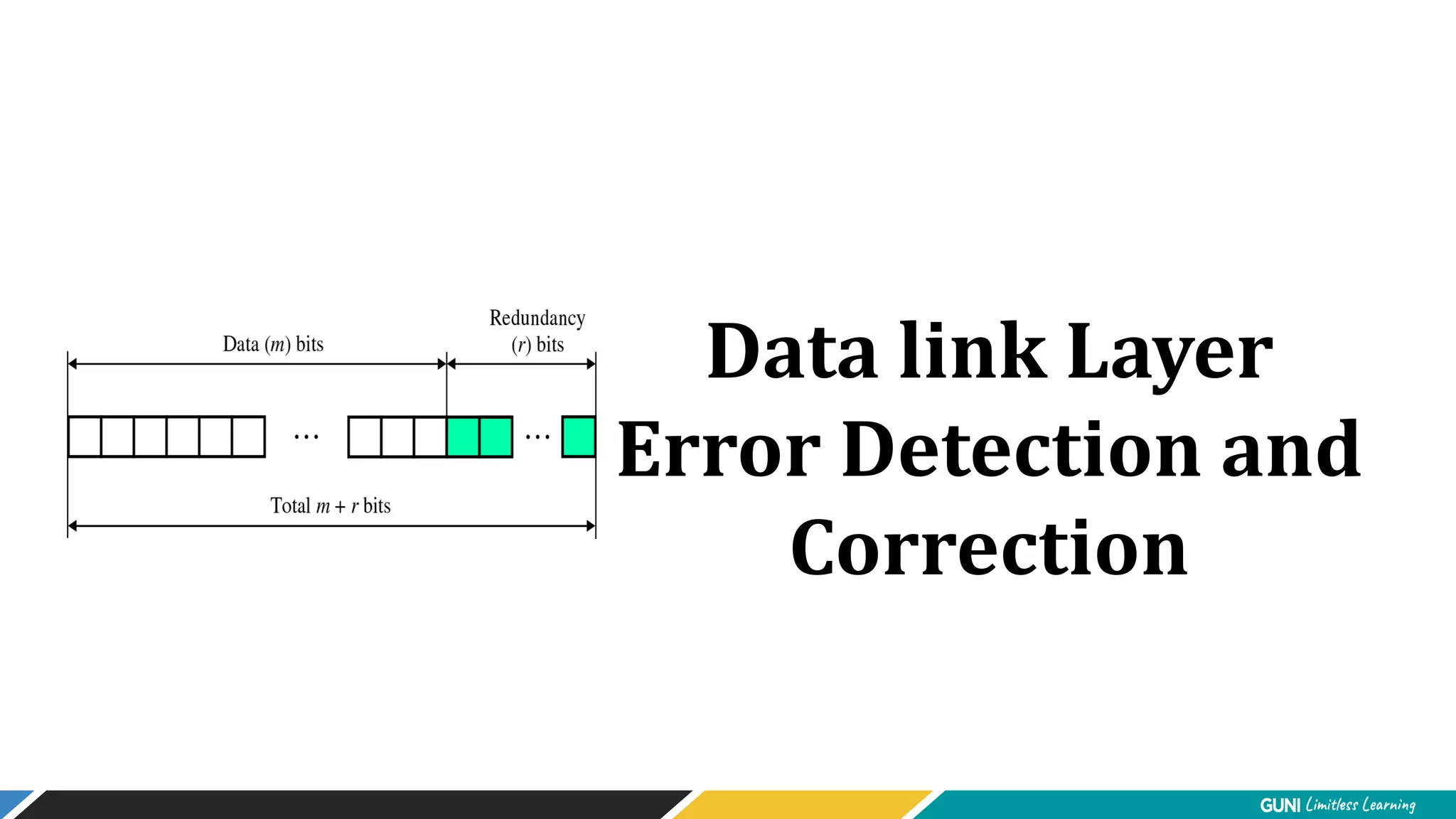
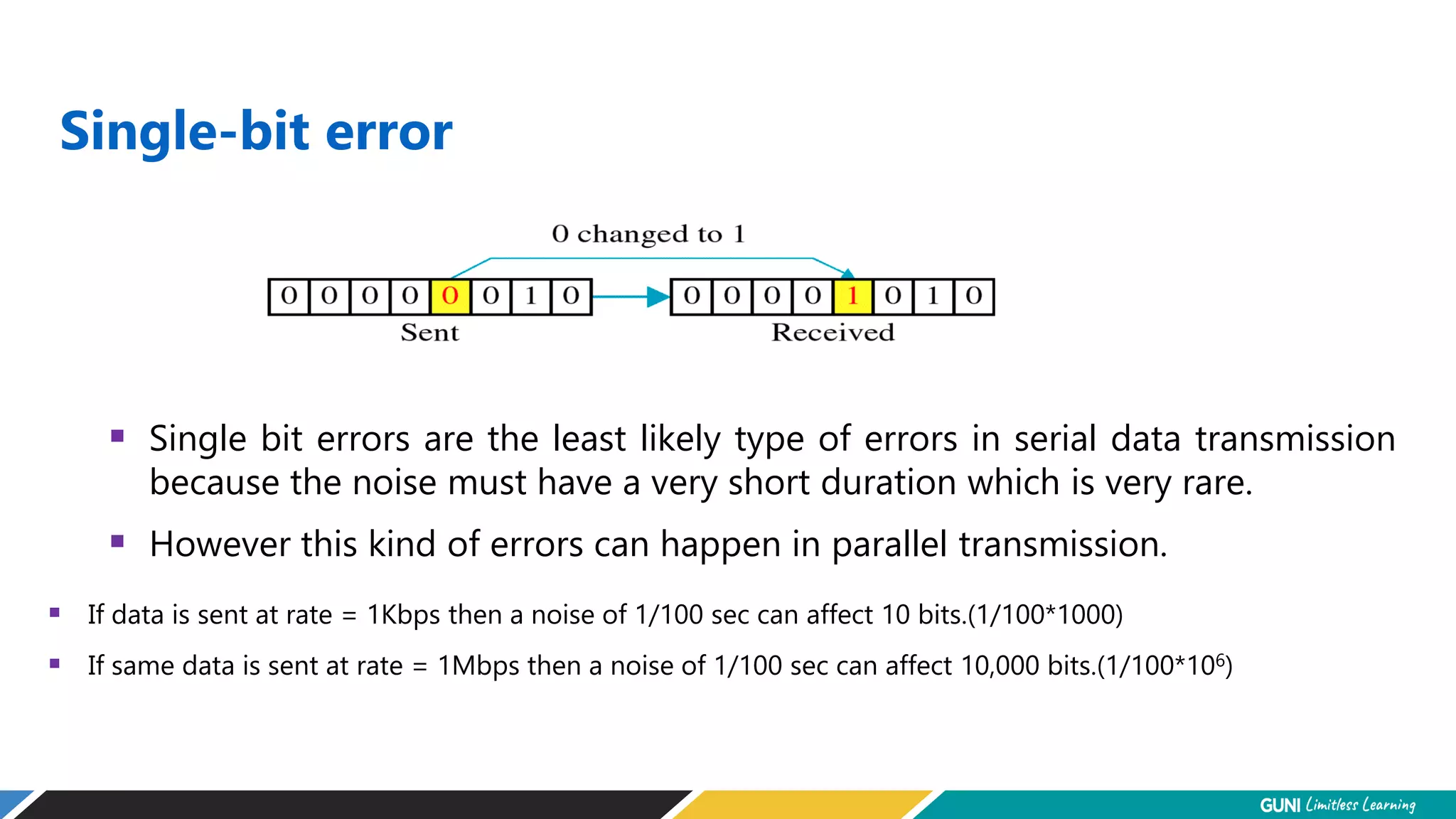
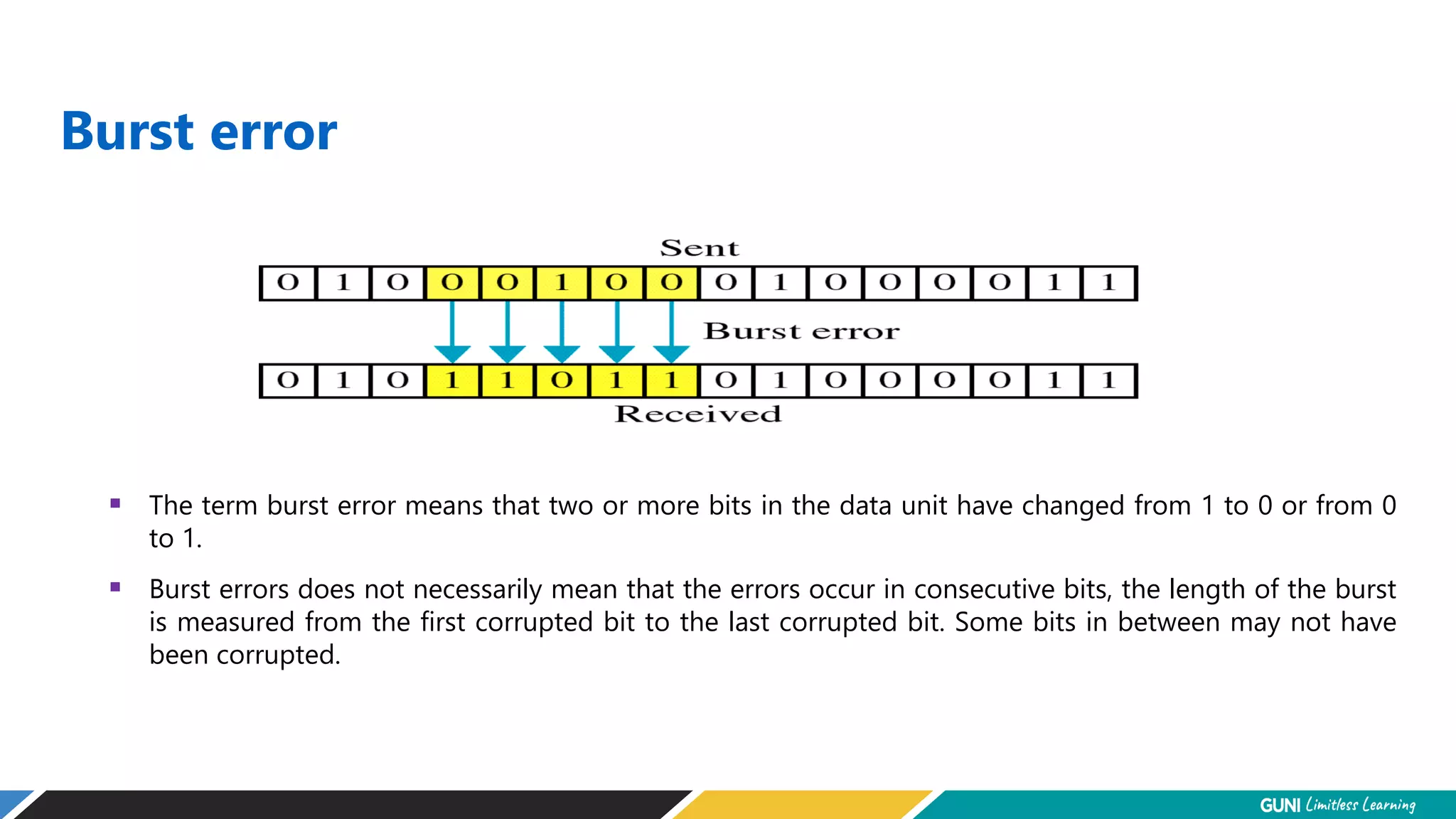
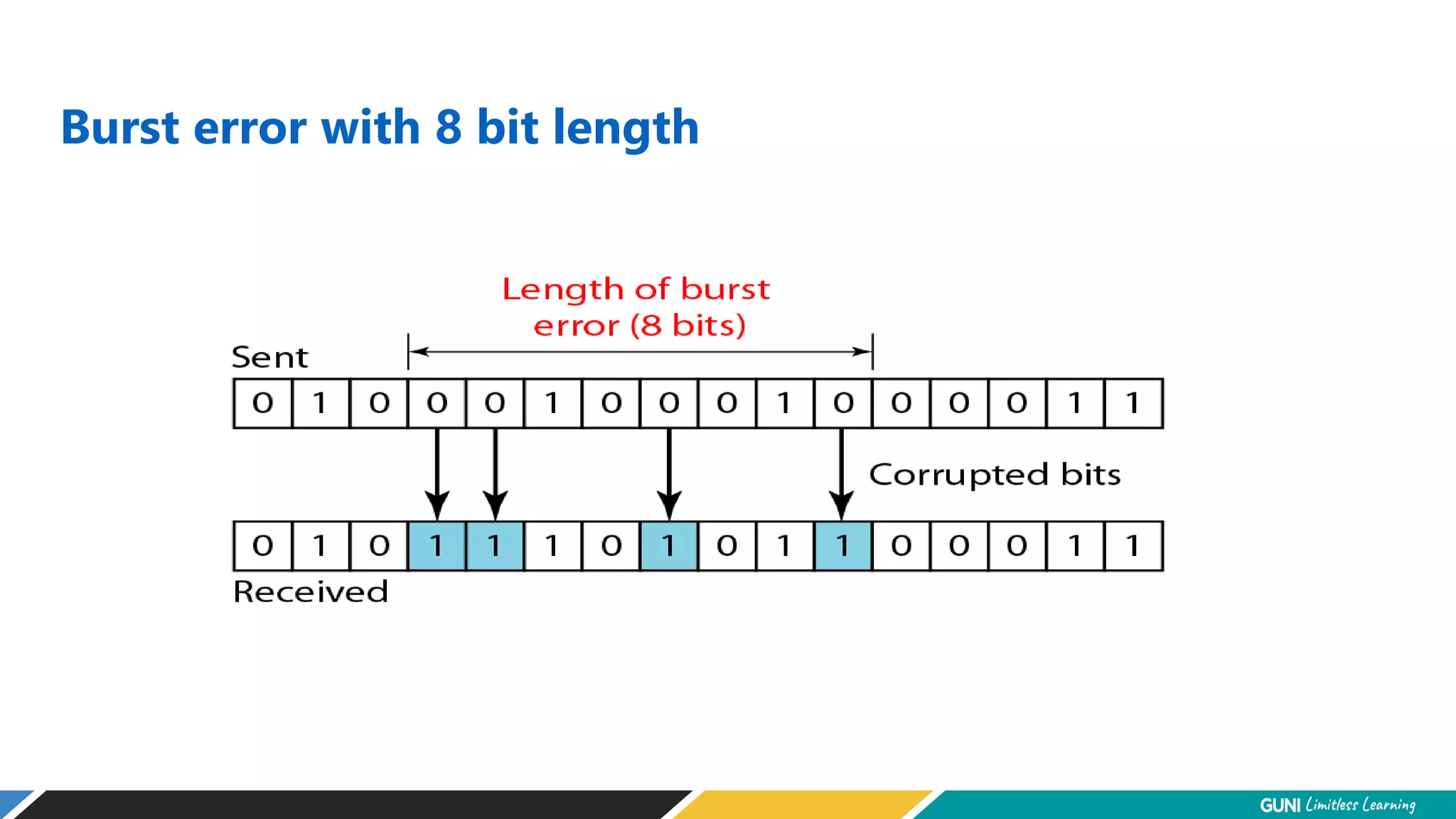
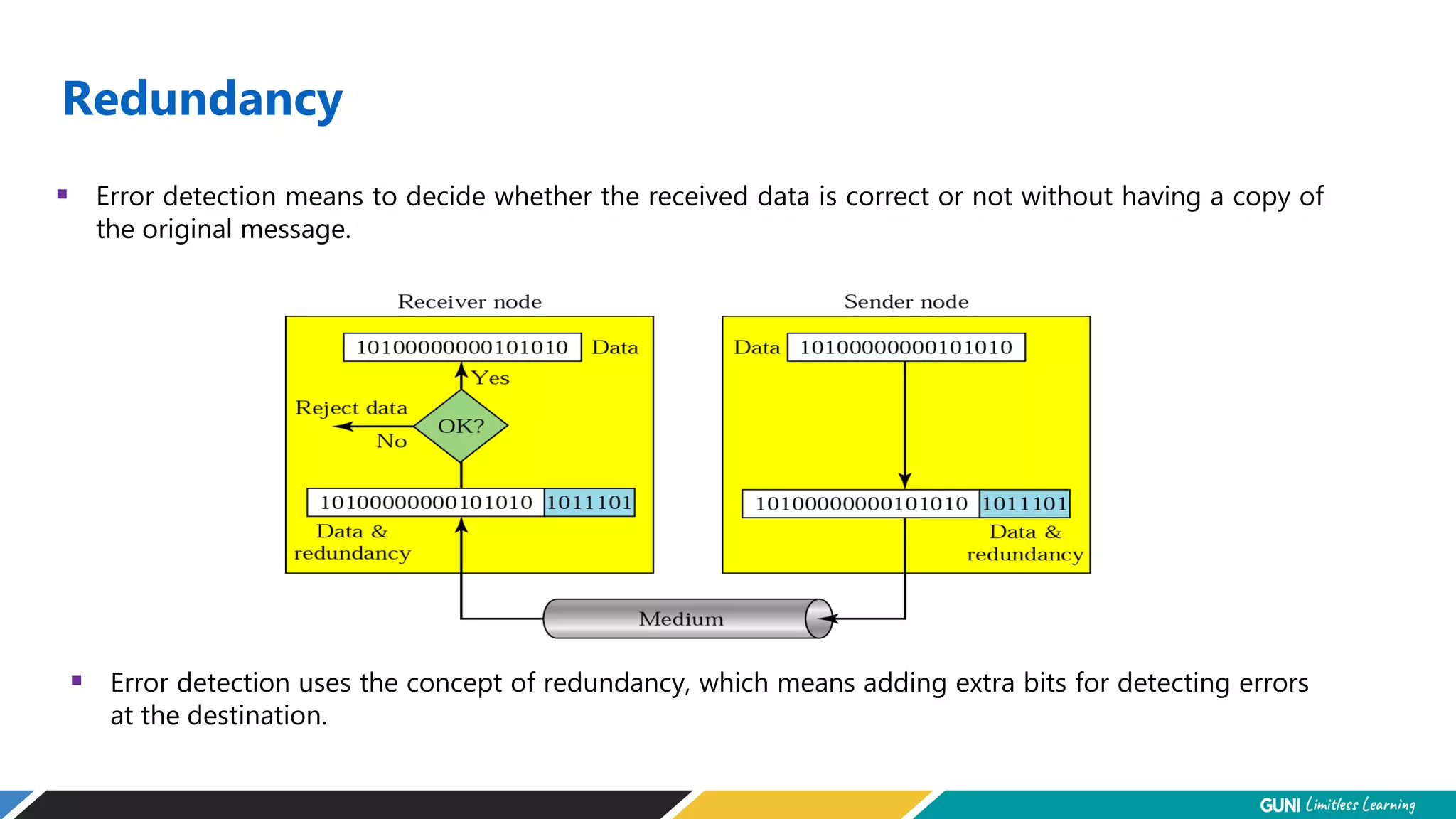
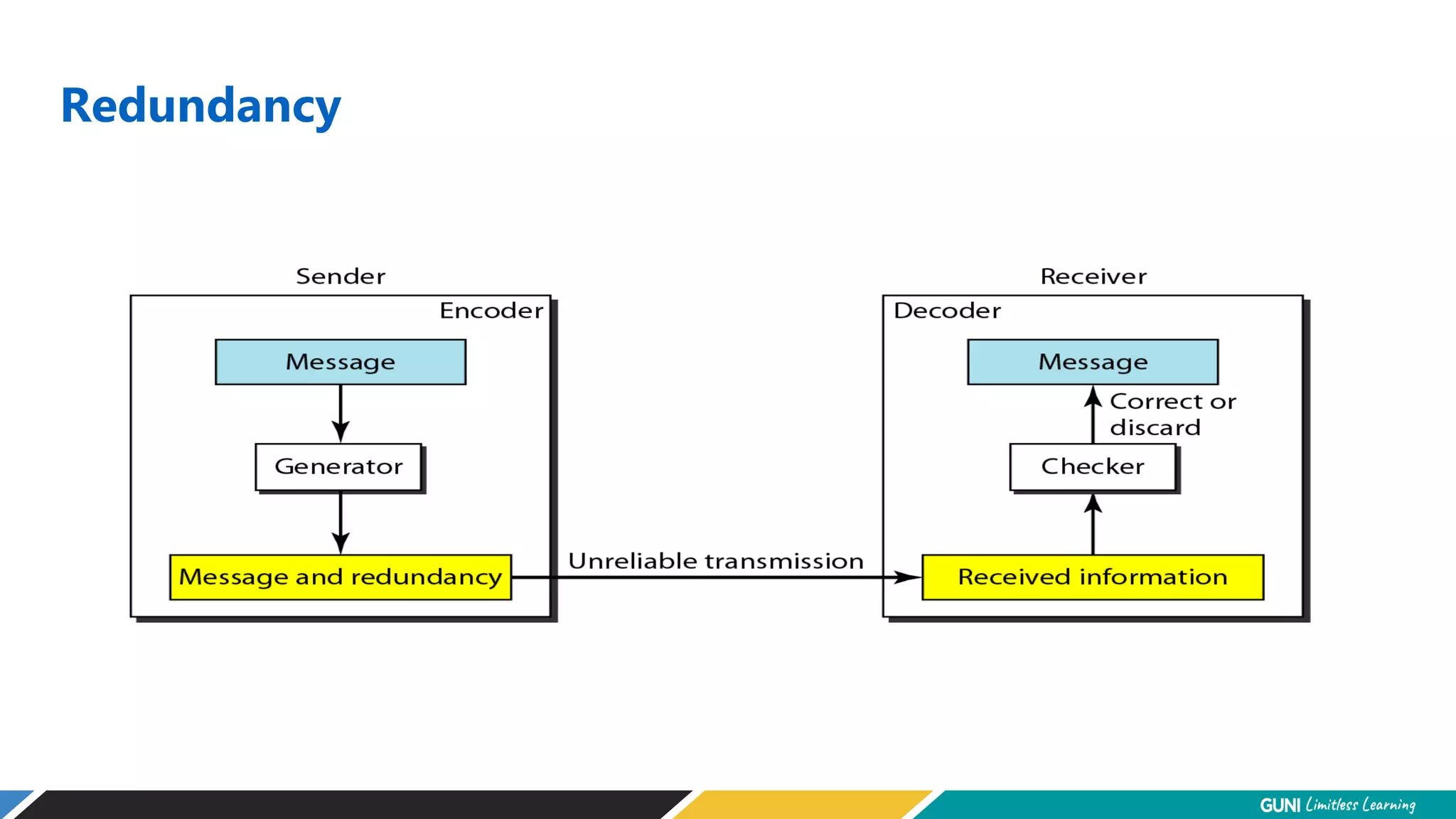
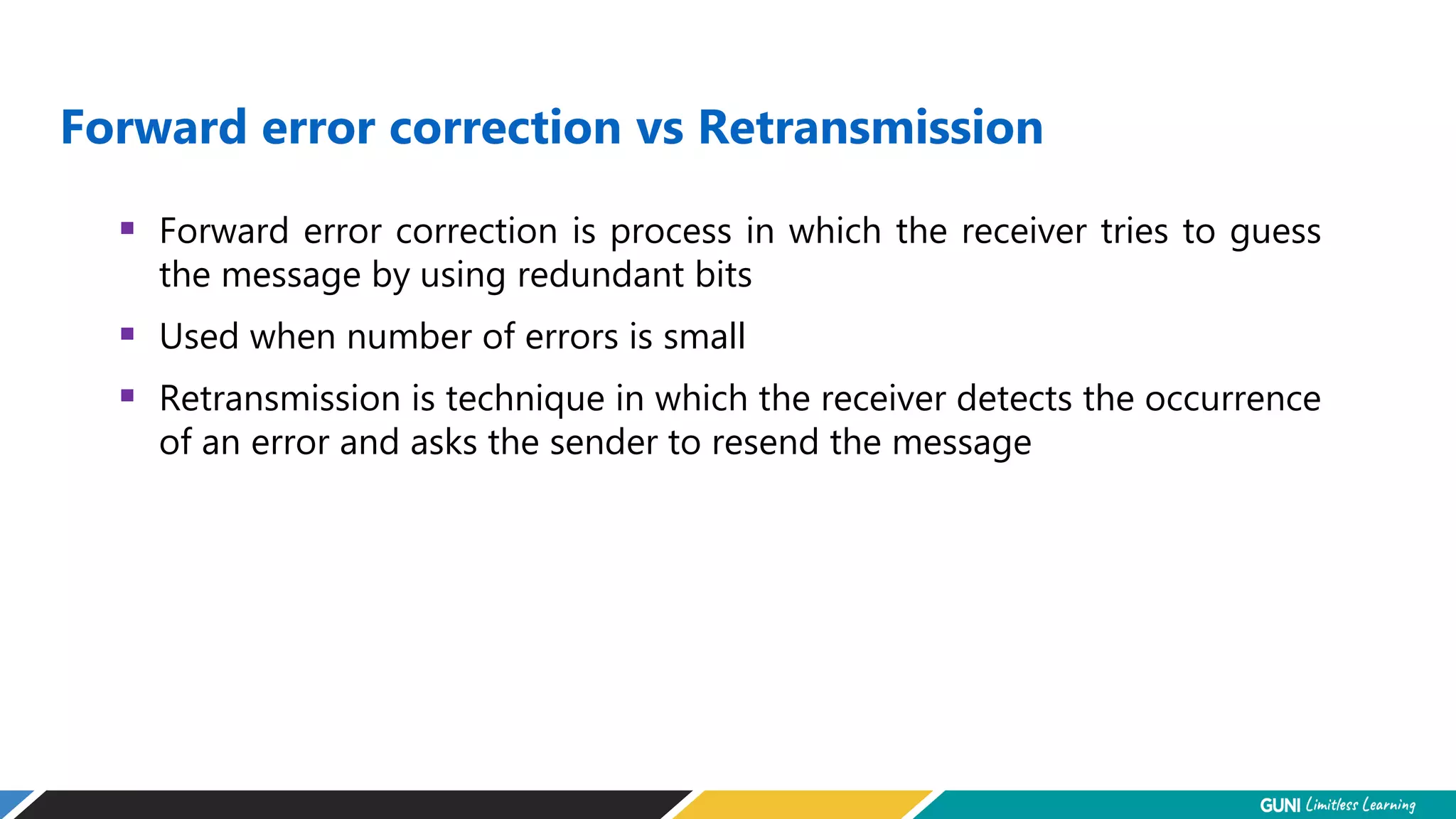
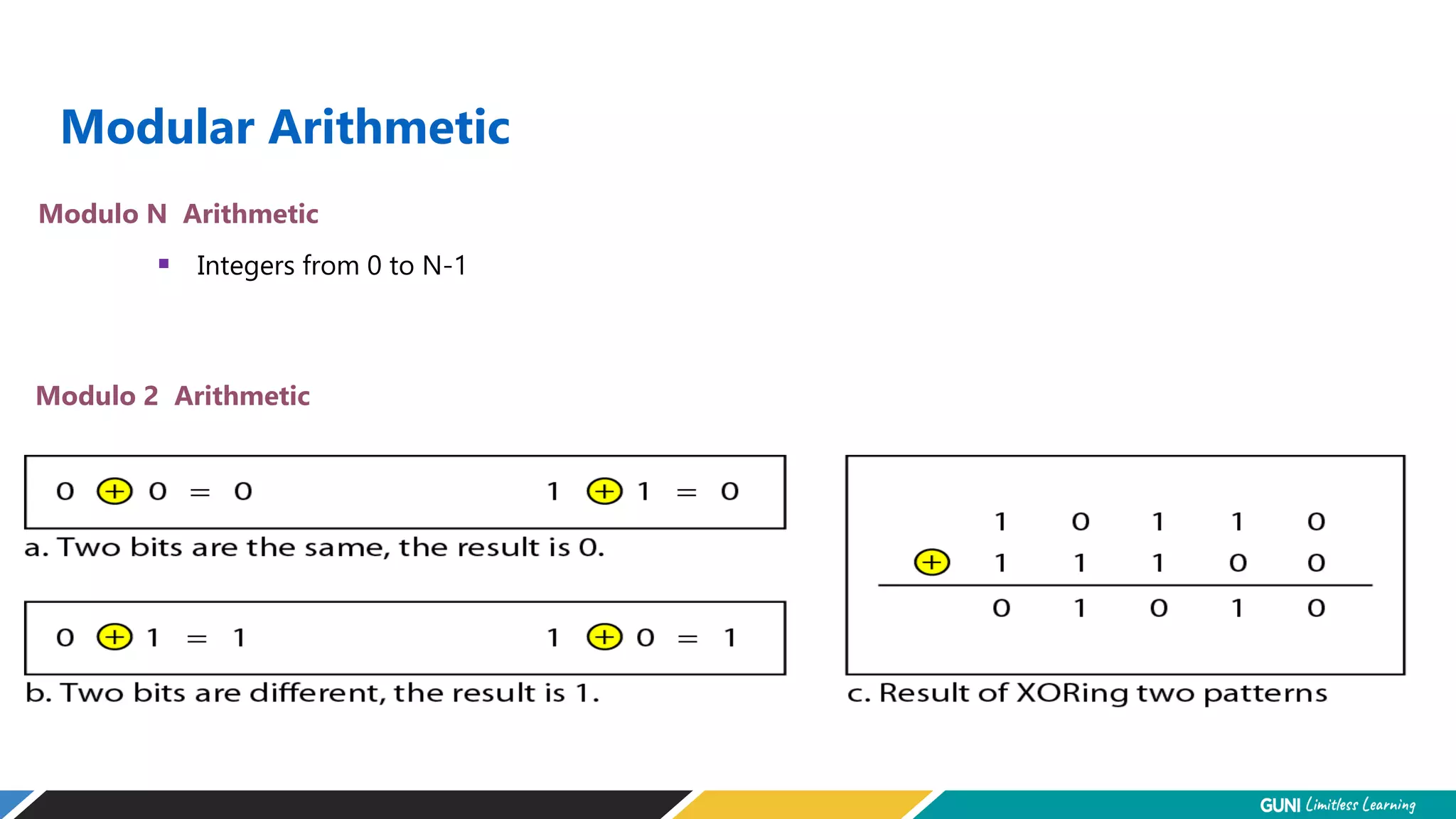
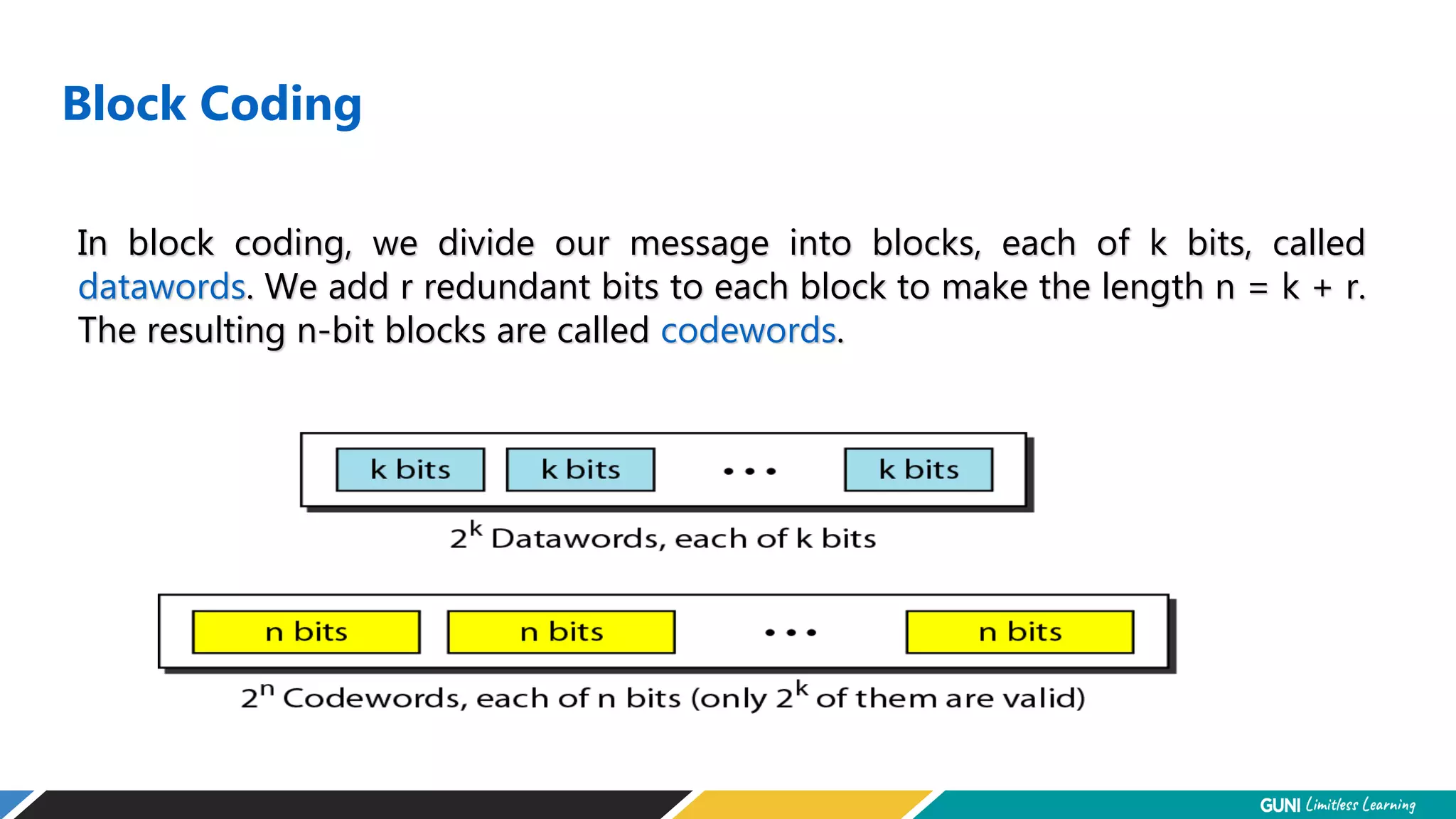
