This document discusses various techniques used in ethical hacking such as password cracking, Trojans, phishing, and social engineering. It covers related topics like IP addresses, torrent blocking, cookies, spoofing, denial of service (DoS) attacks, and steganography. The document provides definitions and examples of these terms. It also lists some best security practices for protecting systems and data, such as using a firewall, antivirus software, strong passwords, and encryption.

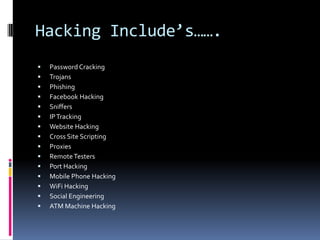







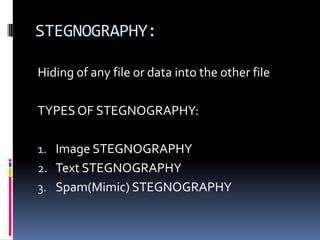
![DOS ATTACK:
To bring down an entire network
-Each system connected to internet has
limited bandwidth available.
[If our computer has bandwidth of 2mbps &
the criminal sends 100mbps of data then our
computer will crack]](https://image.slidesharecdn.com/ethicalhackingpallavi-120315152022-phpapp01/85/Ethical-Hacking-12-320.jpg)
![TYPES OF DOS ATTACK:
1.Ping Of Death:
2.TearDrop:
1]Ping Of Death:
65,536 bytes is the size of data packet.
(Not Larger Attack)](https://image.slidesharecdn.com/ethicalhackingpallavi-120315152022-phpapp01/85/Ethical-Hacking-13-320.jpg)