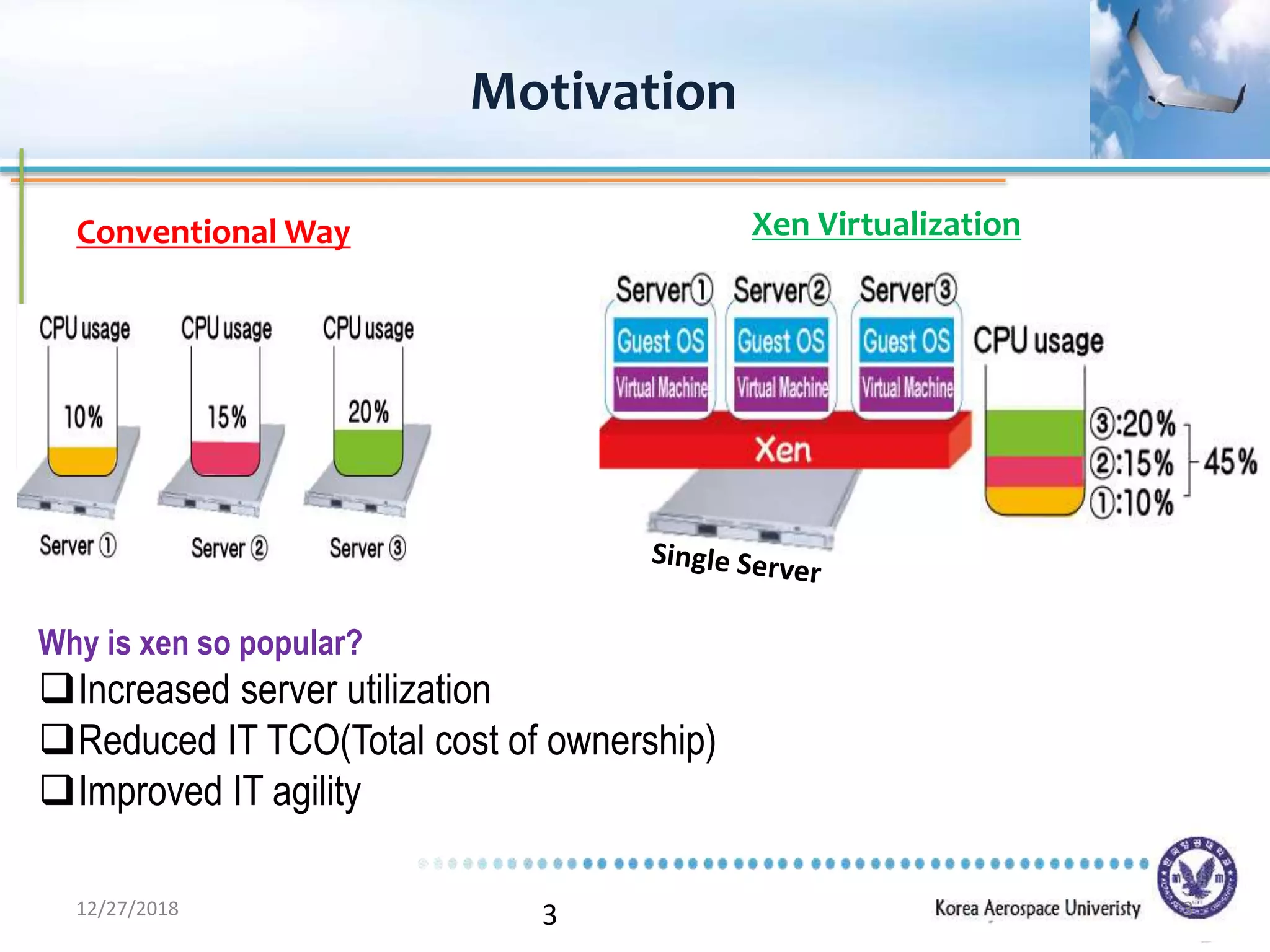
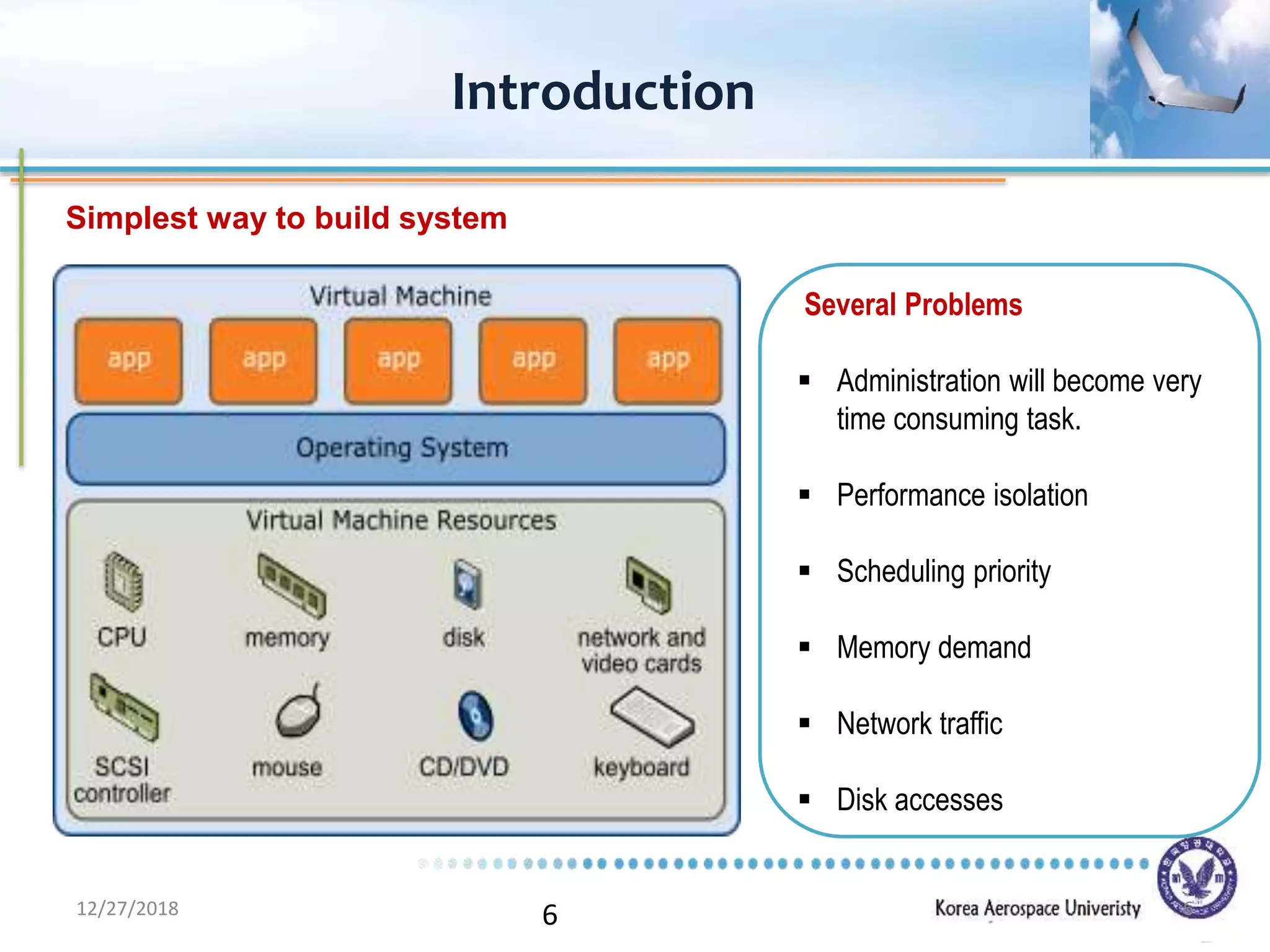
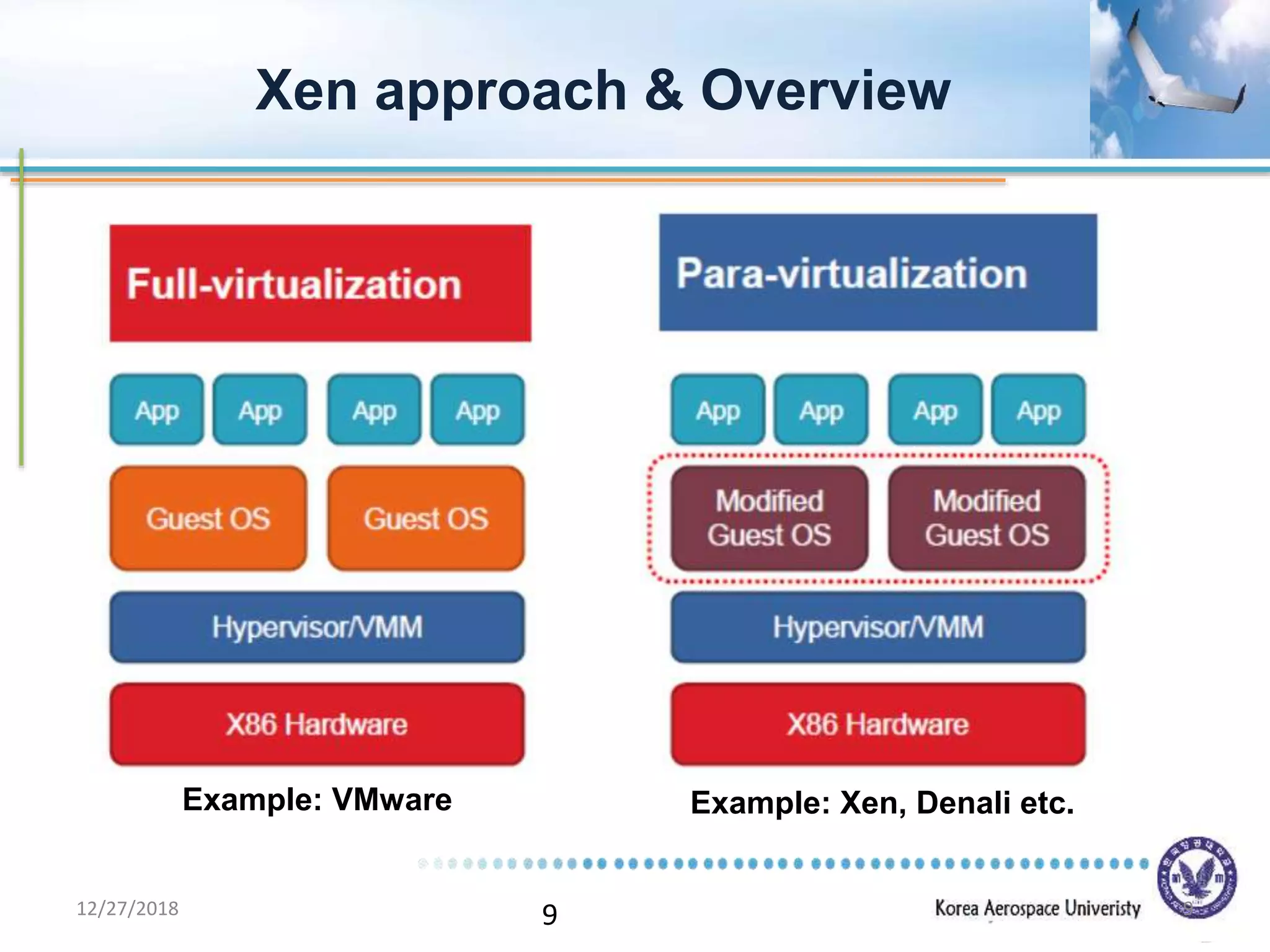
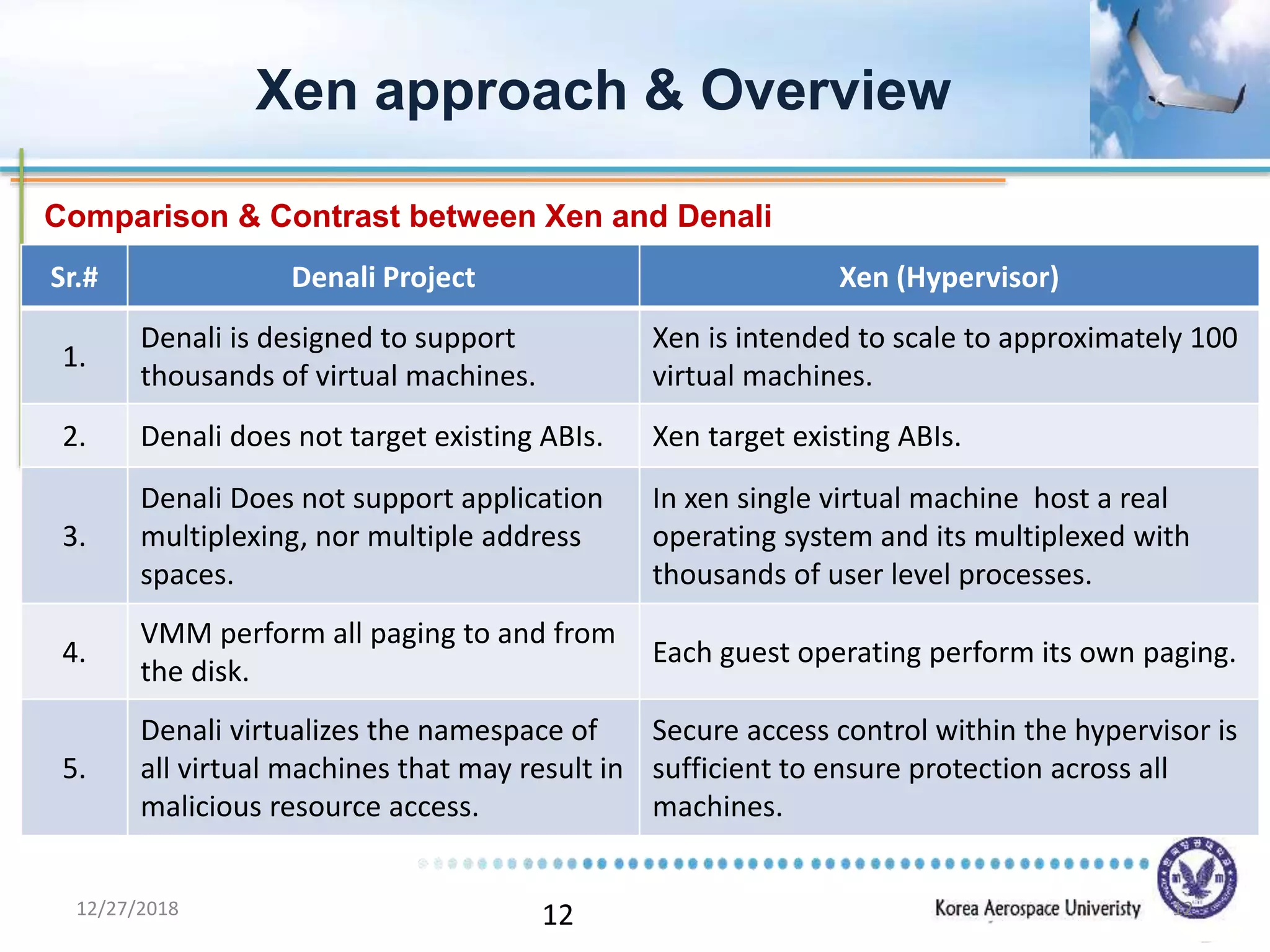
