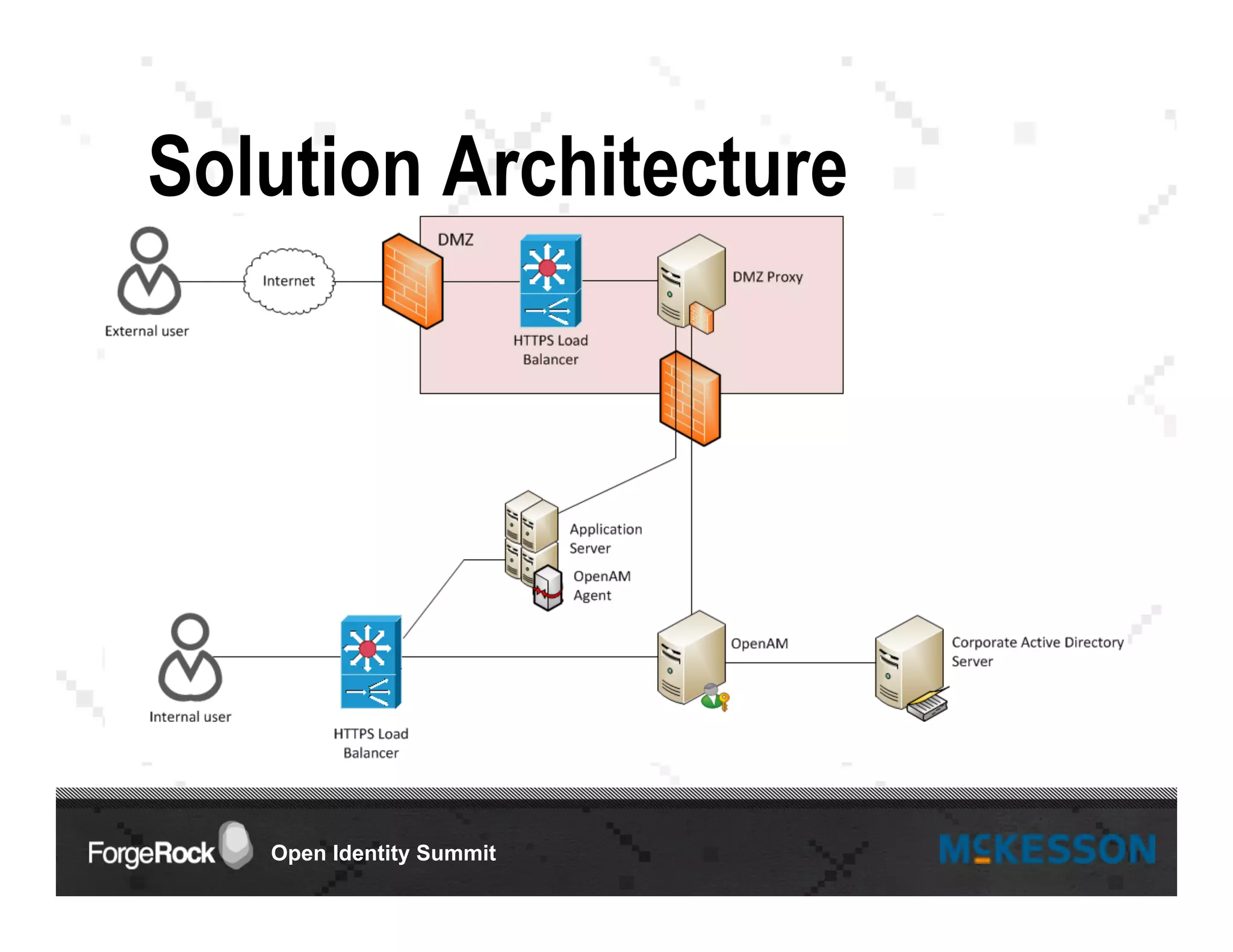
