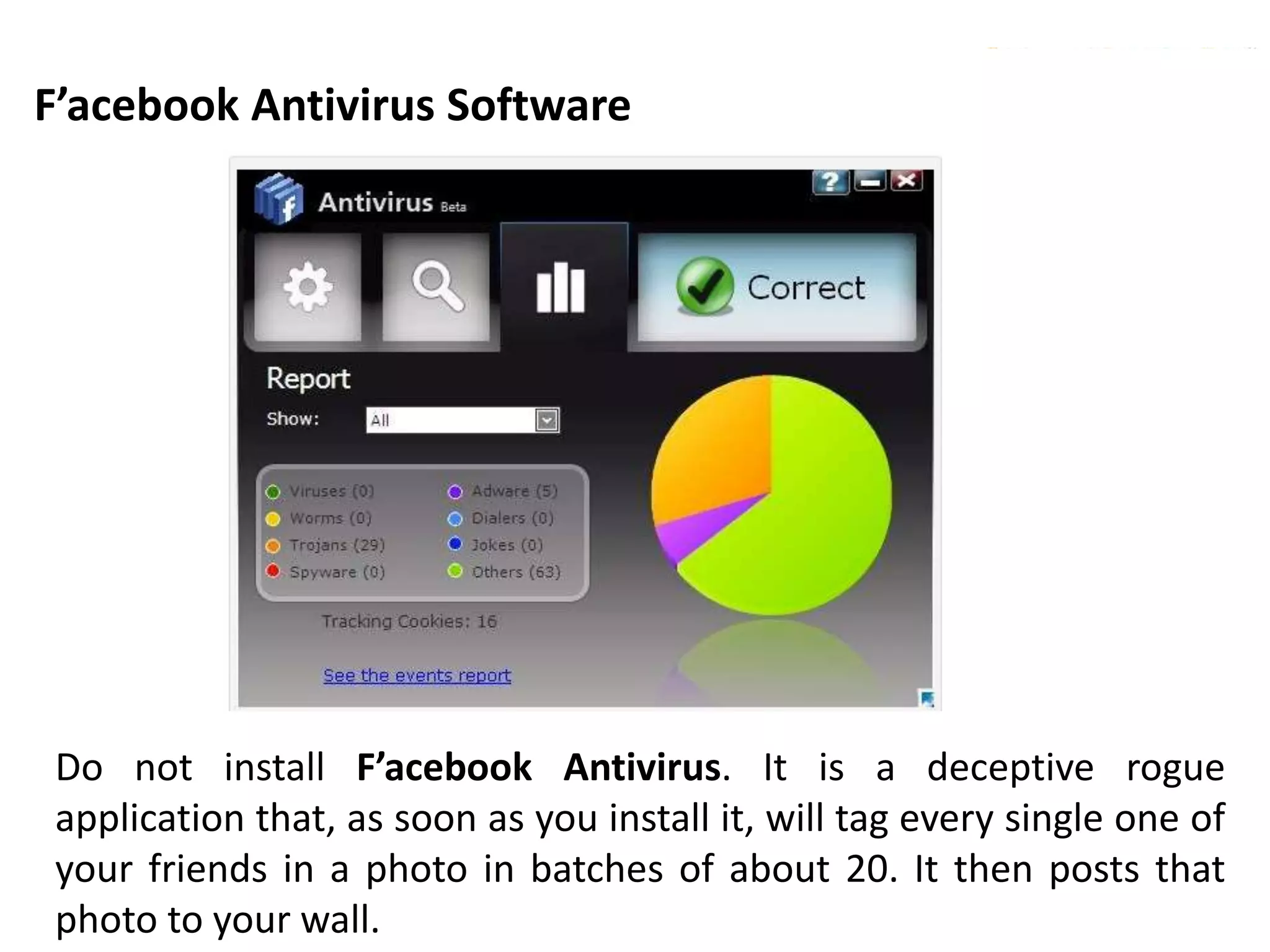
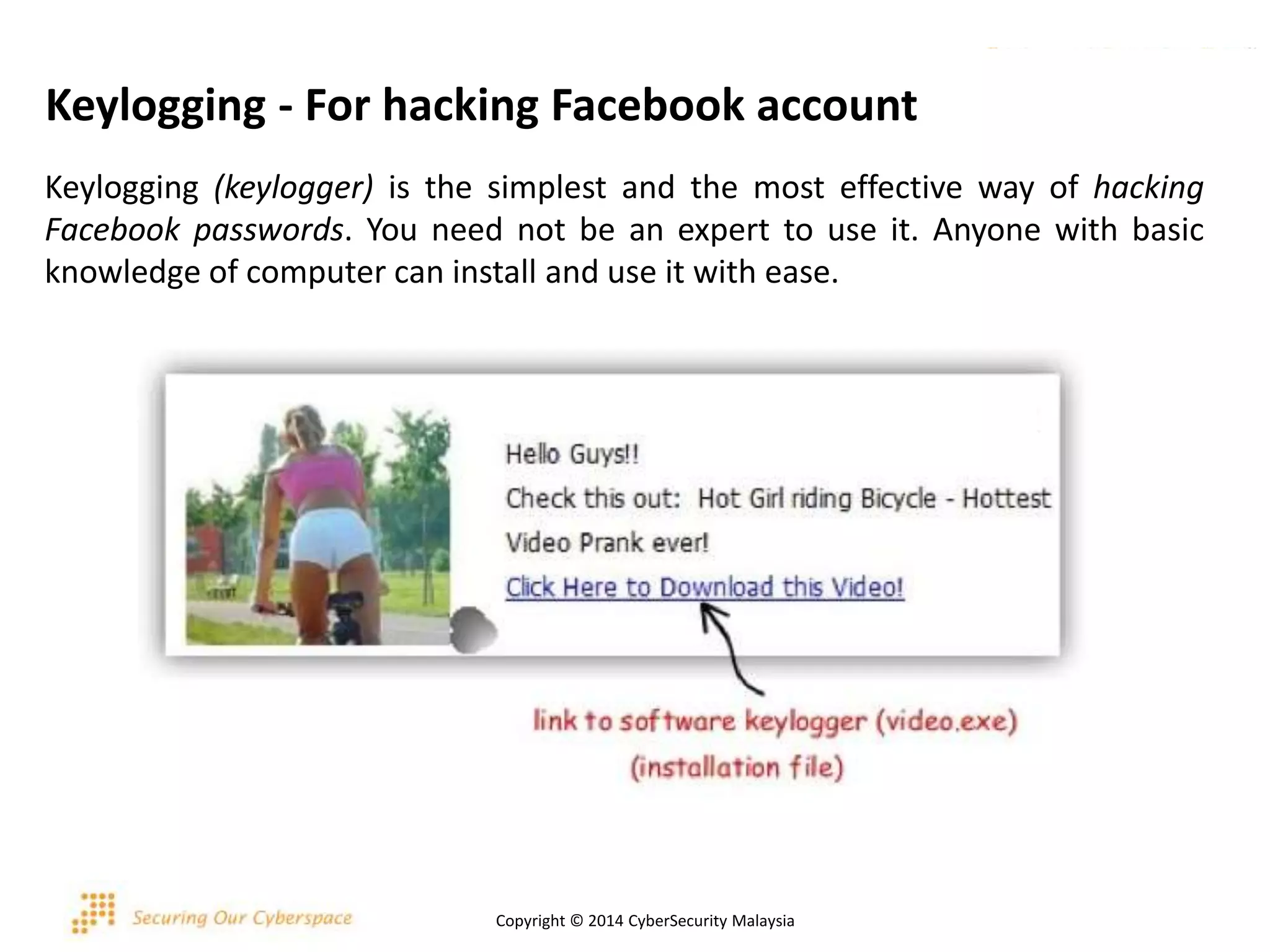
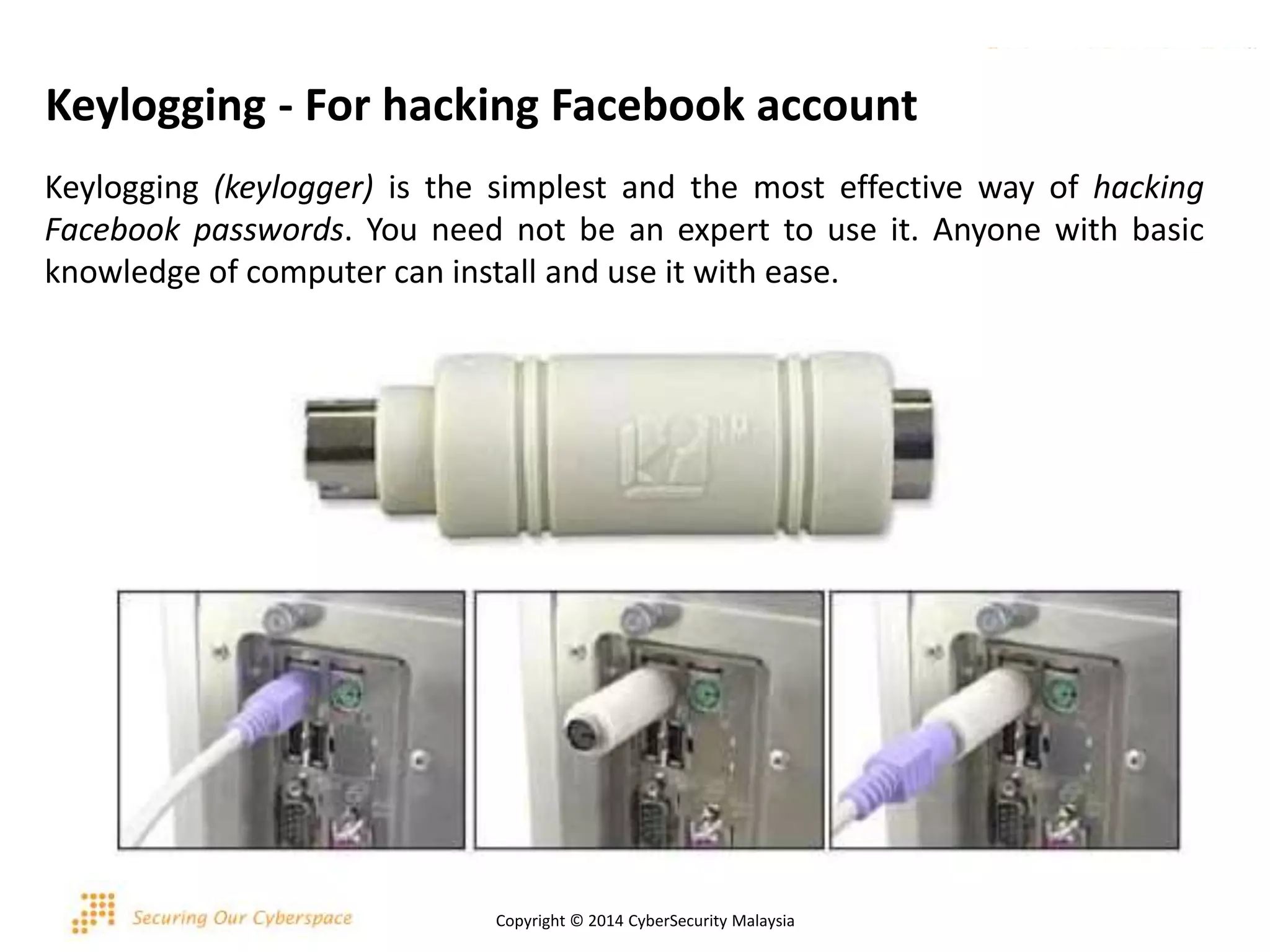
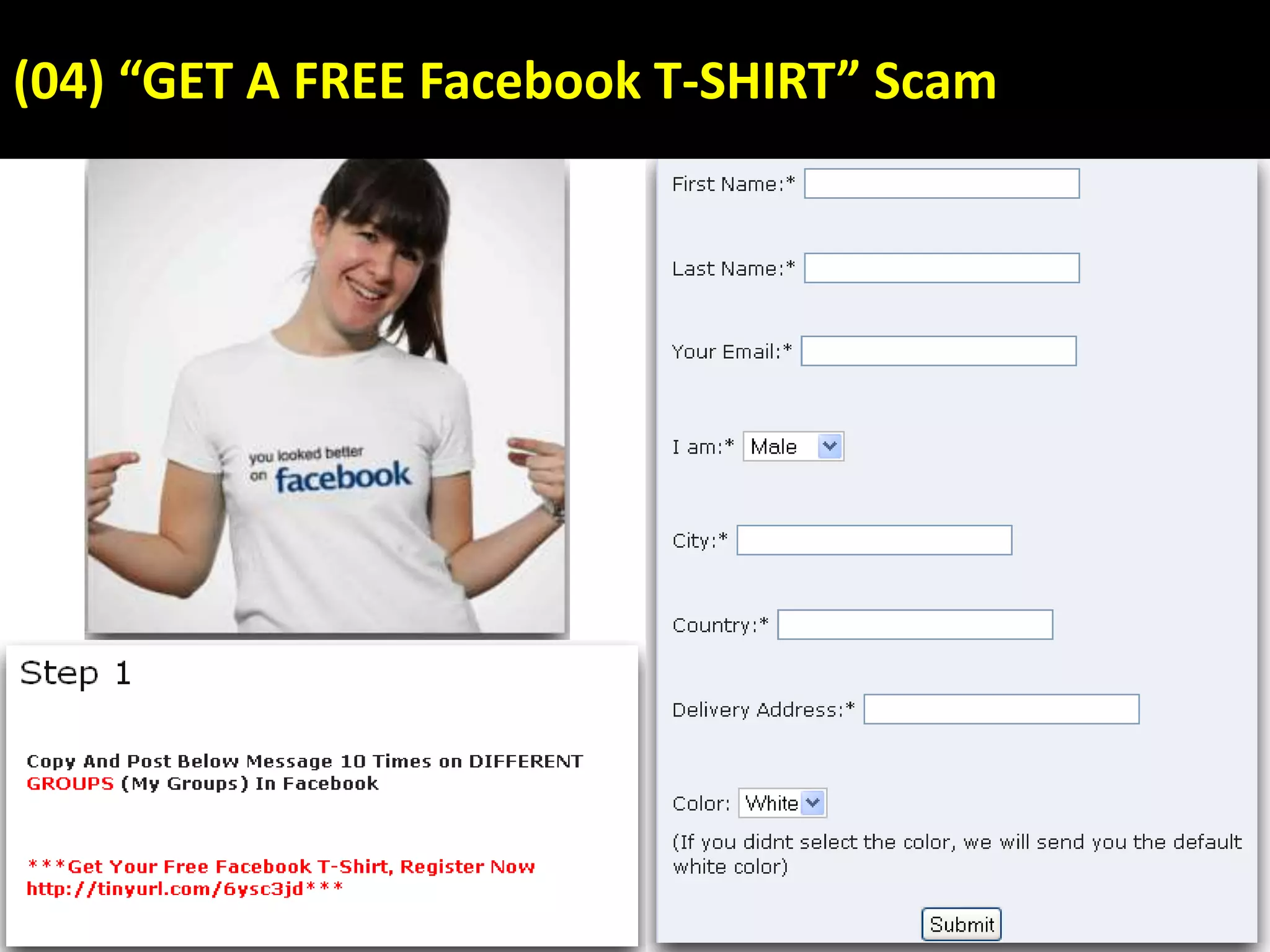
