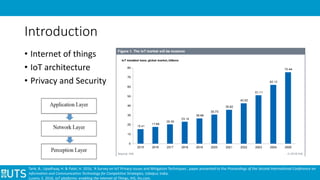
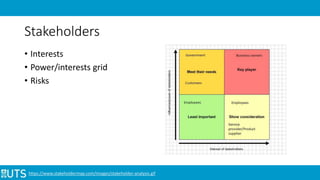
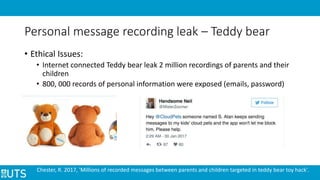
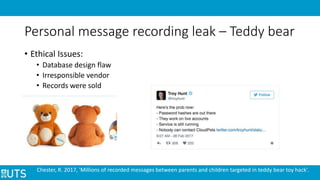
This document discusses ethical issues related to smart technology in IoT. It begins with an introduction to IoT, architecture, and privacy/security concerns. It then examines stakeholders and their interests/risks. Resolutions discussed include security measures at different layers and increasing user awareness. Two specific examples are analyzed: a teddy bear hack that leaked personal recordings, and Fitbit sharing customer health data. Considerations for dealing with ethical issues include regulations, following ethics codes, customer benefit, and security improvements. Examples of IoT uses in business and related incidents/vulnerabilities are also summarized.