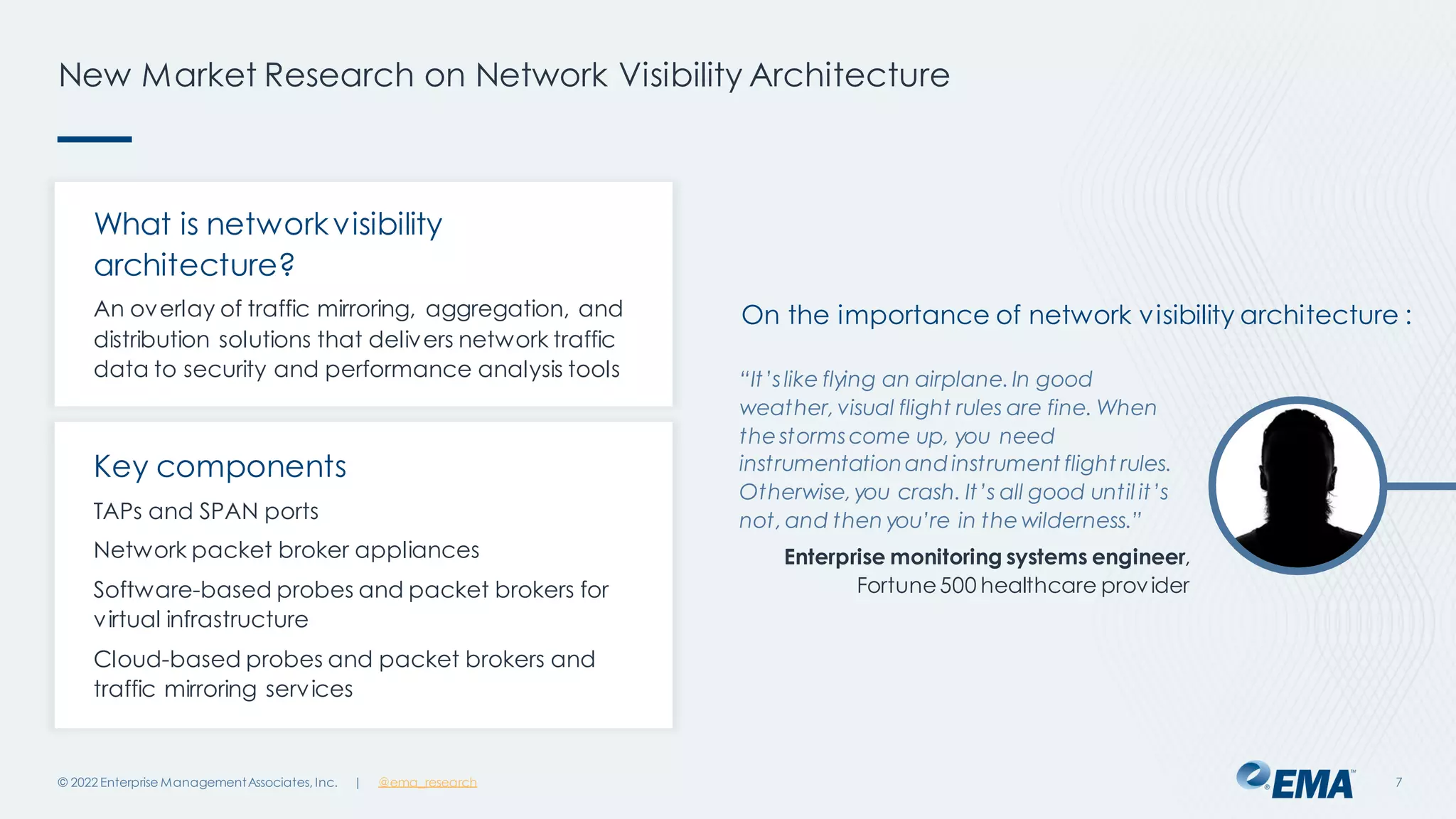
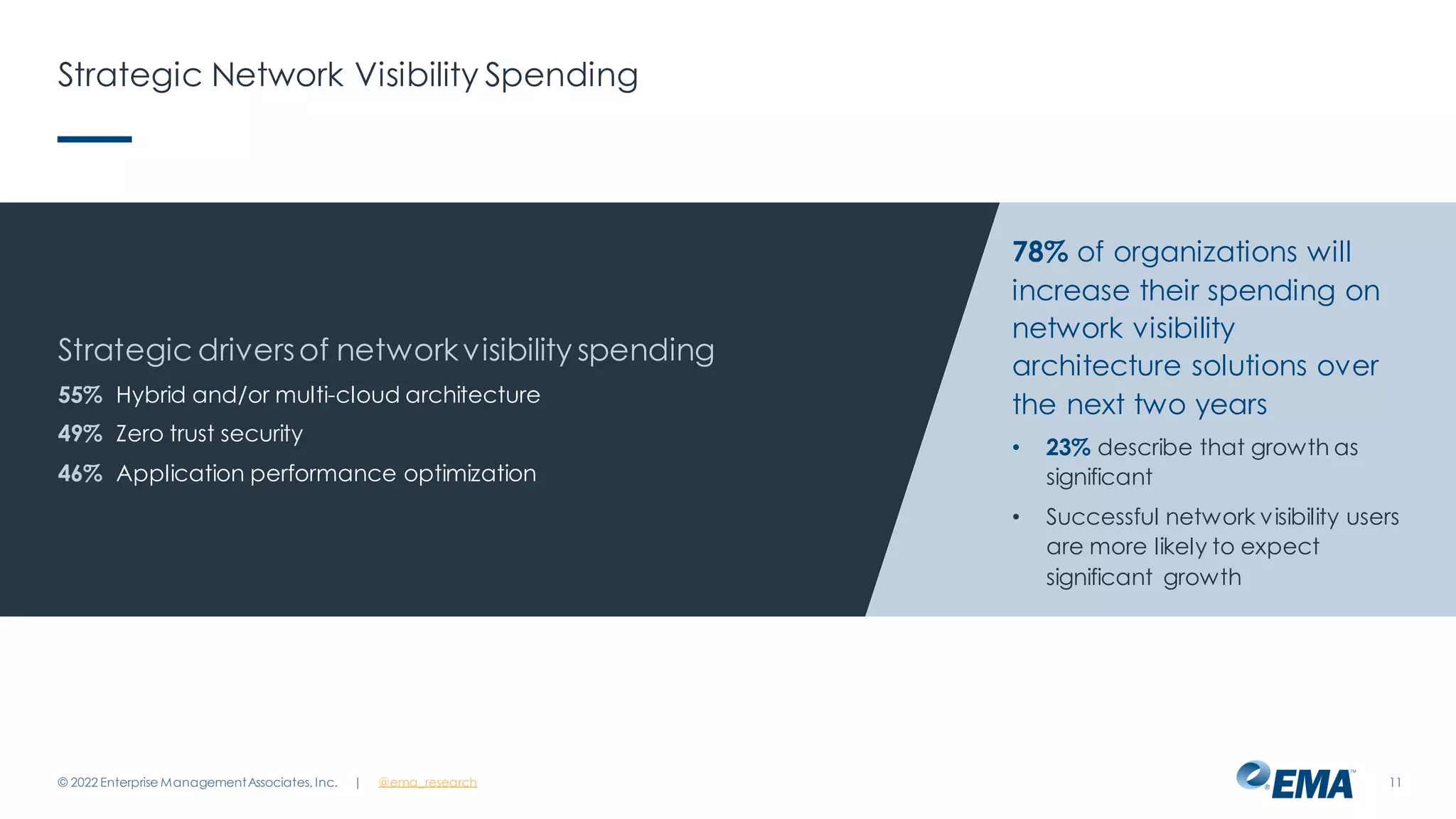
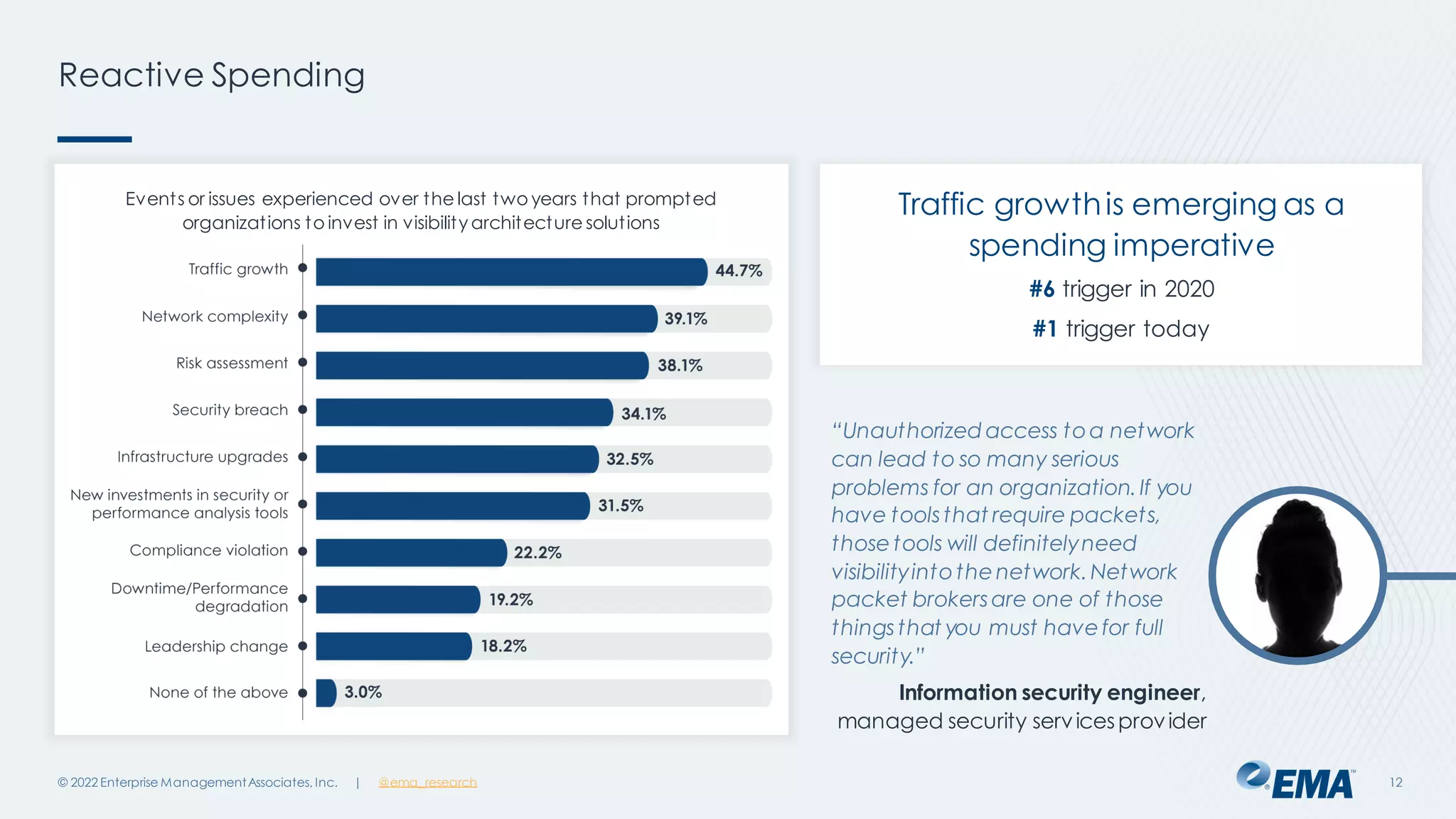