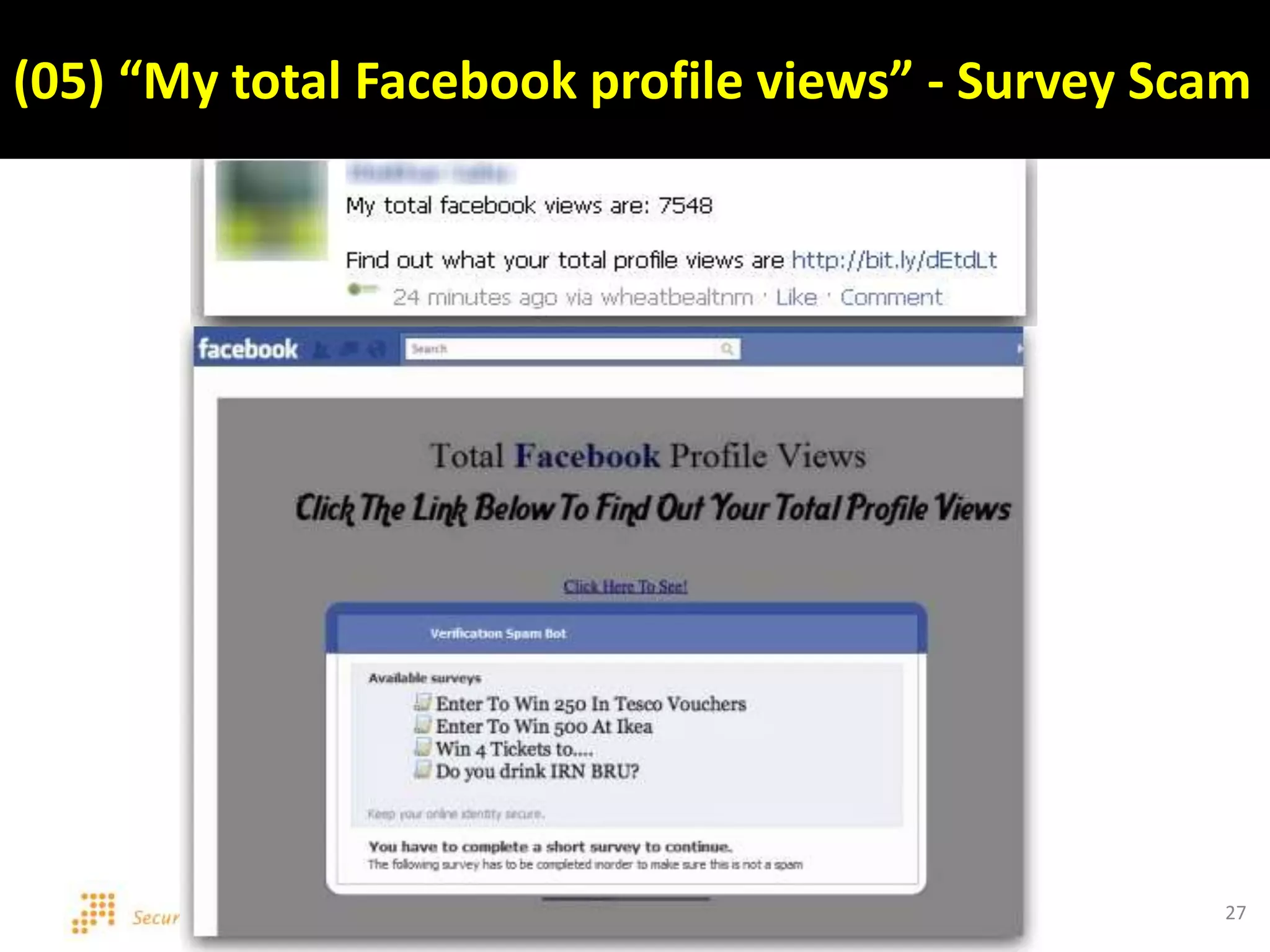
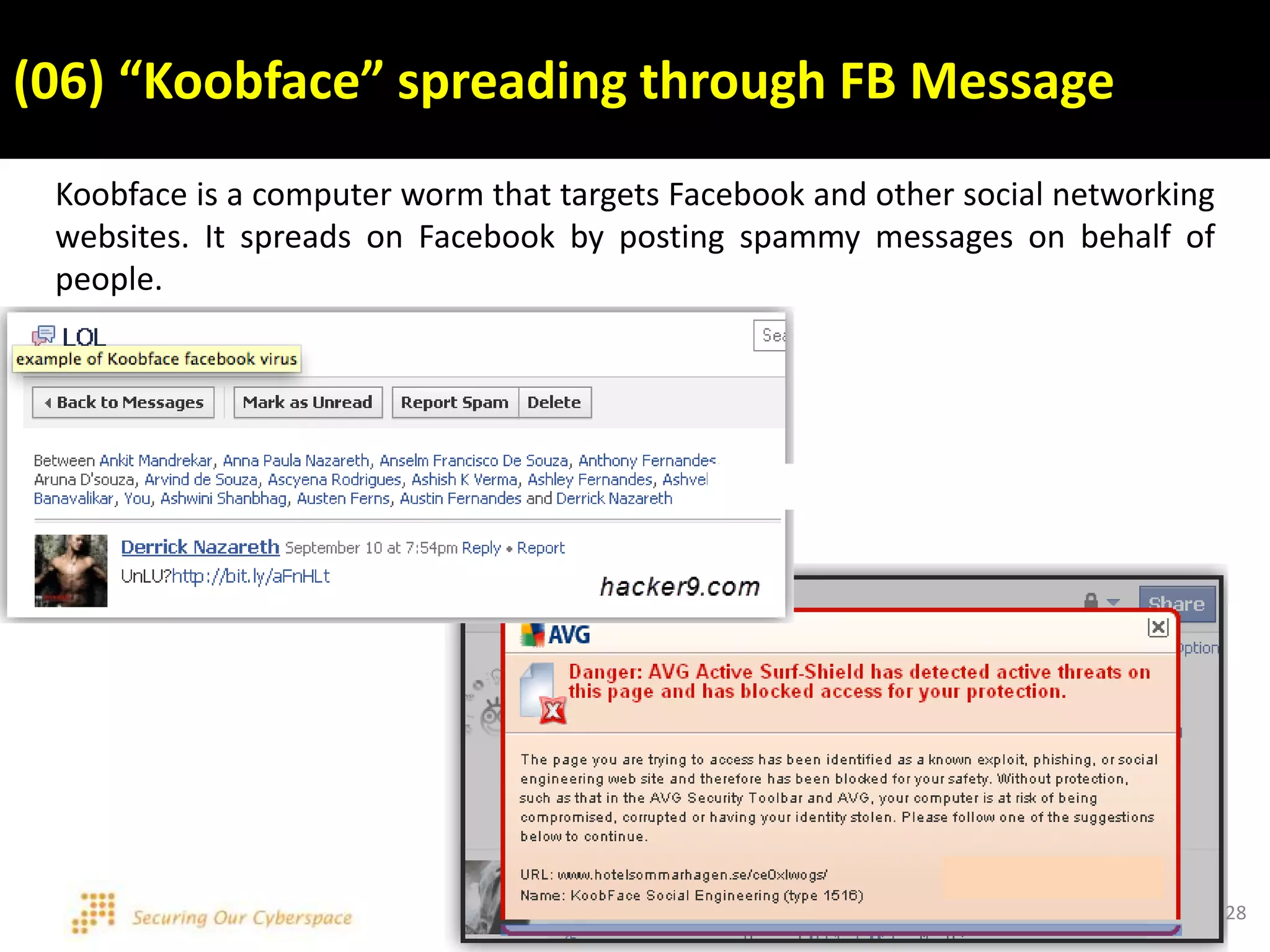
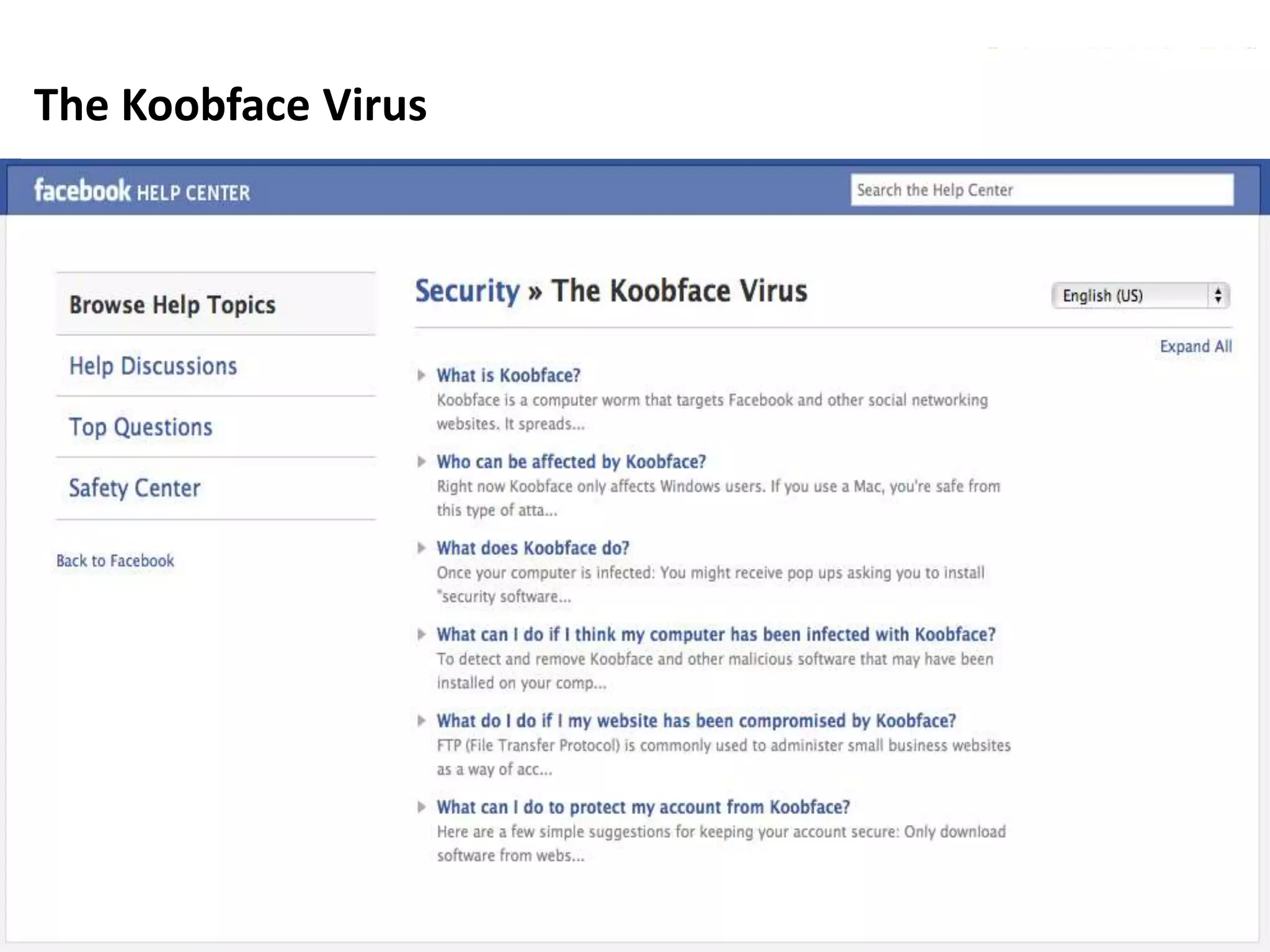
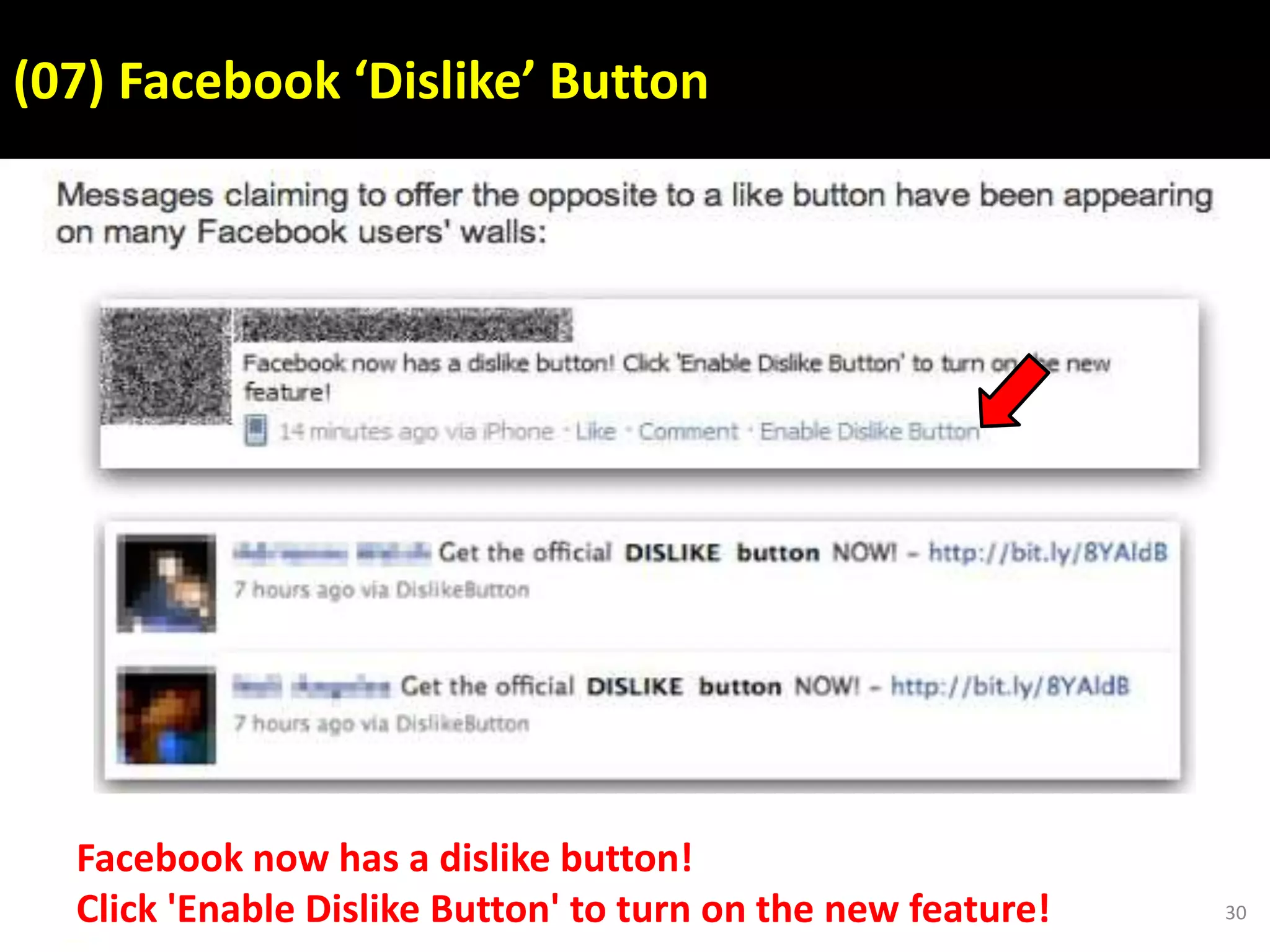
