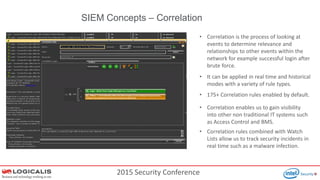
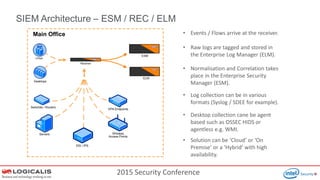
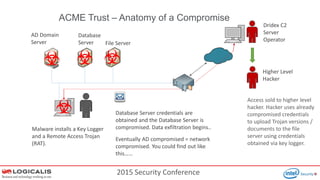
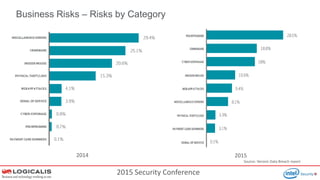
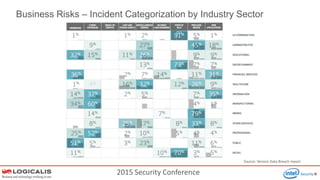
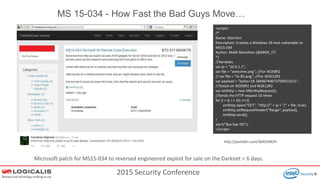
The document presents insights from a 2015 security conference focused on Security Information and Event Management (SIEM), highlighting the speaker's expertise in penetration testing and managed SIEM services for various clients. Key topics include the importance of SIEM for real-time threat visibility, compliance requirements, and the analysis of business risks associated with malware like Dridex. The document also outlines the architecture and features of SIEM solutions, emphasizing the need for efficient incident management and response strategies in cybersecurity.






![2015 Security Conference
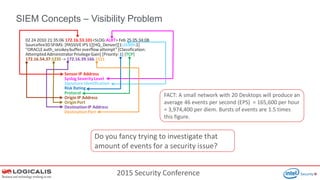
SIEM Concepts – Anatomy of an Event / Flow Life
Raw Logs / Flows
<164>Apr 15 2015 10:04:53:
%ASA-4-106023: Deny tcp src
InsideLAN:192.168.4.35/50381 dst
Outside:216.41.215.186/80 by
access-group "inside_in" [0x0, 0x0]
Raw Logs stored and forensically
tagged.
Raw logs are normalised.
Log Processed by Correlation
Engine
Raw logs stored in raw format.
Security Alert !!
• Events come from devices
such as workstations,
routers , AD servers and
security devices.
• Flows come from flow
collectors or flow
enabled devices such as
firewalls.
• Lots of different flow types
supported such as Netflow /
Qflow.
• Lots of different device
types and logging options.
Normalisation = the process of
getting different record formats
from different devices into a
common format.
SIEM solutions are sized by
capacity in term of Events Per
Second (EPS) primarily.](https://image.slidesharecdn.com/pd-siem-security-conference-160129141647/85/Logicalis-Security-Conference-12-320.jpg)