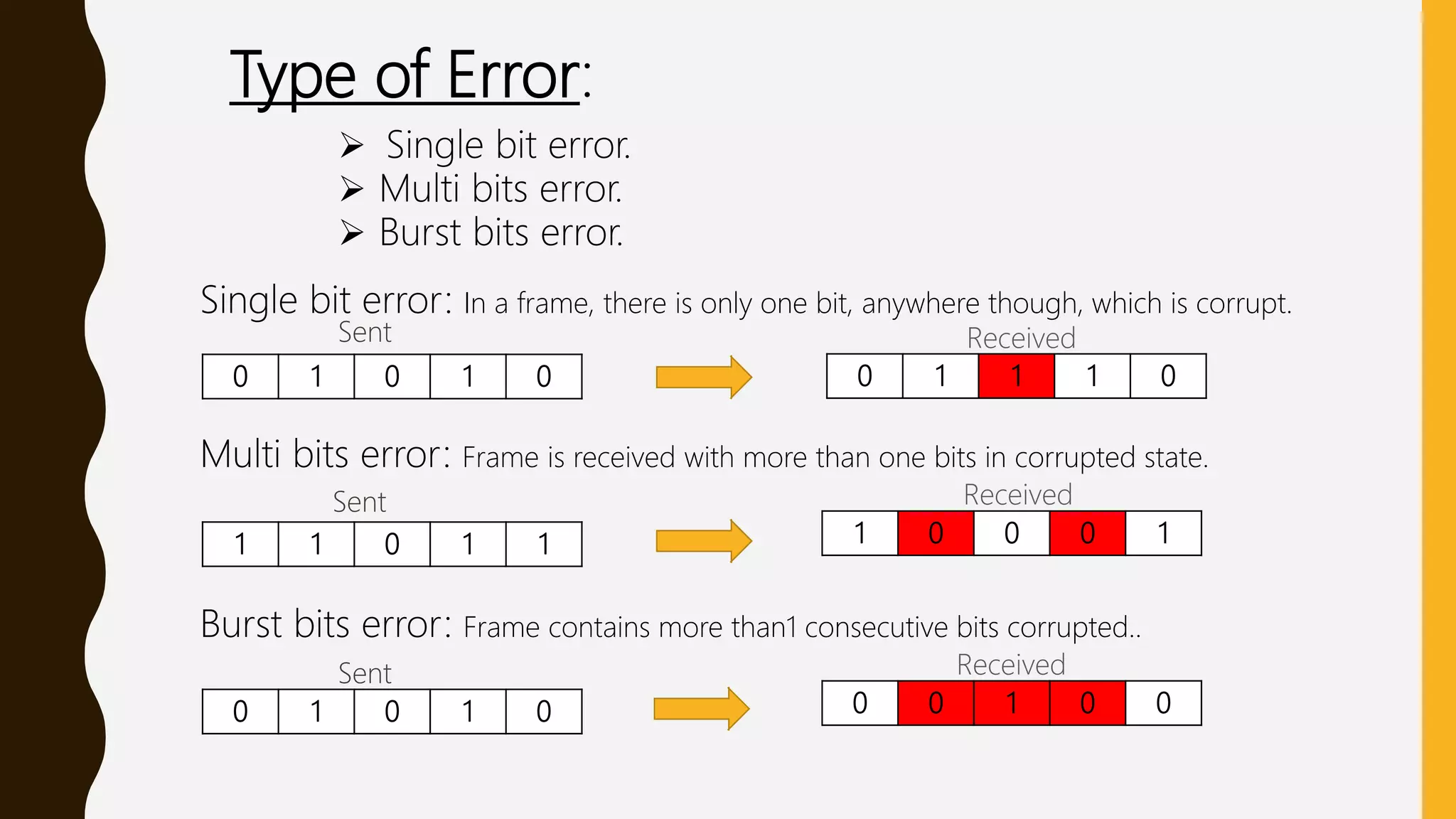
The presentation discusses error detection and correction techniques, specifically focusing on Hamming code, which can detect up to two-bit and correct one-bit errors during data transmission. It defines different types of errors such as single bit errors, multi-bit errors, and burst errors, explaining how Hamming codes are applied for correction and the role of parity bits. While Hamming code is effective for single-bit errors, it has limitations when handling multiple bit errors.