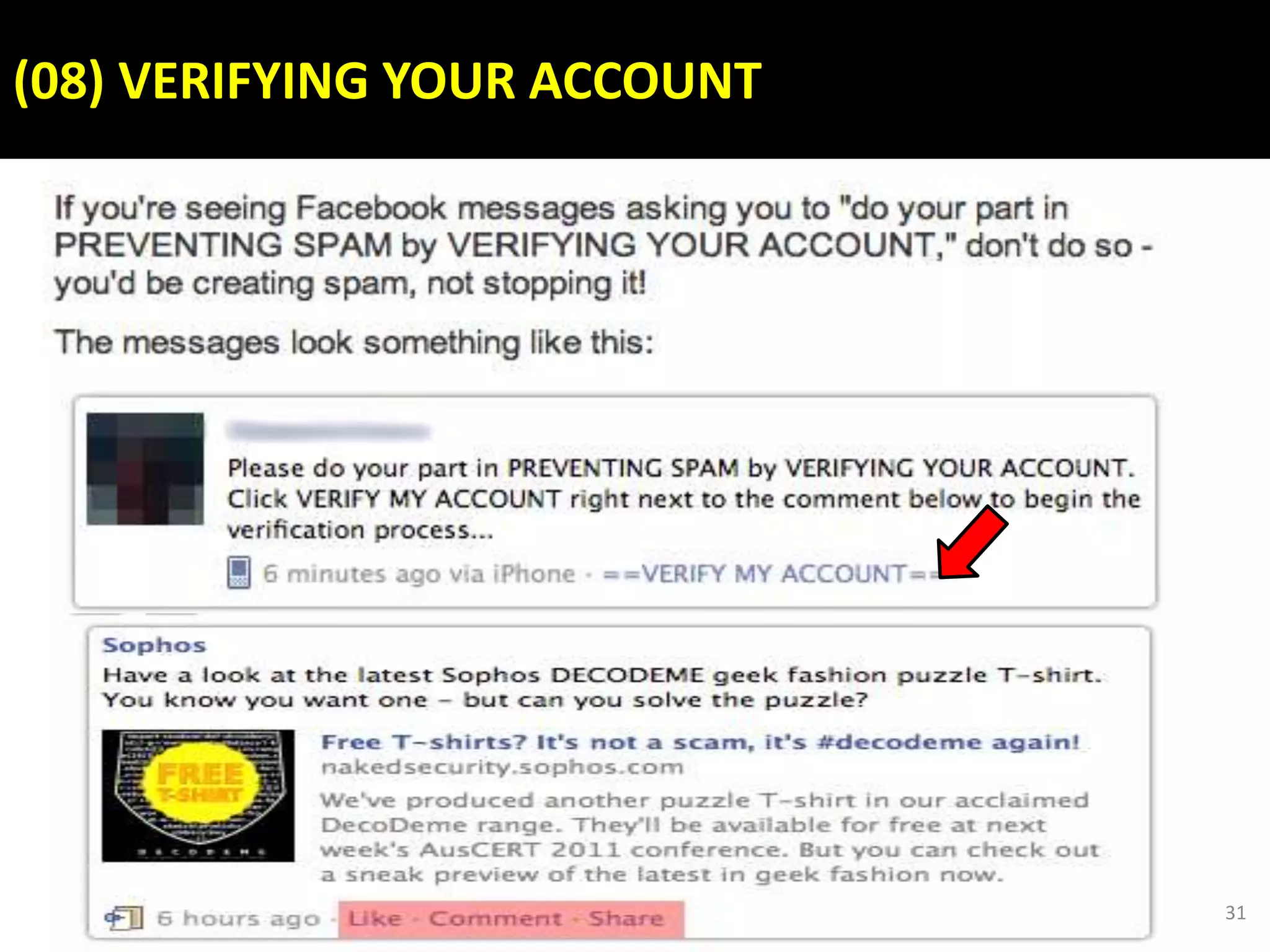
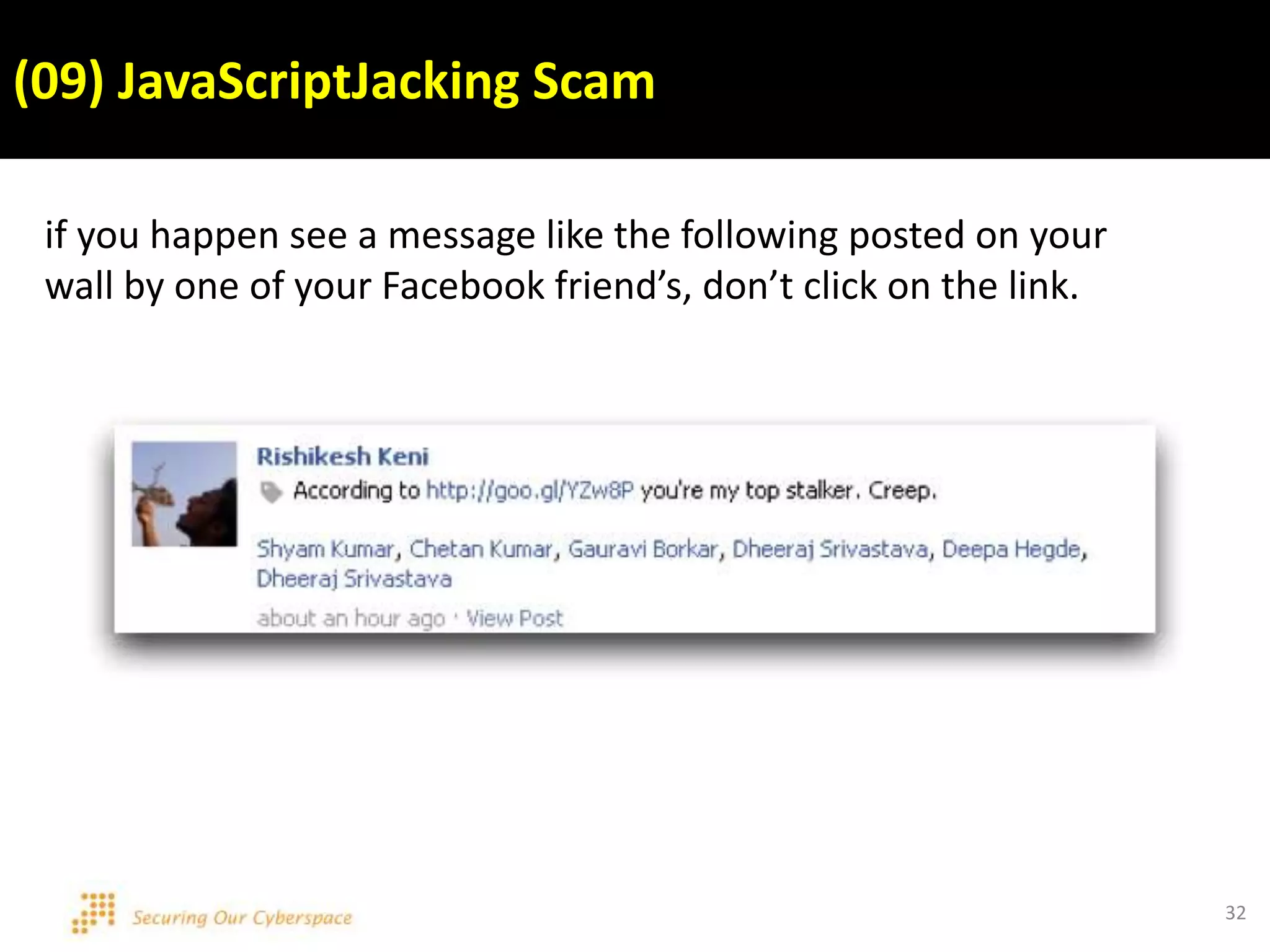
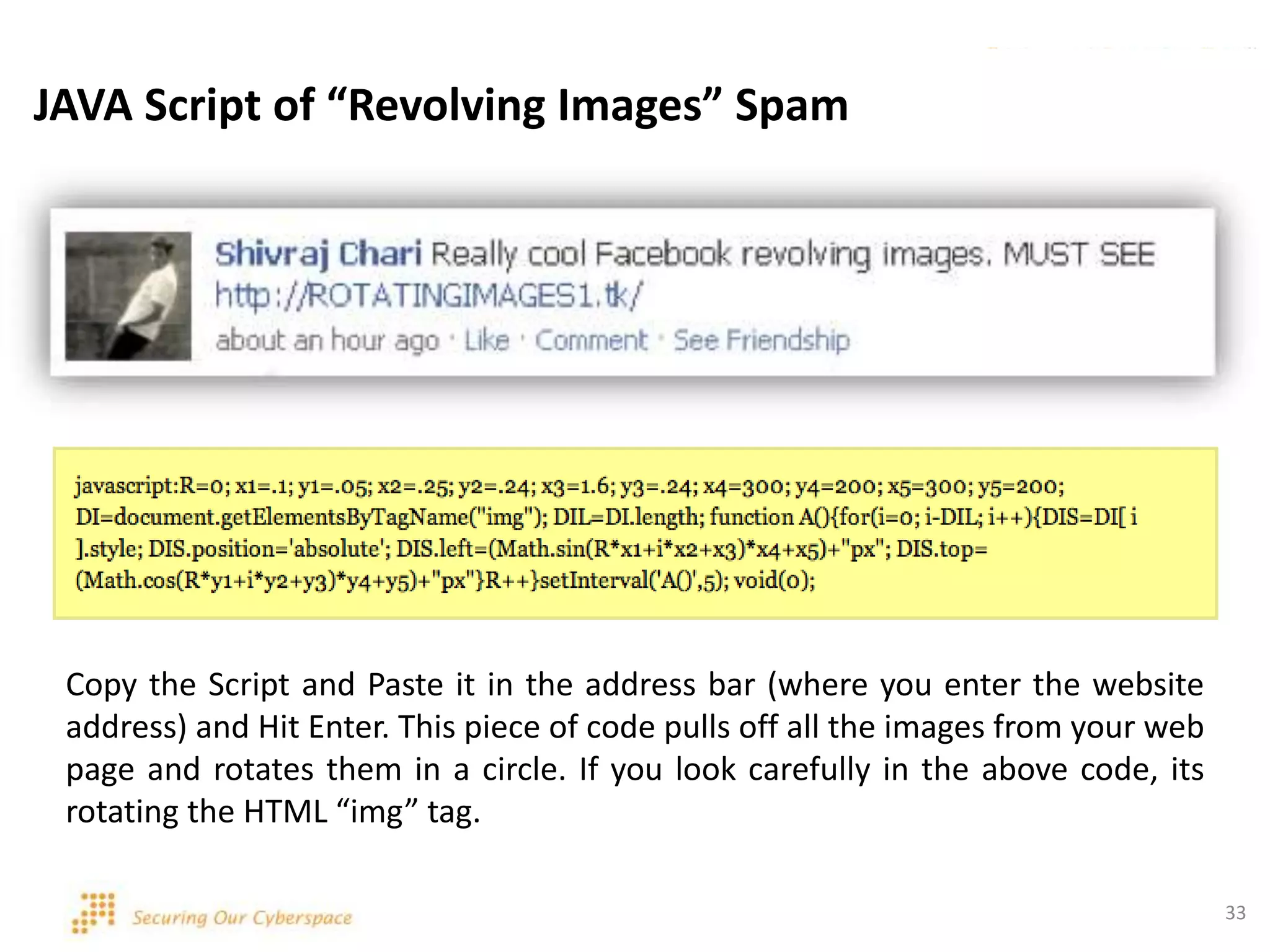
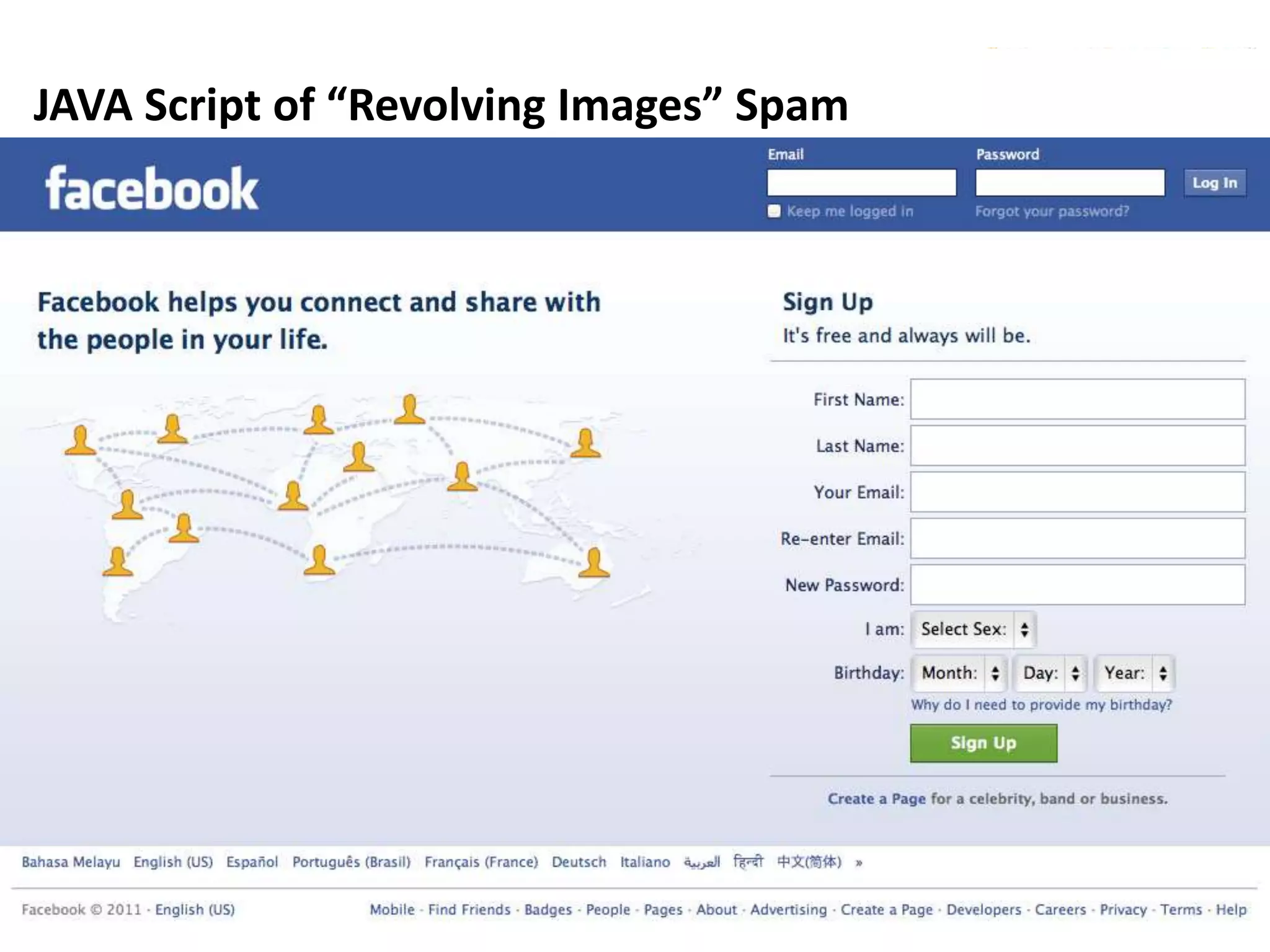