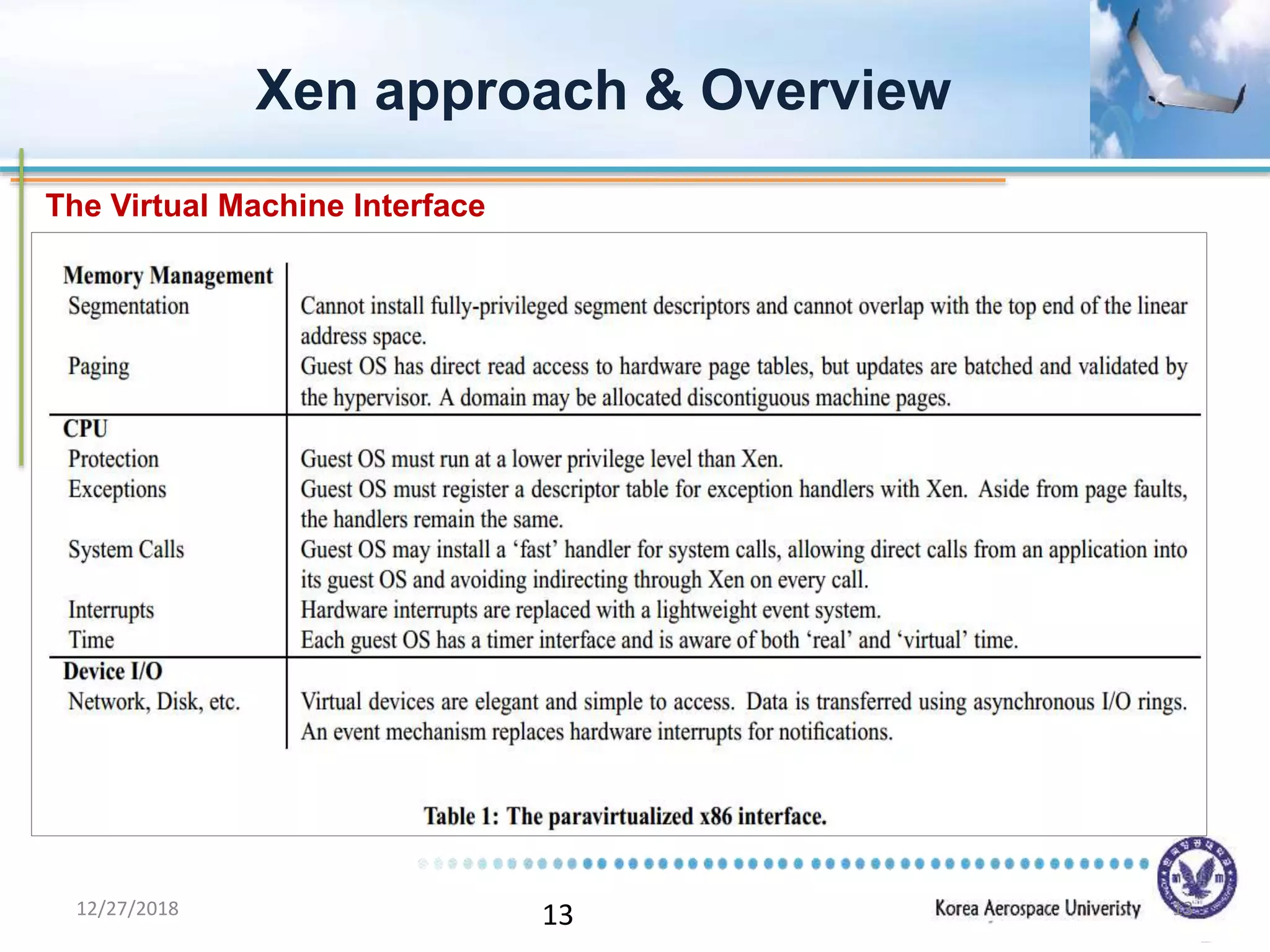
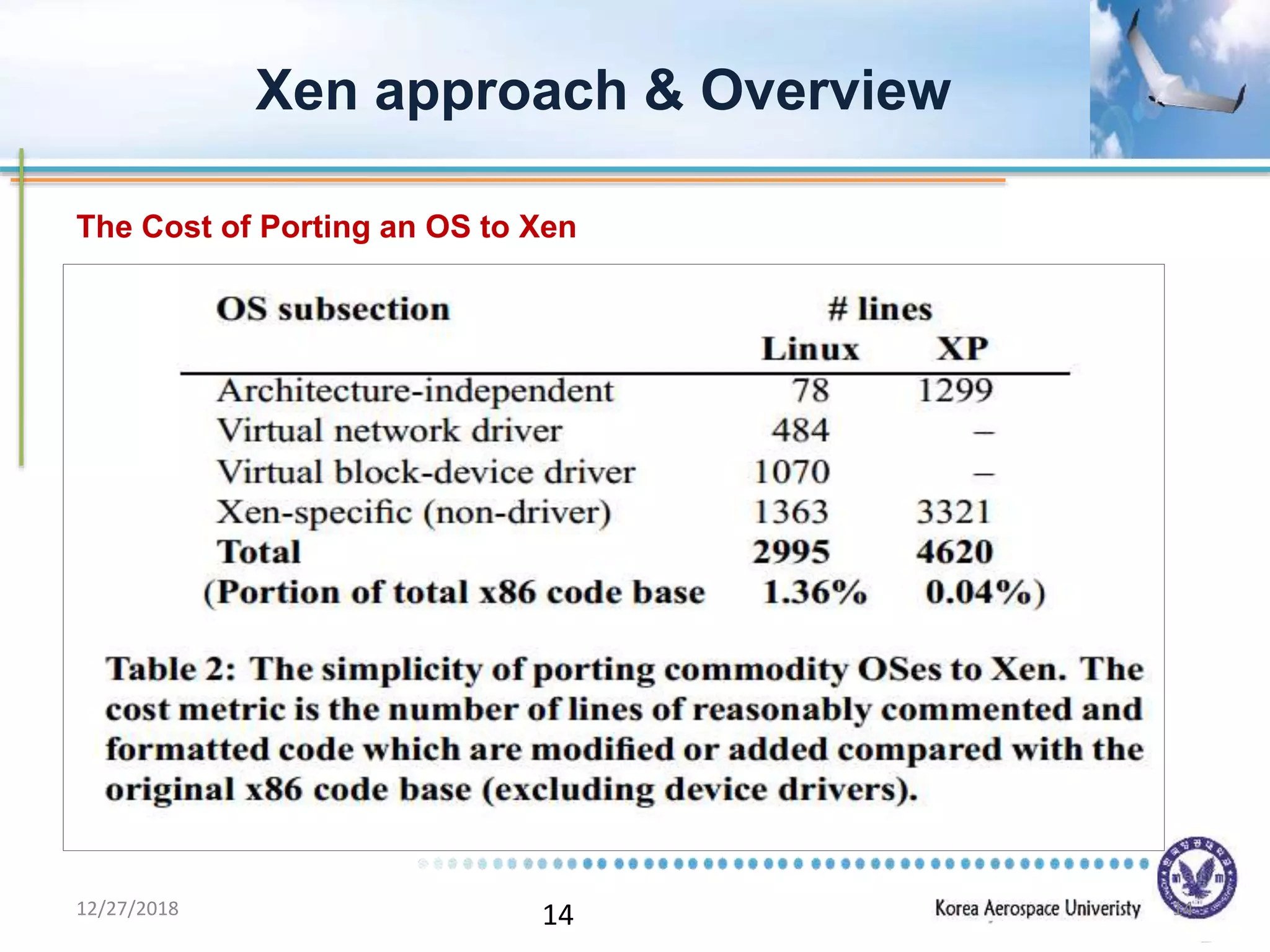
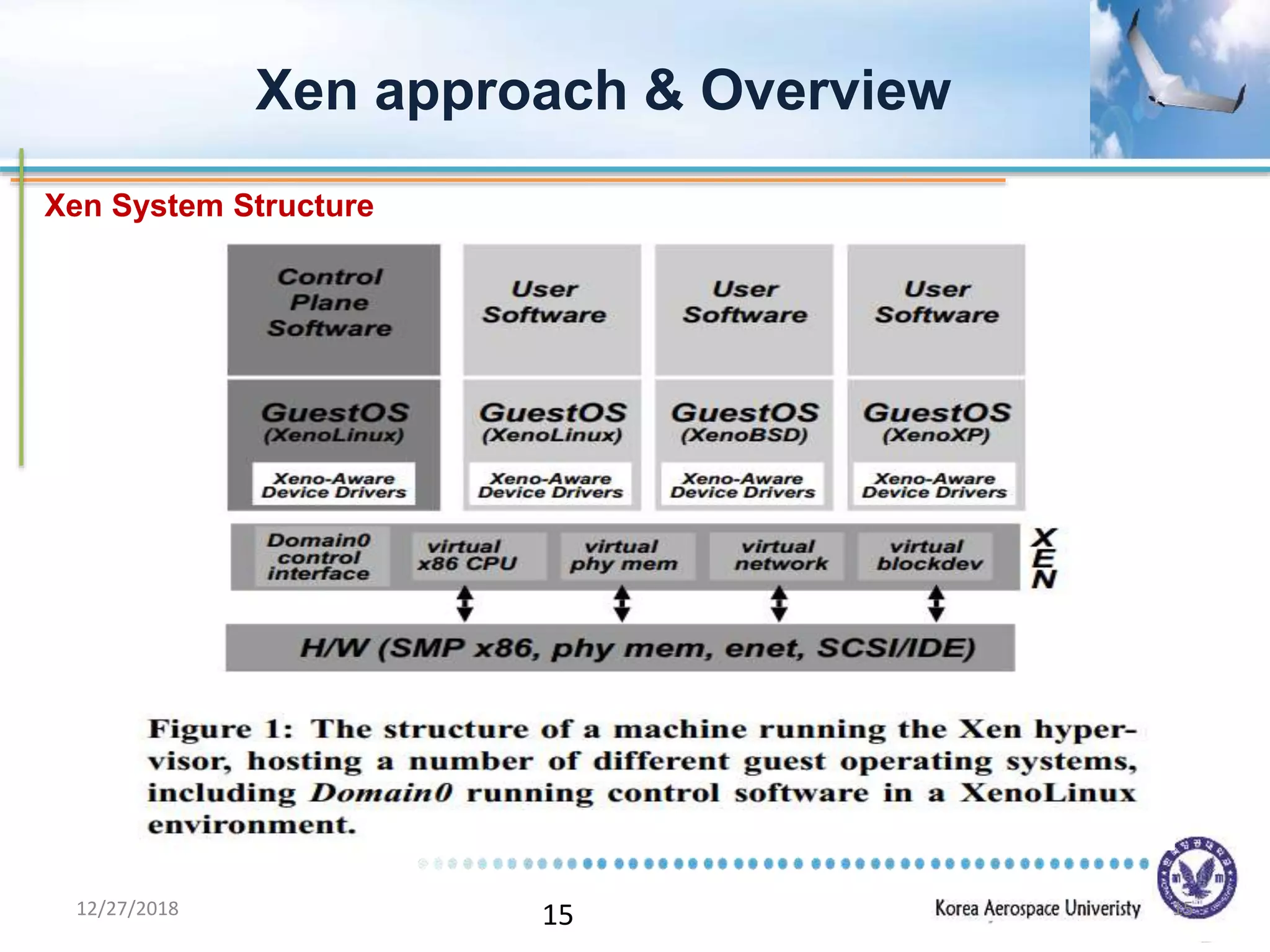
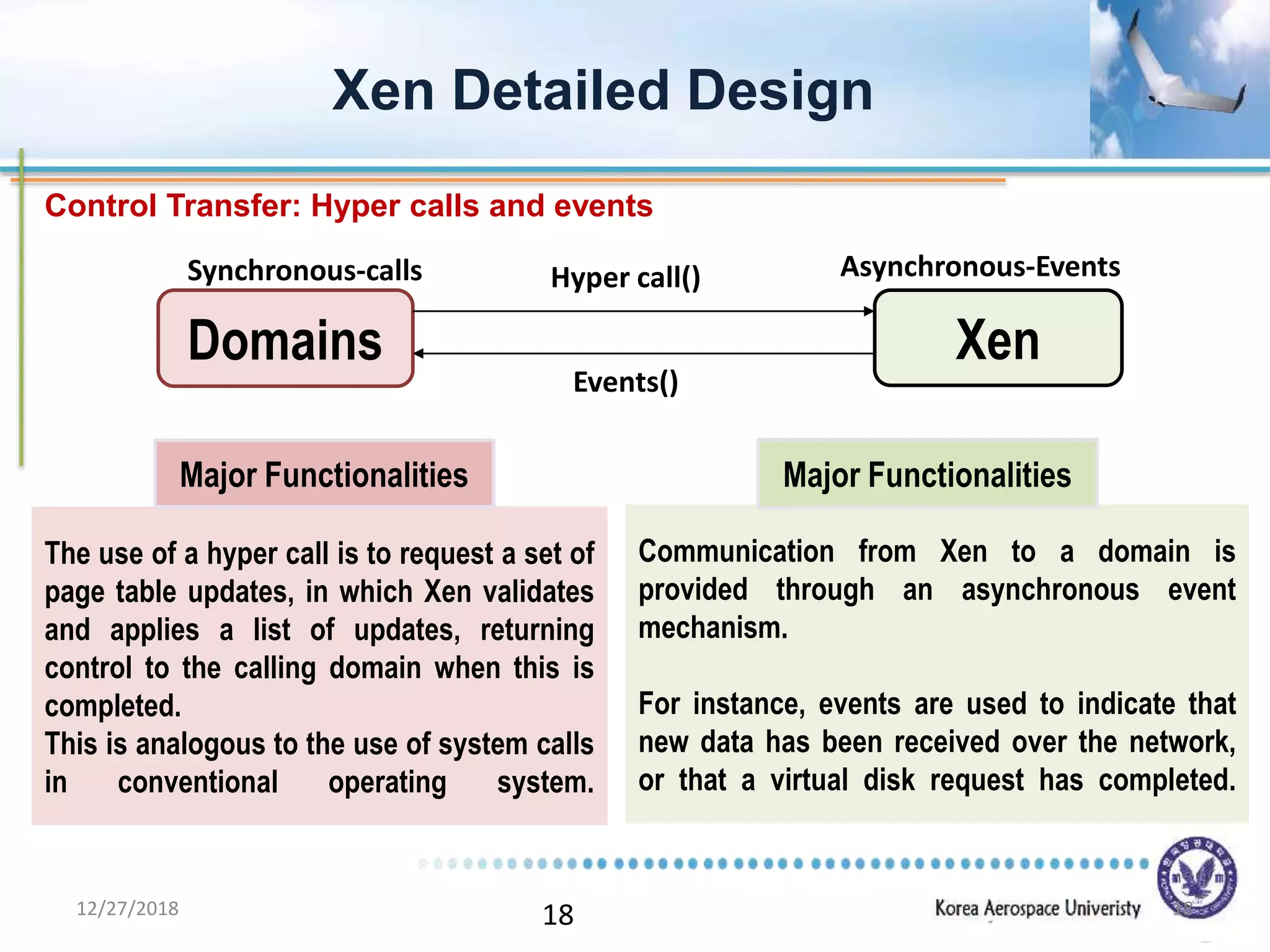
