Embed presentation
Downloaded 60 times




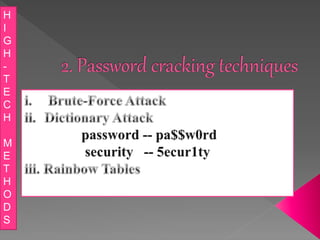

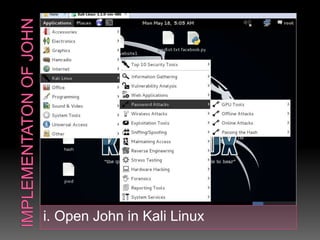
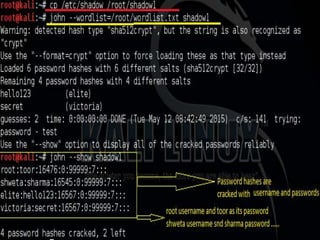
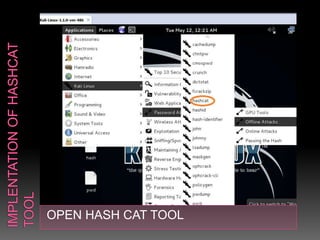
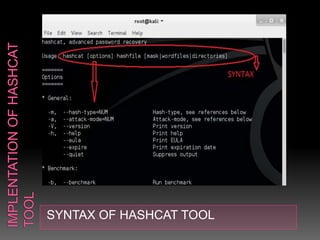
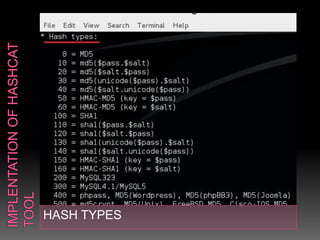
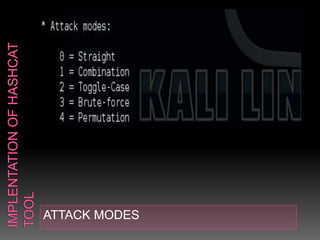
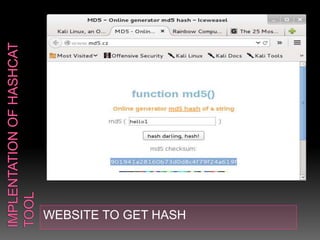
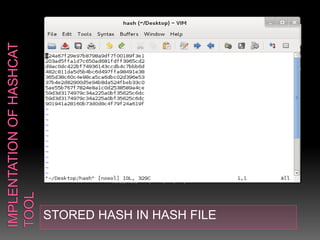
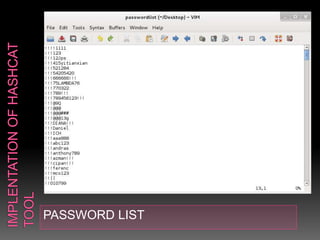
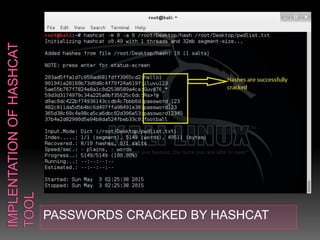
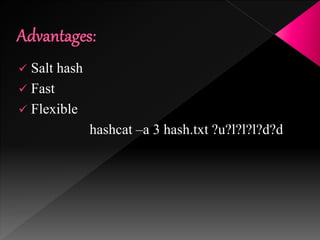

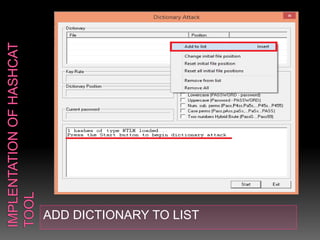
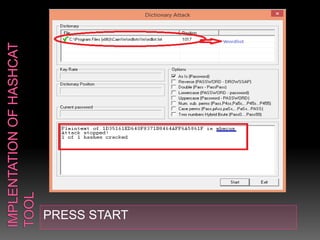
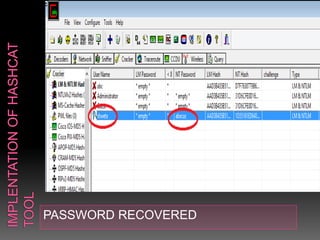

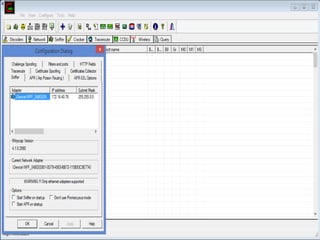
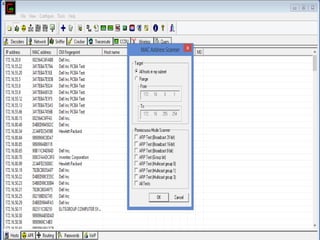
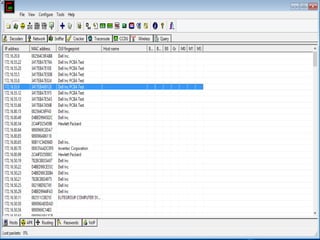
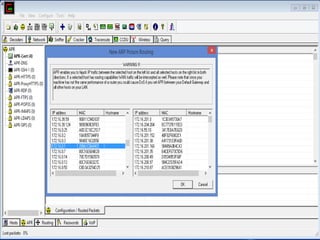
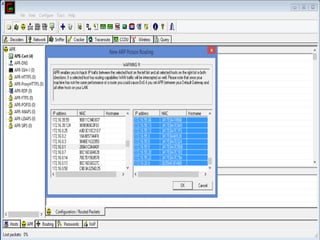
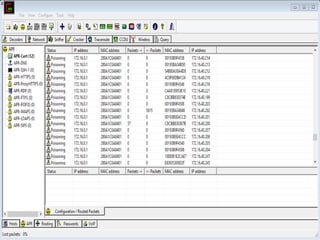
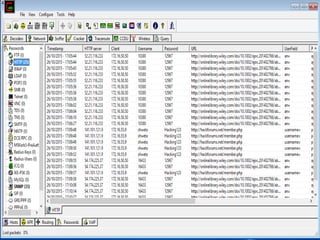
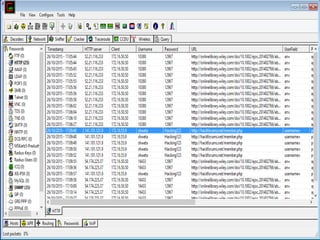
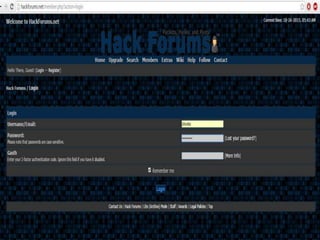
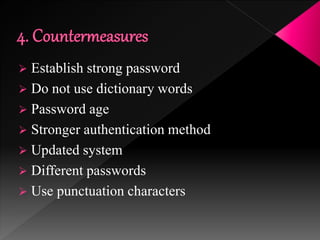




This document discusses various high-tech and low-tech methods used for password cracking such as social engineering, shoulder surfing, guessing passwords, and tools like John the Ripper, Hashcat, Cain and Abel, Hydra, Rainbow Crack, and Brutus. It provides information on how these tools work, their features, and the different modes used for password cracking. Finally, it discusses some best practices for password security such as using strong passwords, not reusing passwords, avoiding password sharing, and enforcing strong password policies.

























