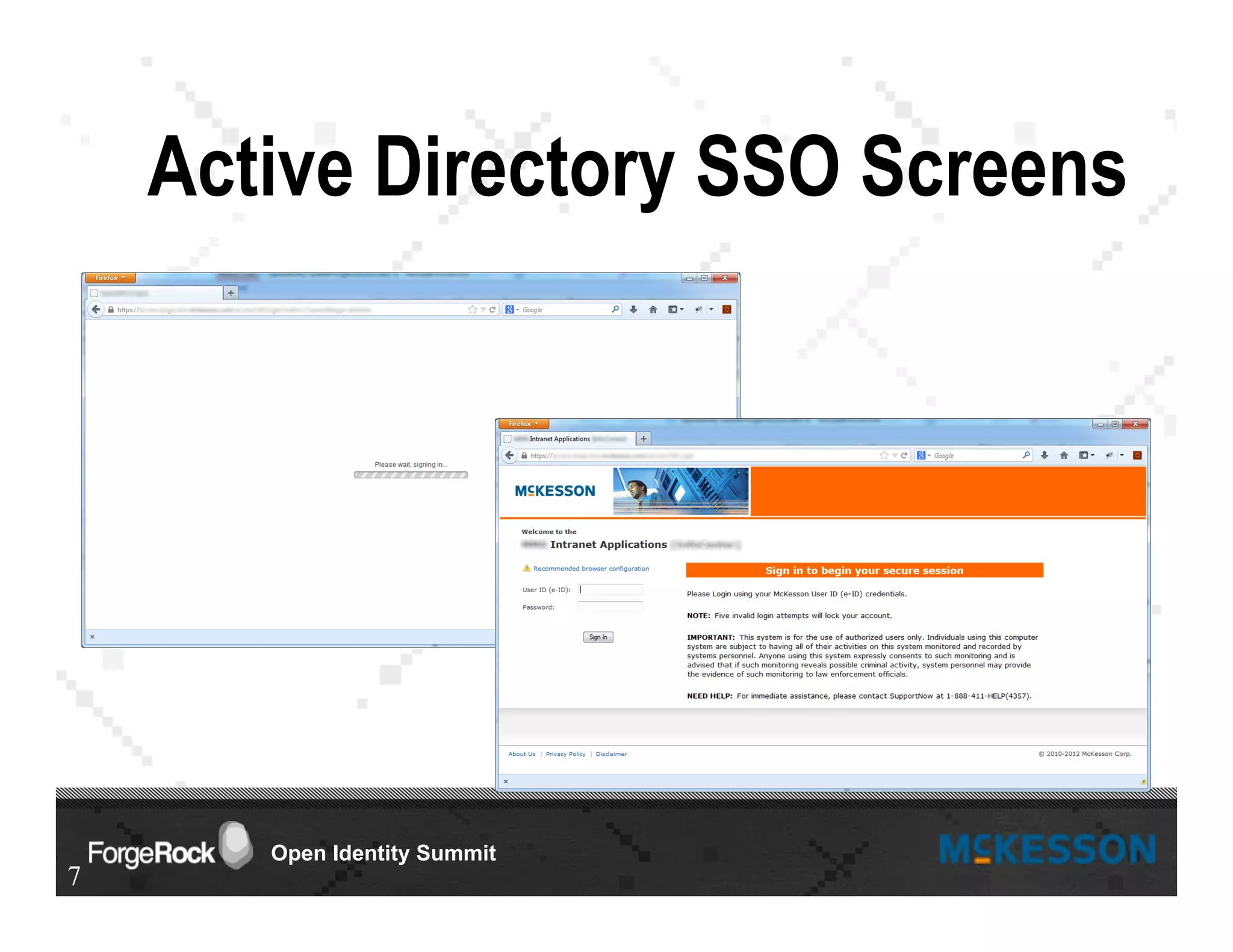