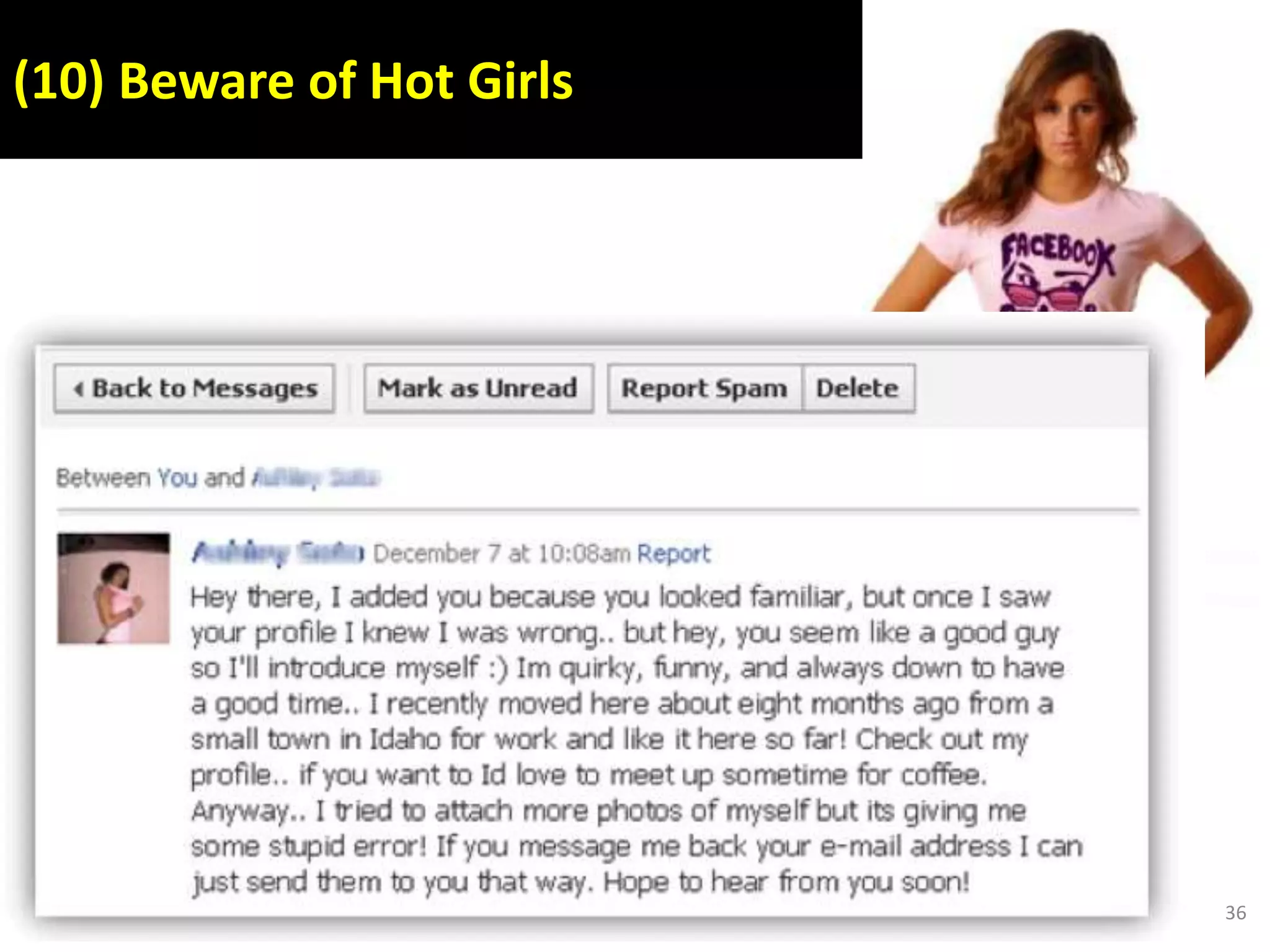
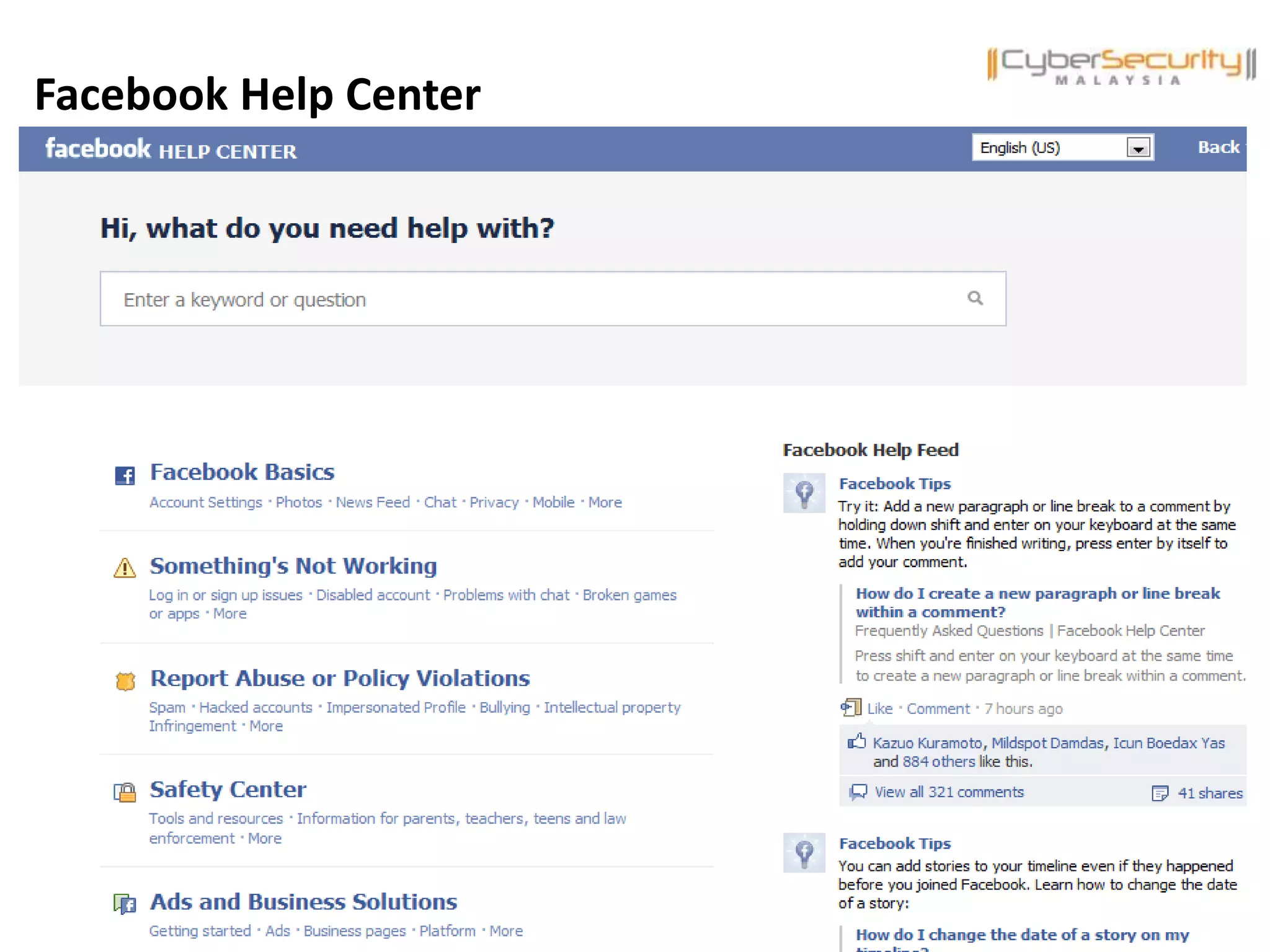
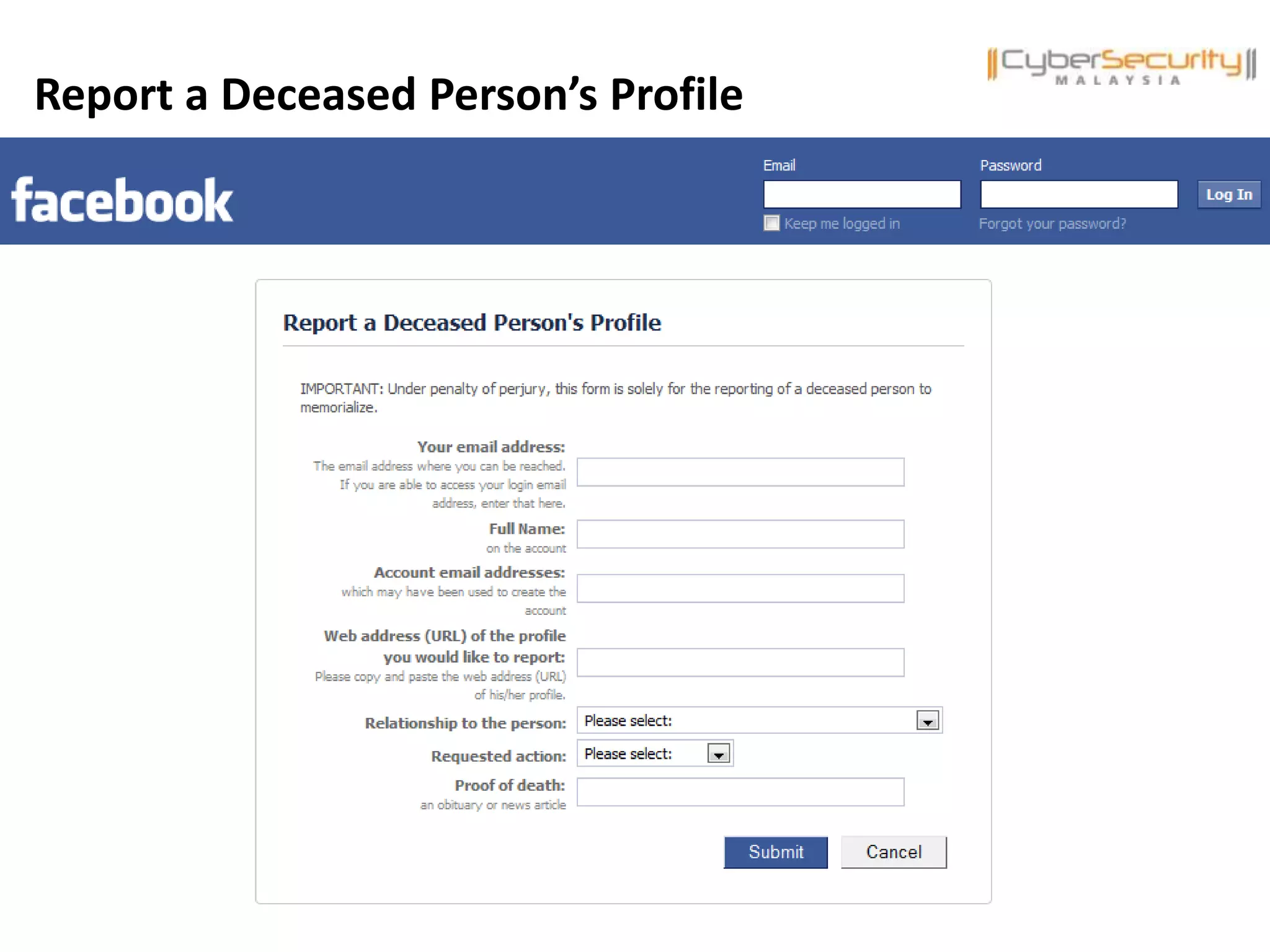
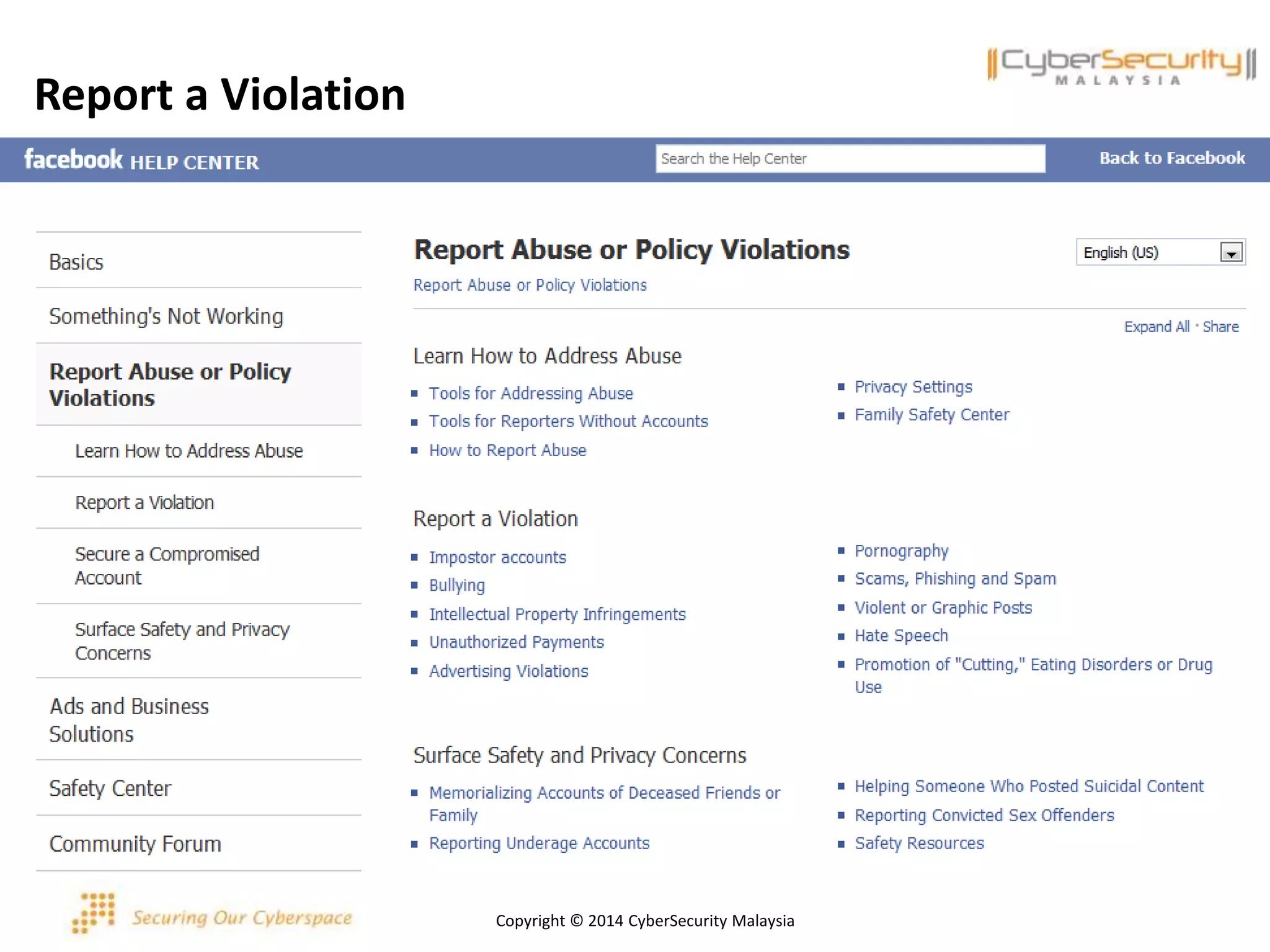