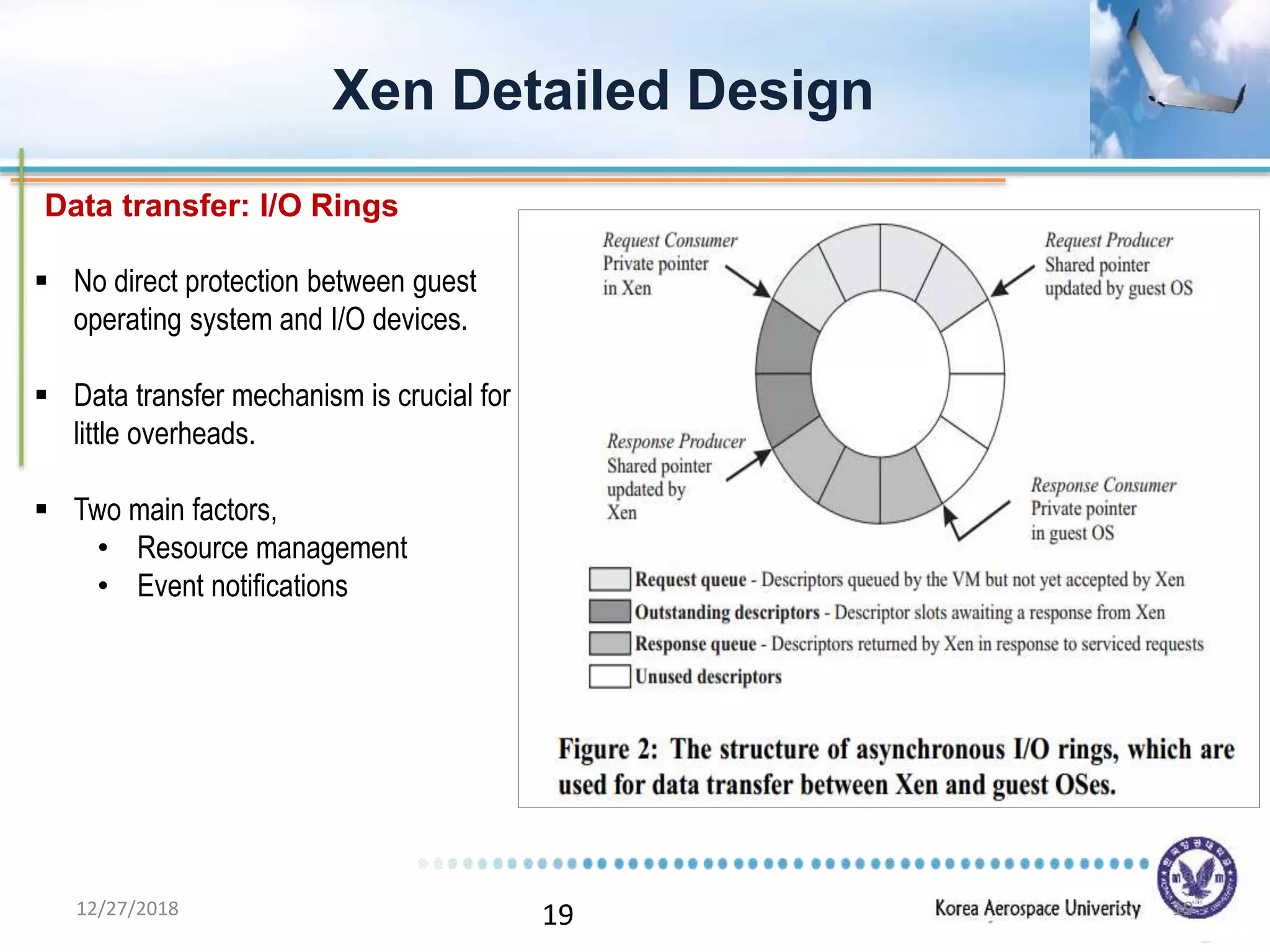
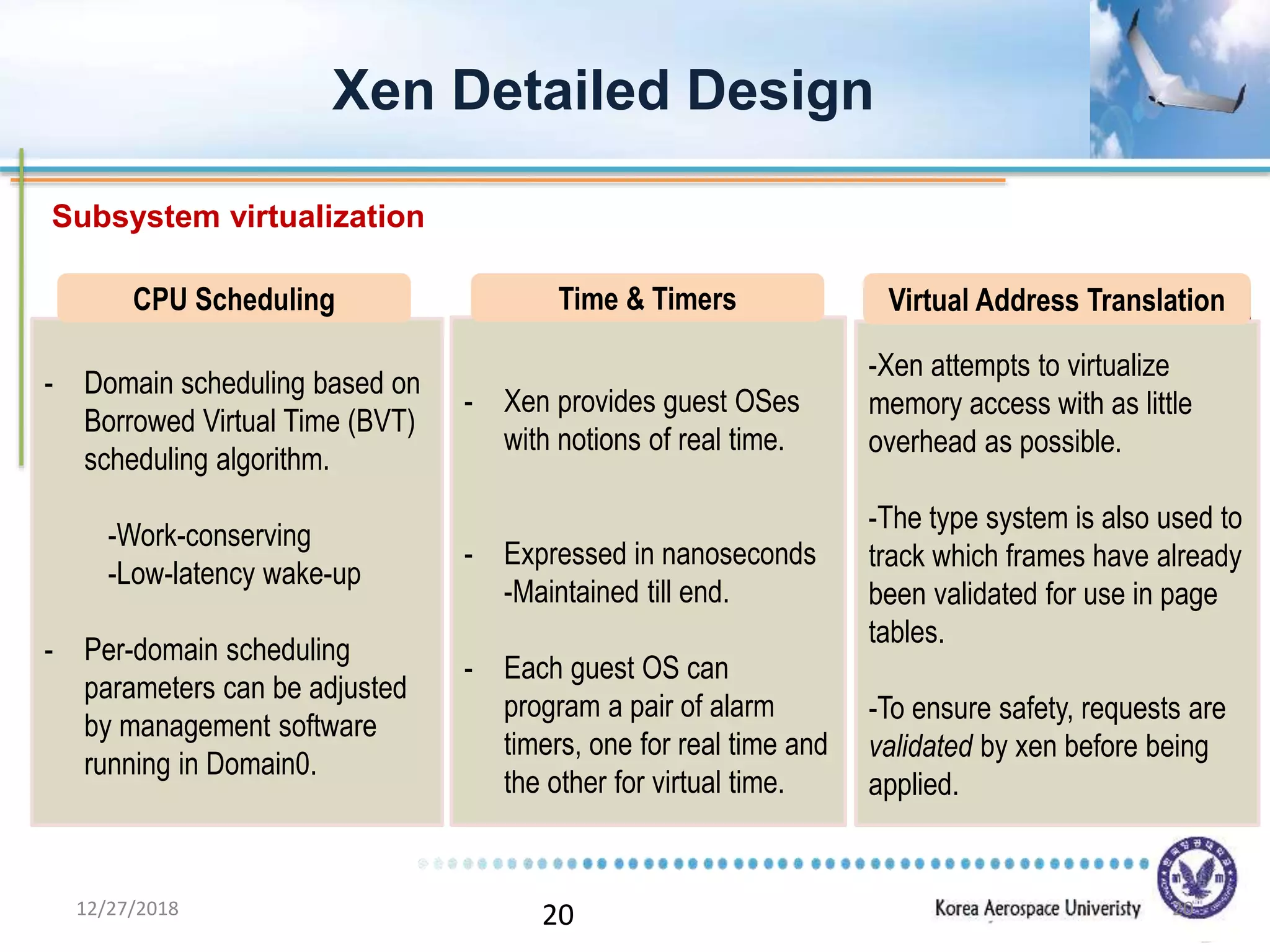
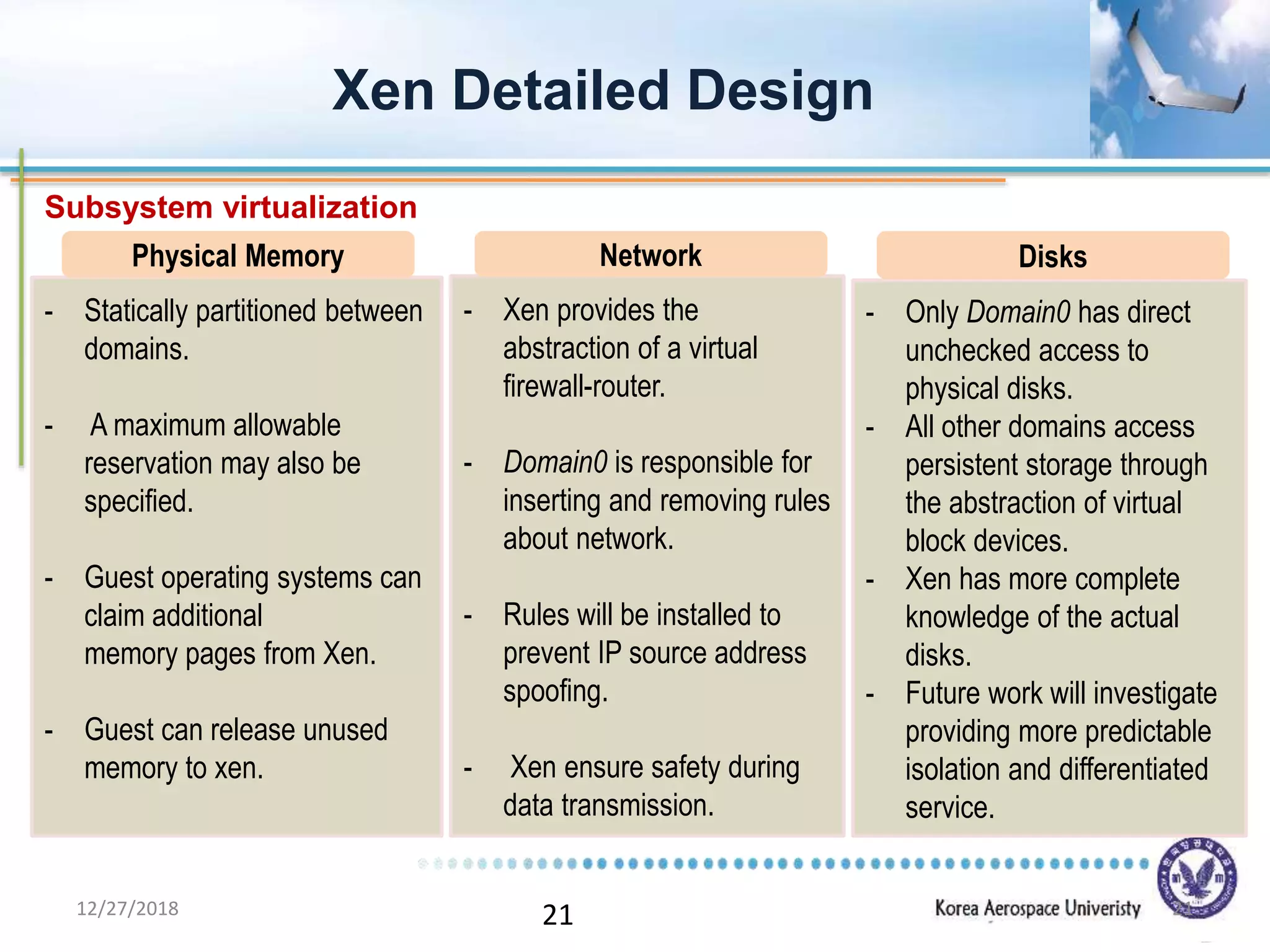
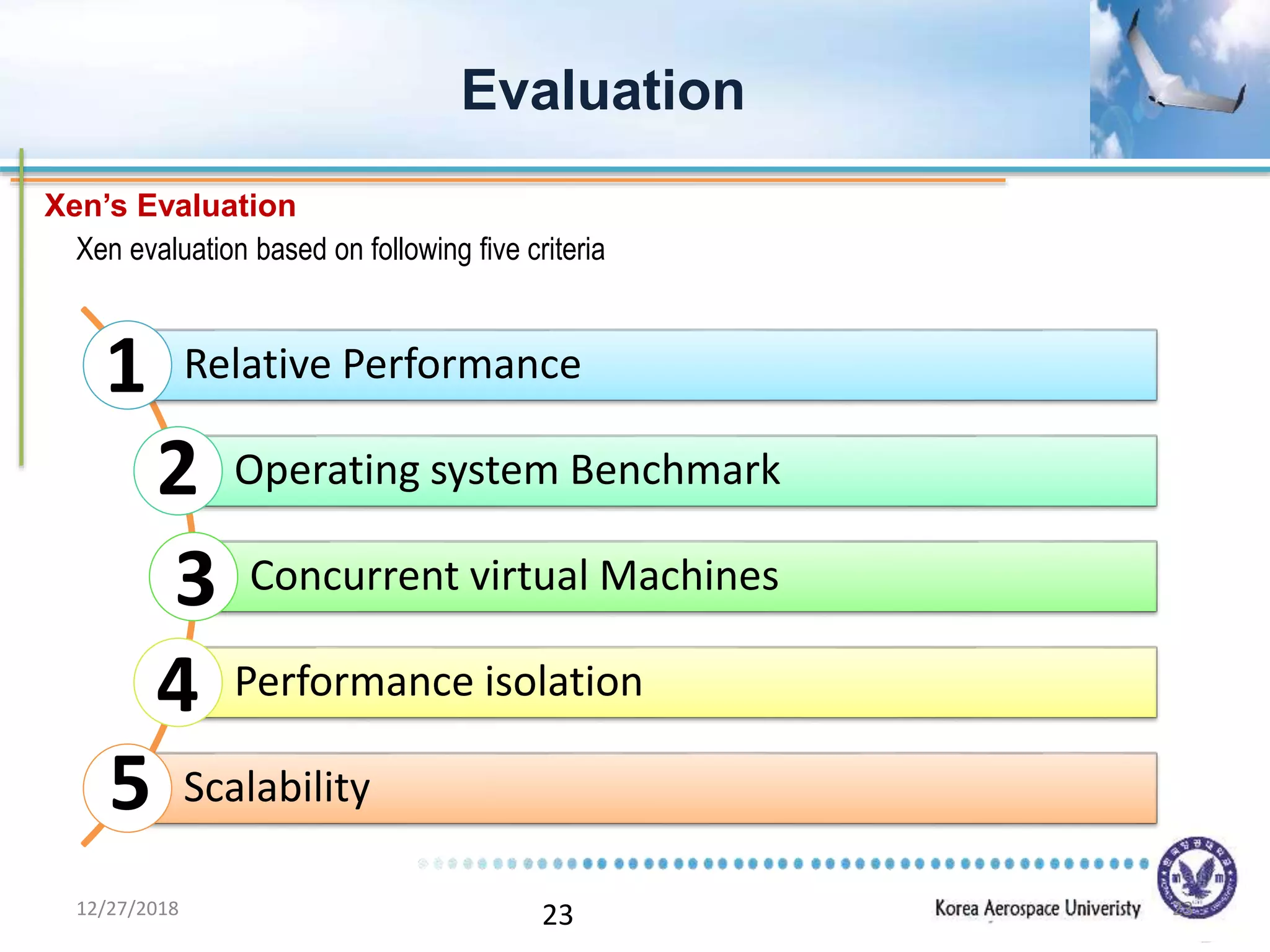