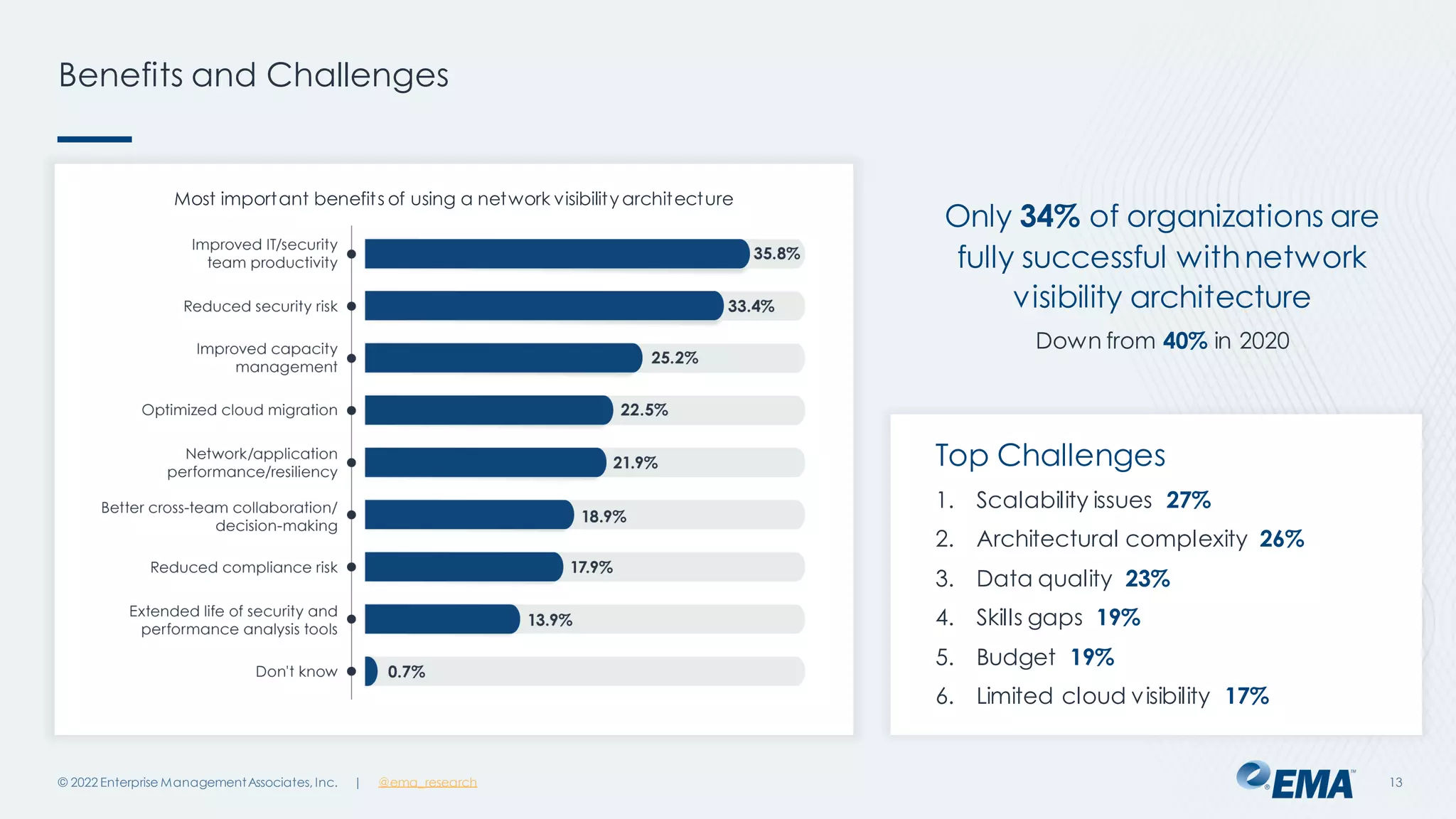
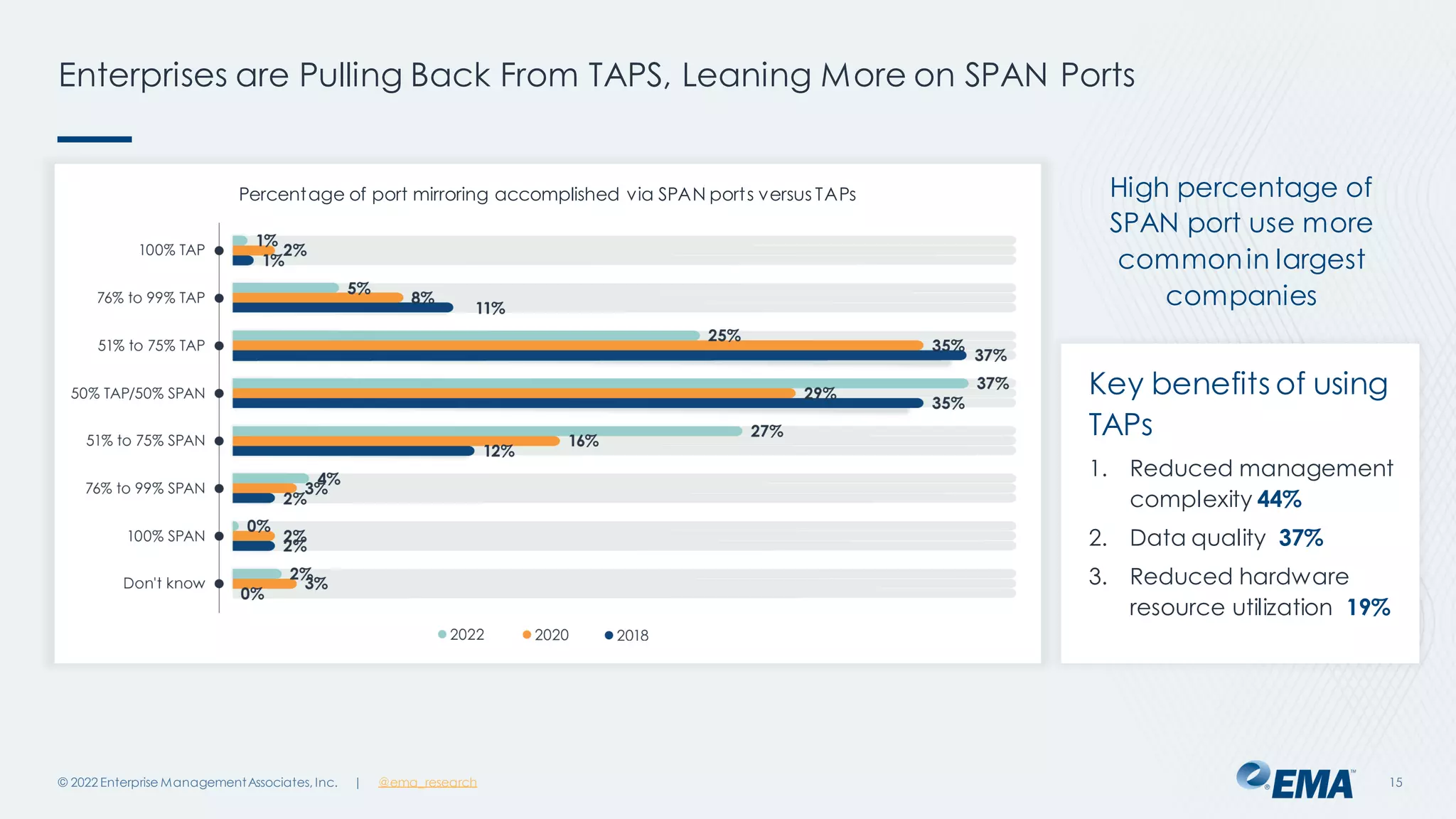
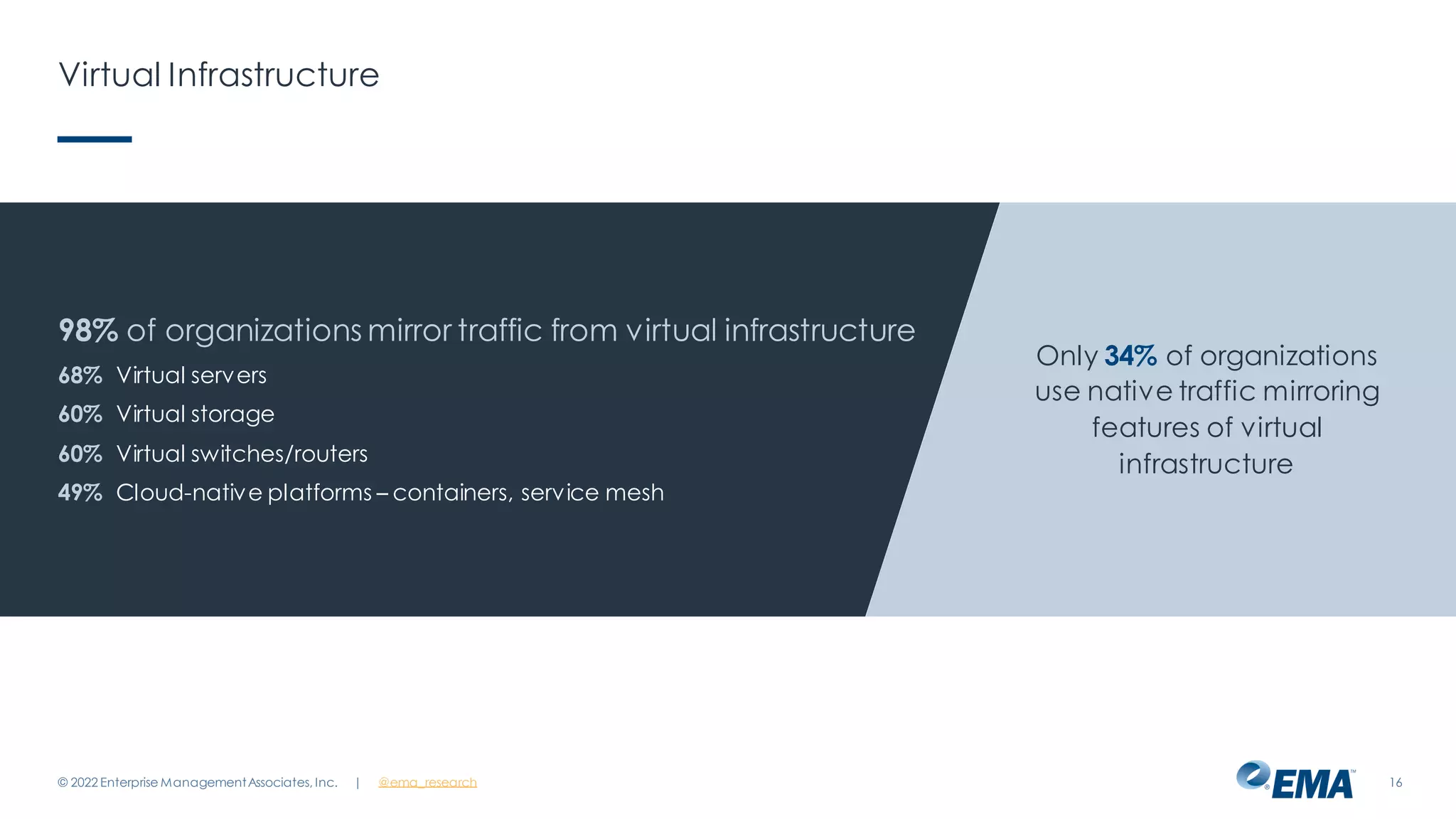
