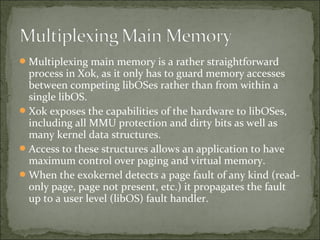
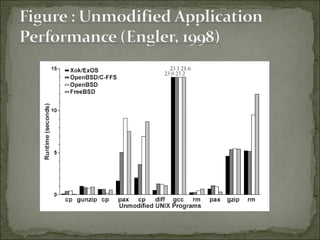
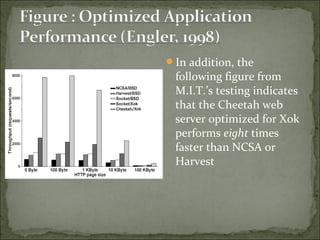
The document discusses the concept and advantages of an exokernel operating system, which allows applications to manage low-level physical resources directly, leading to enhanced performance and flexibility compared to traditional operating systems. It outlines the design principles behind exokernels, such as resource multiplexing, secure bindings, and user-level fault handling, as well as the ongoing research and development efforts at MIT. Additionally, the document addresses both the benefits and challenges of implementing exokernels, particularly in terms of balancing power and protection for applications.