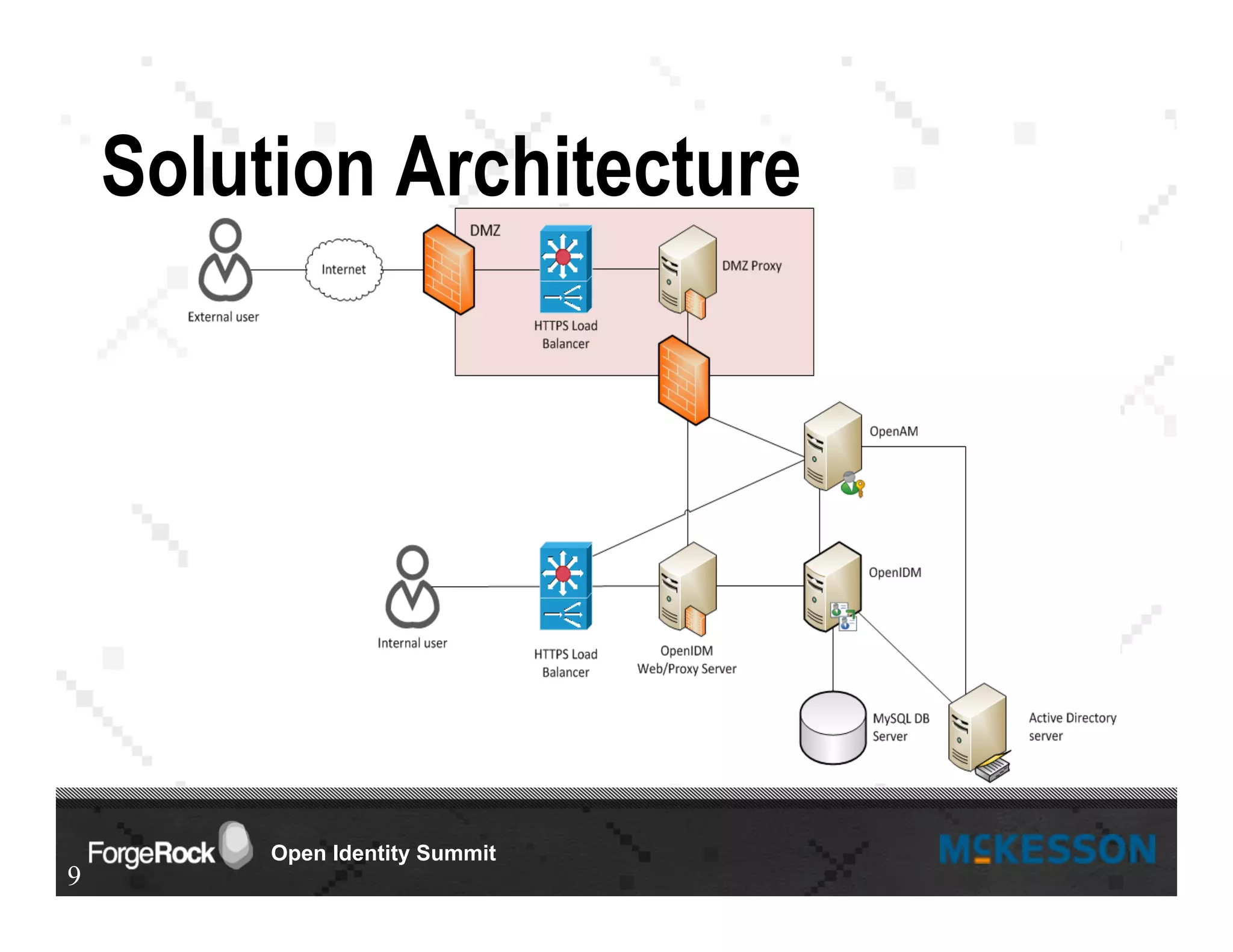