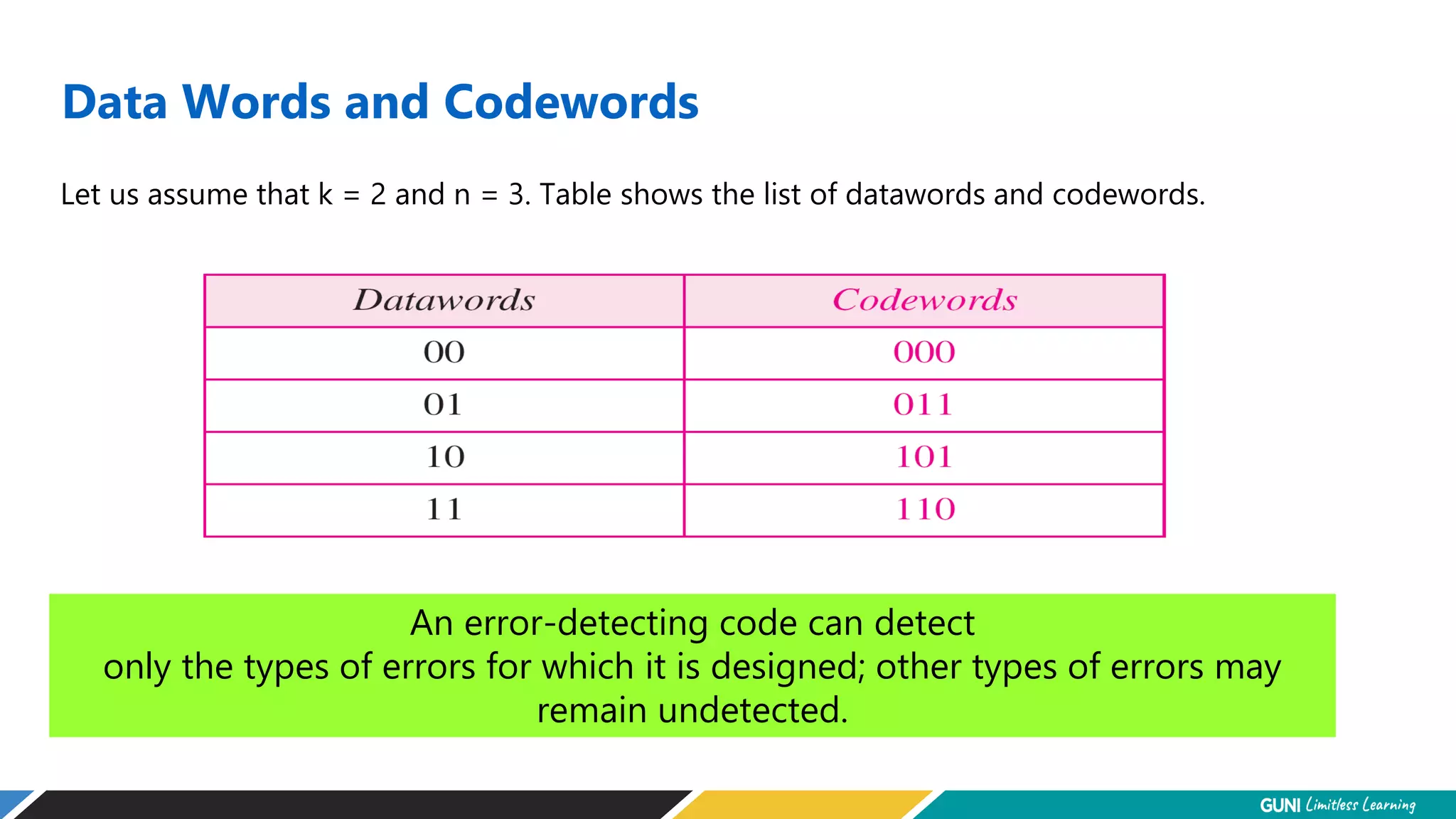
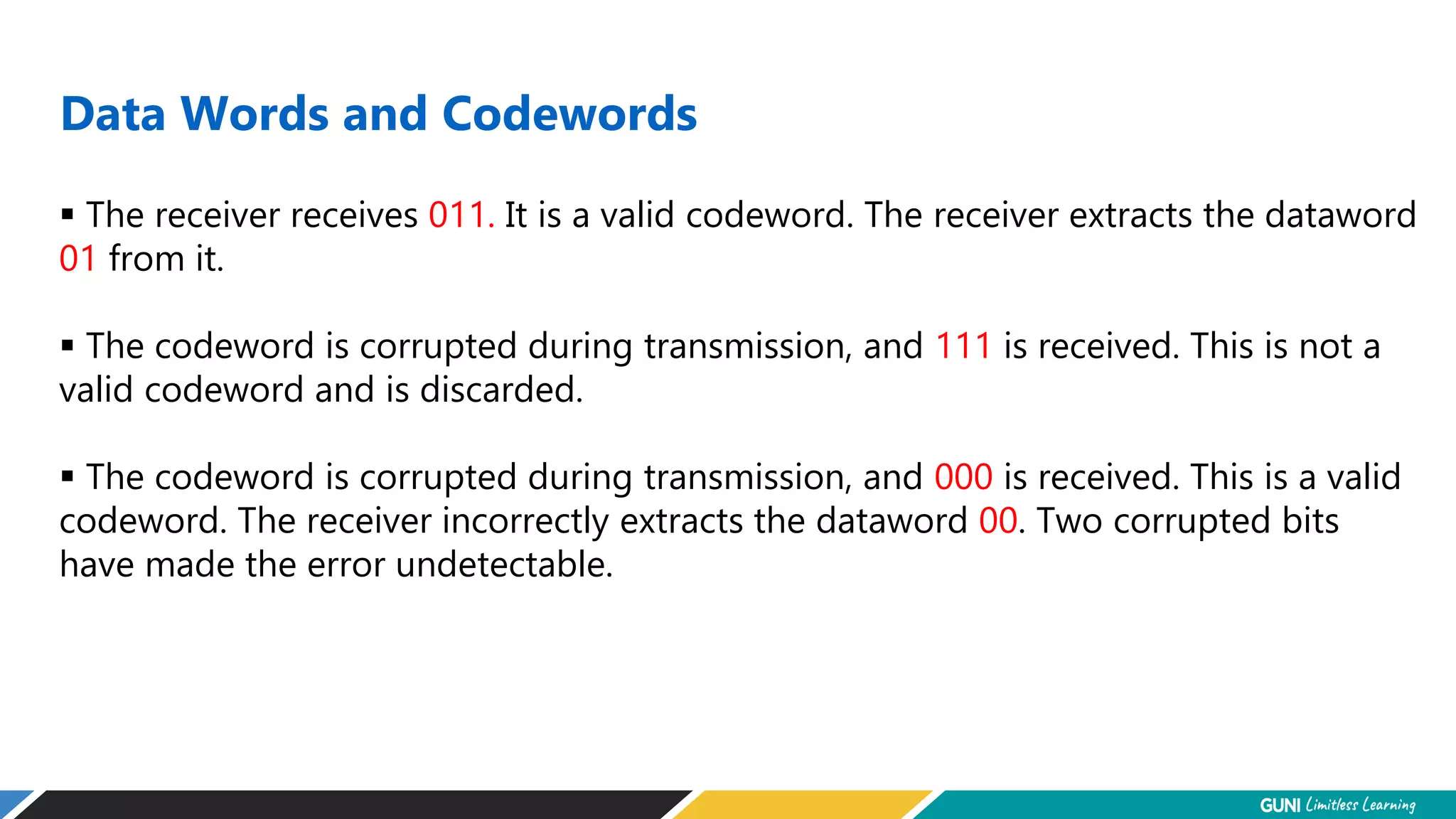
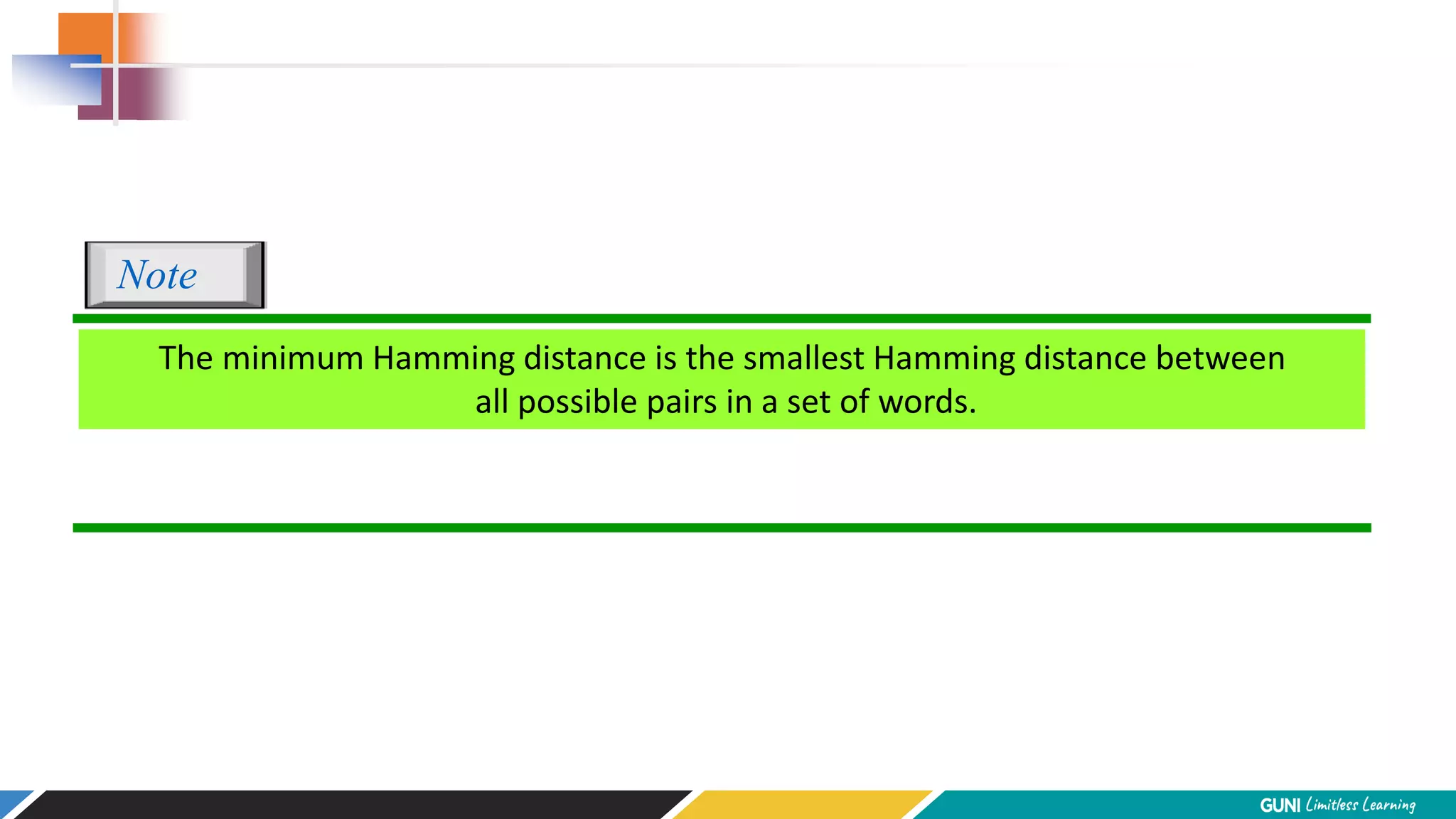
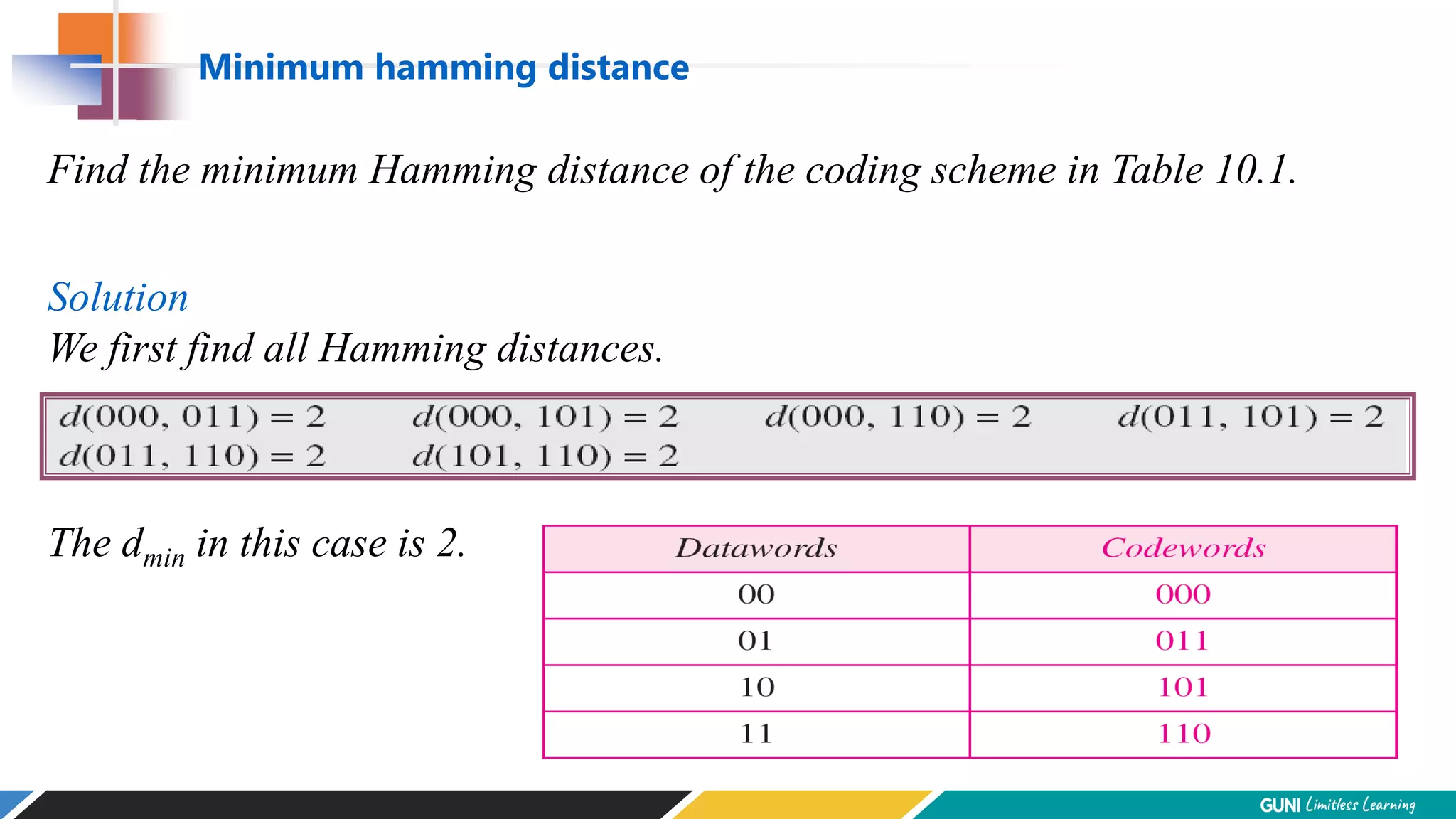
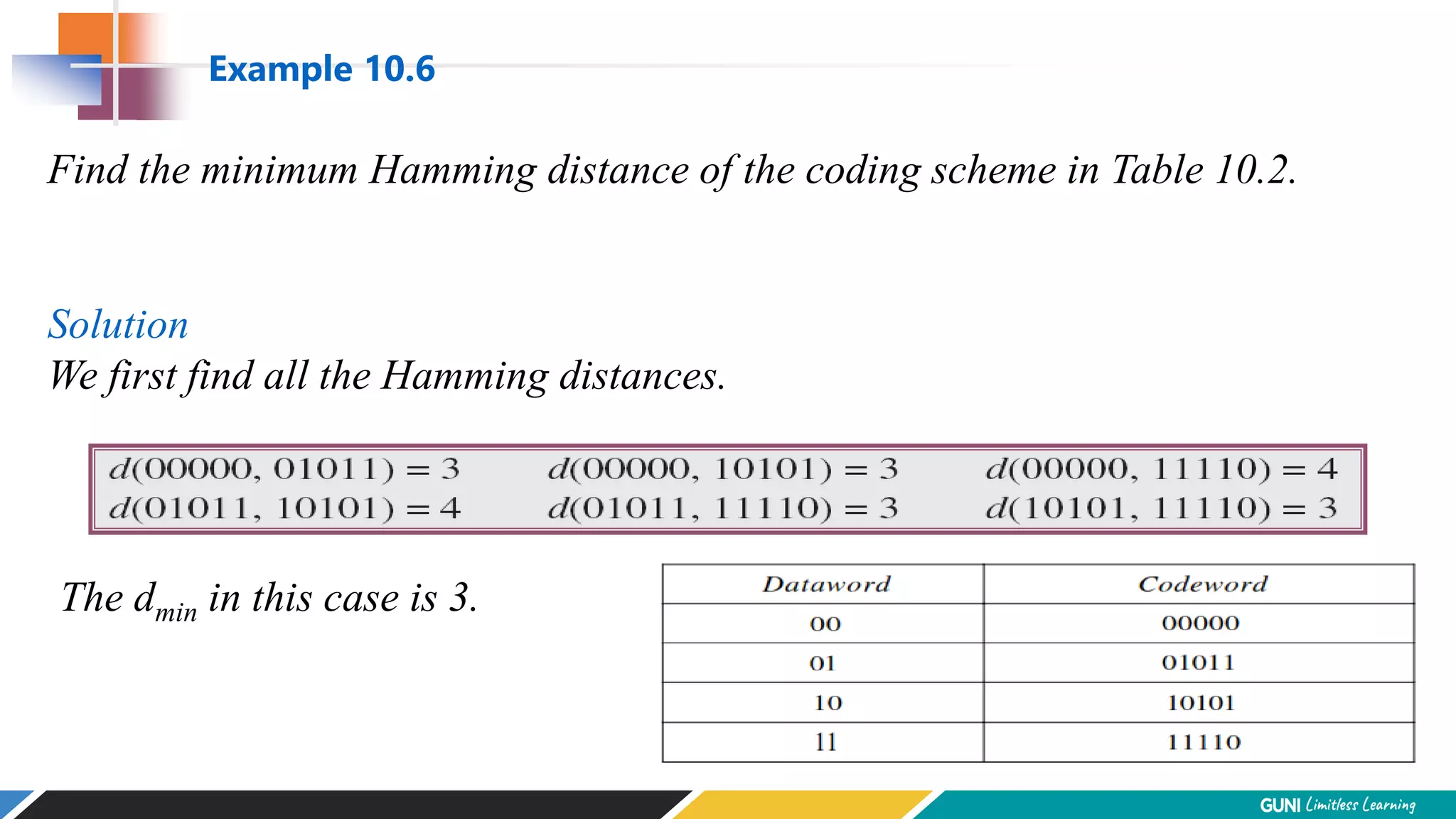
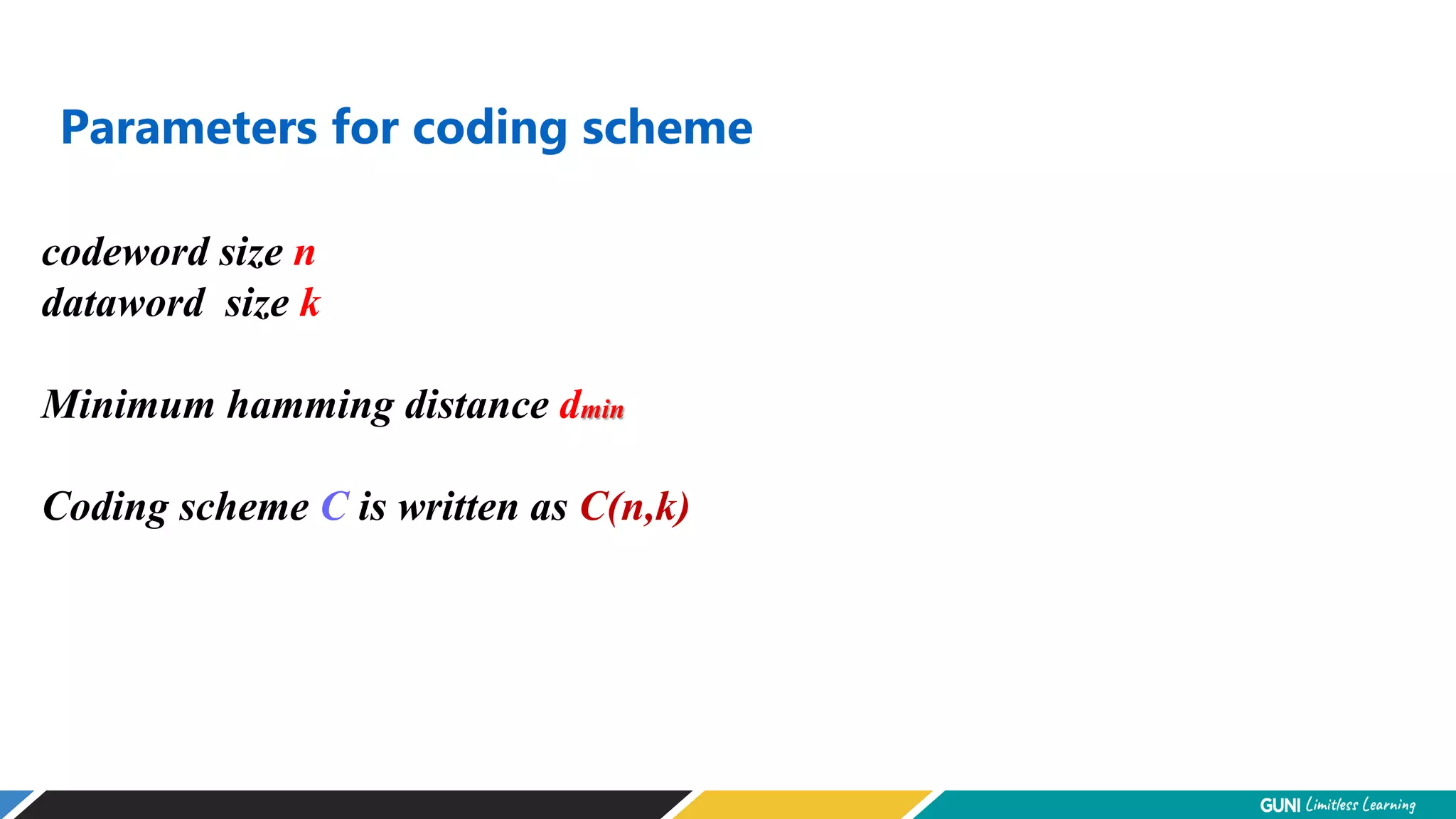
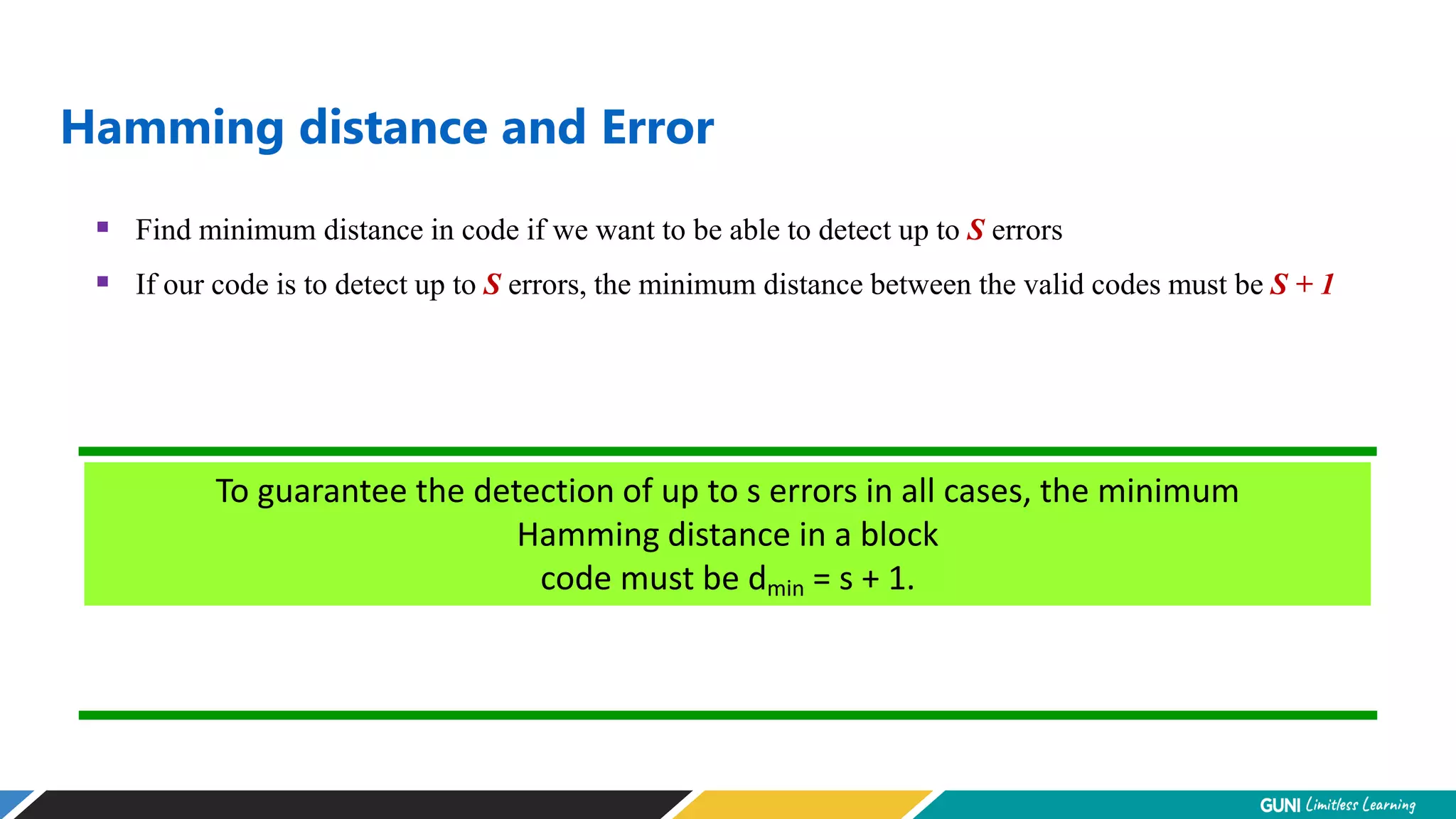
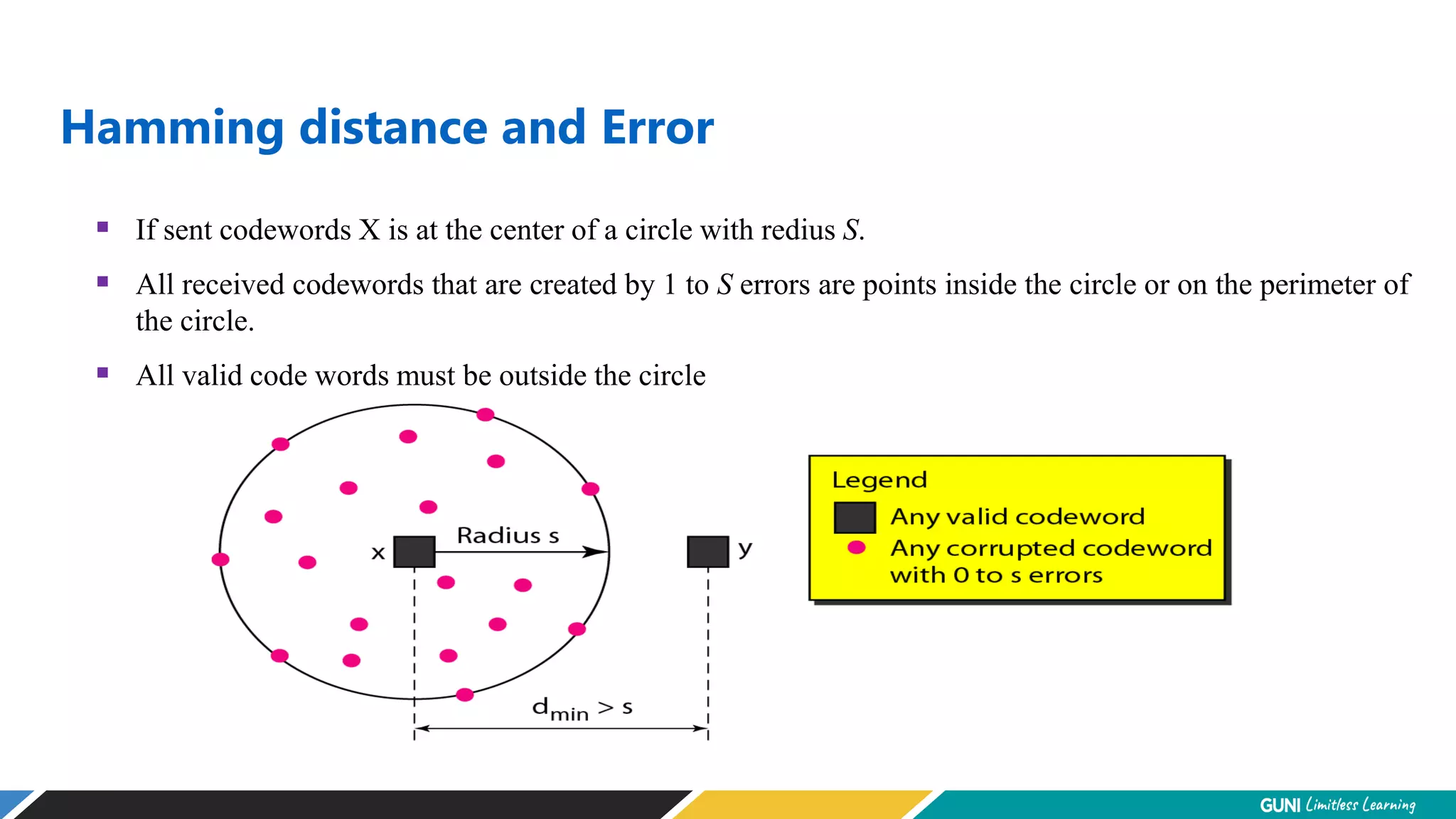
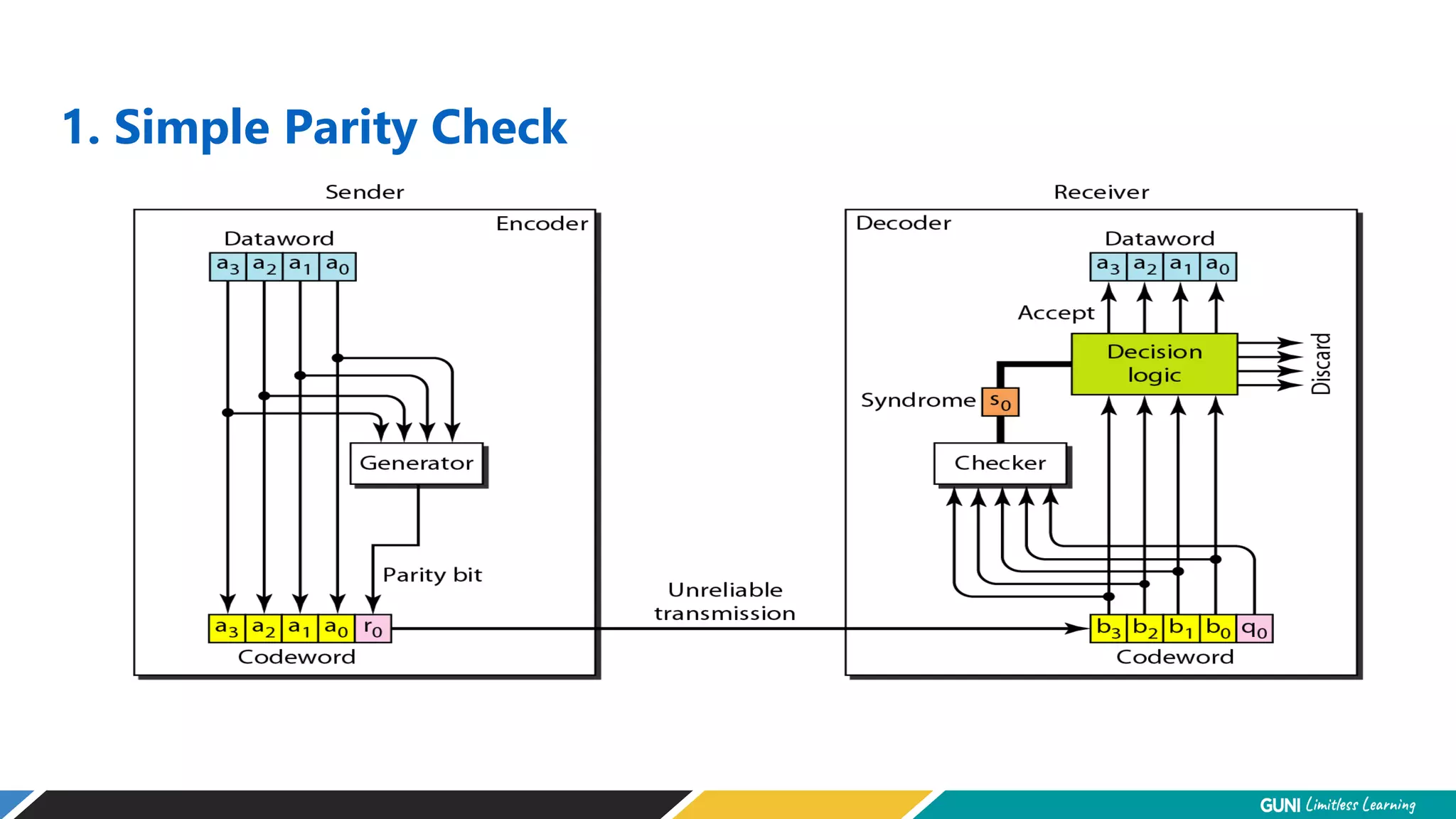
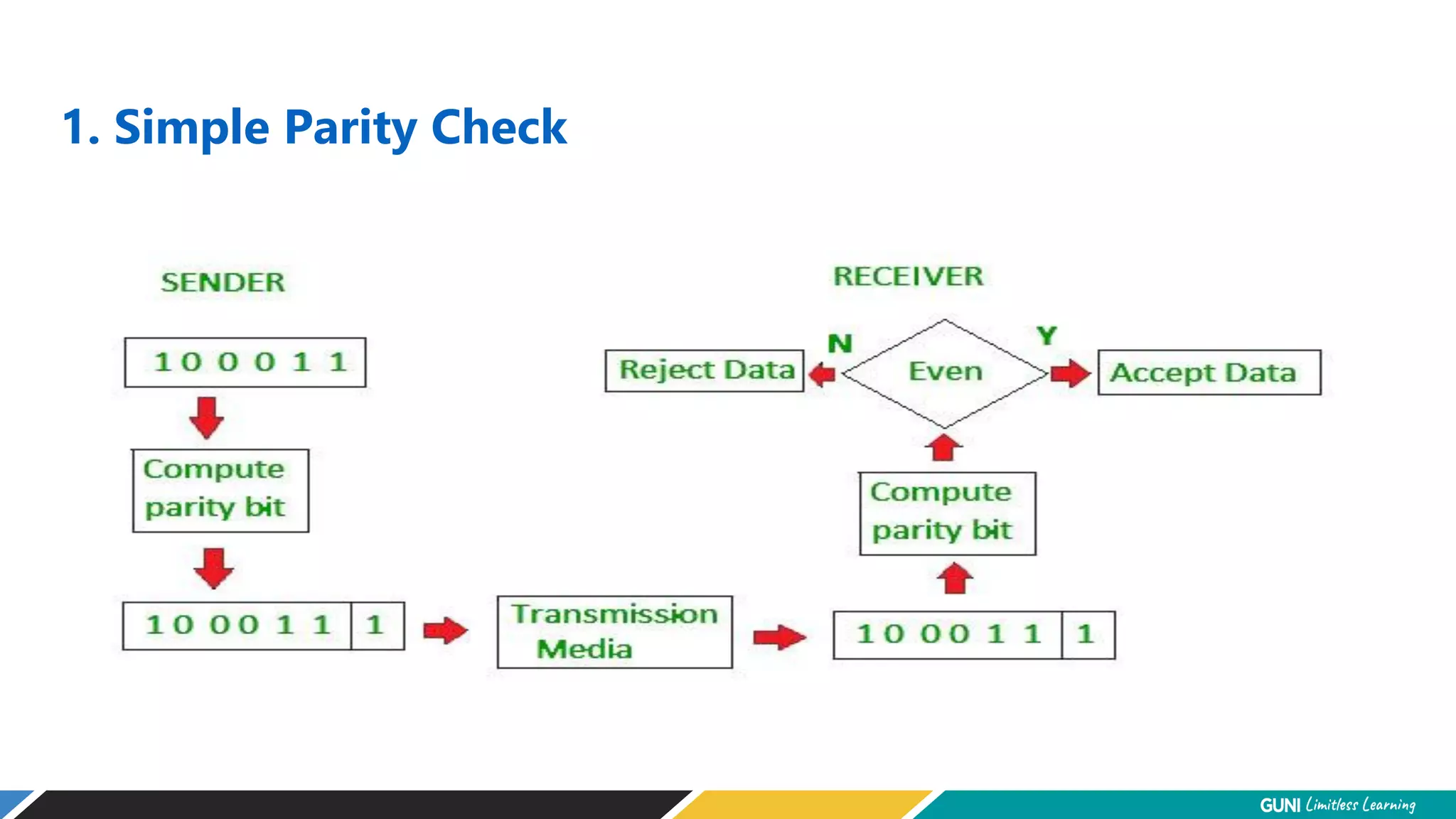
