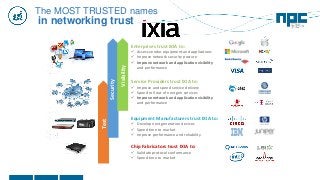
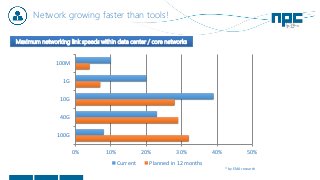
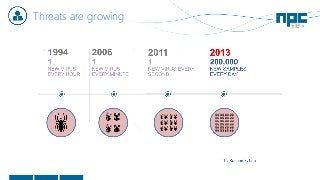
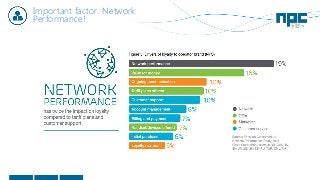
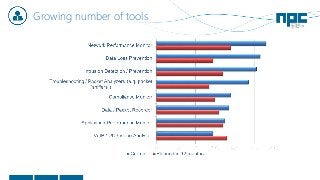
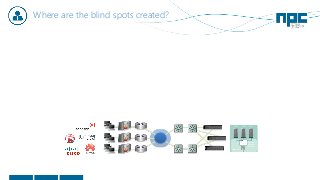
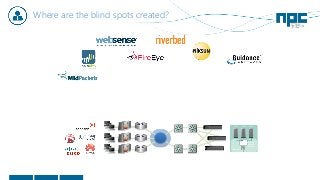
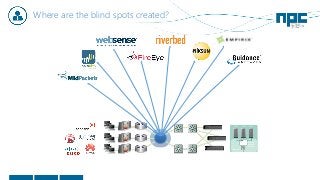
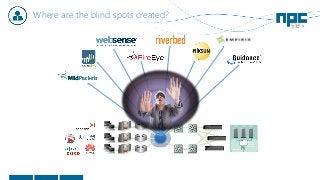
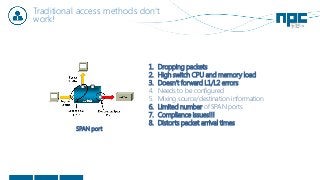
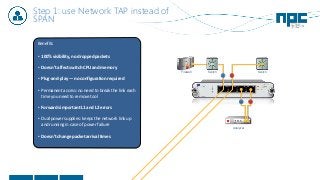
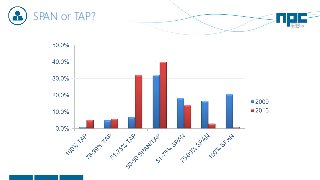
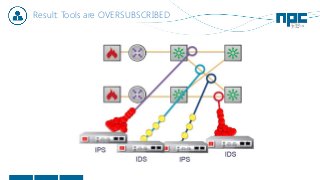
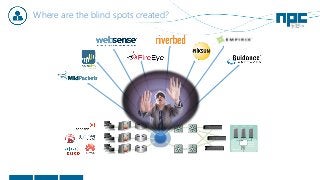
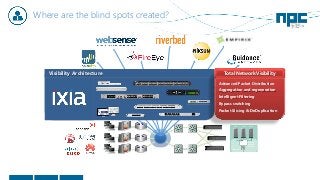
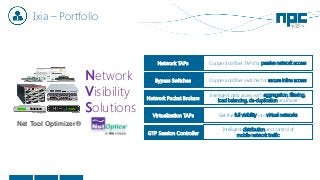
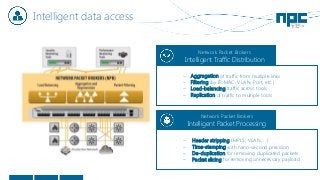
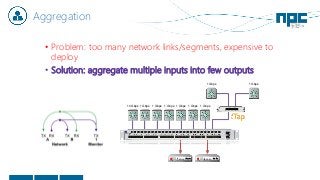
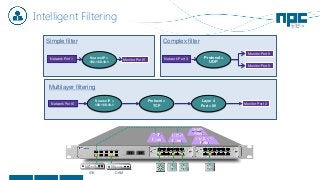
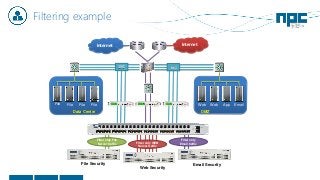
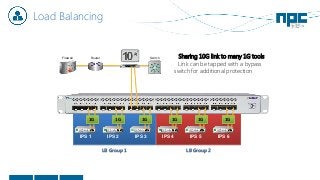
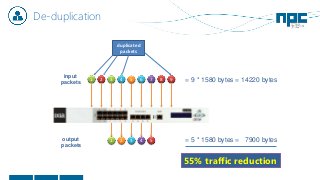
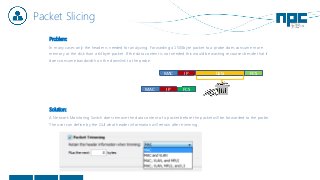
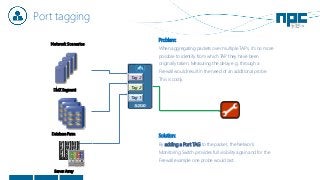
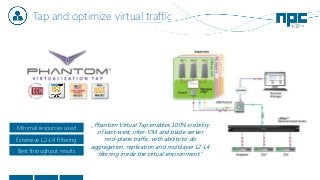
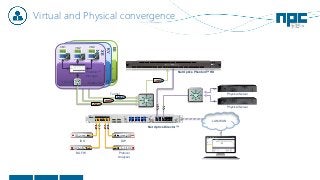
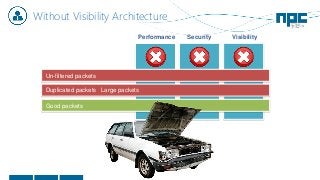
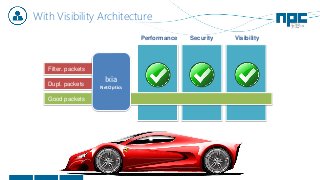
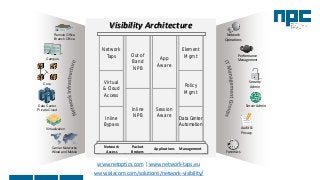
The document discusses network visibility solutions from Net Optics and Ixia. It summarizes that Net Optics was acquired by Ixia but will remain a brand name. It then discusses challenges of network growth outpacing monitoring tools, security threats increasing, and the need for improved network performance and visibility. The document promotes Ixia and Net Optics solutions like network taps, packet brokers, and virtual monitoring tools that provide intelligent traffic distribution and filtering to gain complete network visibility without blind spots.