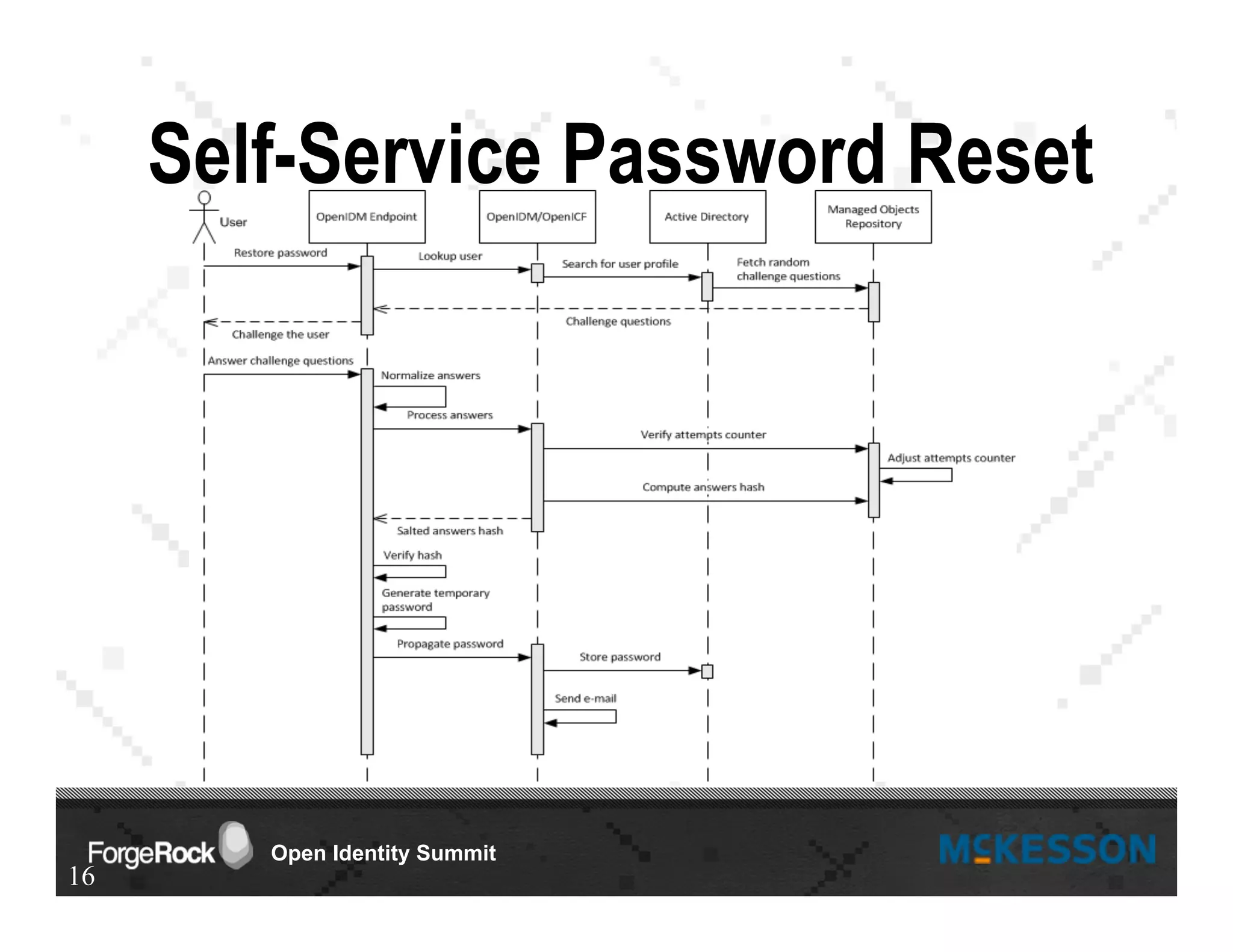