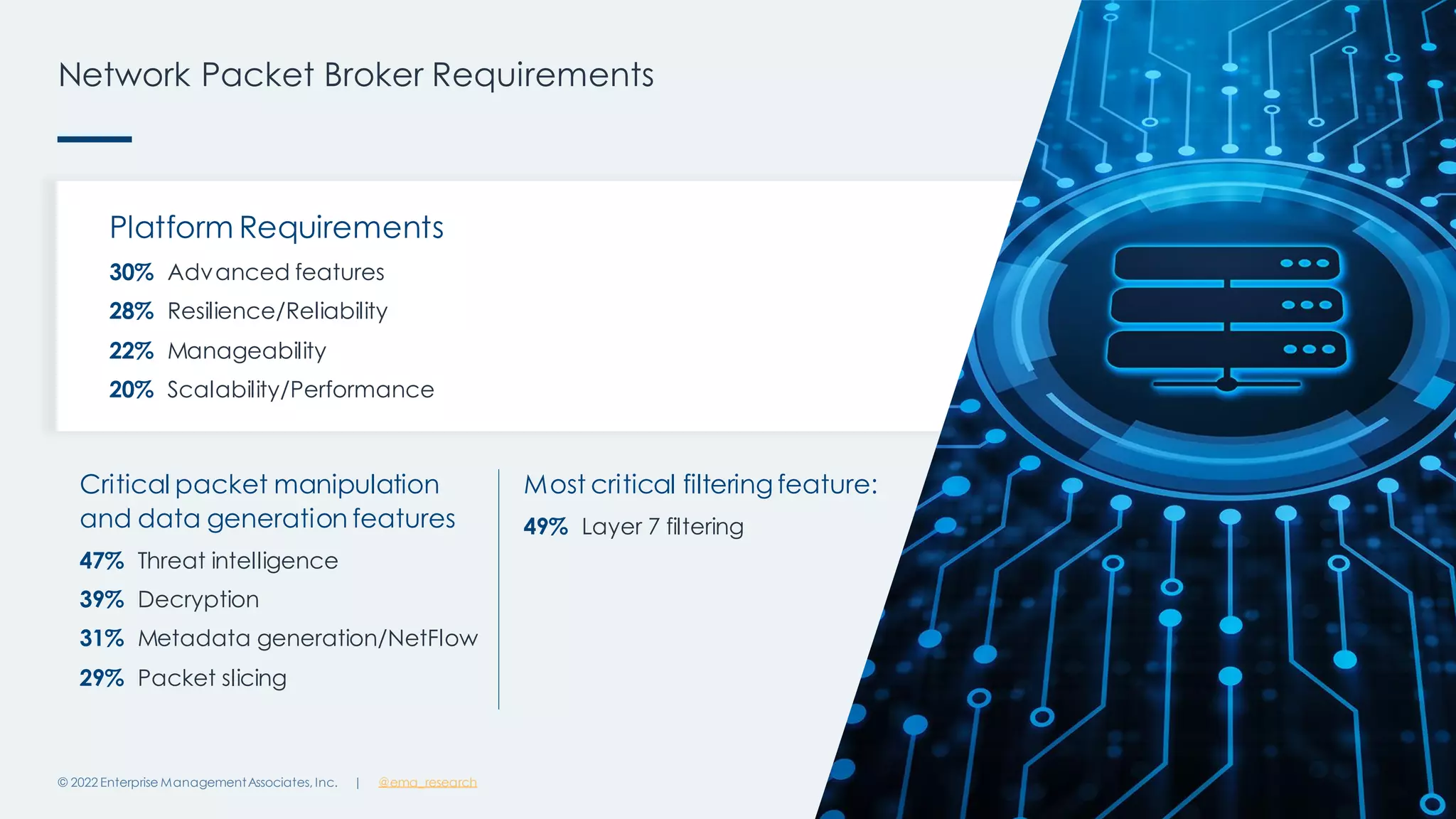
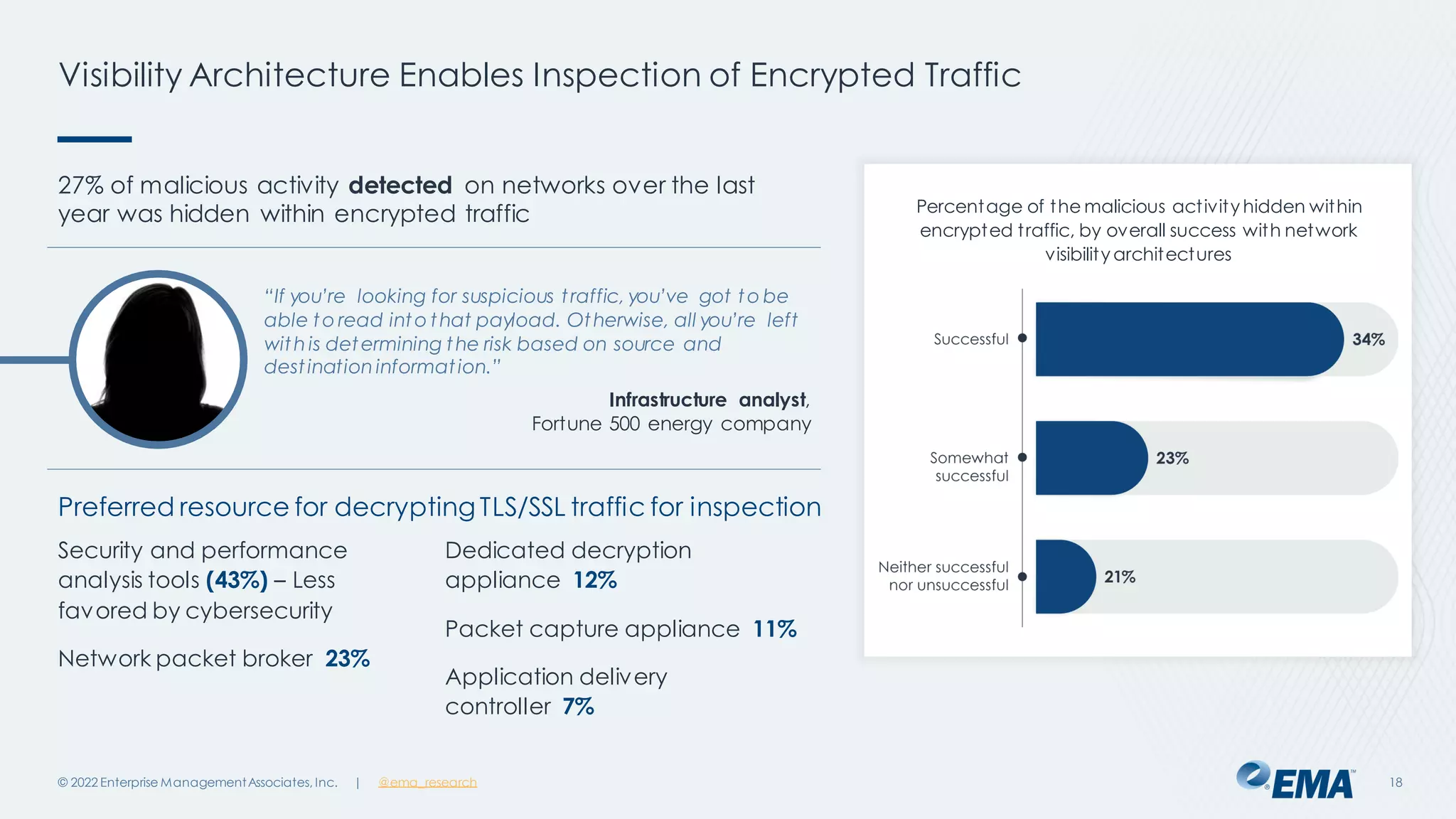
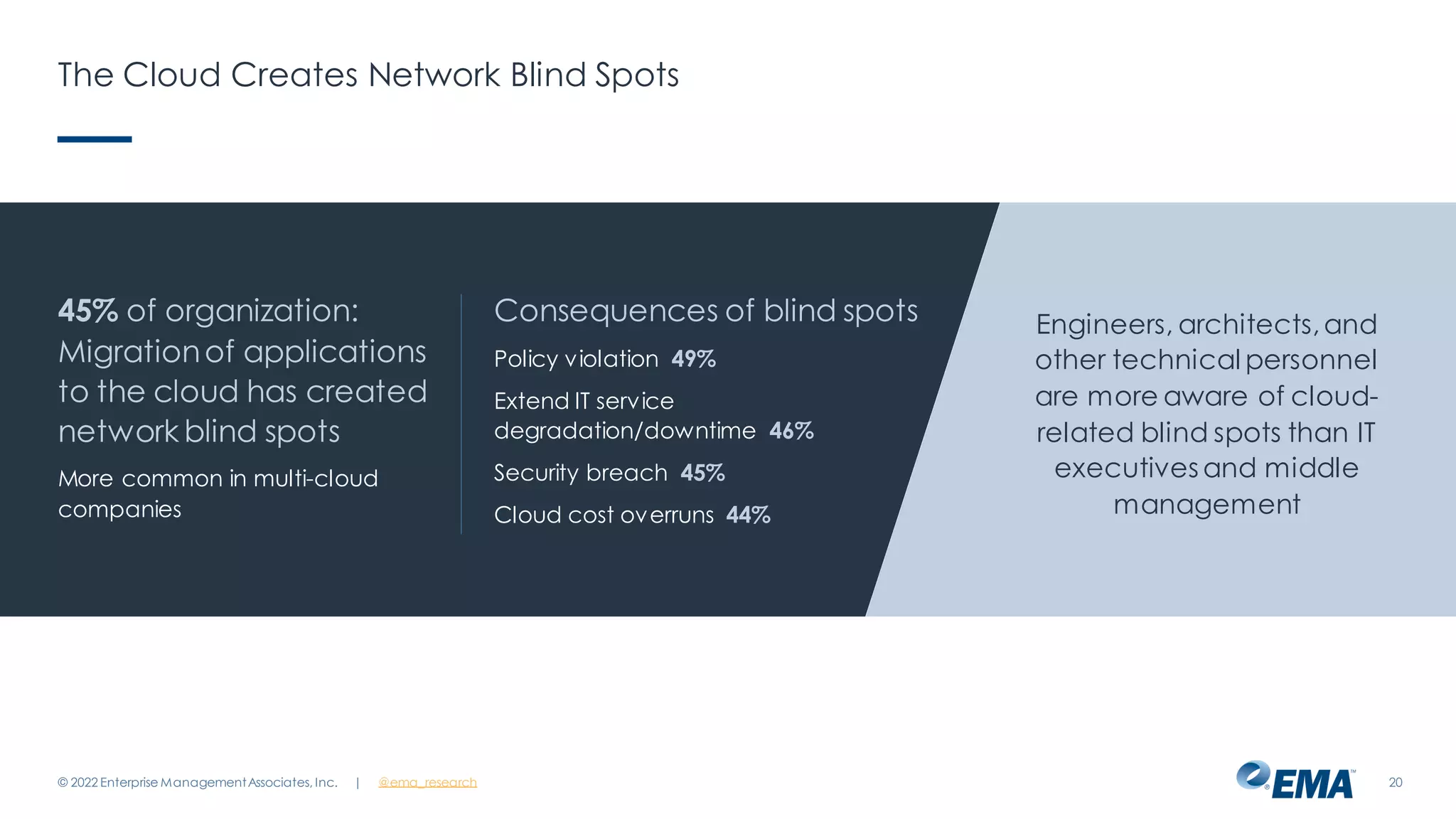
