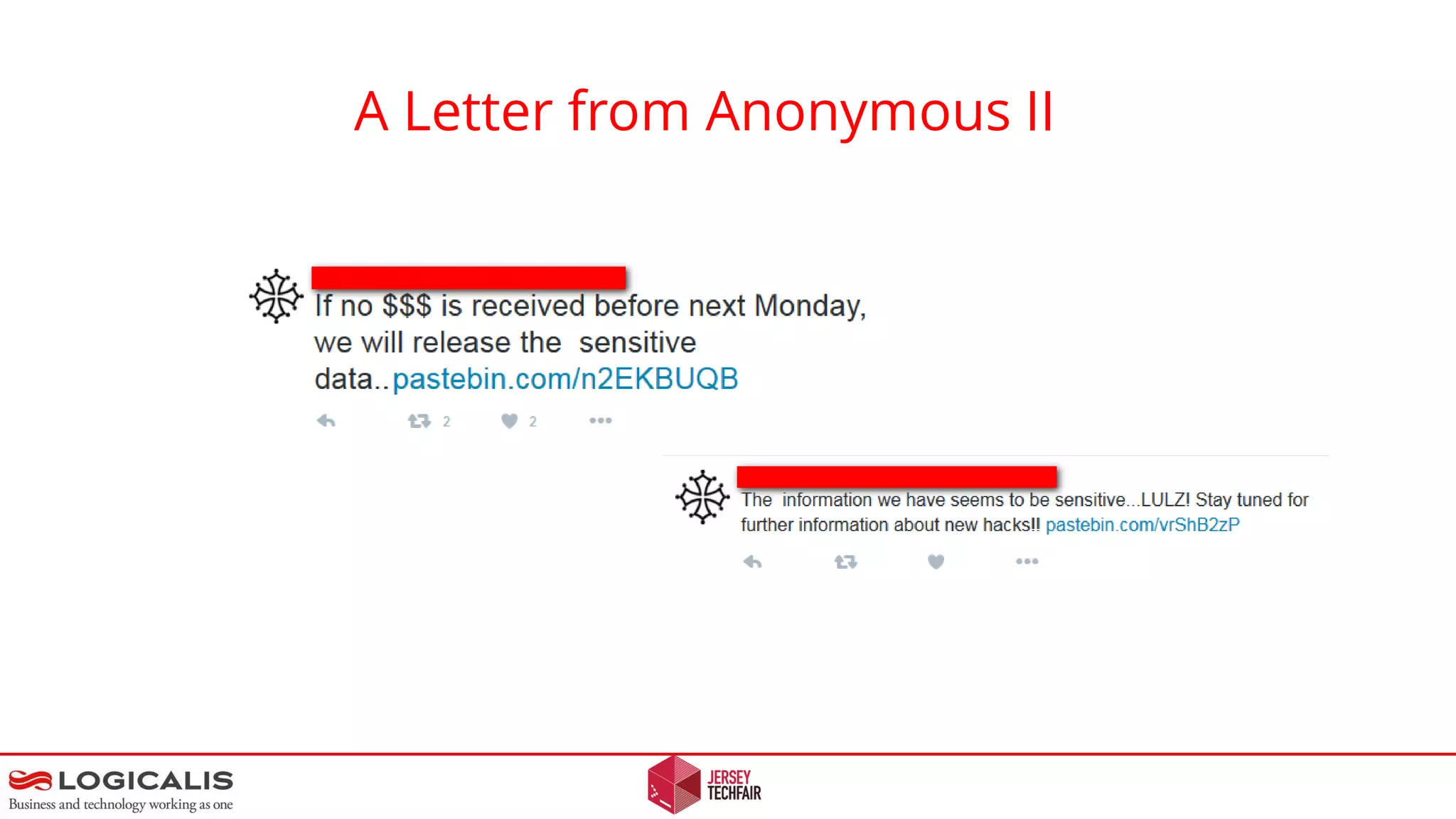
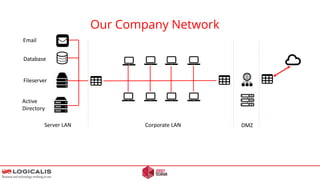
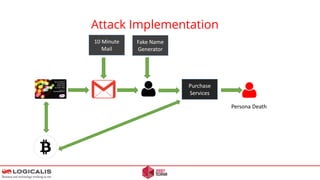
An anonymous letter discusses a hypothetical ransomware attack on a professional services company. The letter outlines how attackers could compromise the target's network through a phishing email containing malware. This initial access could allow the attackers to laterally move within the network and exploit other systems to exfiltrate confidential data. The letter warns that paying the ransom demand does not guarantee the stolen data will not be leaked or that the attackers won't target the company again in the future. It concludes by questioning how the target would respond to such an attack and emphasizes that proper security measures are needed to prevent network compromise.
![Disclaimer
[1] Some of the topics discussed / demonstrated are criminal in nature
[2] “Don’t try this at home unless you want to go to jail. You have been warned,
I am not responsible for your actions.”
[3] You will gain more from the lecture if you participate at times.
[4] Any likeness to real people or organisations does not imply anything about
security
[5] Questions at the end please…](https://image.slidesharecdn.com/letter-anonymous-ii-novideo-160129140230/85/Letter-anonymous-II-2-320.jpg)
![Our Topic
[1] What if you received a Cyber ransom / extortion threat?
[2] What would be your response?
[3] How would the attackers evade capture?
[4] How might you be attacked / compromised ?
[5] This will be focused from a professional services company point of view
e.g. Doctors, Lawyers, Accountants and Telco’s where confidentiality is
paramount.](https://image.slidesharecdn.com/letter-anonymous-ii-novideo-160129140230/85/Letter-anonymous-II-3-320.jpg)