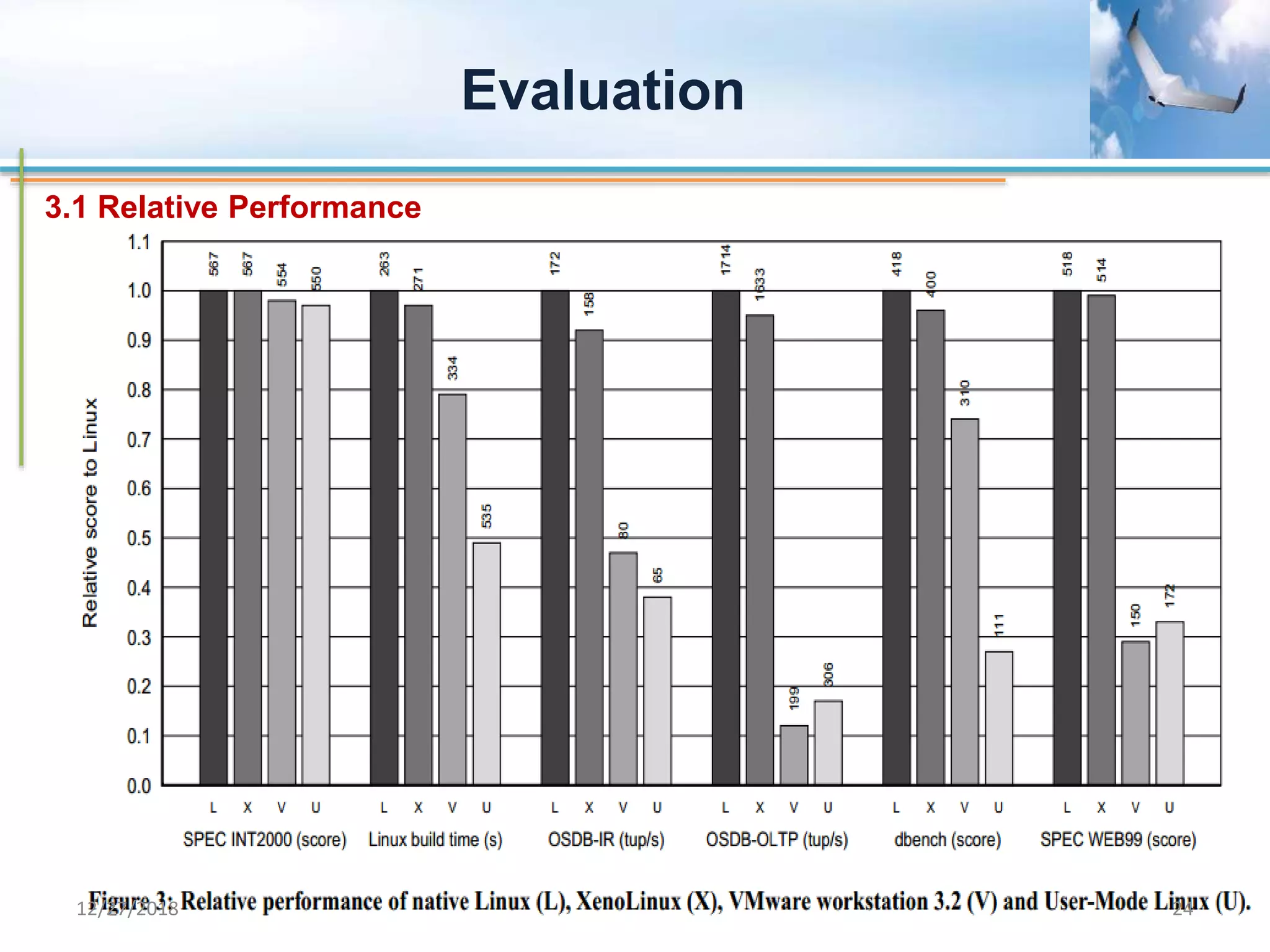
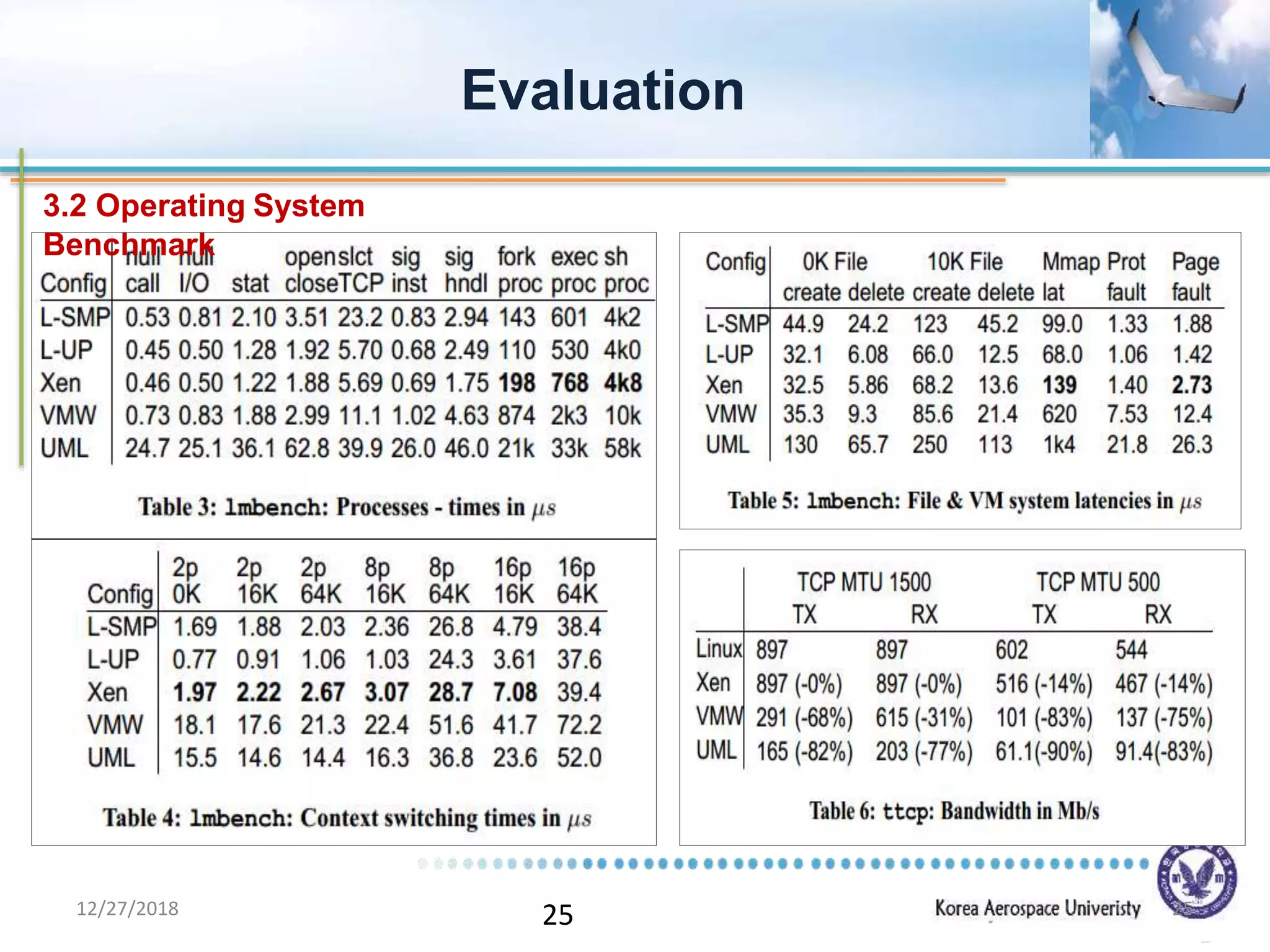
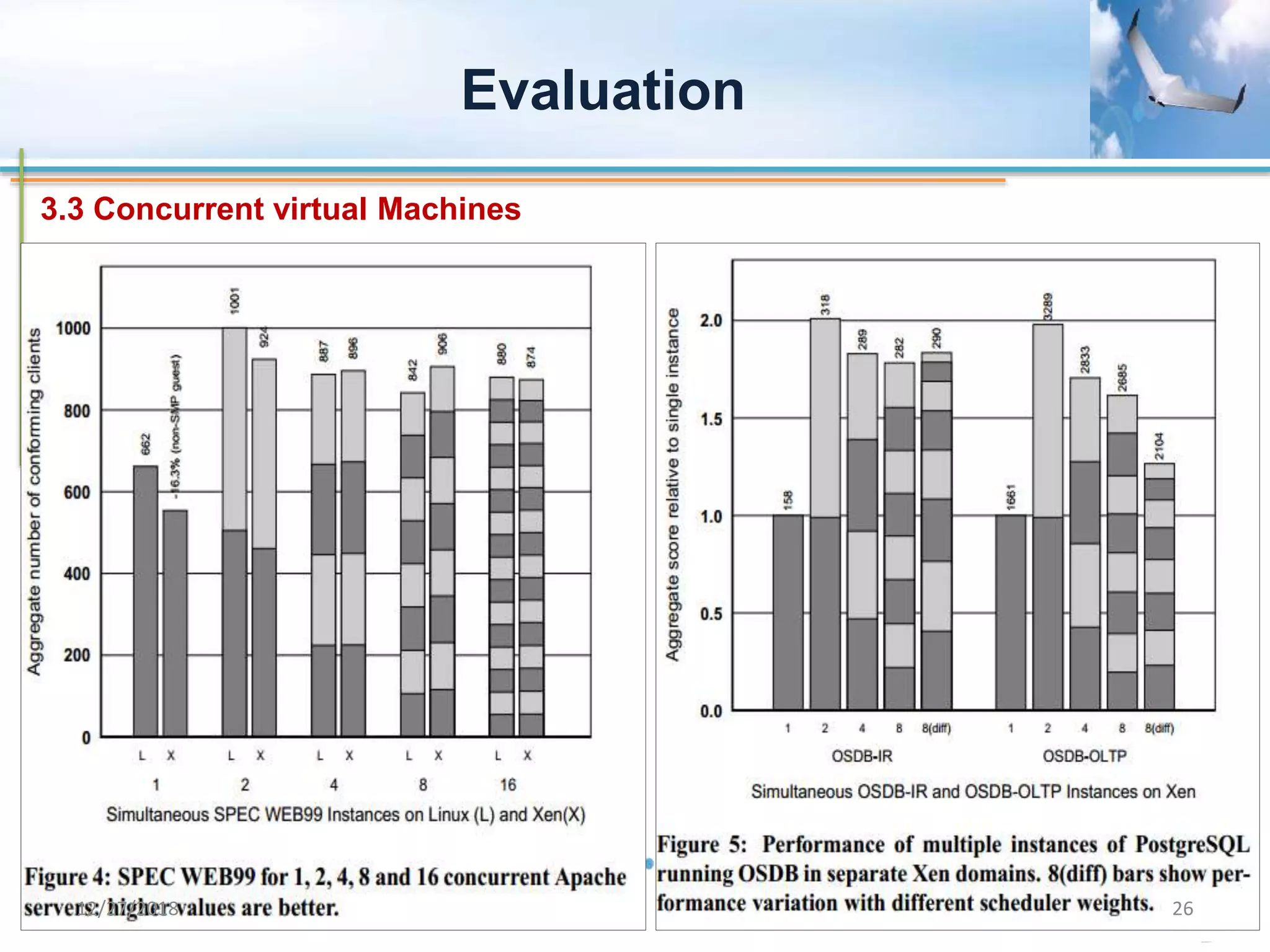
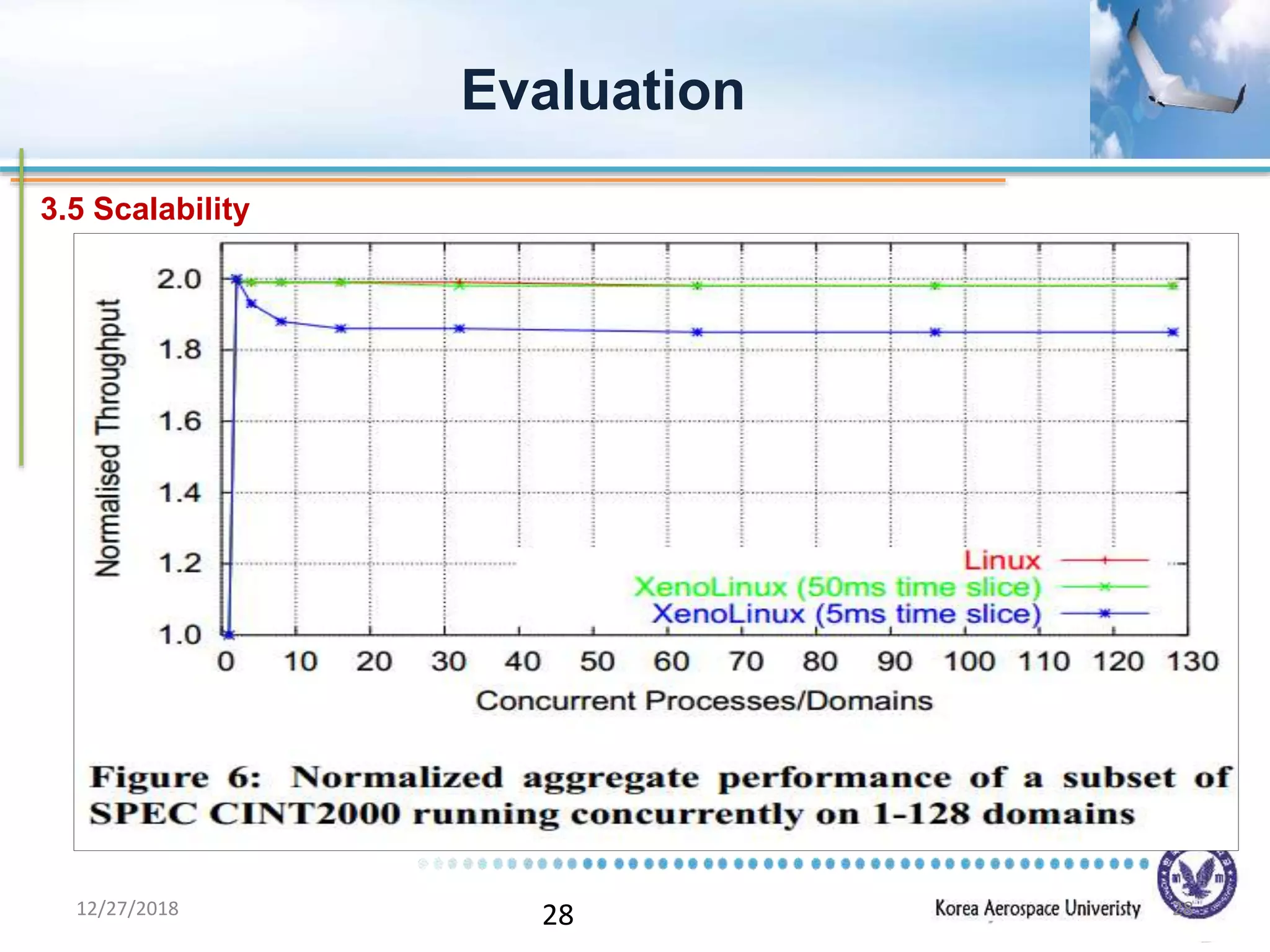
Xen is a virtual machine monitor that allows multiple operating systems to run concurrently on a single physical machine. It uses paravirtualization rather than full virtualization to improve performance. Xen provides performance isolation between guest operating systems and can host different operating systems with only small modifications required. Evaluation shows Xen achieves near native performance for guest operating systems and provides strong performance isolation even under malicious workloads. Future work aims to improve memory performance and support additional guest operating systems like Windows.