The document discusses various code vulnerabilities related to TOCTOU (time-of-check to time-of-use) injections and their implications in security. It covers real-world cases, injection techniques, buffer overflows, return-oriented programming (ROP), and various mitigations against these attacks, including safe functions, ASLR, and control flow integrity. The document also addresses definitions and classifications of these vulnerabilities to provide a comprehensive understanding of the security challenges they pose.




















![TOCTOU Injection Conclusion
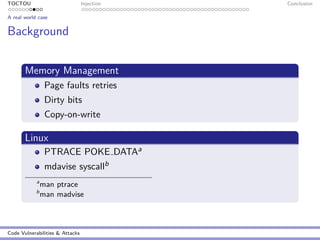
Buffer Overflow
Vulnerable code
Listing 1: Vulnerable code
i n t main ( i n t argc , char ∗ argv [ ] )
{
char s t r [ 3 2 ] ;
s t r c p y ( str , argv [ 1 ] ) ;
r e t u r n 0;
}
Code Vulnerabilities & Attacks](https://image.slidesharecdn.com/attacks-190810045646/85/Code-Vulnerabilities-Attacks-22-320.jpg)


![TOCTOU Injection Conclusion
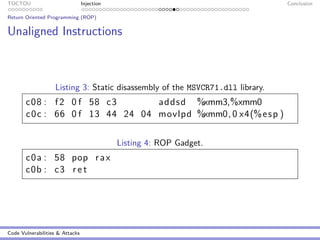
Buffer Overflow
Still overflowing
Listing 2: variable overflow
i n t main ( i n t argc , char ∗ argv [ ] )
{
i n t a = 10;
char s t r [ 3 2 ] ;
scanf (”%s ” , s t r ) :
p r i n t f (”%dn ” , a ) ;
r e t u r n 0;
}
Code Vulnerabilities & Attacks](https://image.slidesharecdn.com/attacks-190810045646/85/Code-Vulnerabilities-Attacks-25-320.jpg)
















![TOCTOU Injection Conclusion
Mitigations
Safe functions/languages
Listing 7: String definition example
typedef s t r u c t s t r {
char s t r [MAX] ;
u i n t s i z e ;
u i n t max=MAX;
} s t r i n g ;
Listing 8: Concat implementation example
concat ( str1 , s t r 2 )
i f str1 −>s i z e + str2 −>s i z e < str1 −>max
Code Vulnerabilities & Attacks](https://image.slidesharecdn.com/attacks-190810045646/85/Code-Vulnerabilities-Attacks-43-320.jpg)

















