1) E-safety guidance is important for learners of all ages as technology and online learning have become integrated into education.
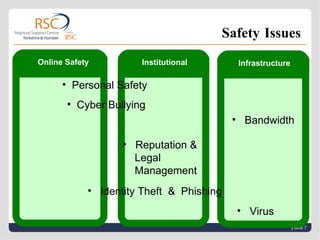
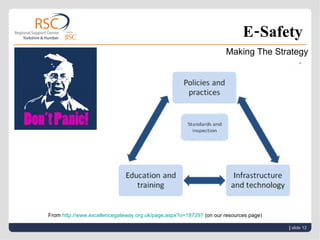
2) There are personal, technical, and institutional issues to consider regarding e-safety, including cyberbullying, identity theft, virus protection, and reputation management.
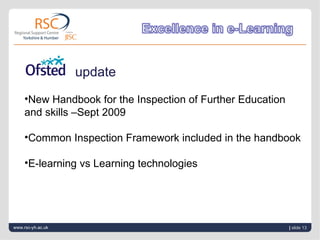
3) OFSTED now evaluates how educational institutions support e-safety and promote responsible digital literacy among learners.