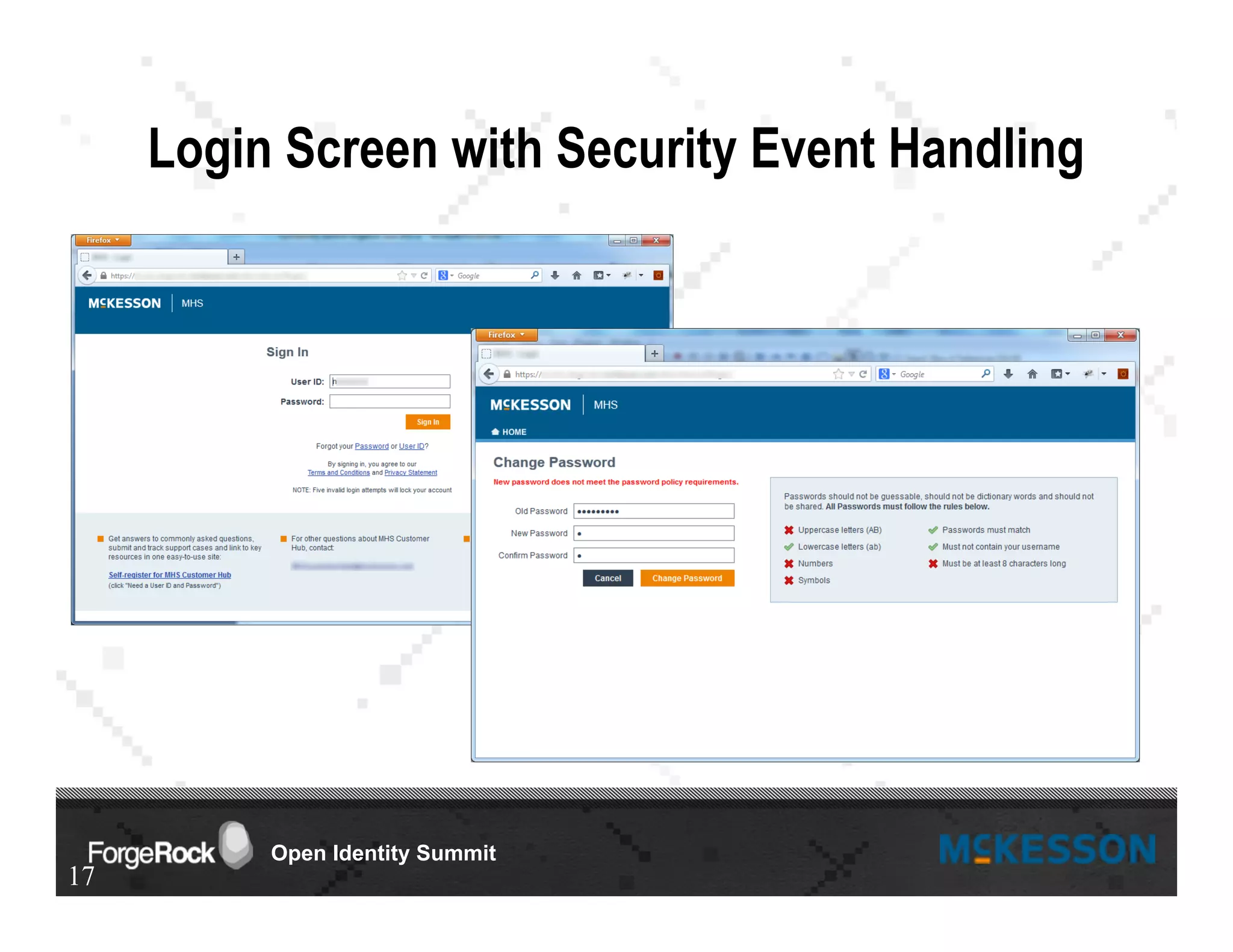
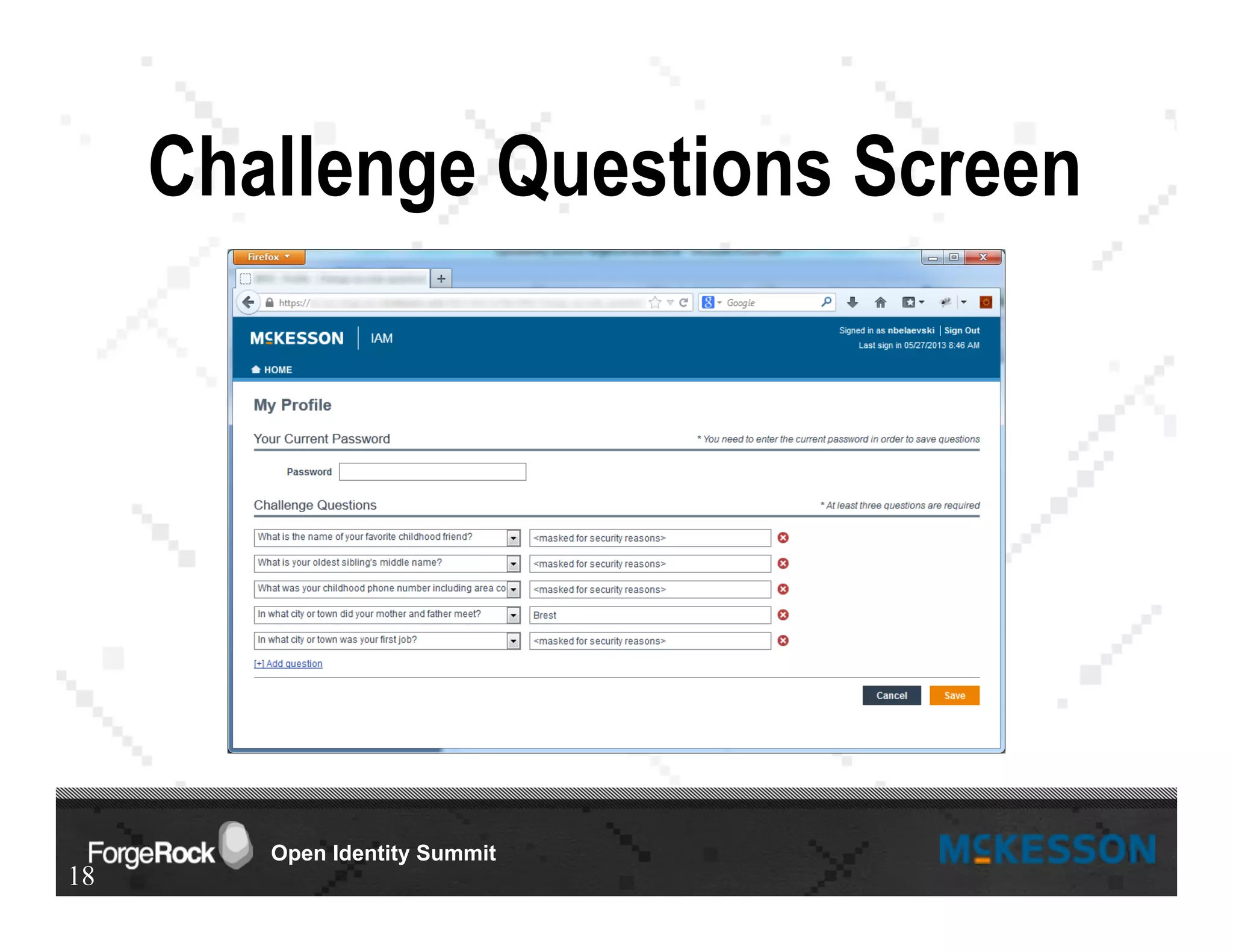