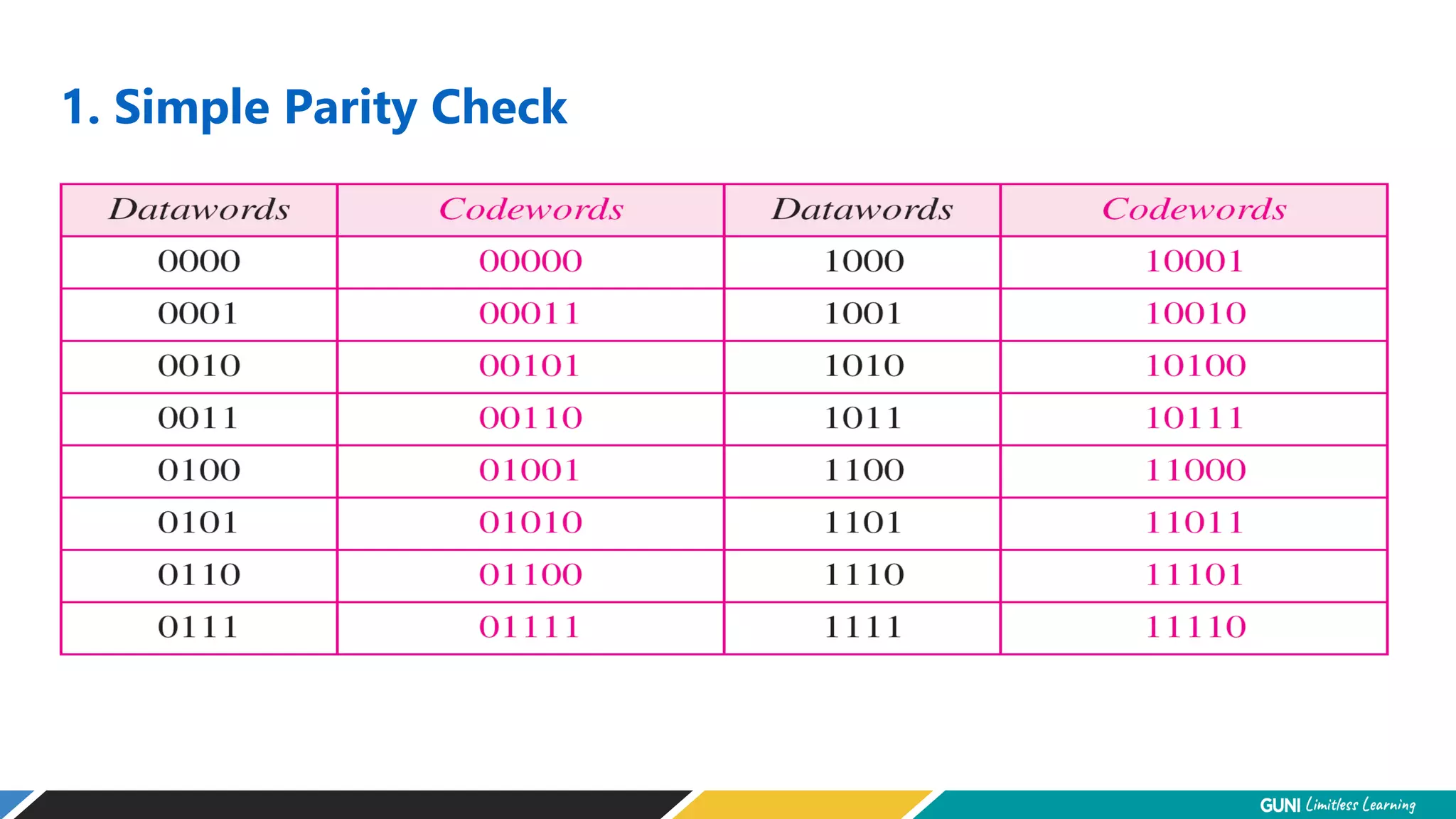
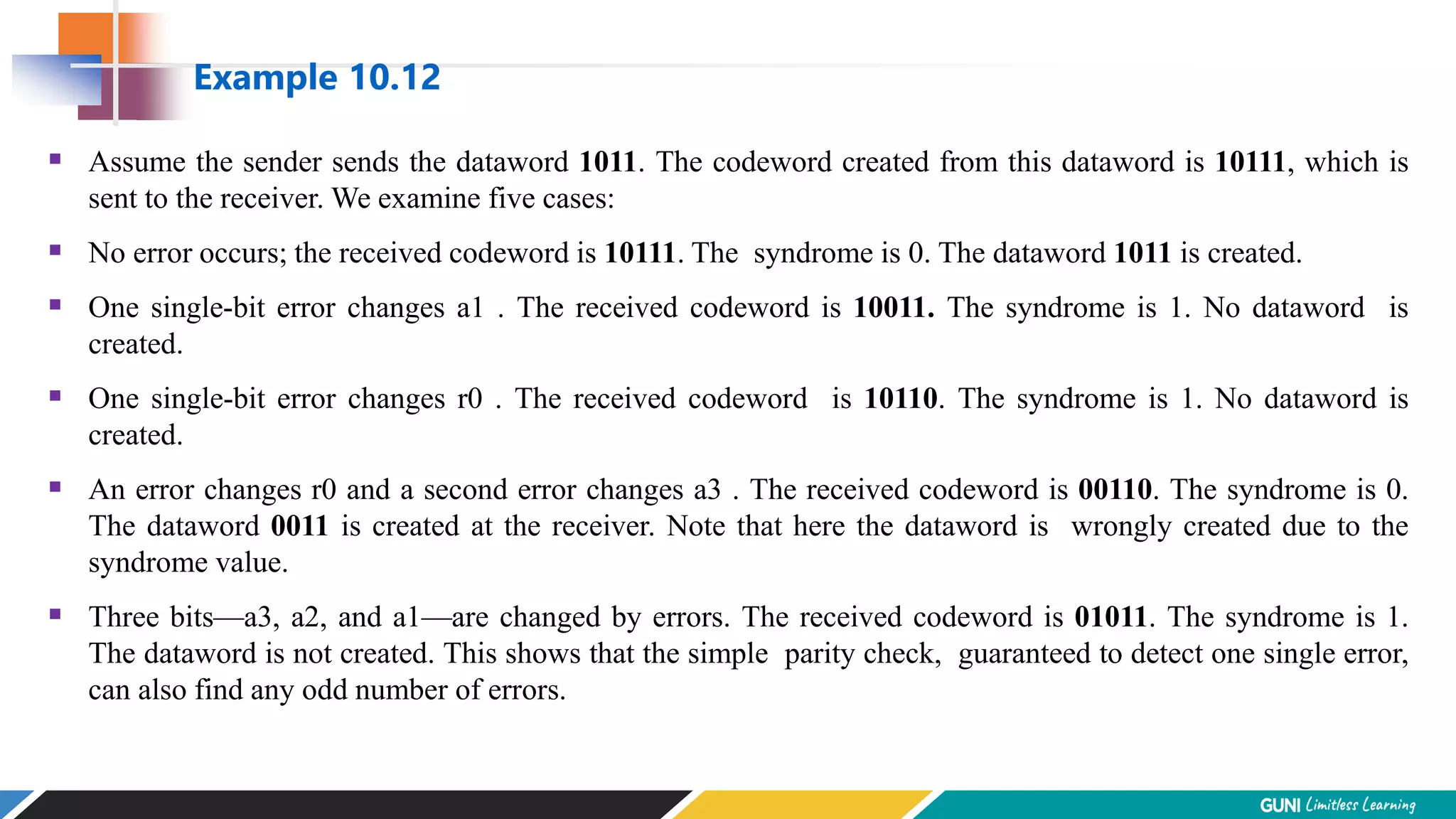
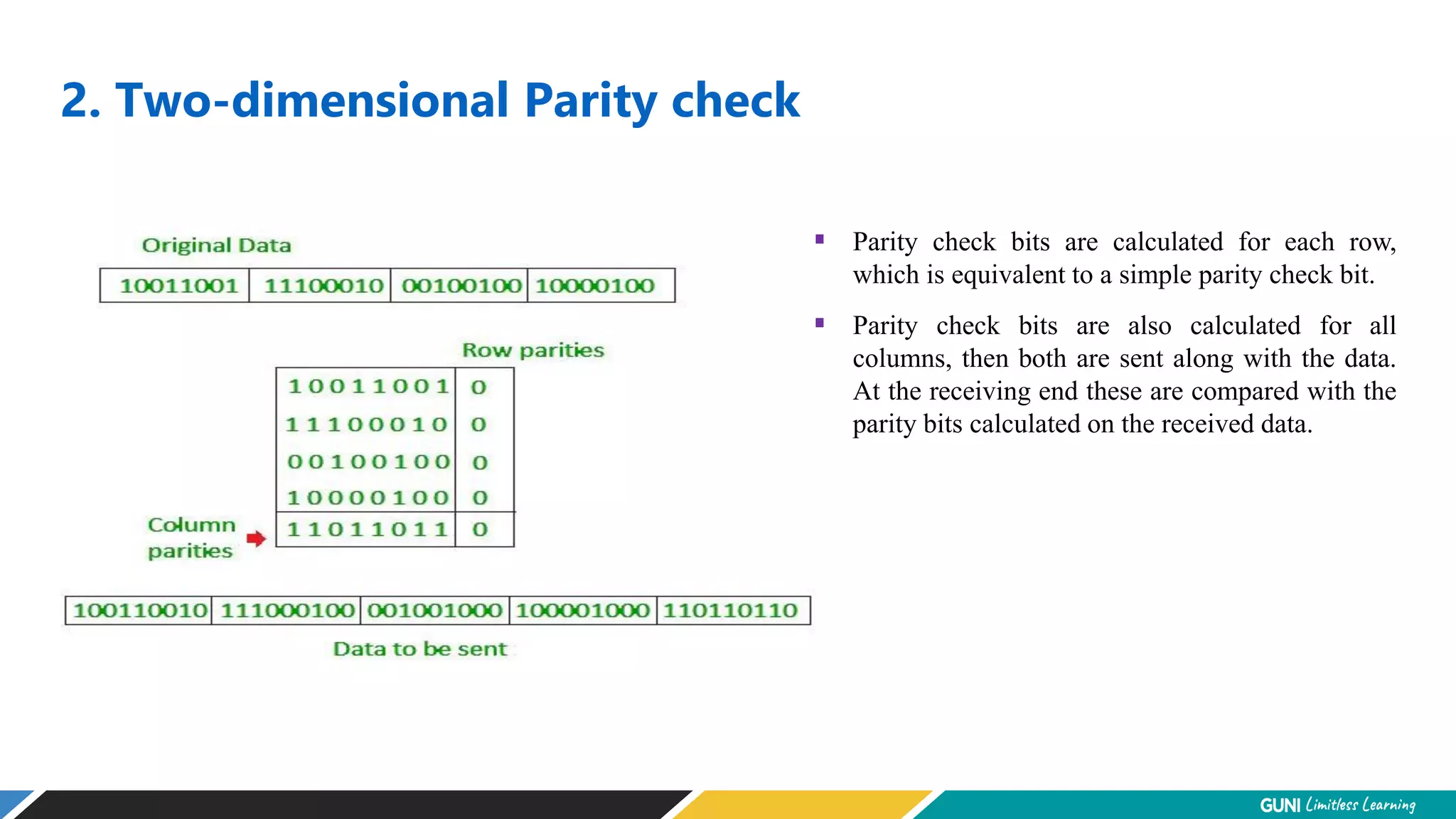
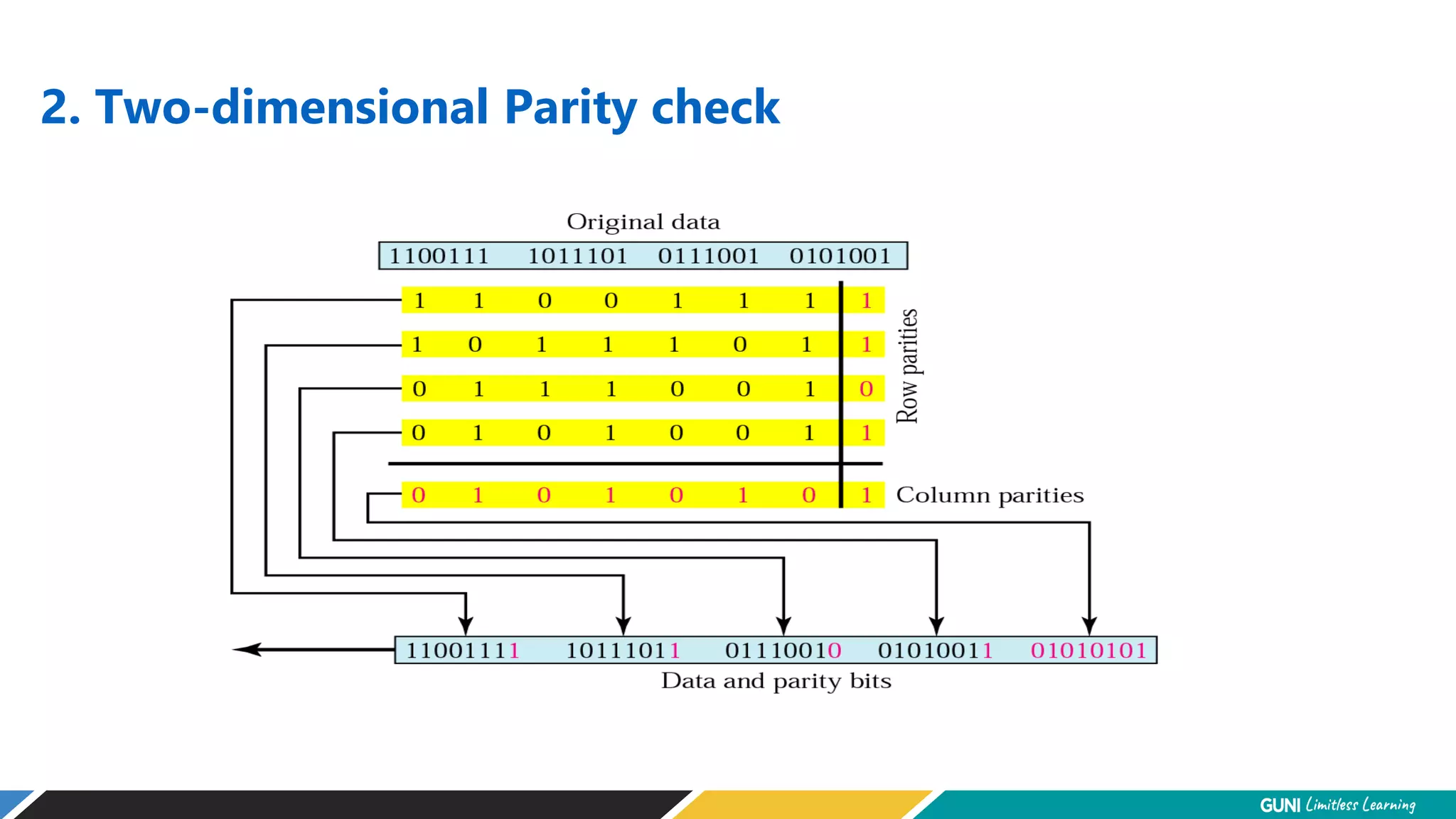
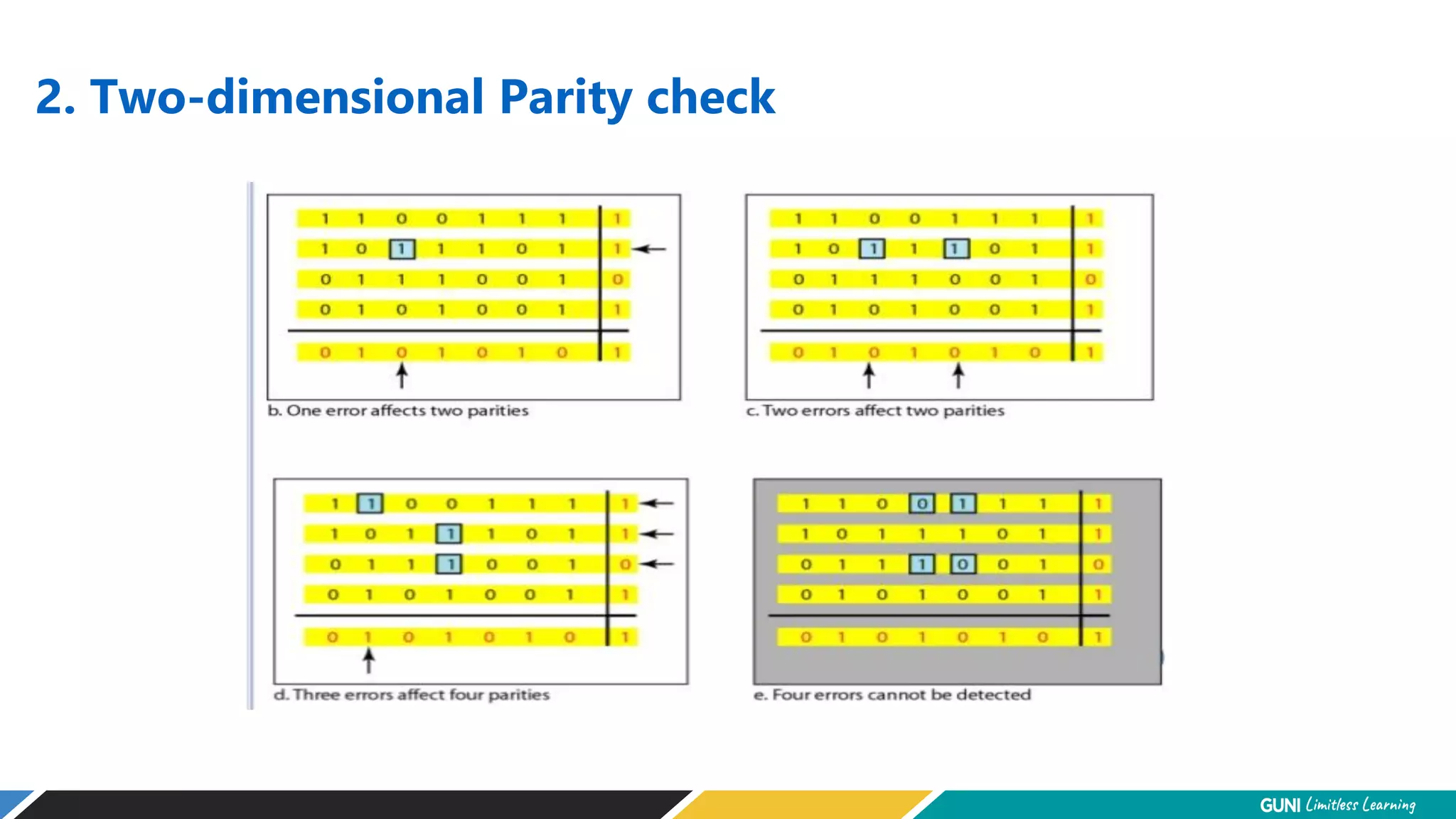
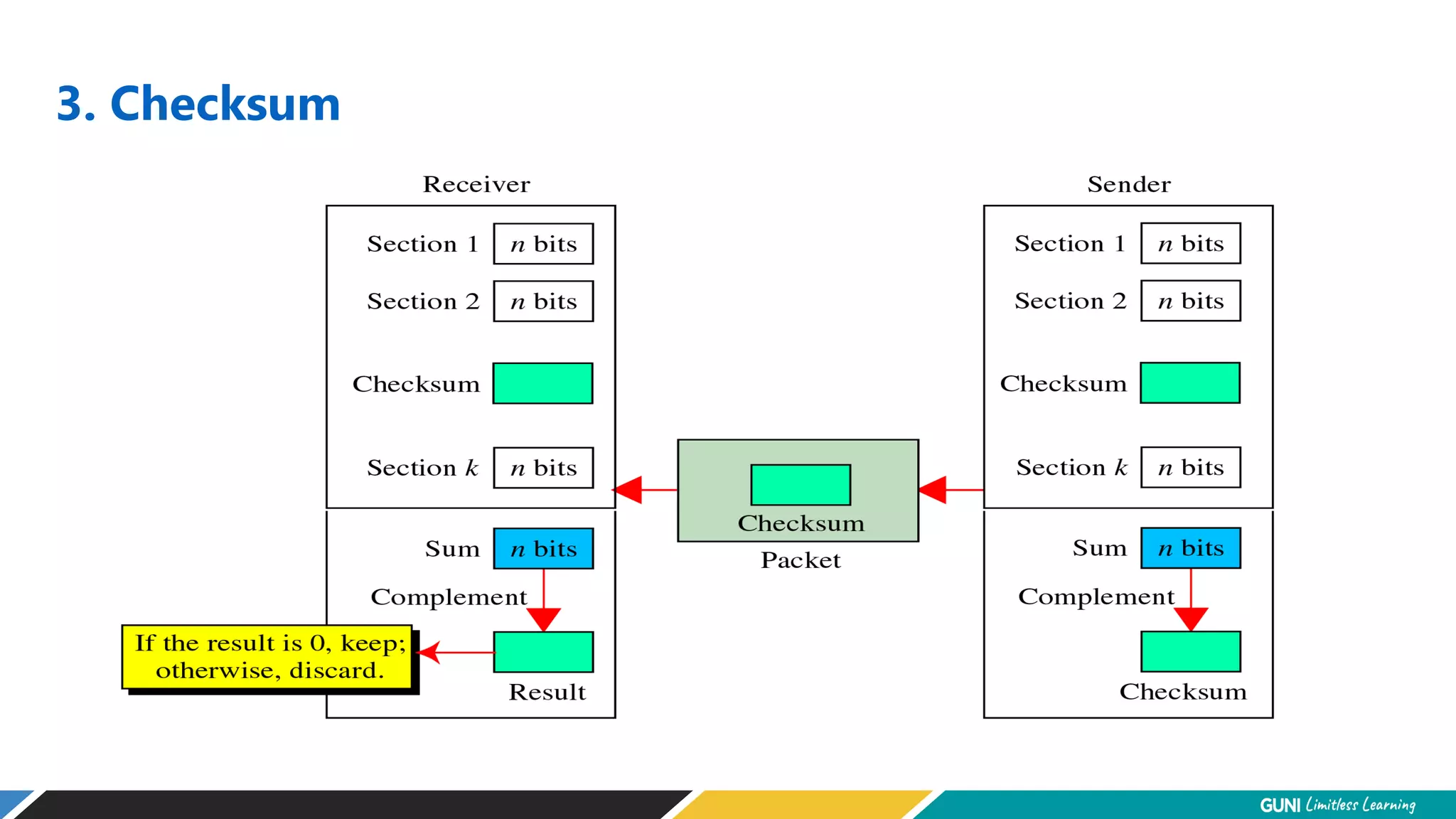
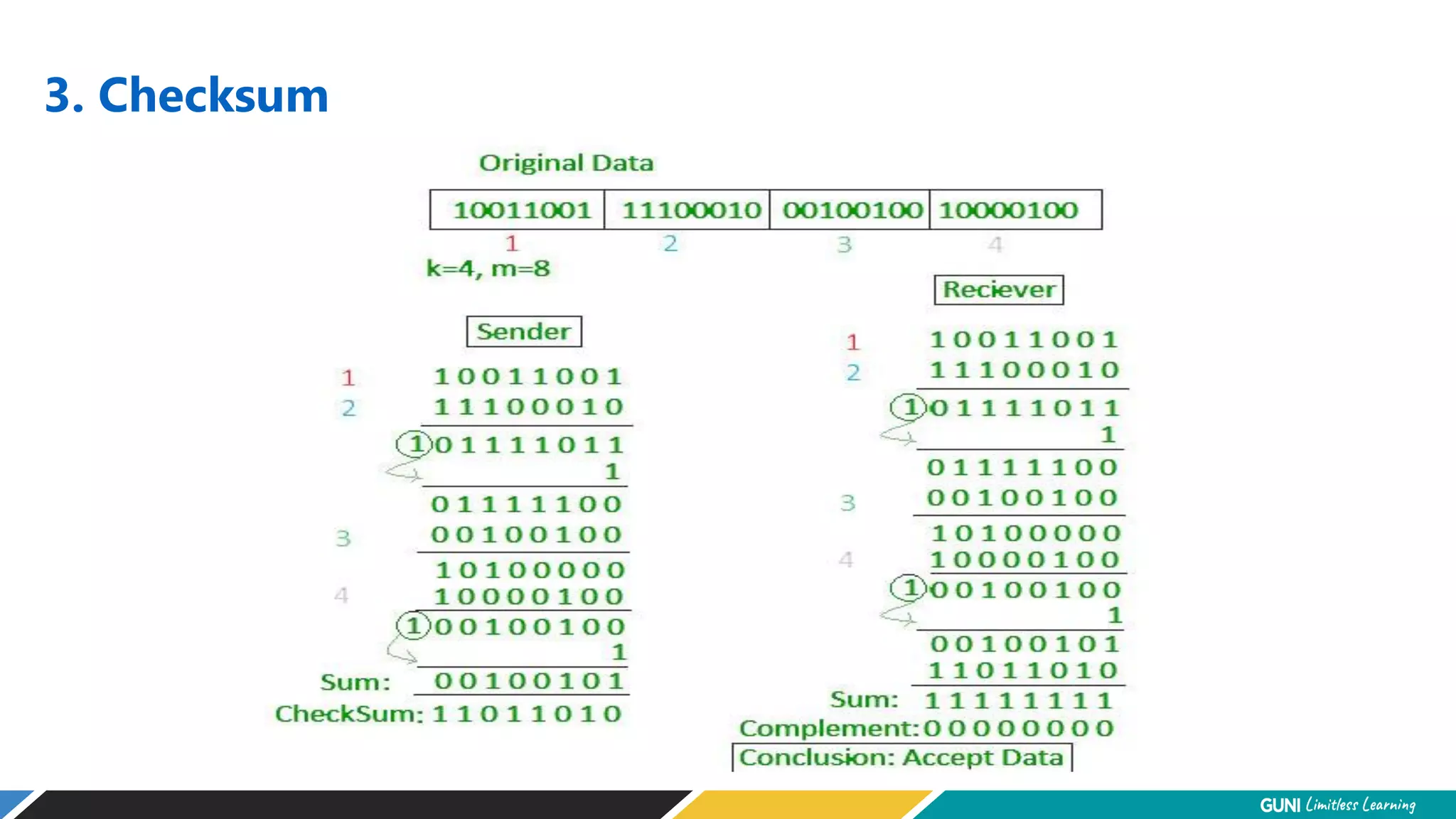
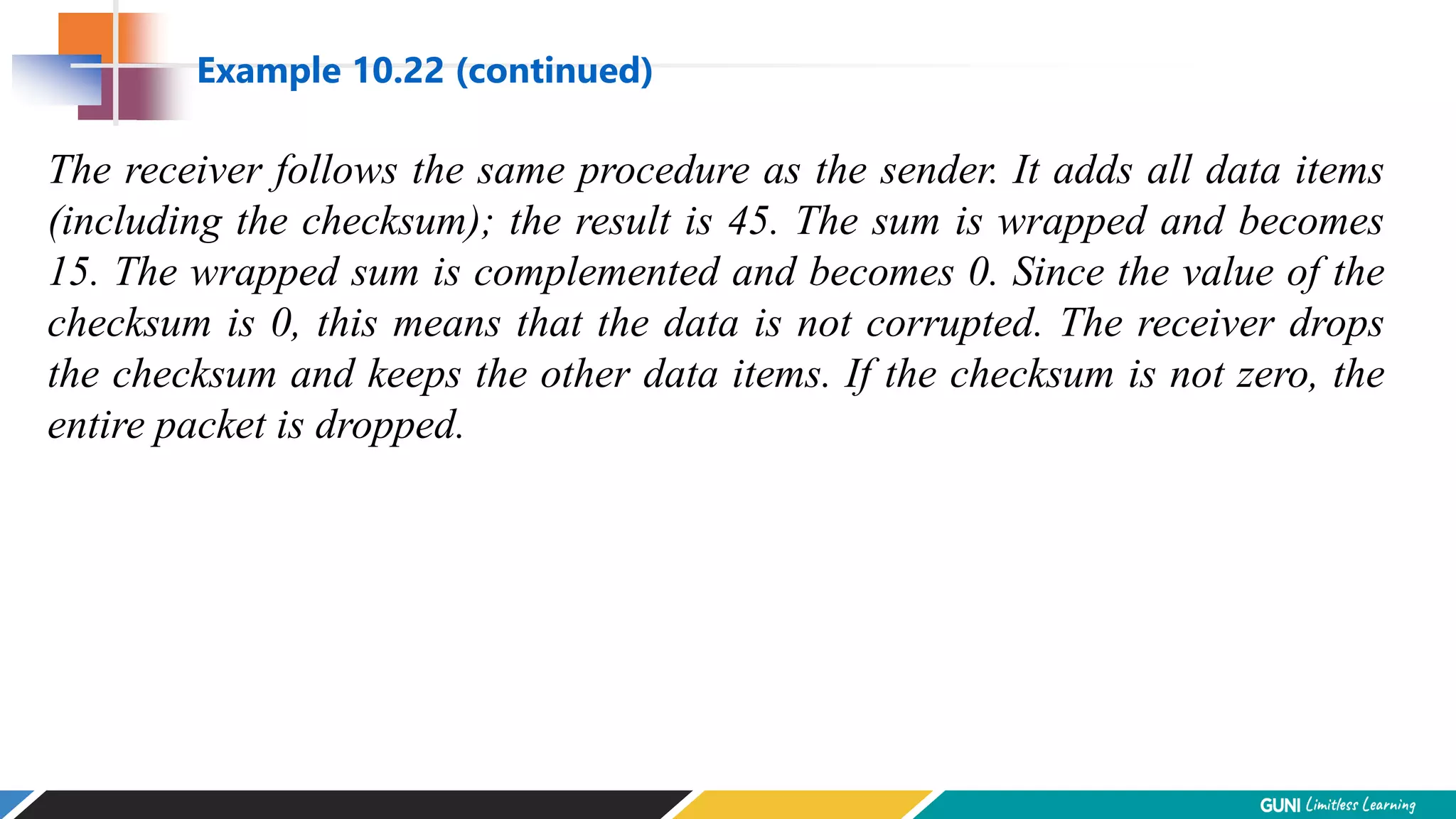
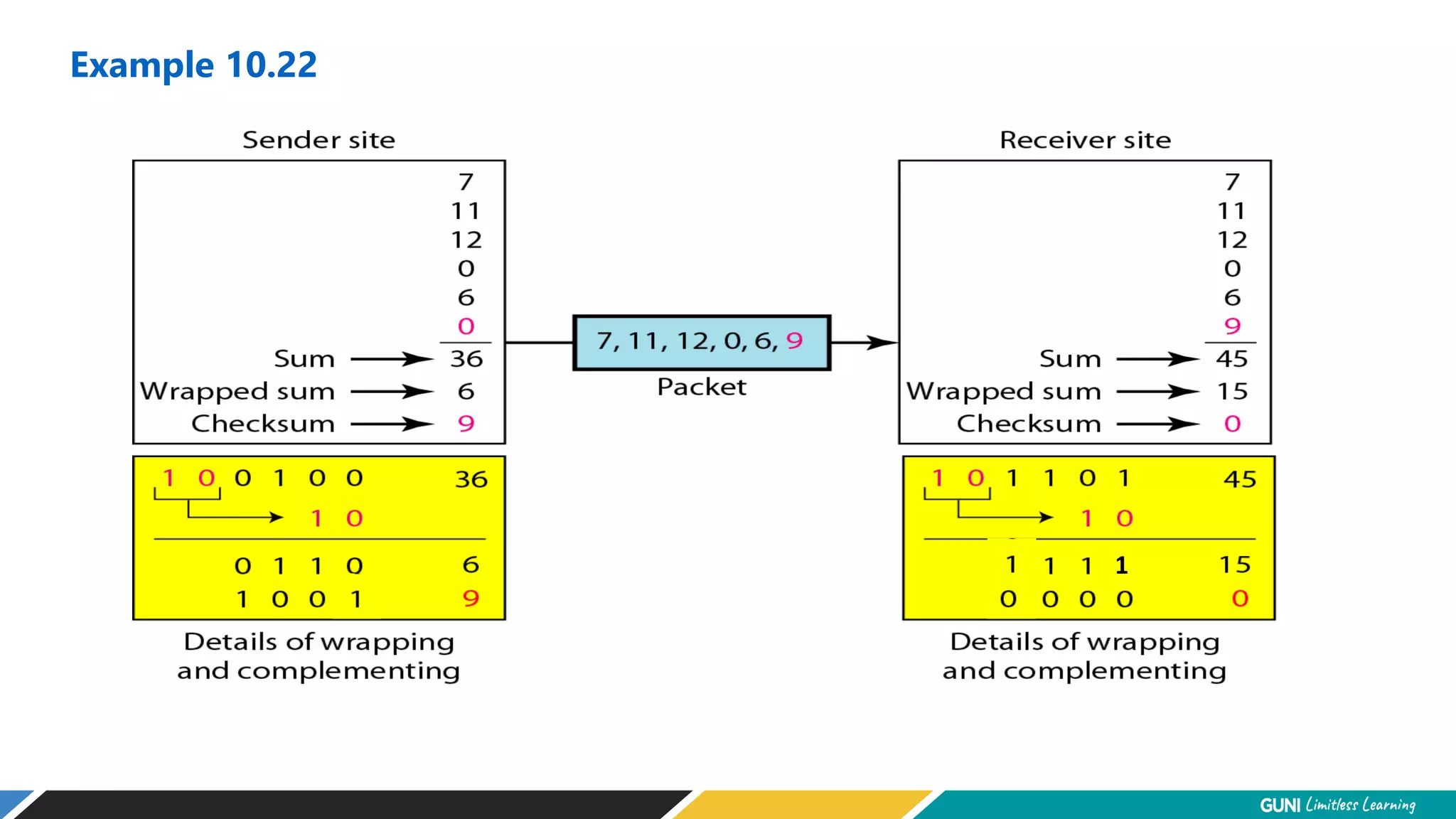