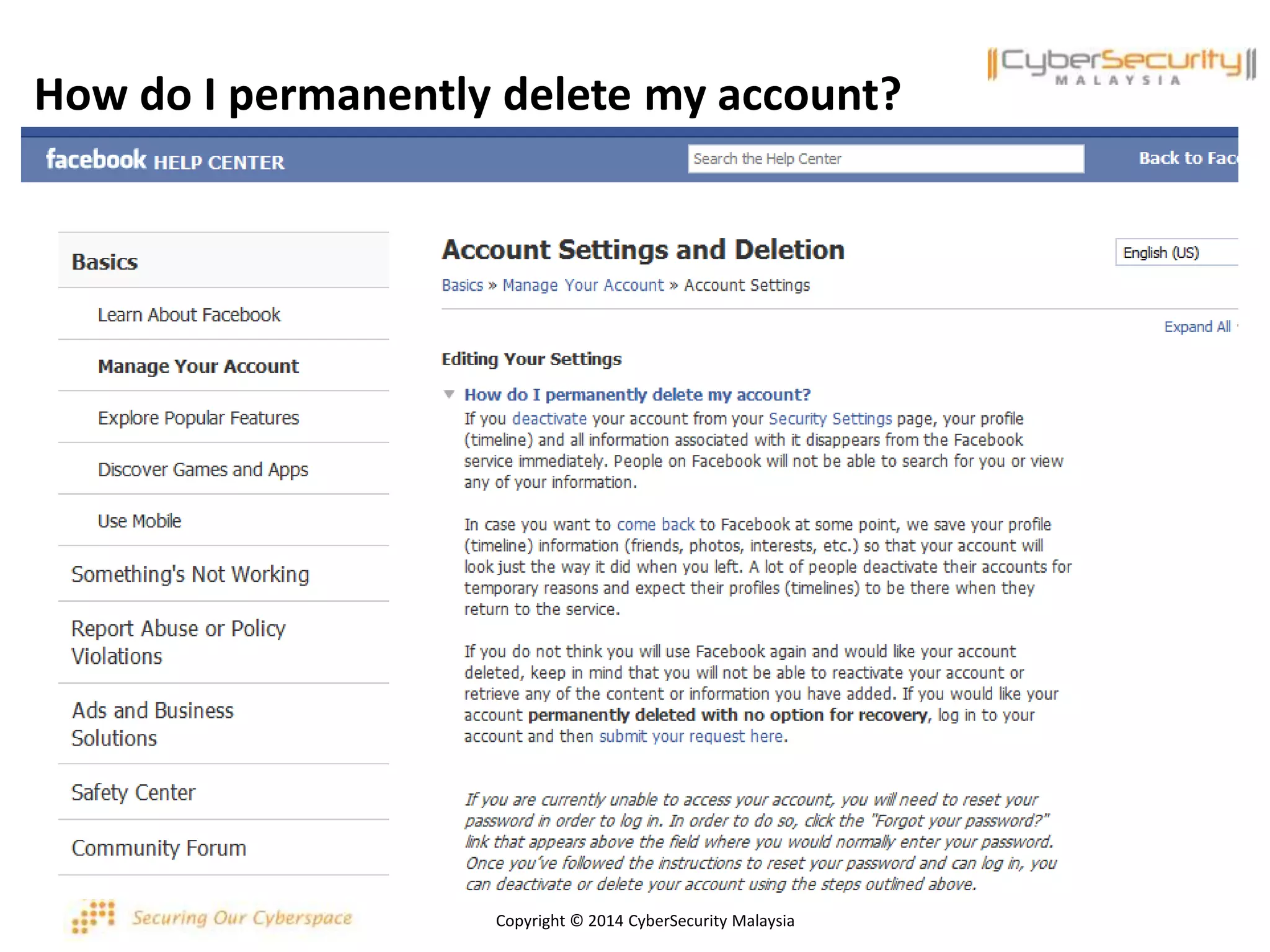
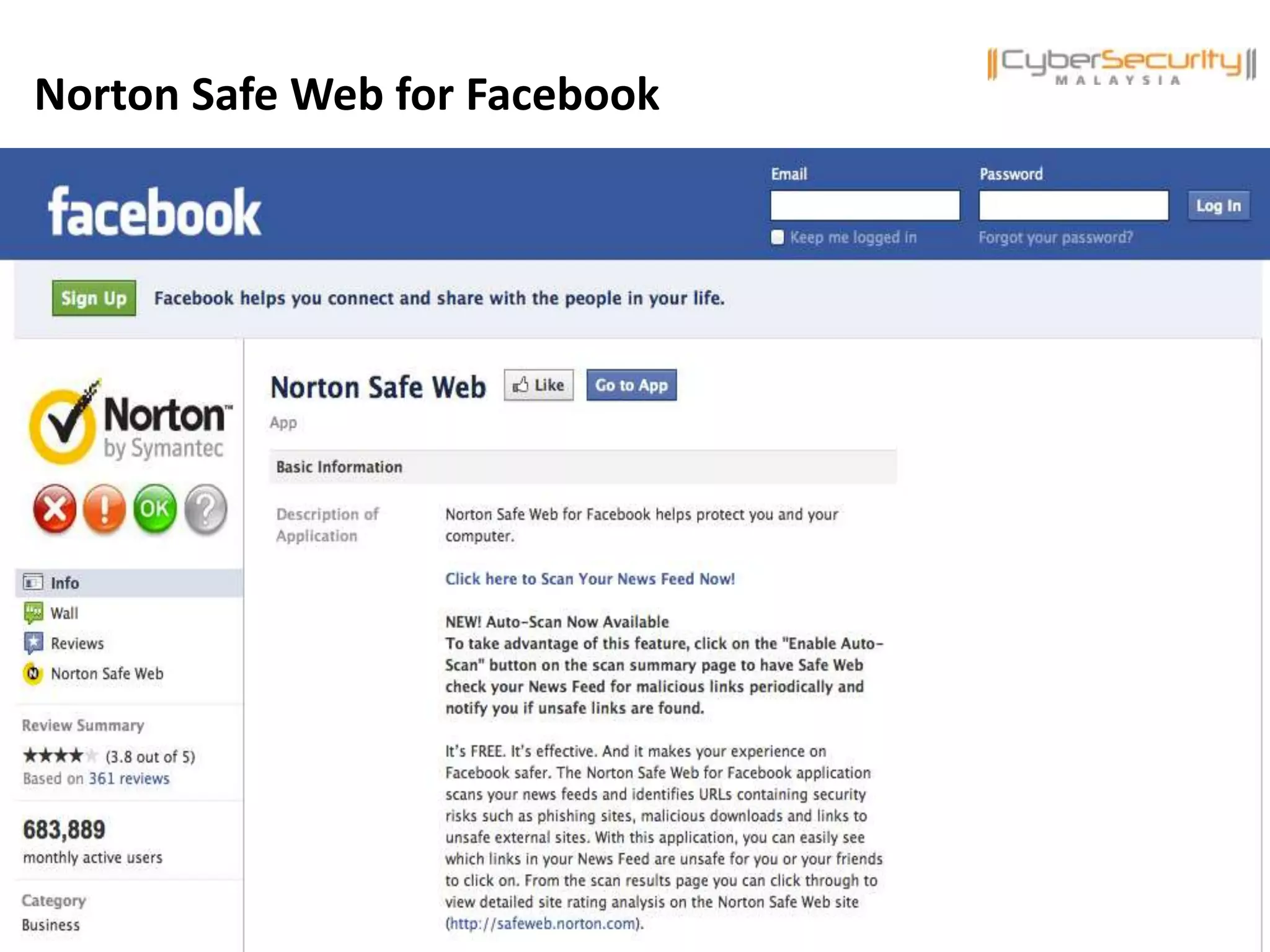
This document discusses various security issues related to using Facebook including privacy settings, potential scams, and tools to enhance security. It provides information on common scams like fake antivirus software, surveys asking for personal information, messages pretending to be from friends containing malicious links, and hoaxes about features that don't exist. It also gives details on keylogging software used to steal Facebook passwords and viruses that can spread through Facebook messages. Finally, it lists some Facebook pages and tools for reporting issues and staying safe online.