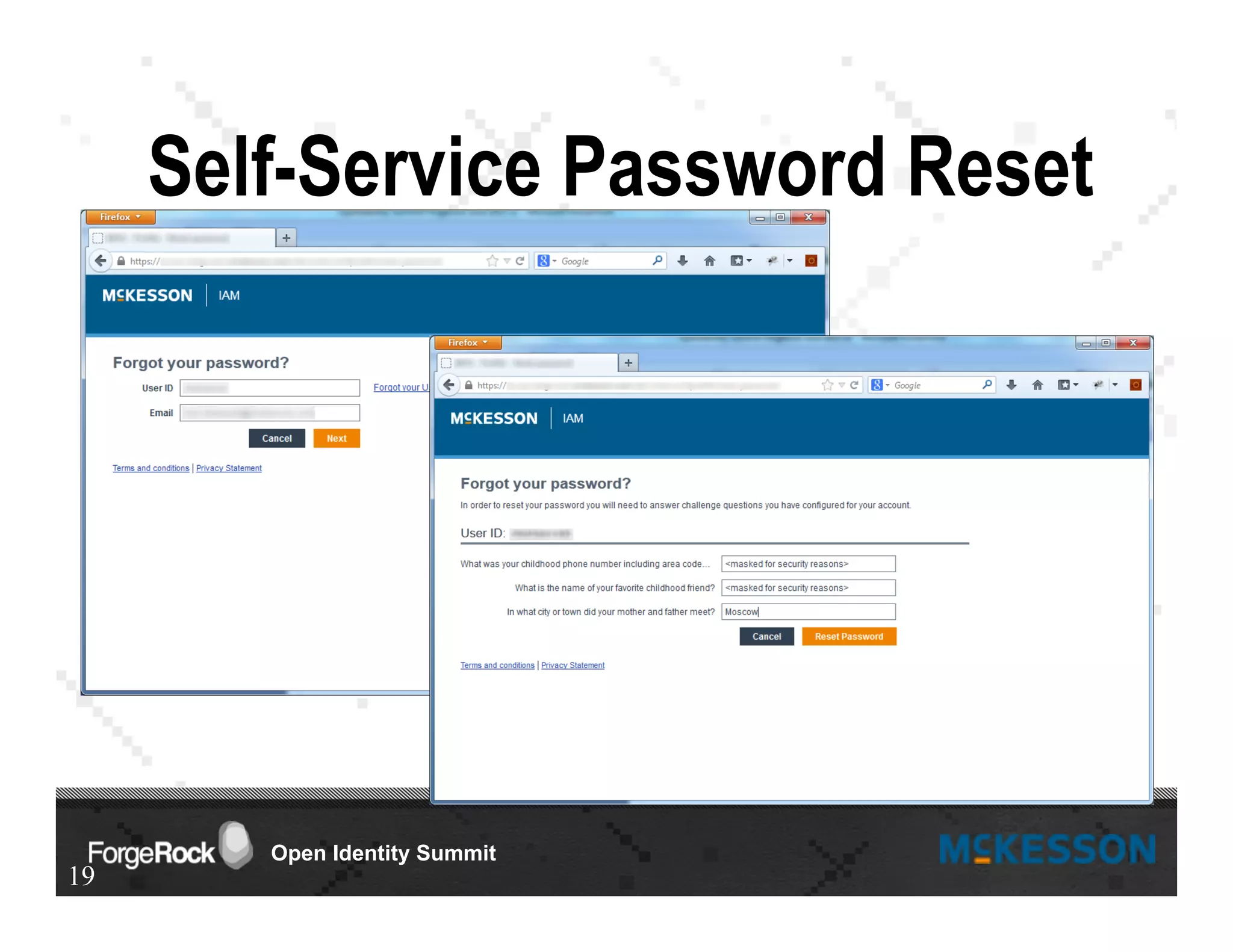
