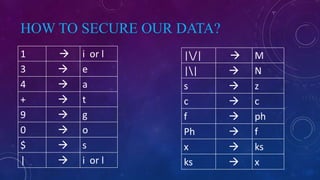
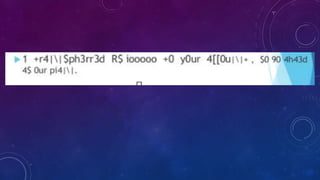
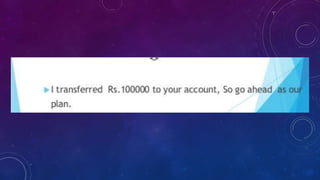
The document outlines a seminar on hacking, including its definition, history, types, techniques, and security measures. It explains the different motivations behind hacking, such as fun or malicious intent, and provides guidance on what to do after being hacked and how to secure data. Additionally, it highlights both the advantages and disadvantages of hacking practices.