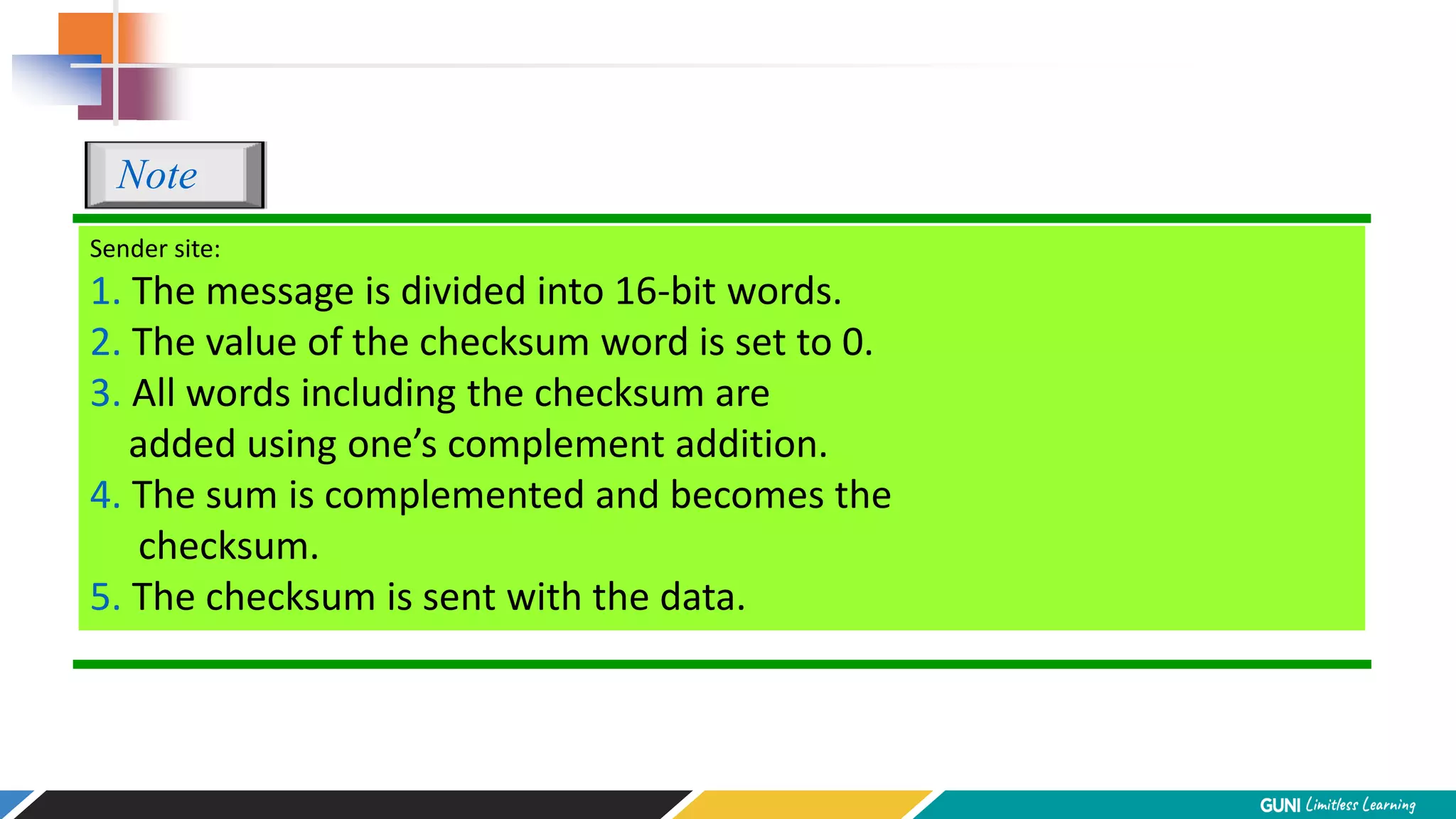
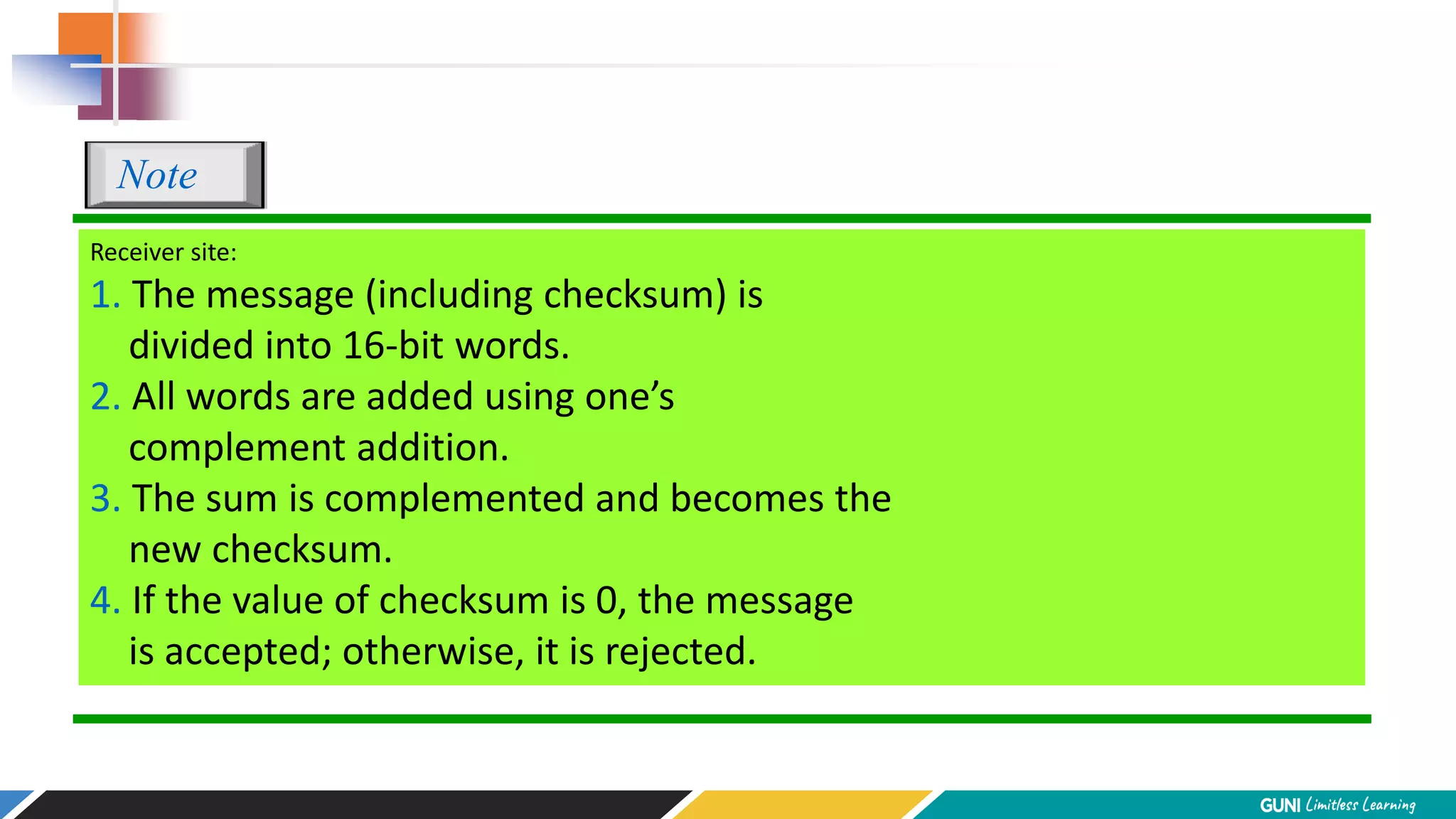
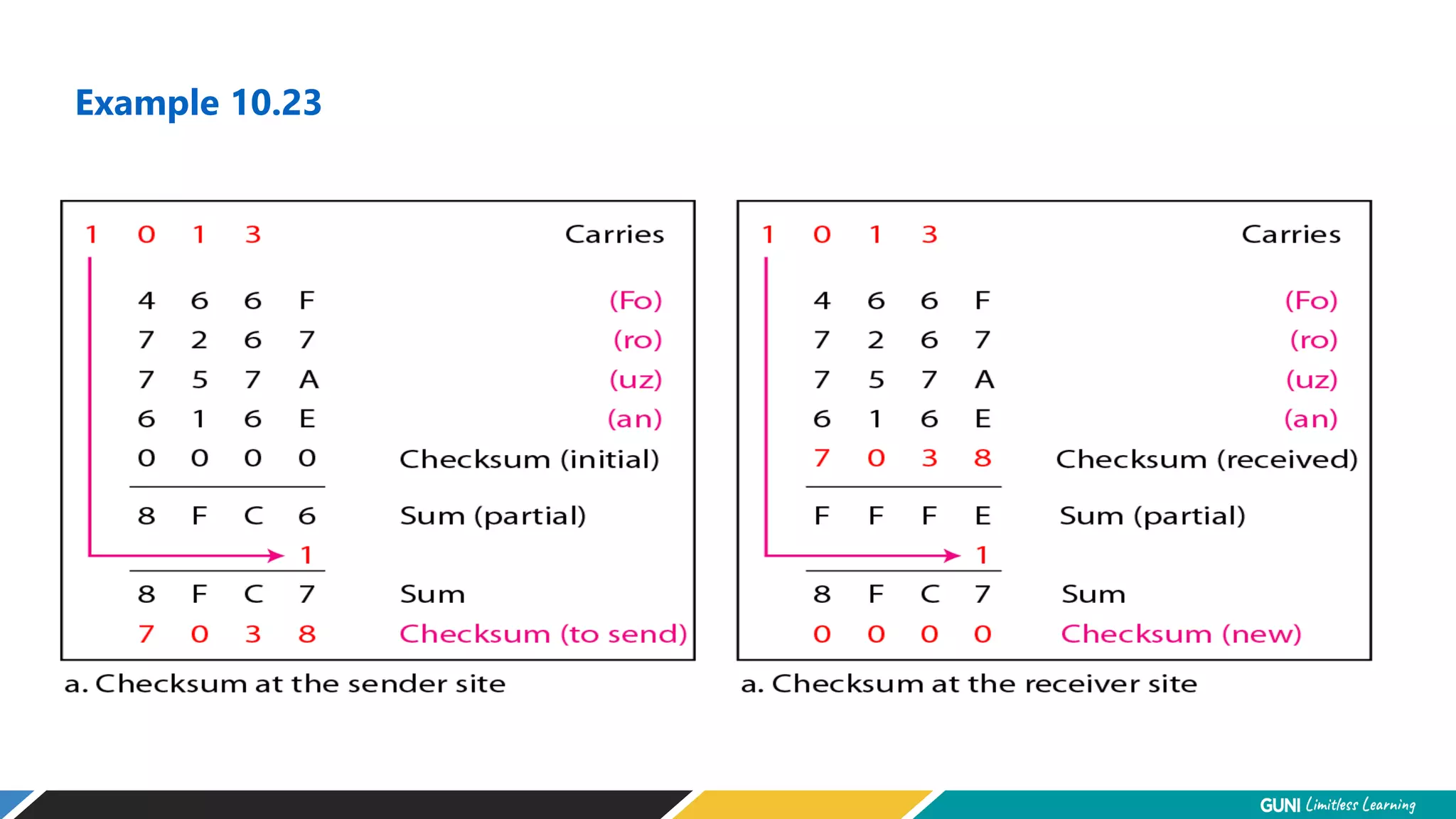
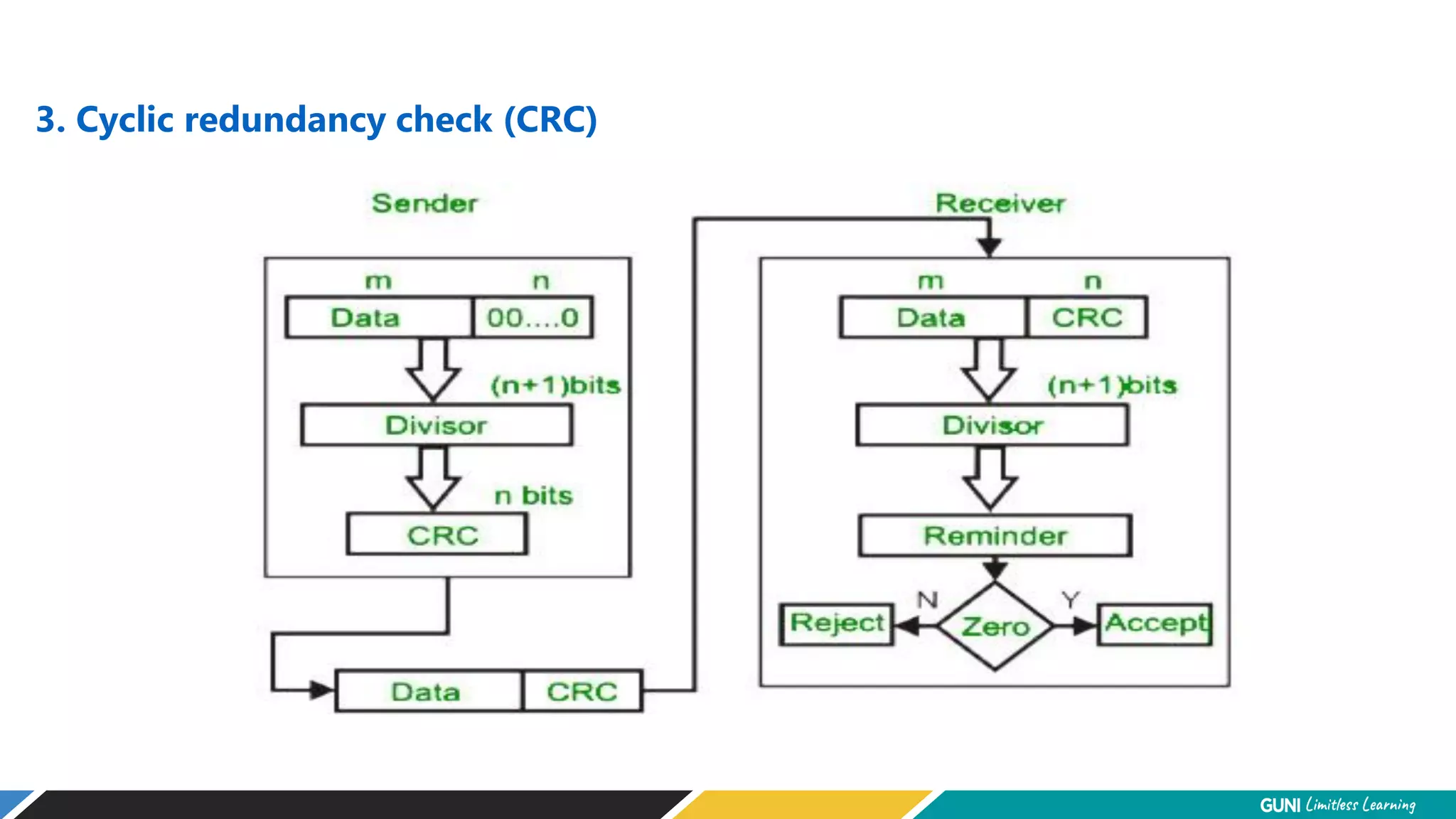
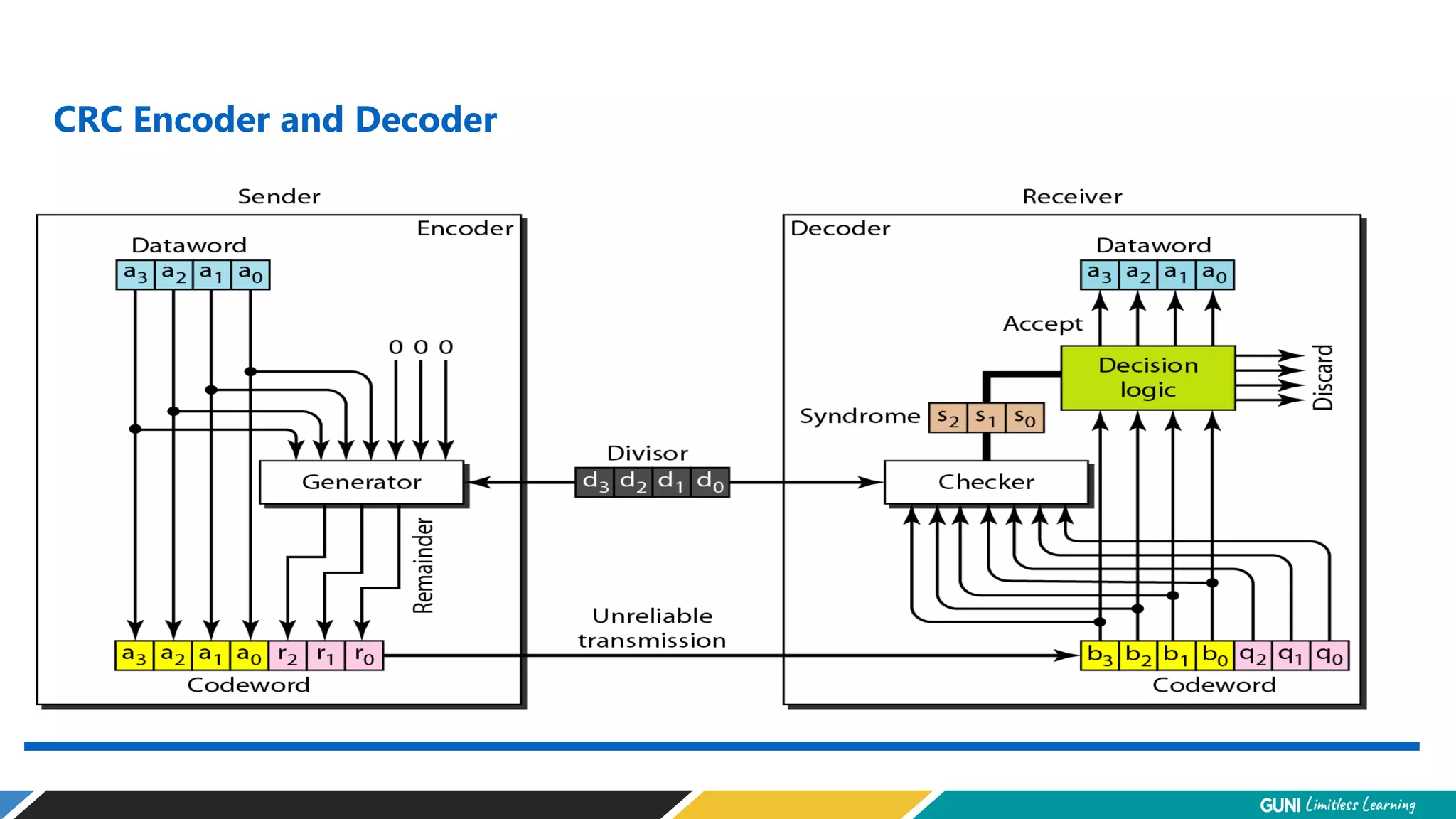
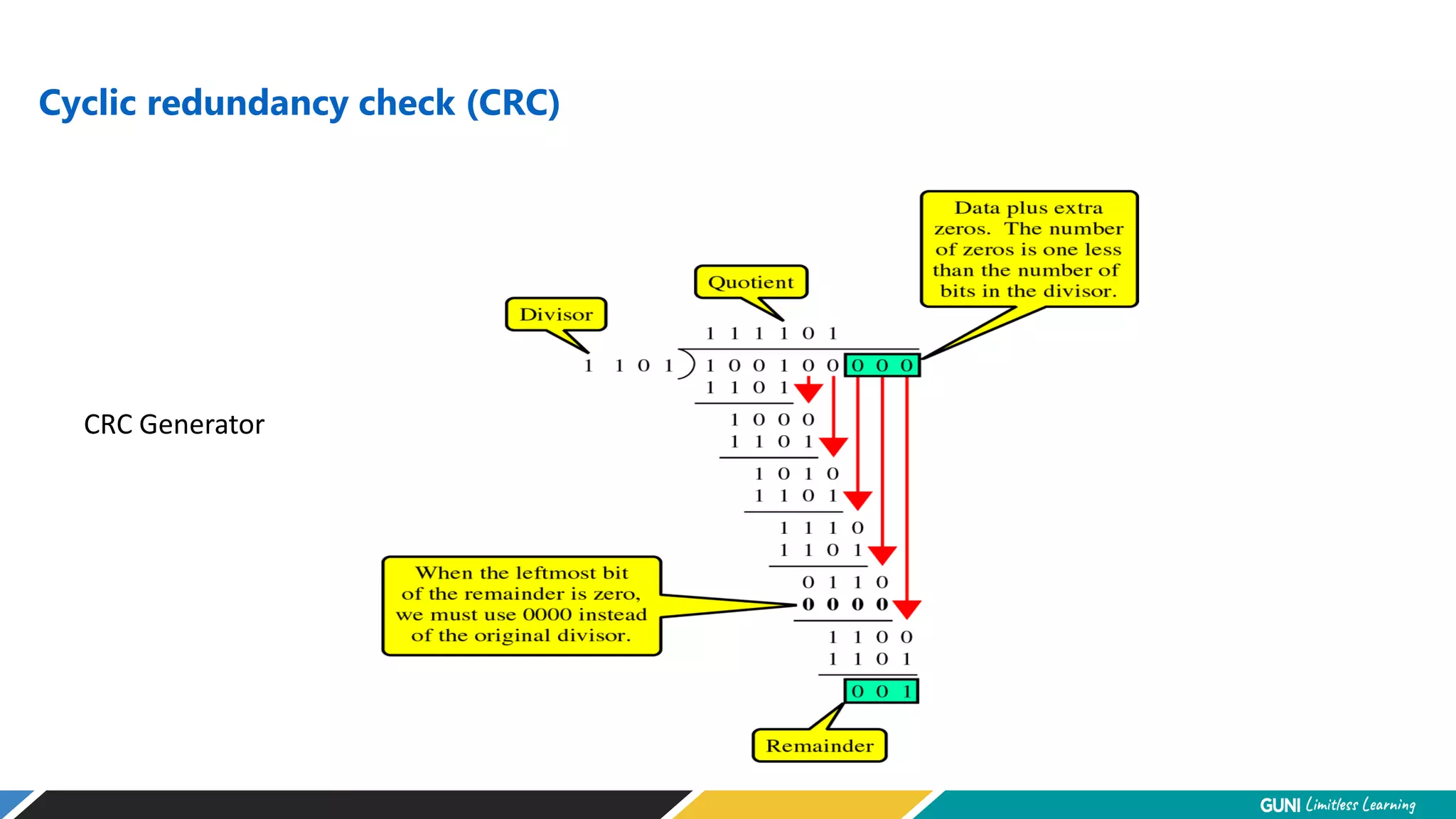
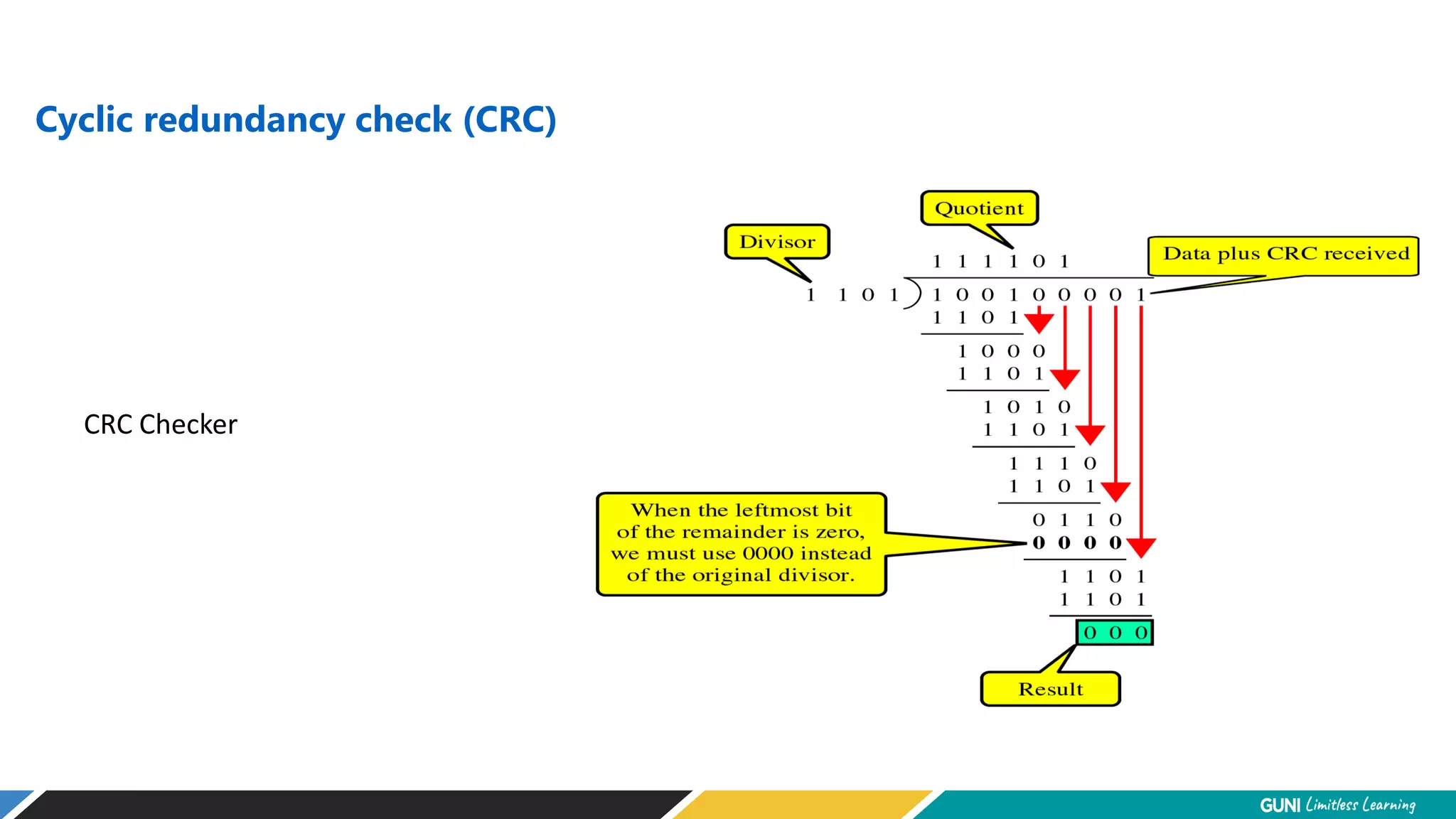
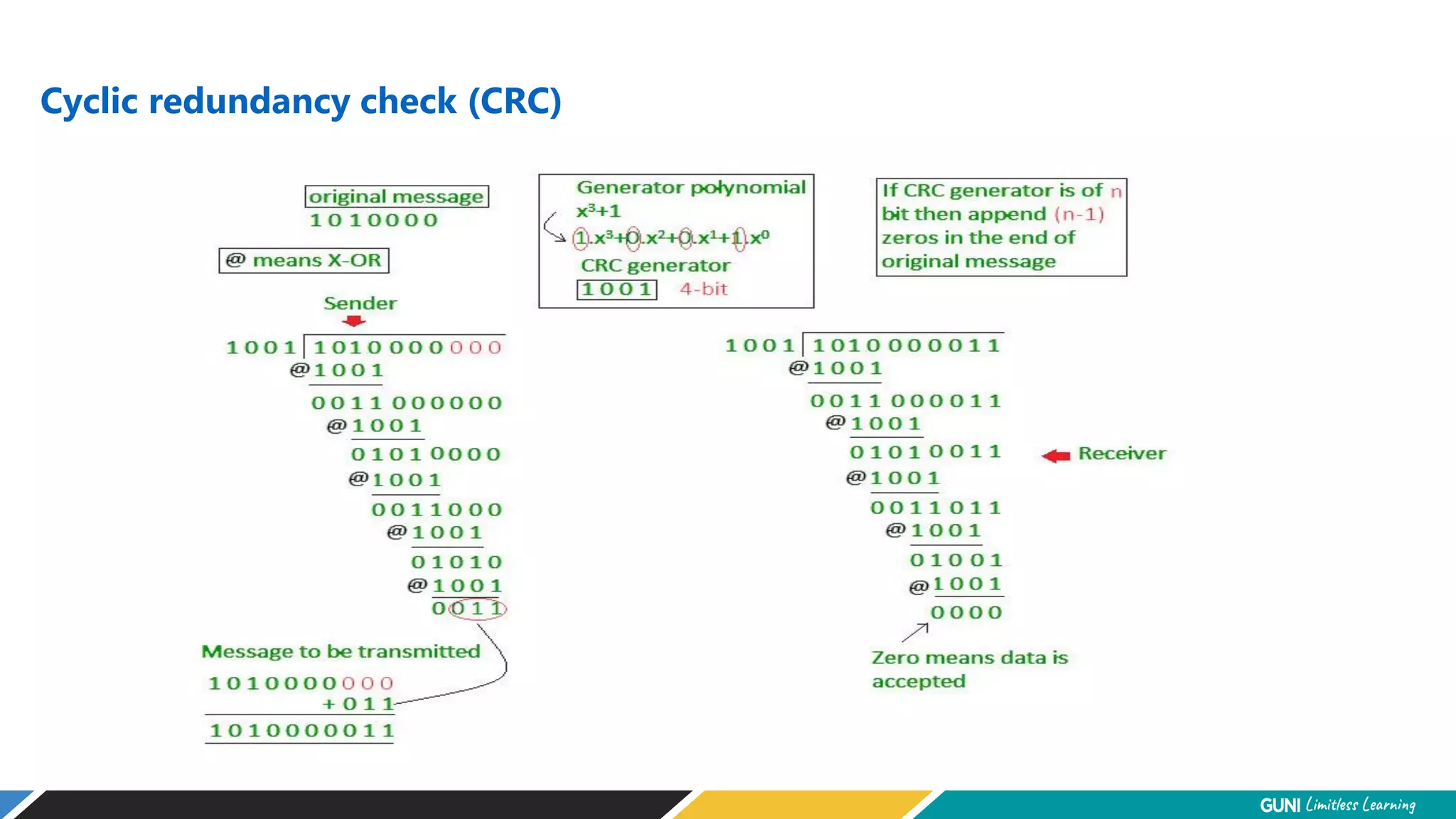
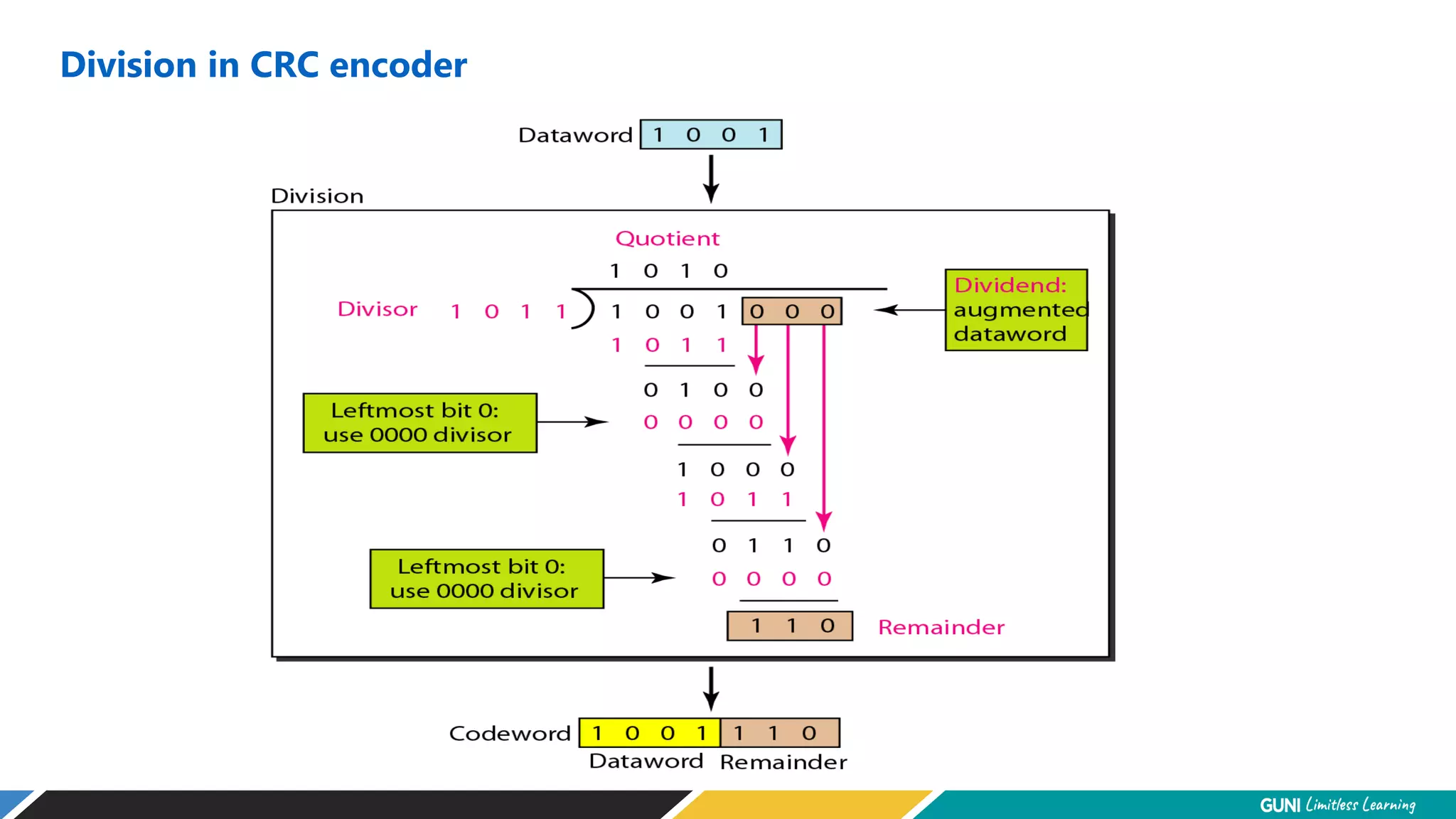