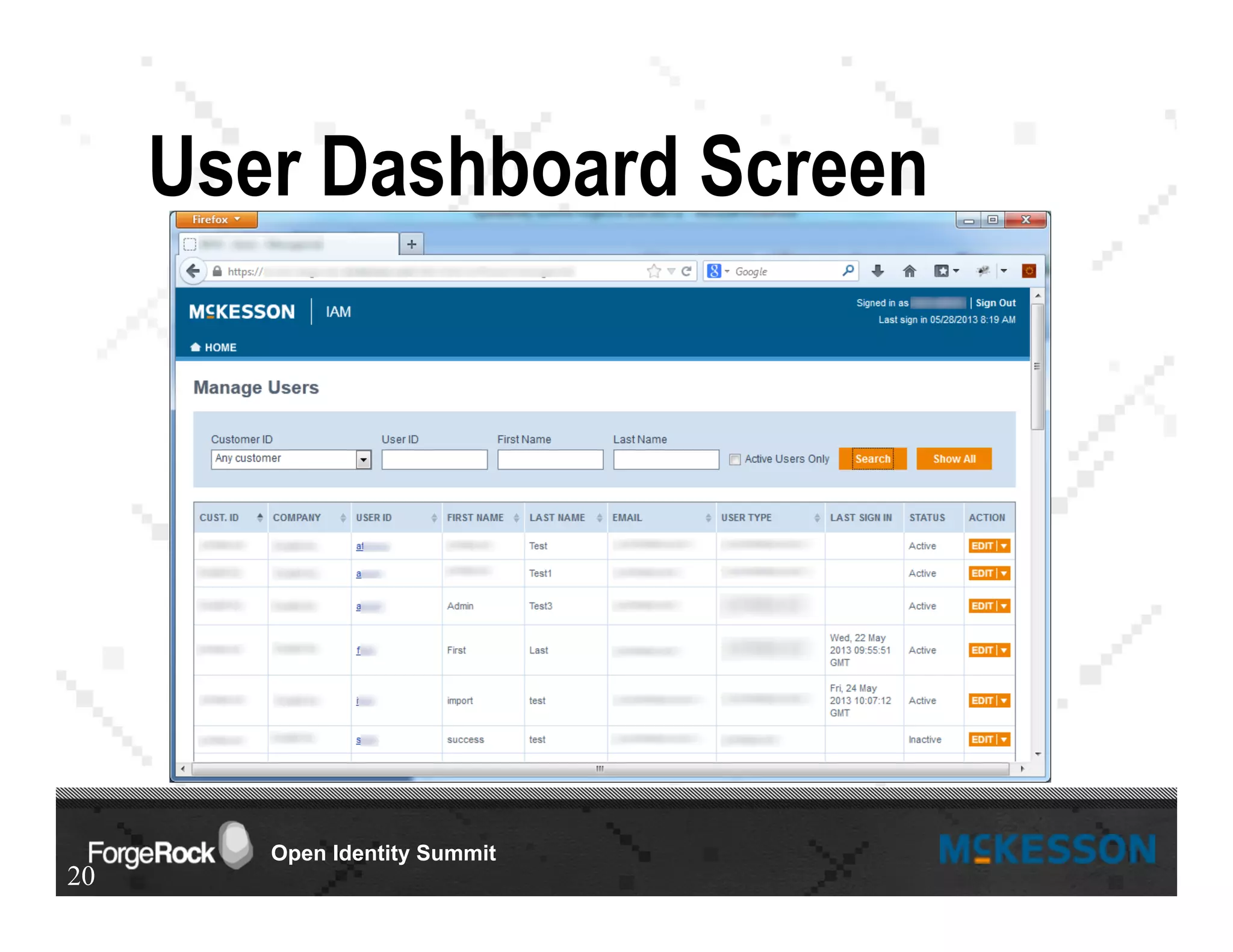