![Hacker Manifesto
[1]
[2]
[3]
[4]
[5]
Unlike other groups out there, we have no interest whatsoever in making any kind of political or social
statement. We are only interested in making money, which brings us to the code of conduct we have put in
place
Communication and/or negotiations between us and our targets is never released, regardless of whether
we get paid or not.
We never discuss or even acknowledge the fact that some of our past targets might have paid us.
We automatically delete all of the stolen data once a full payment has been made.
We never target the same company twice and, for obvious reasons, we always stick with the original requested
amount.
[6]
If we posted the data of a company that has paid us, no other future target would ever agree to pay us. Similarly, asking
for more money once we have already been paid would be pointless as no target would pay a second time out of fear
we might ask for even more money a third time.](https://image.slidesharecdn.com/letter-anonymous-ii-novideo-160129140230/85/Letter-anonymous-II-7-320.jpg)

![Hacker Tradecraft - OPSEC
[1] Never reveal operational details
[2] Never reveal your plans
[3] Never reveal trust anyone
[4] Never confuse recreation / hacking
[5] Never operate from your house
[6] Be proactively paranoid
[7] Keep personnel life / hacking separate
[8] Keep your personnel environment contraband free
[9] Never talk to Police
[10] Don’t Give anyone power over you](https://image.slidesharecdn.com/letter-anonymous-ii-novideo-160129140230/85/Letter-anonymous-II-9-320.jpg)

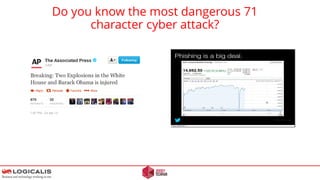
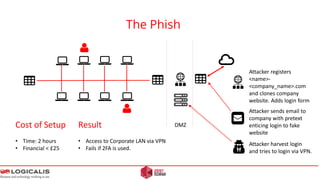

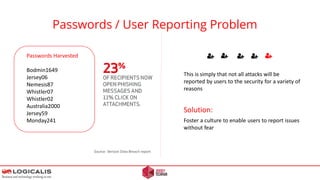
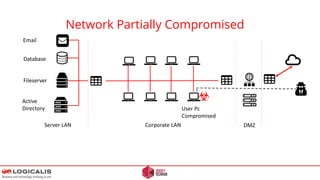
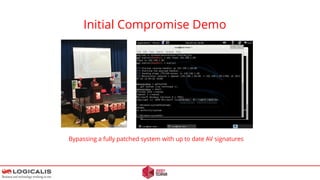

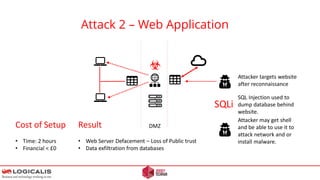
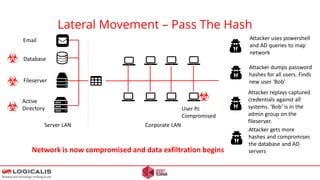


![Final Thoughts - Questions
EU Data Protection Regulations – 2.5 % fine of worldwide turnover for falling to report a breach.
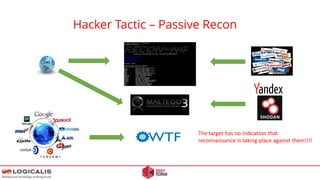
[2] Attackers can stay anonymous. Short time frames make it unlikely that a Police investigation will succeed.
[1]
[3] Once compromised, the game is over.
[4] Test the strength of your counter measures..](https://image.slidesharecdn.com/letter-anonymous-ii-novideo-160129140230/85/Letter-anonymous-II-24-320.jpg)