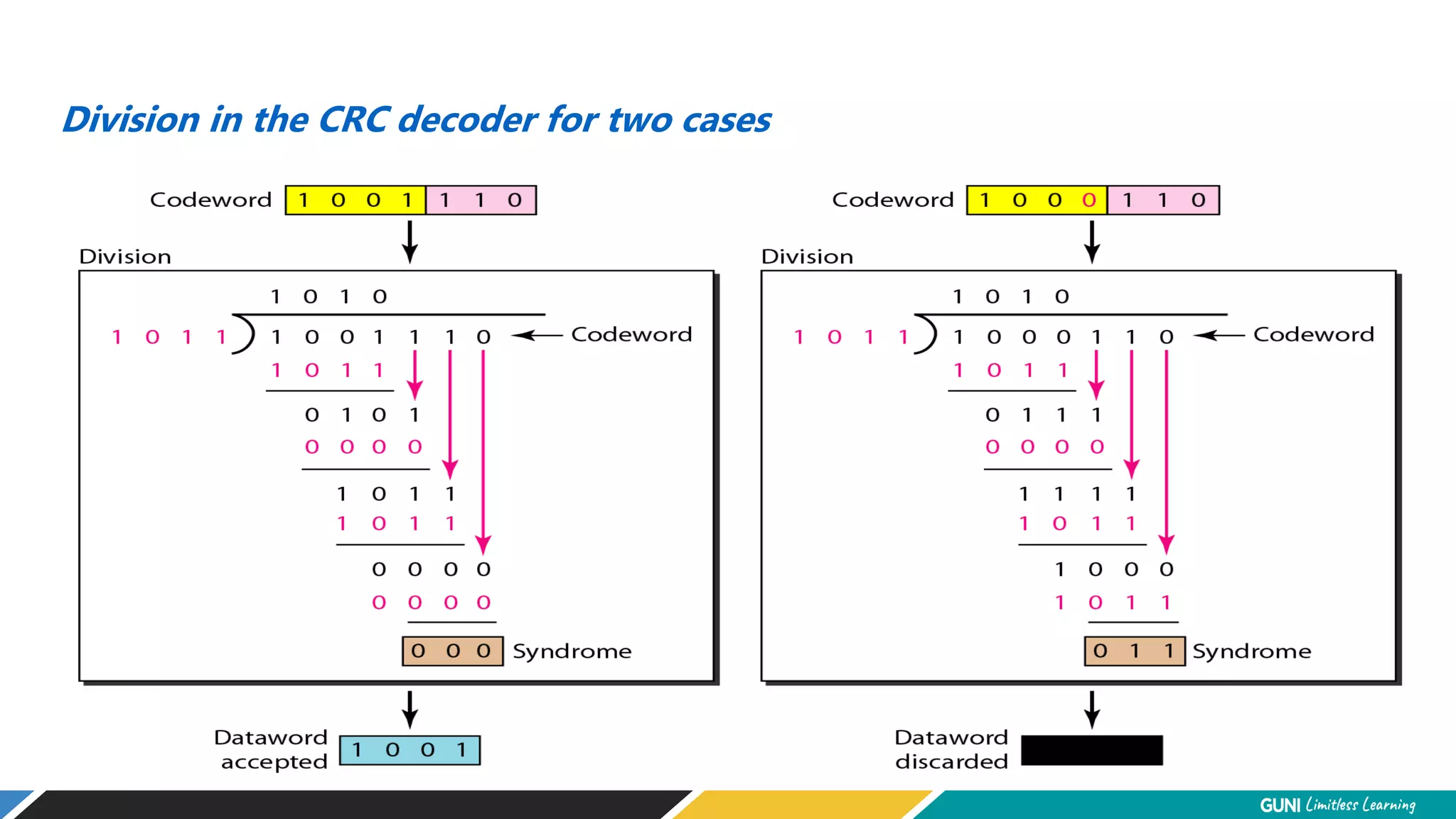
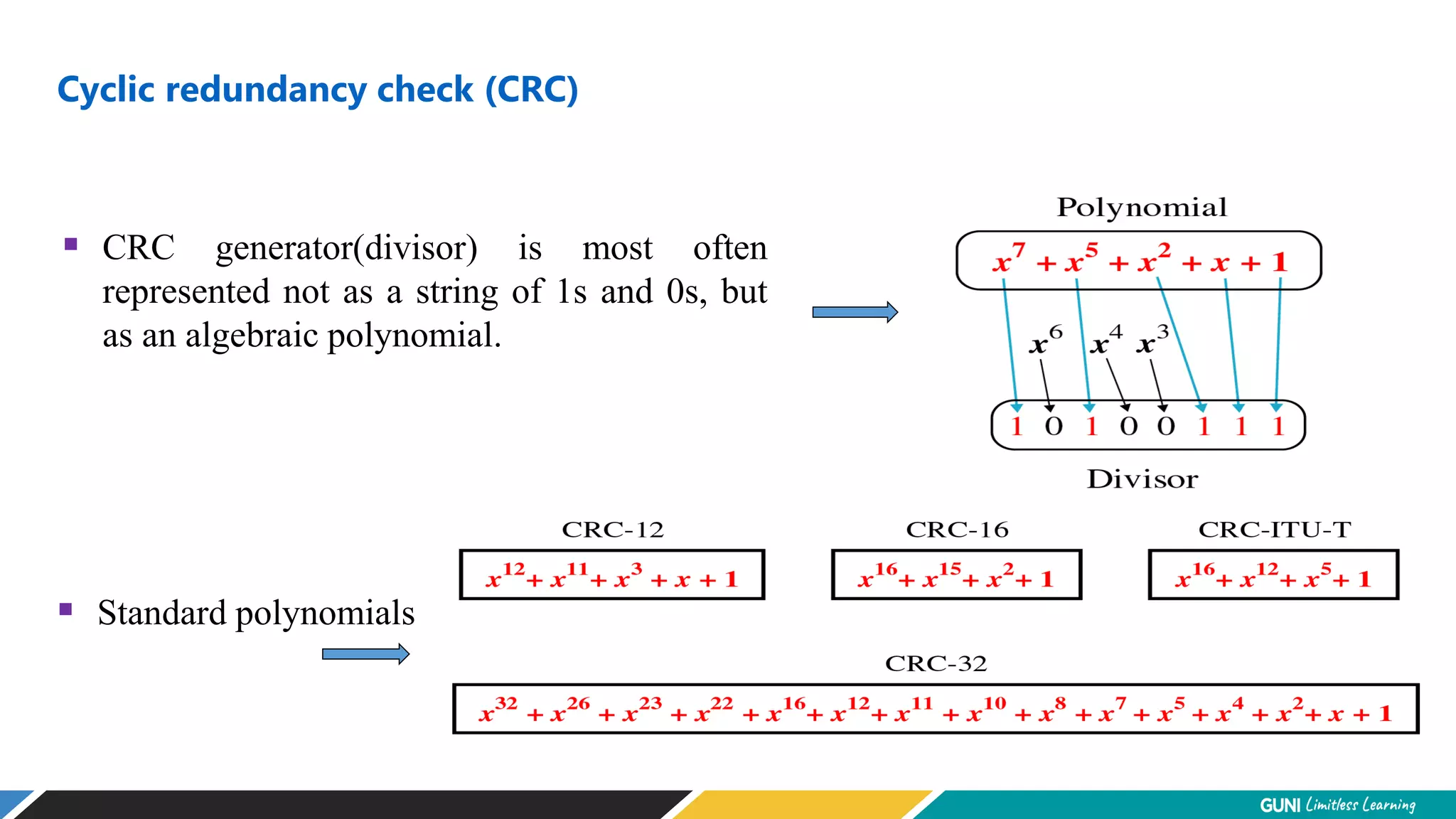
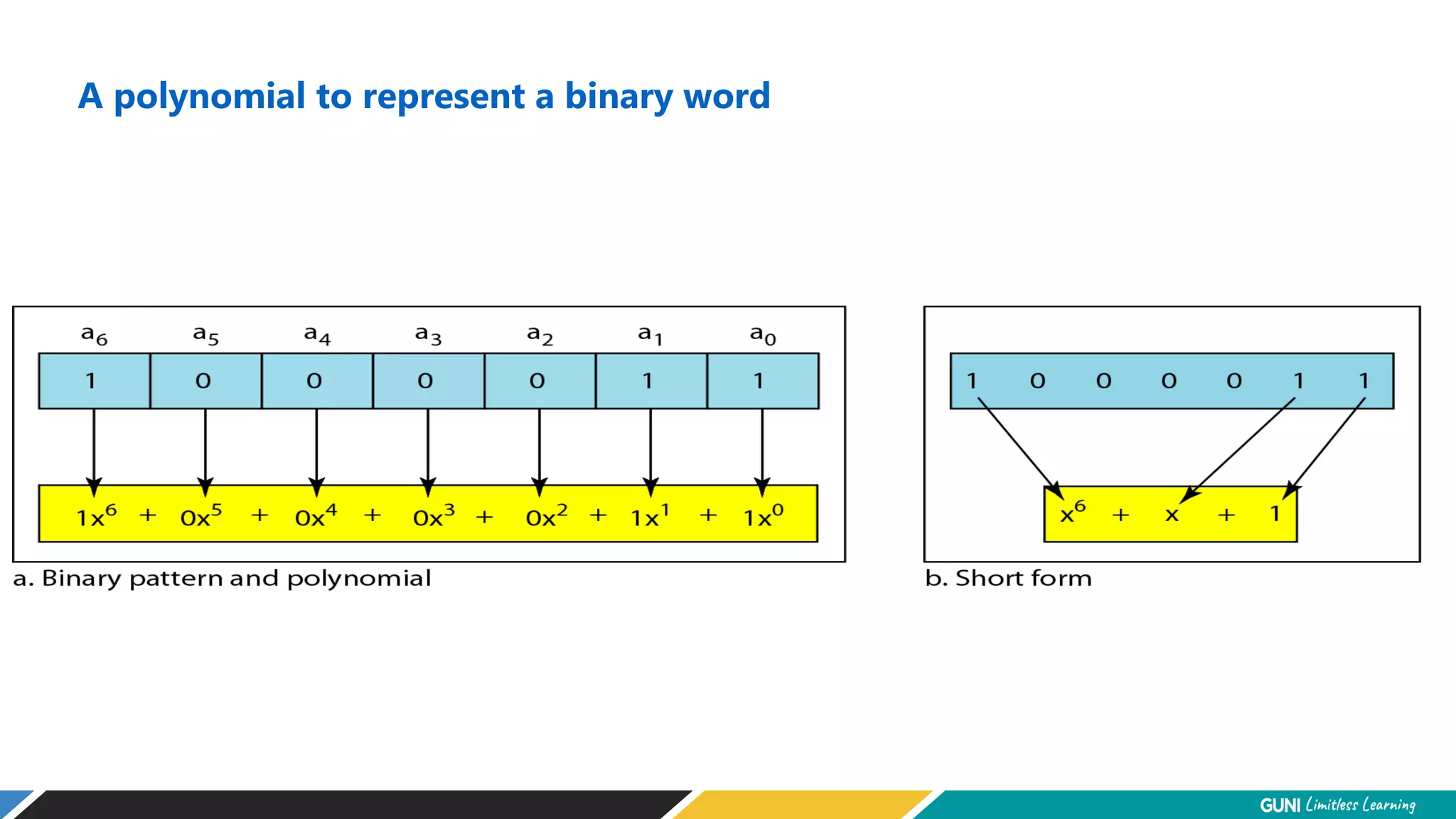
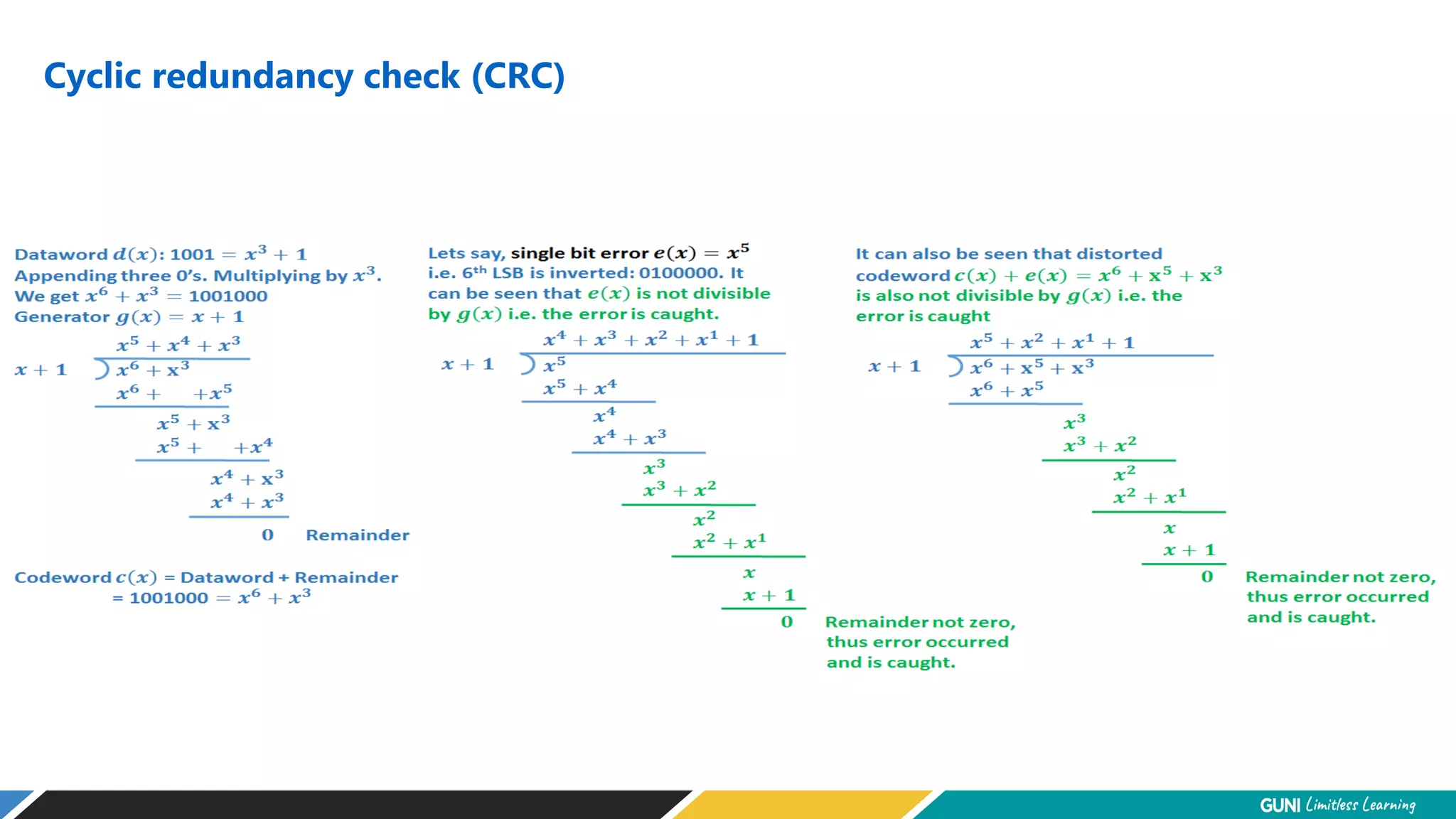
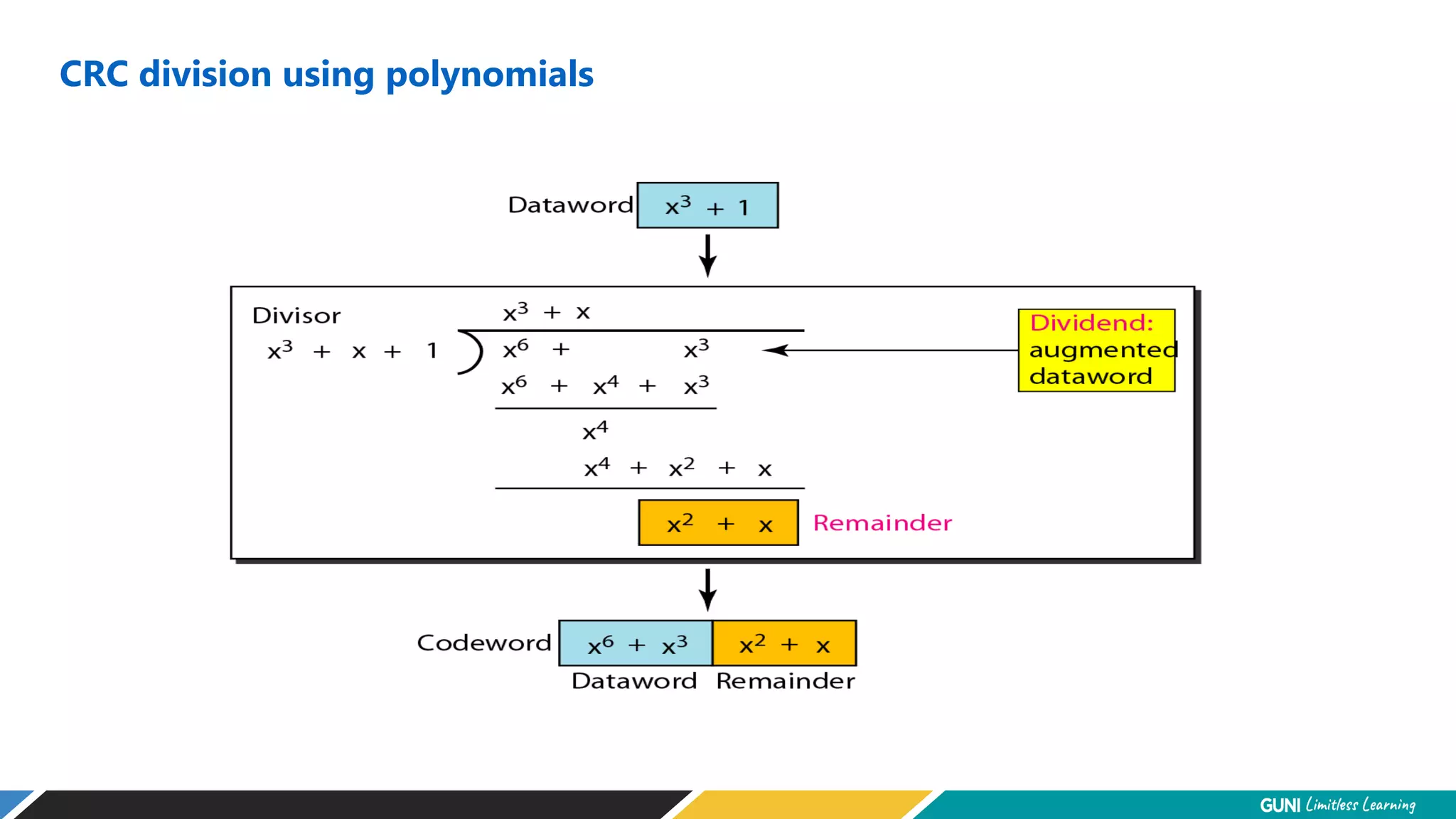
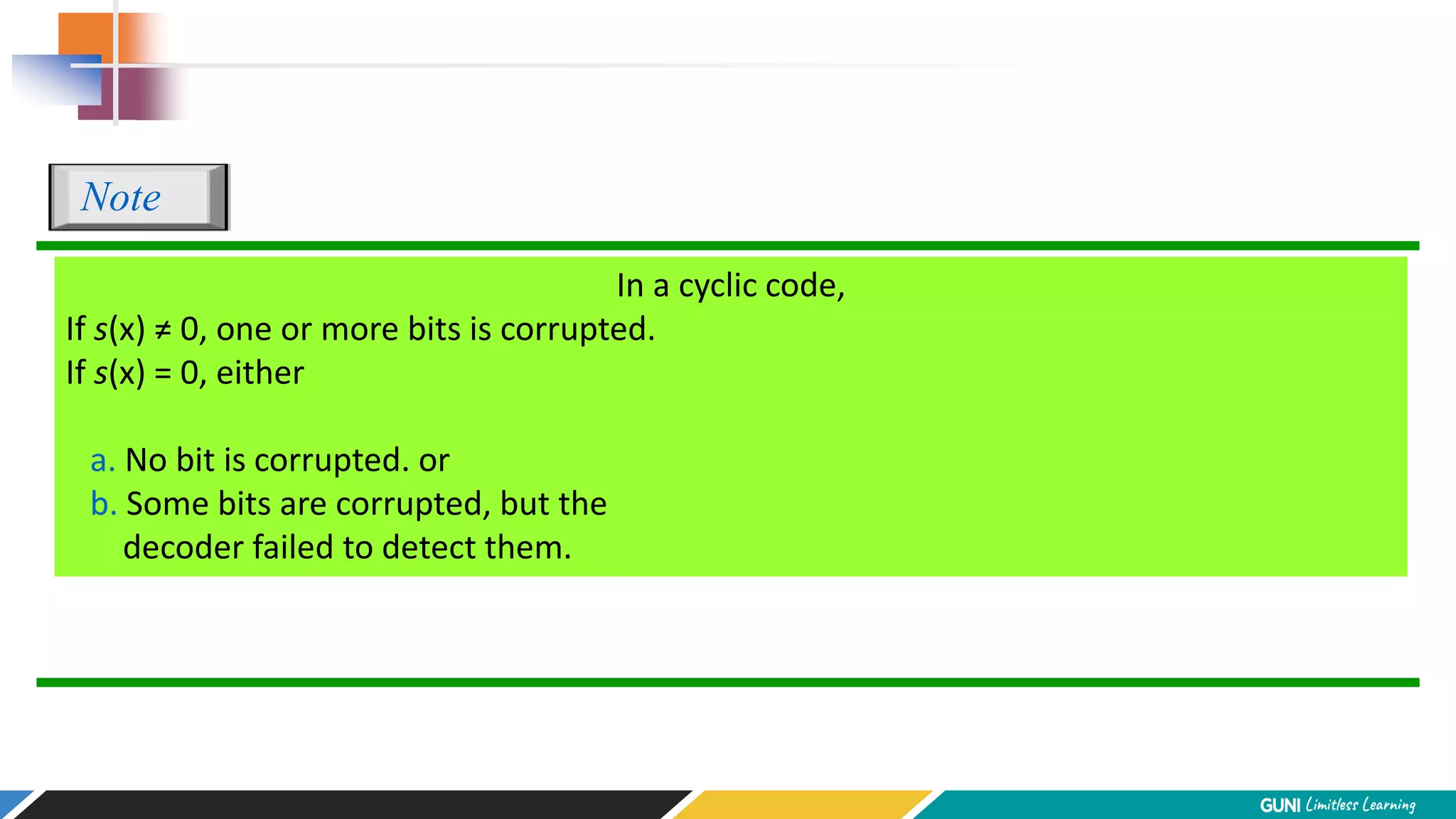
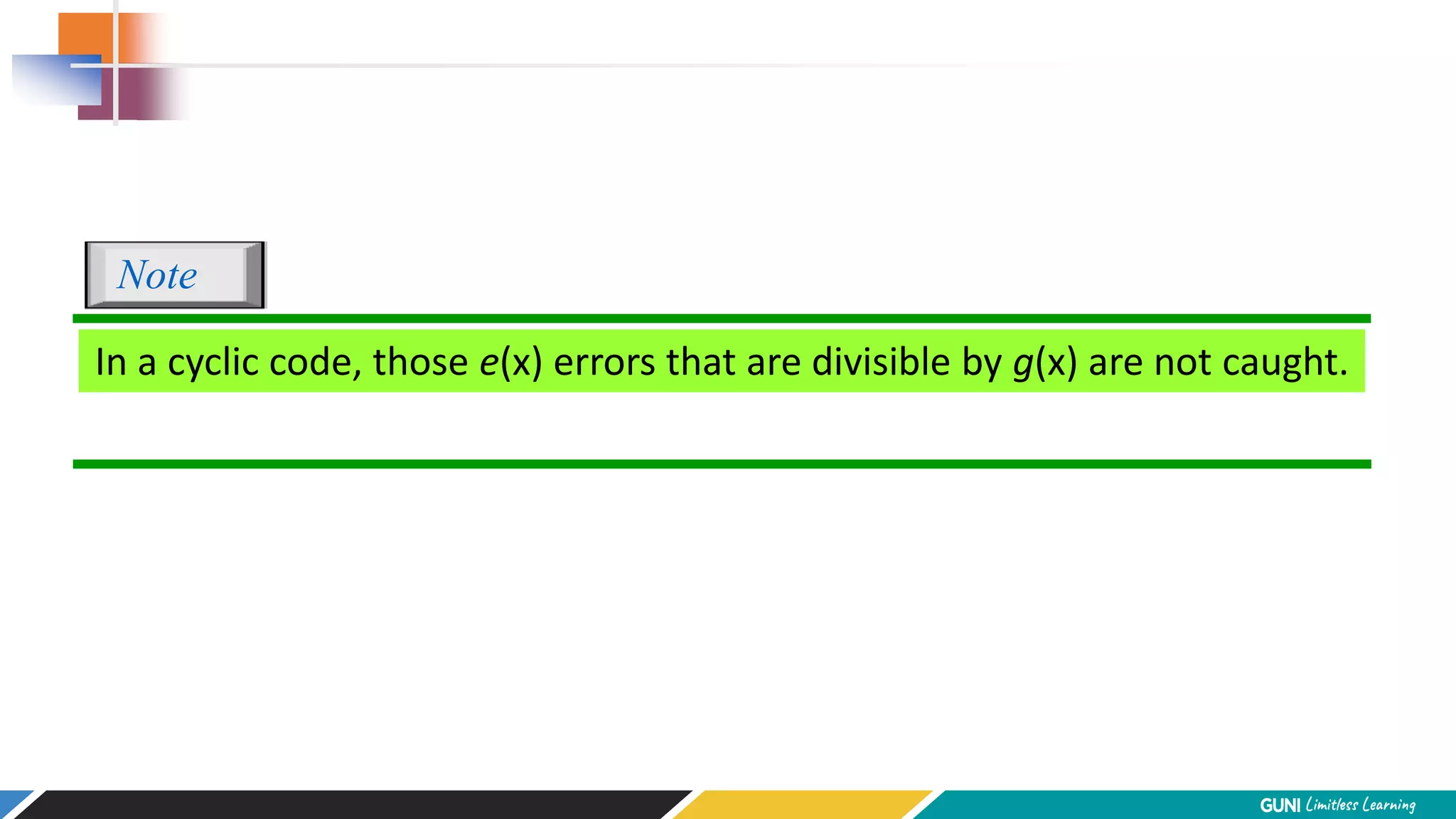
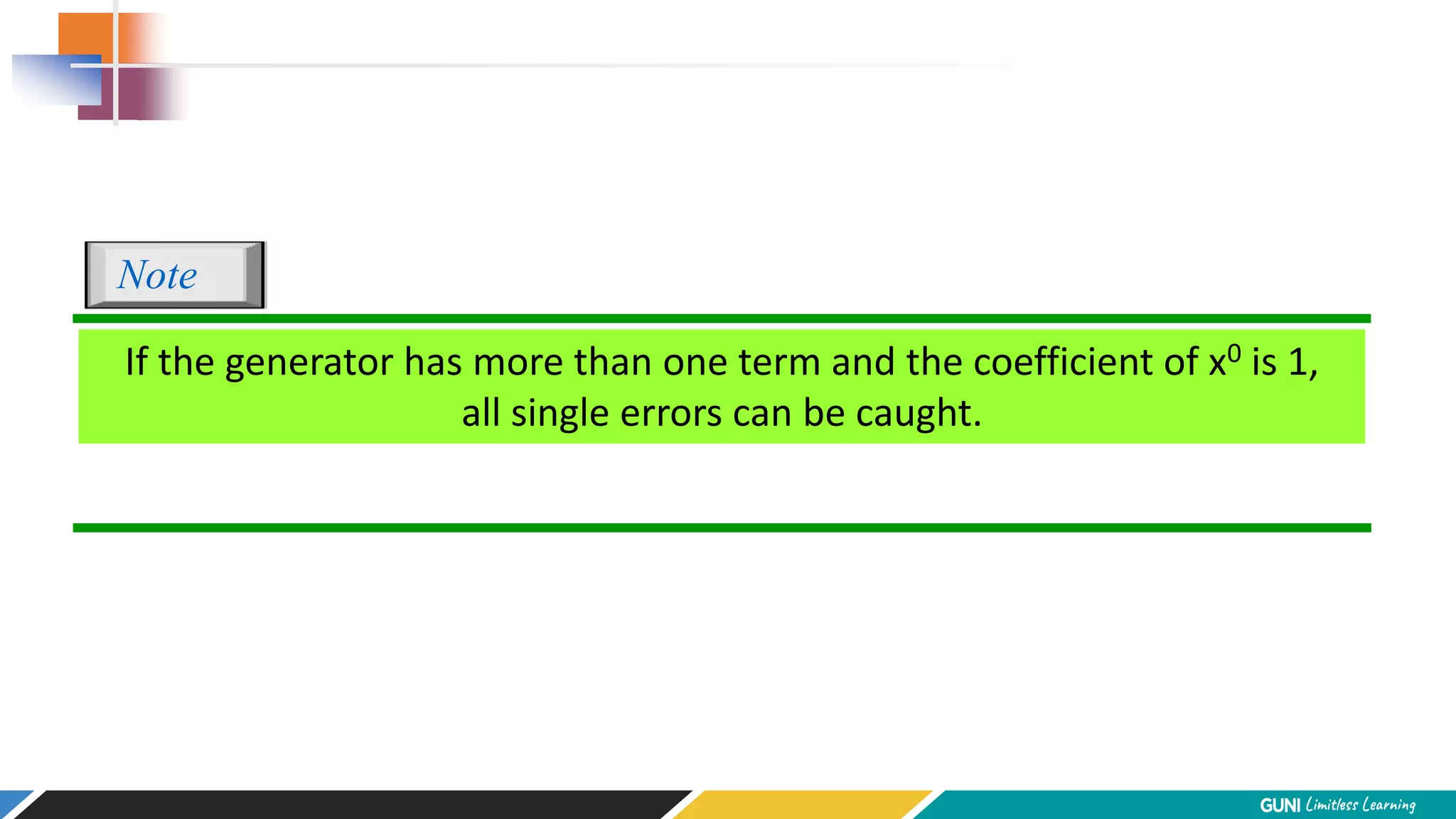
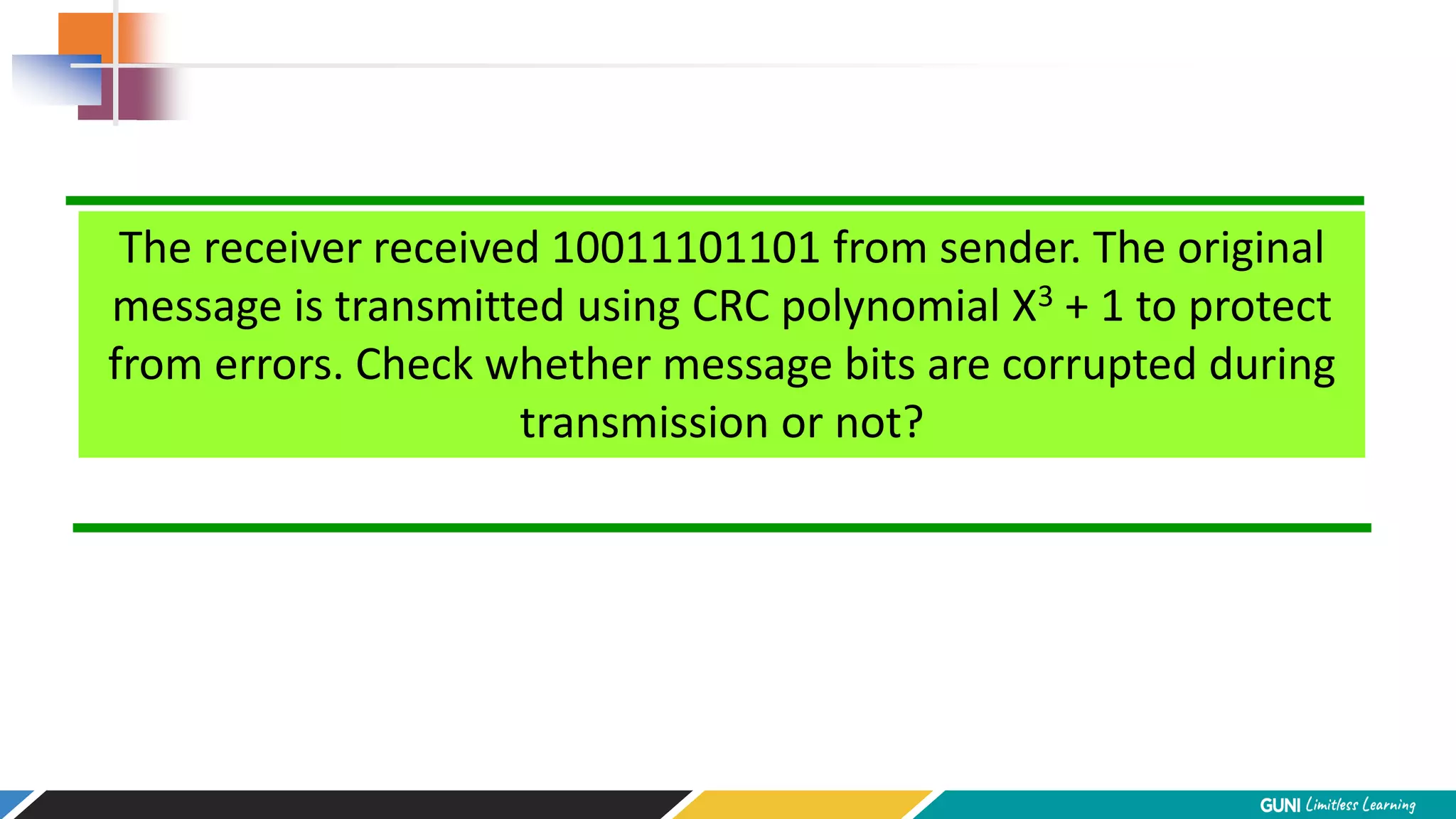
