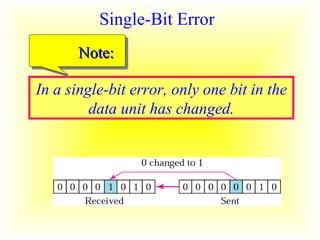
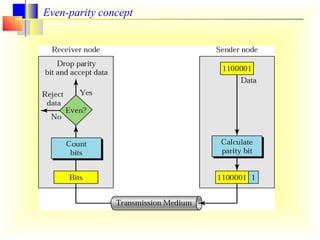
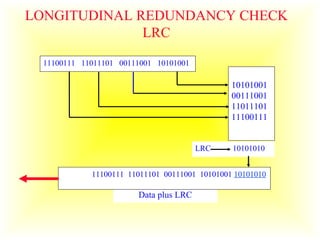
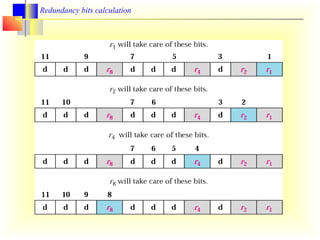
This document discusses error detection and correction in digital communication. It covers the types of errors like single-bit and burst errors. It then explains various error detection techniques like parity checks, longitudinal redundancy checks, and cyclic redundancy checks which work by adding redundant bits. Finally, it discusses Hamming codes, which can not only detect errors but also correct single-bit errors through the strategic placement of redundant bits.