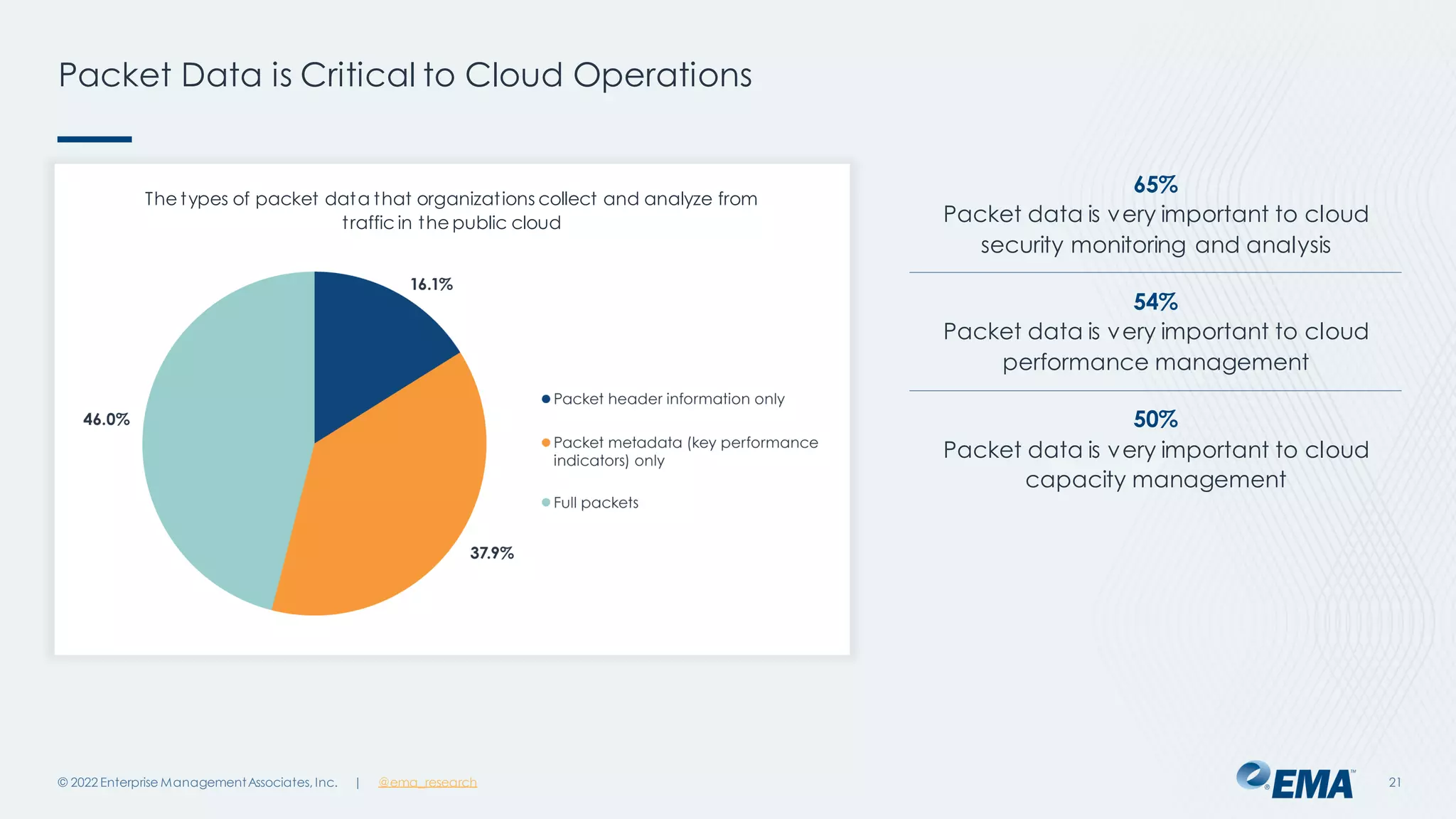
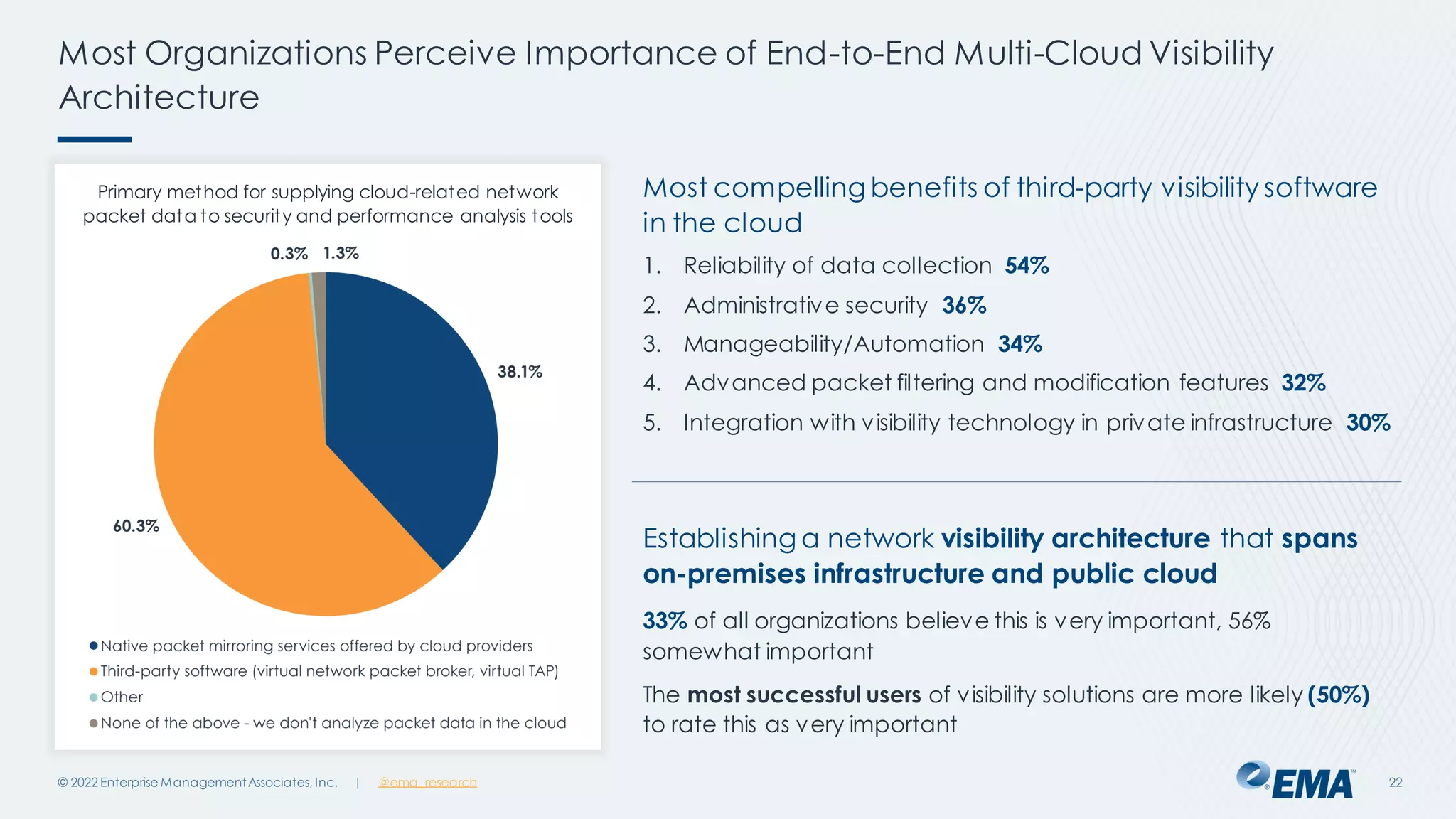
The document outlines the importance of network visibility architecture in hybrid, multi-cloud enterprises, highlighting strategies and components such as traffic mirroring and network packet brokers. It notes that 78% of organizations plan to increase spending on visibility solutions due to challenges like scalability, architectural complexity, and the need for better security against encrypted threats. Cloud migration has created visibility blind spots, leading to potential policy violations and security breaches, emphasizing the need for effective visibility solutions.