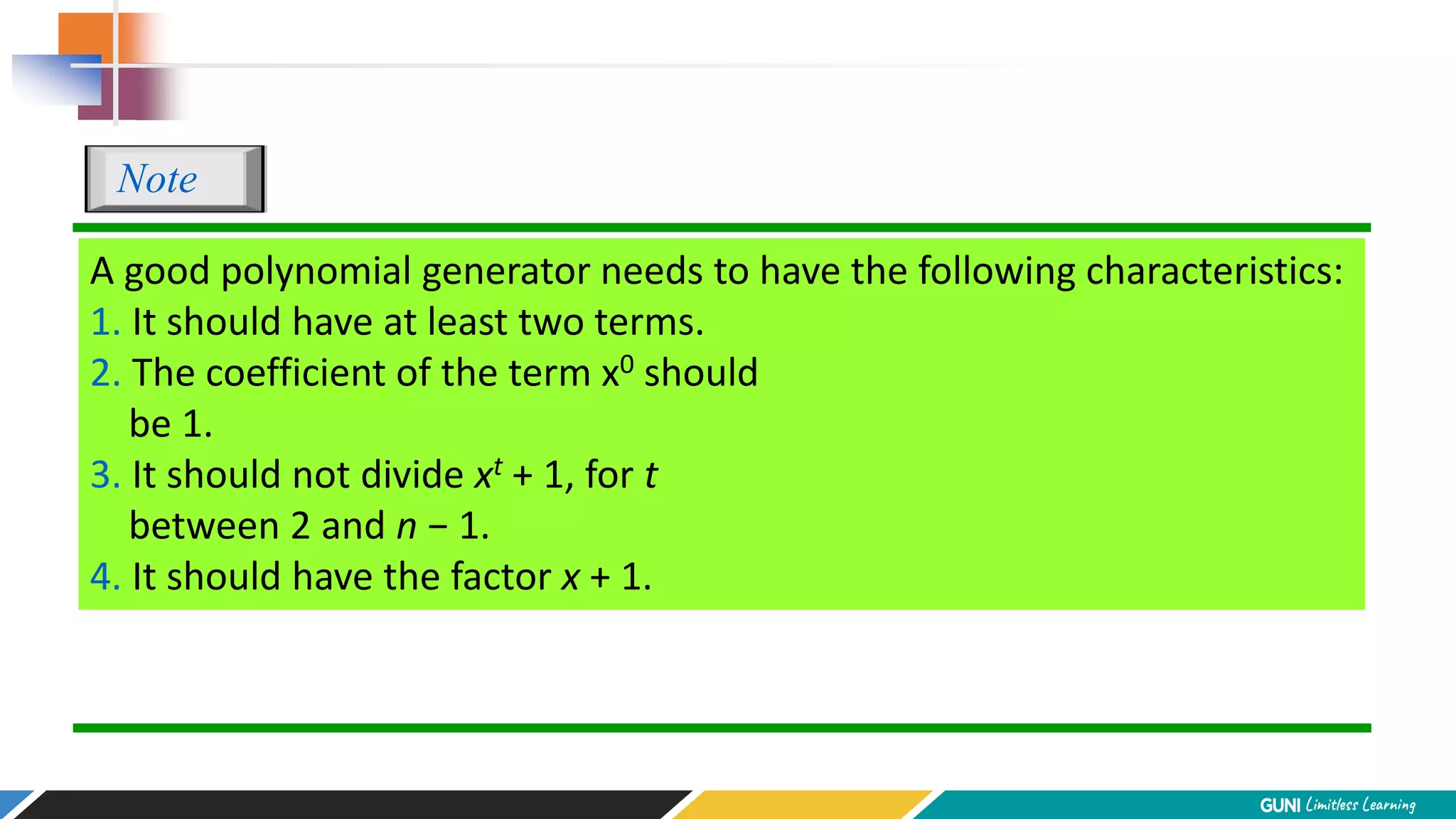
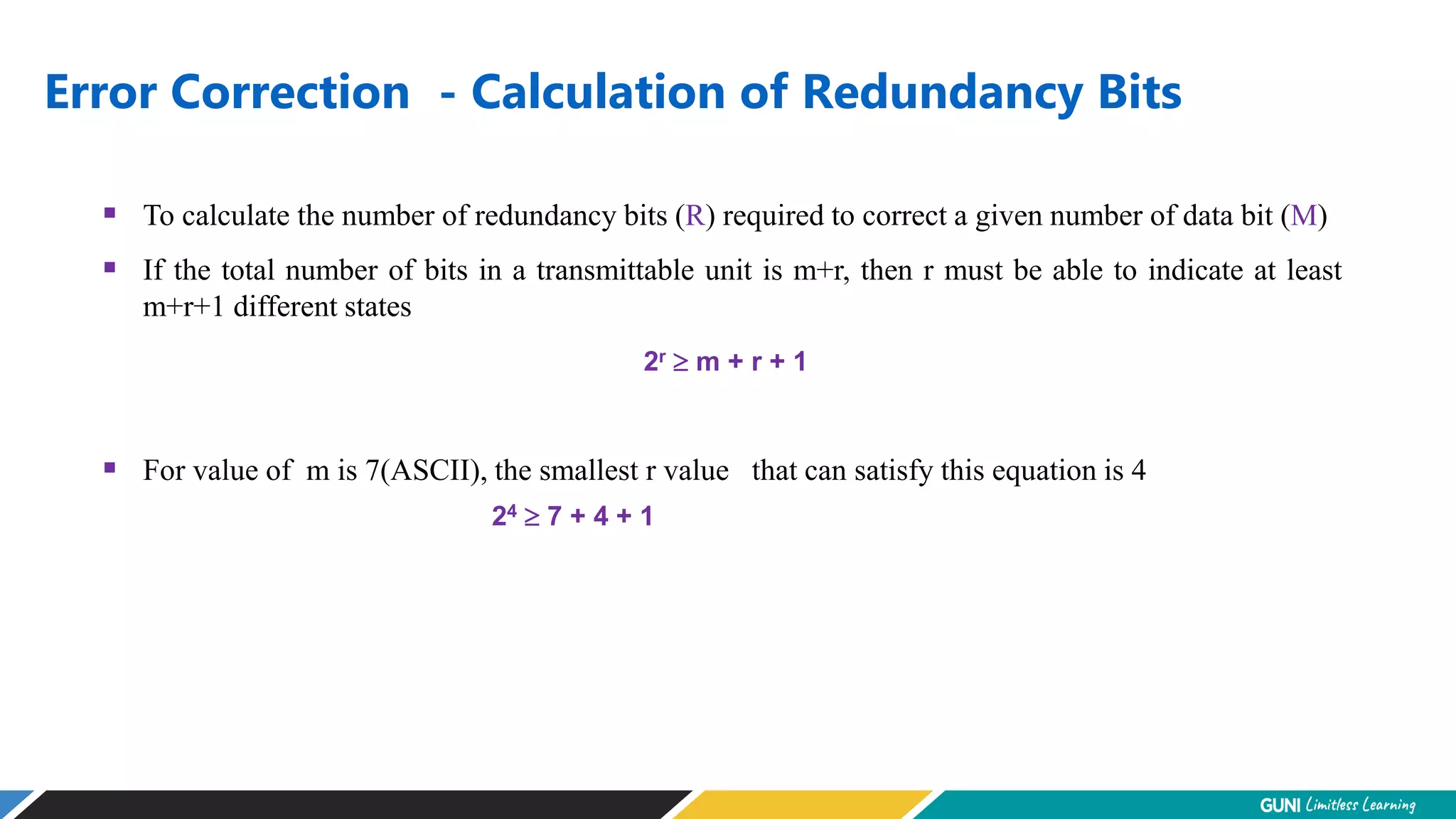
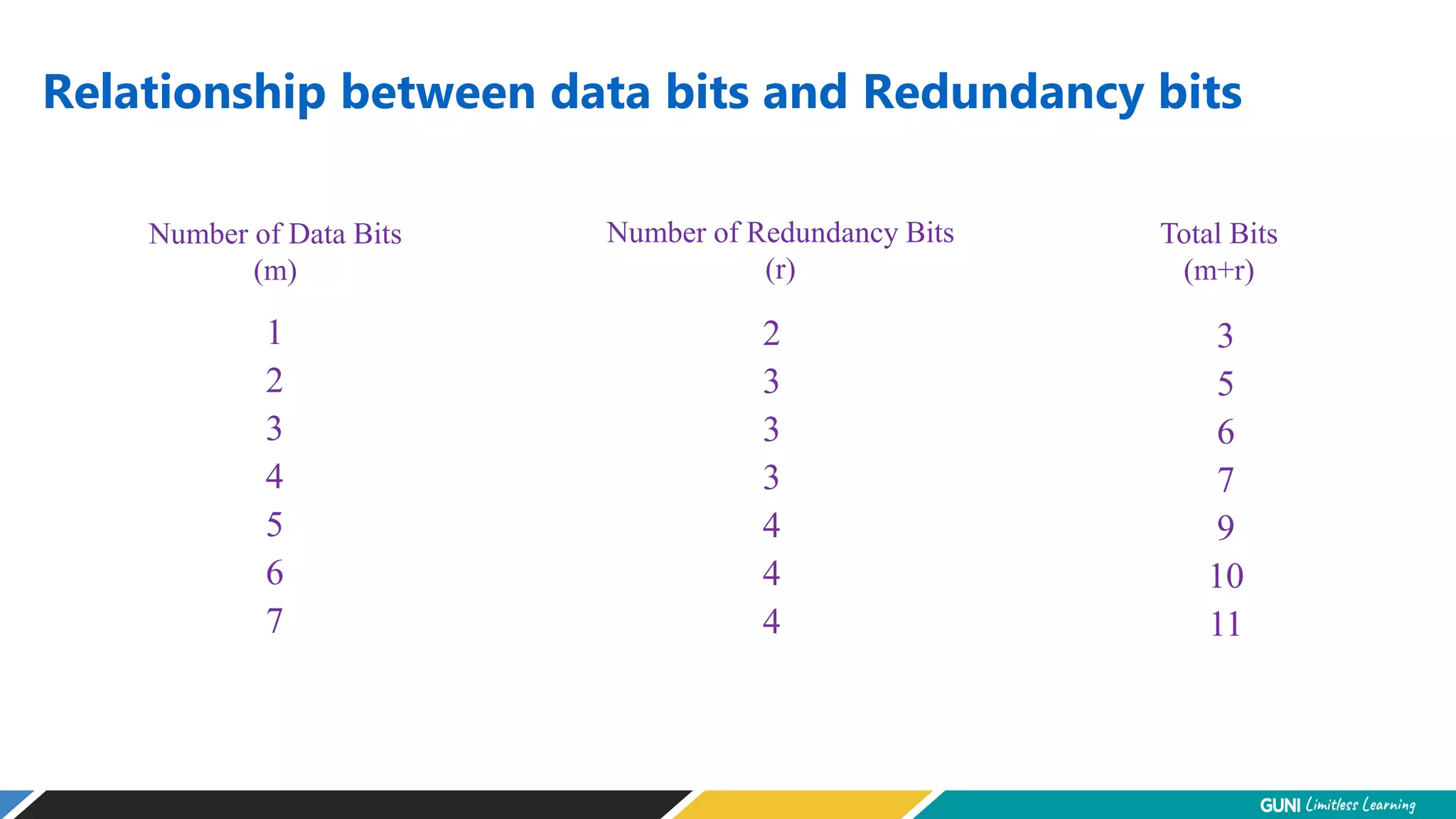
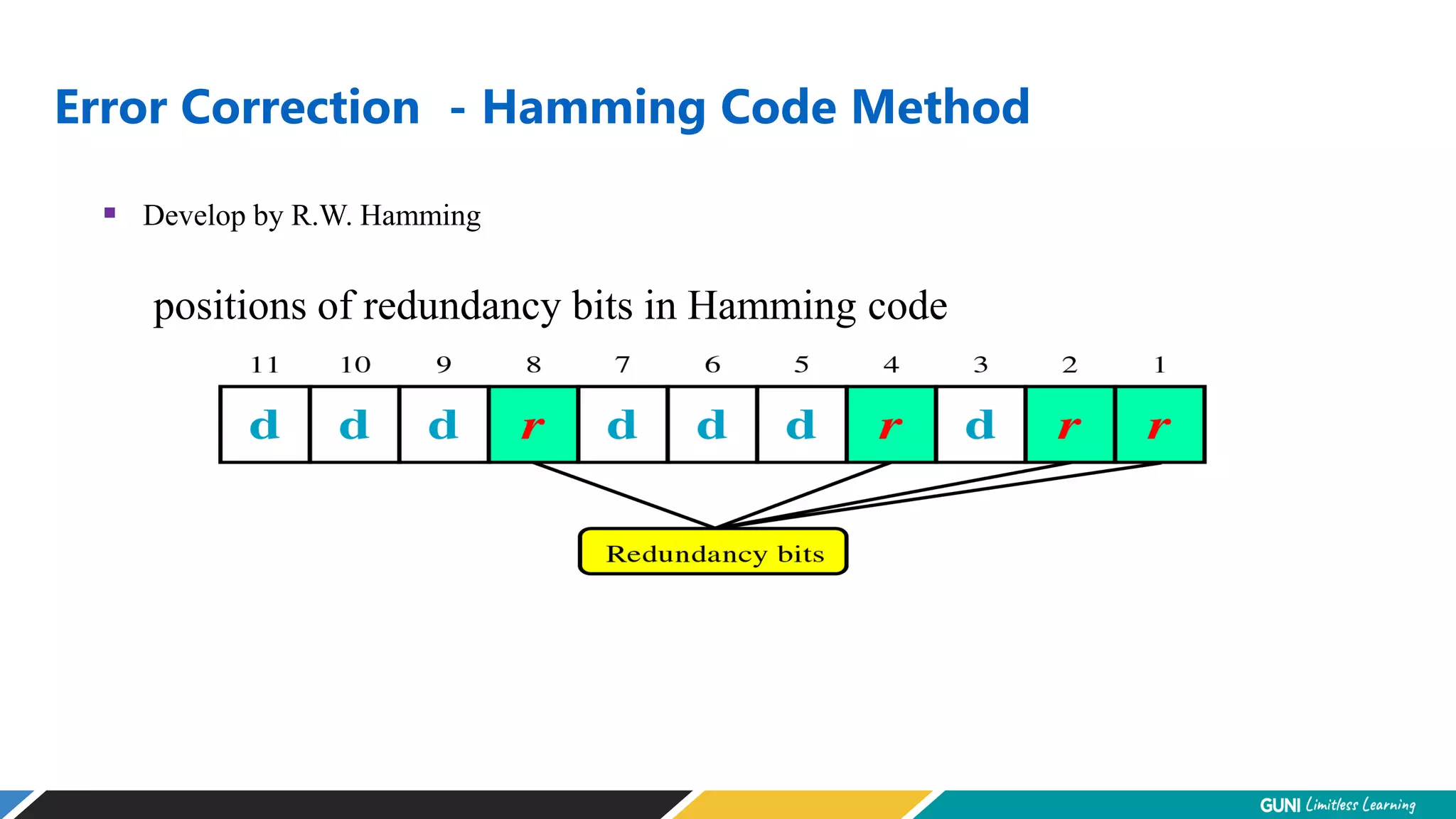
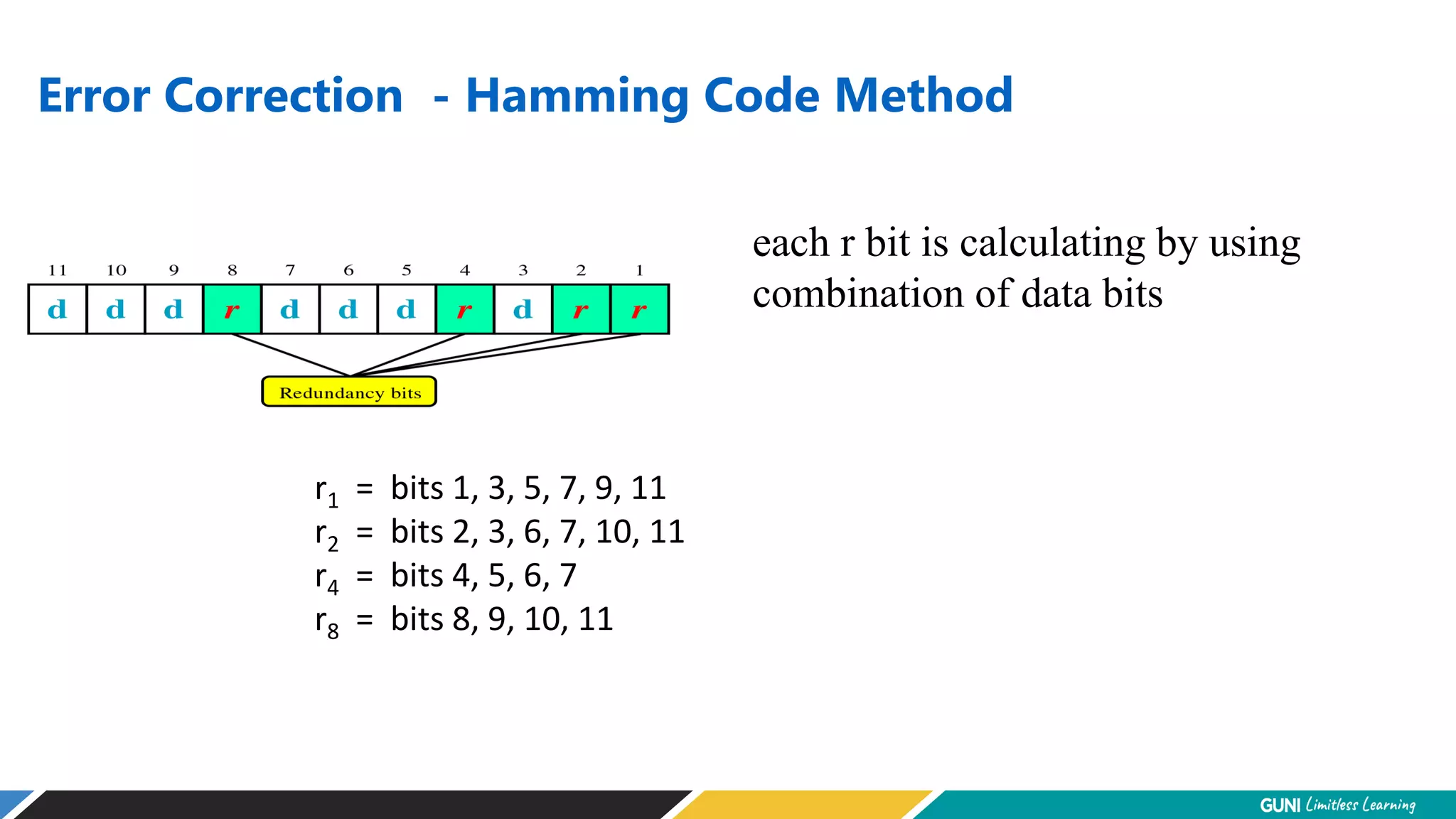
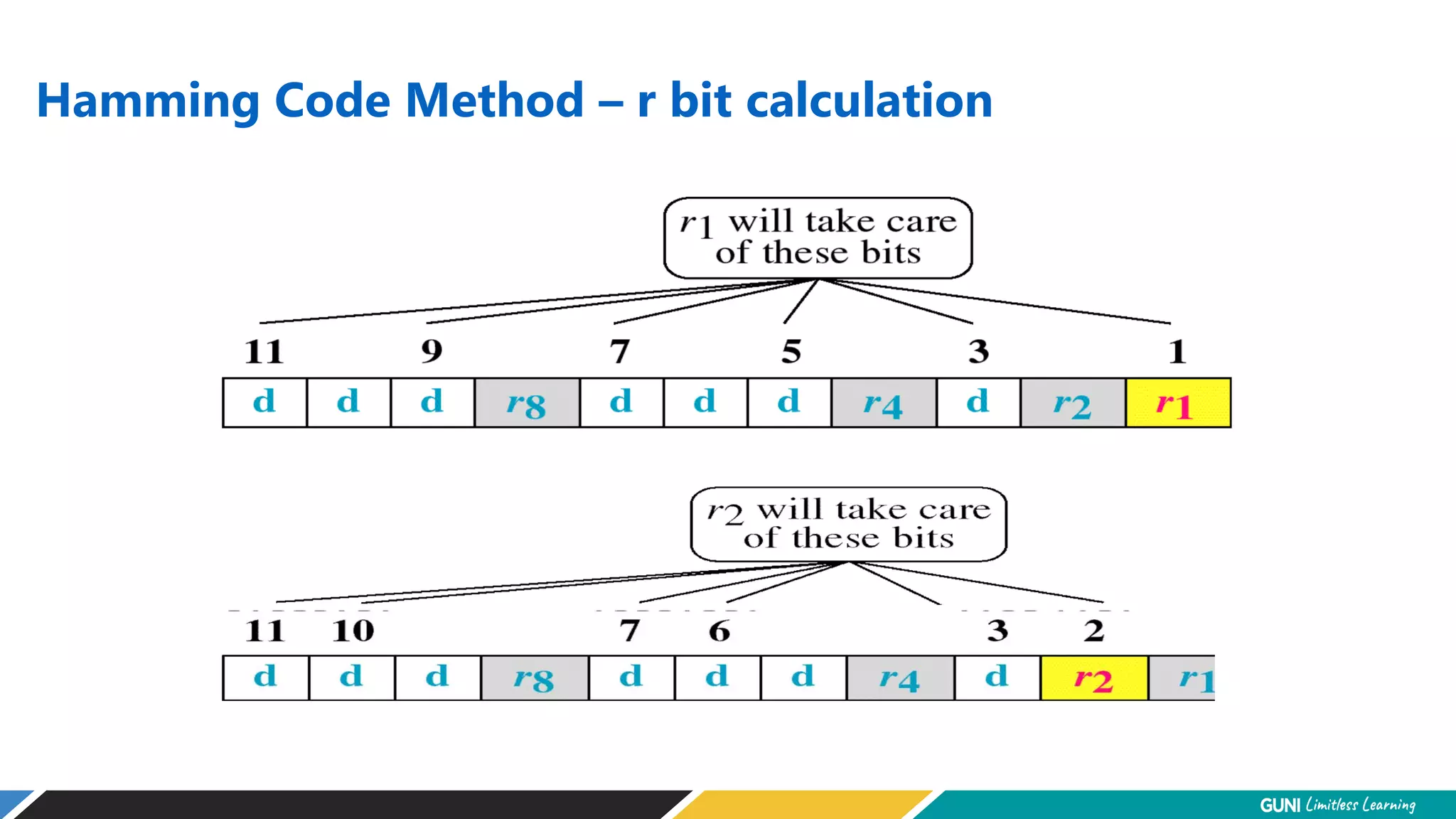
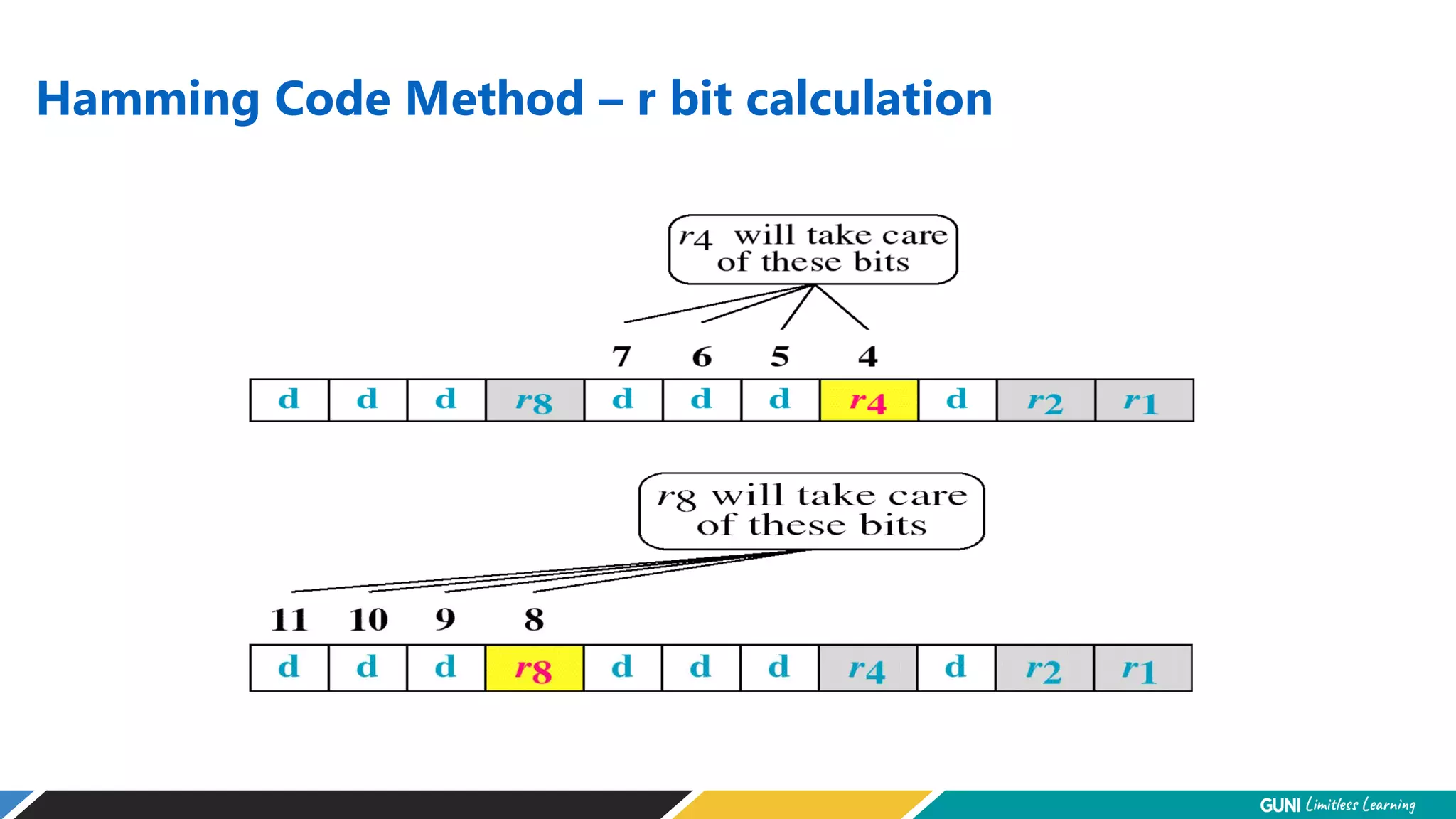
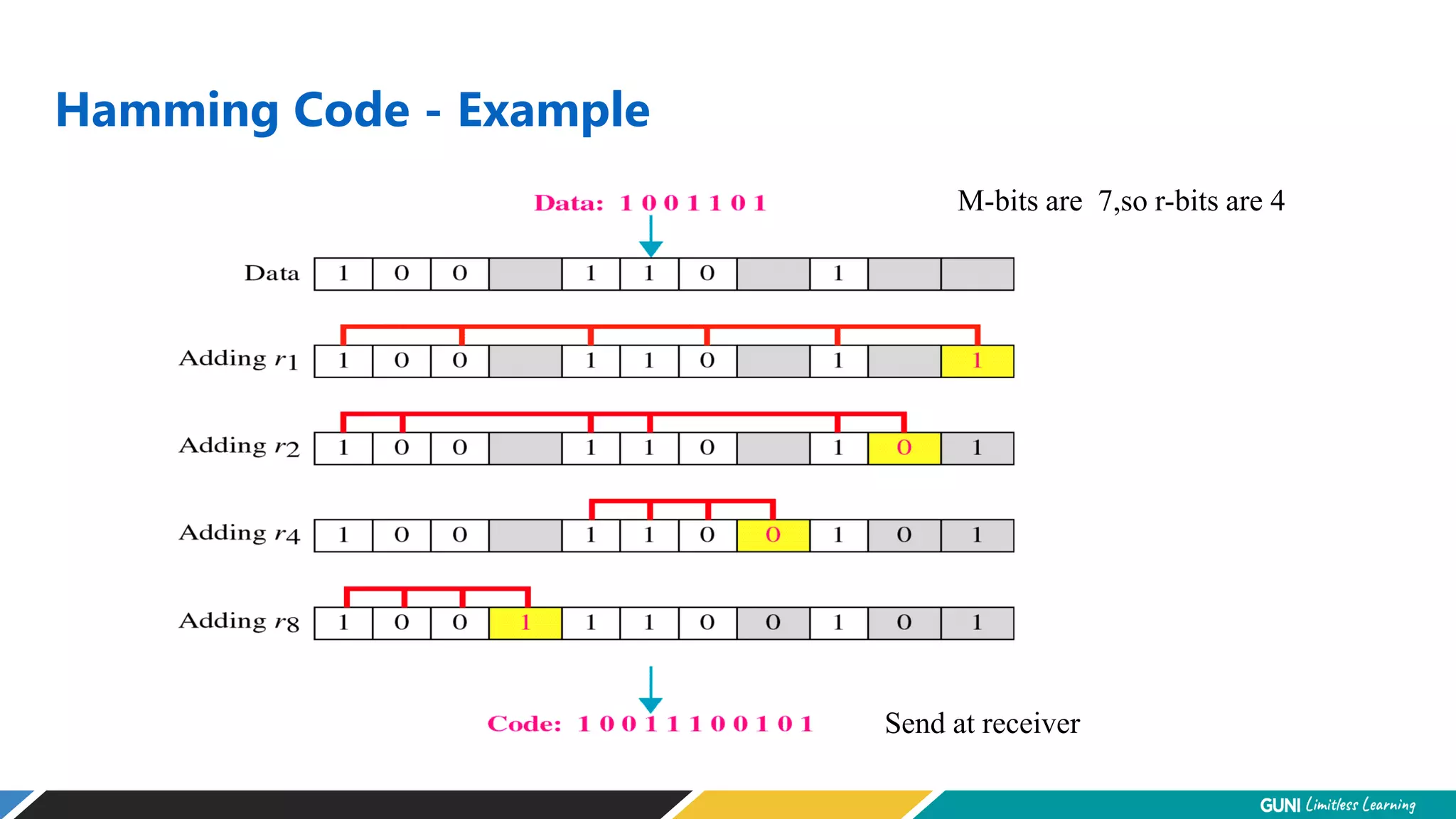
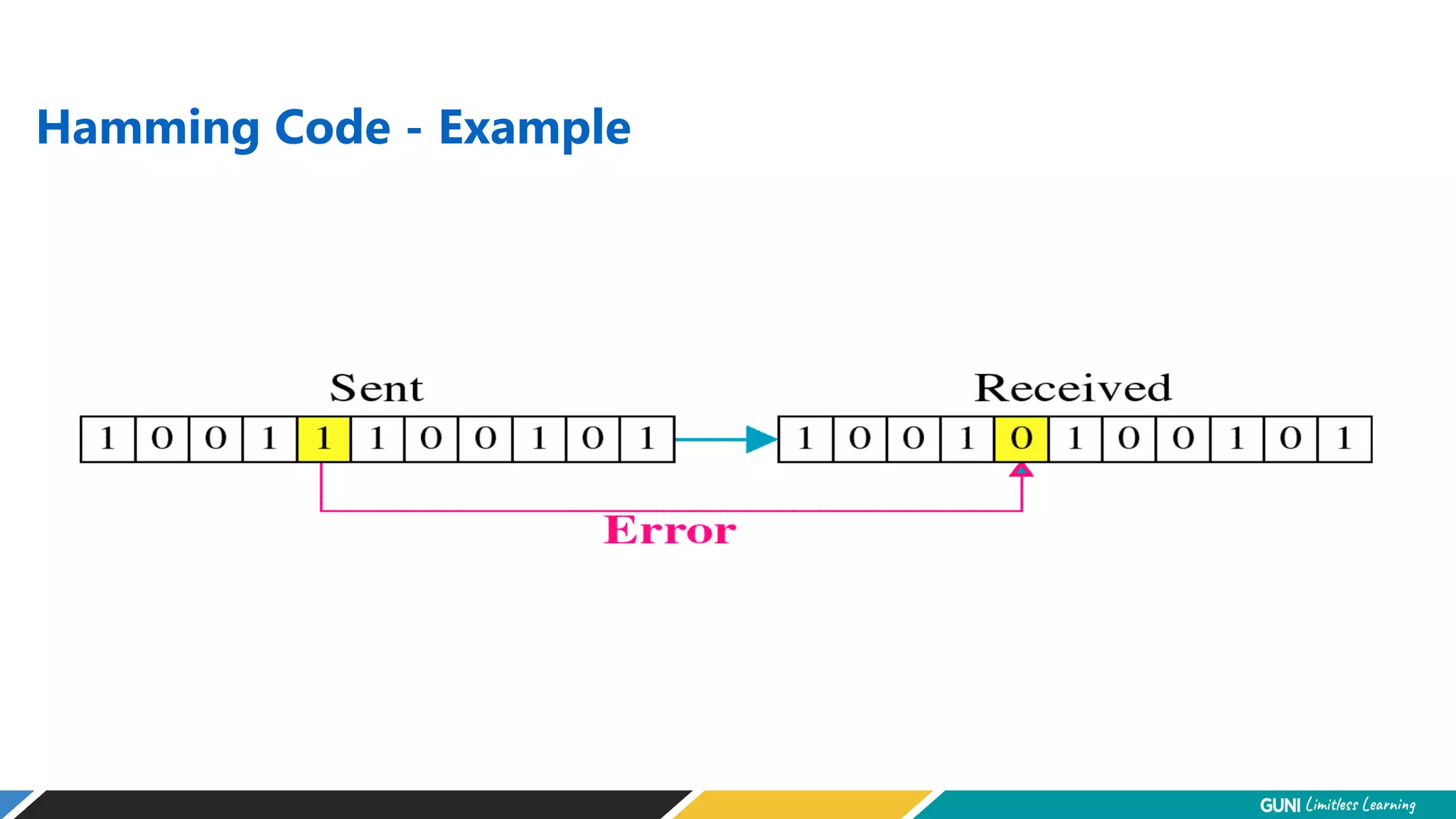
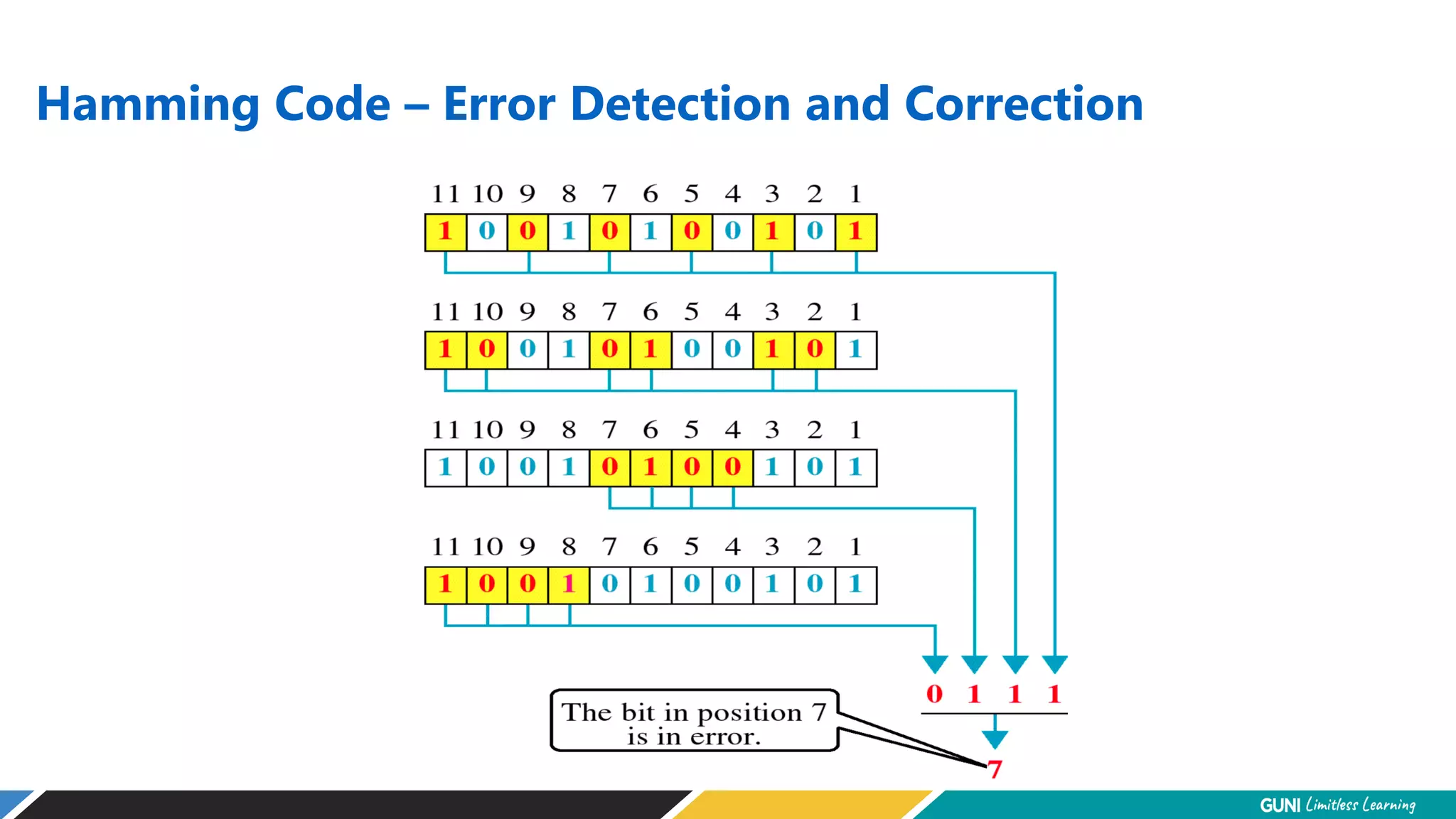
The document discusses error detection and correction techniques at the data link layer. It describes how errors can occur during data transmission and the need for reliable communication. Error detection allows a receiver to detect errors while error correction enables identifying and correcting bit errors without retransmission. Common techniques discussed include parity checks, checksums, and cyclic redundancy checks which add redundant bits to detect errors. CRC is based on binary division of data and checksum on addition. Forward error correction and retransmission are compared. Coding schemes use redundancy to detect or correct errors.
Human: Thank you for the summary. Can you provide a 2 sentence summary that captures the key aspects?