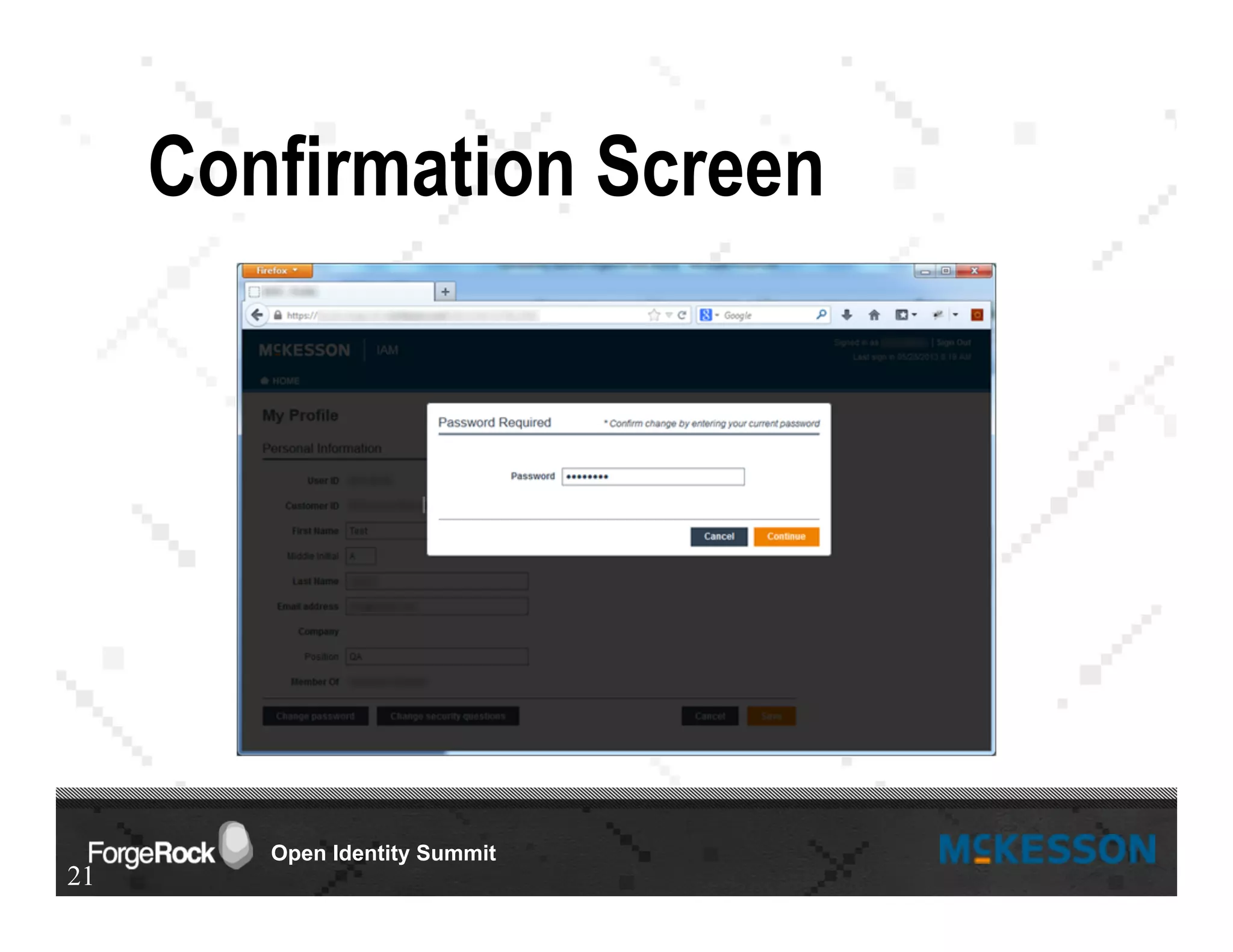
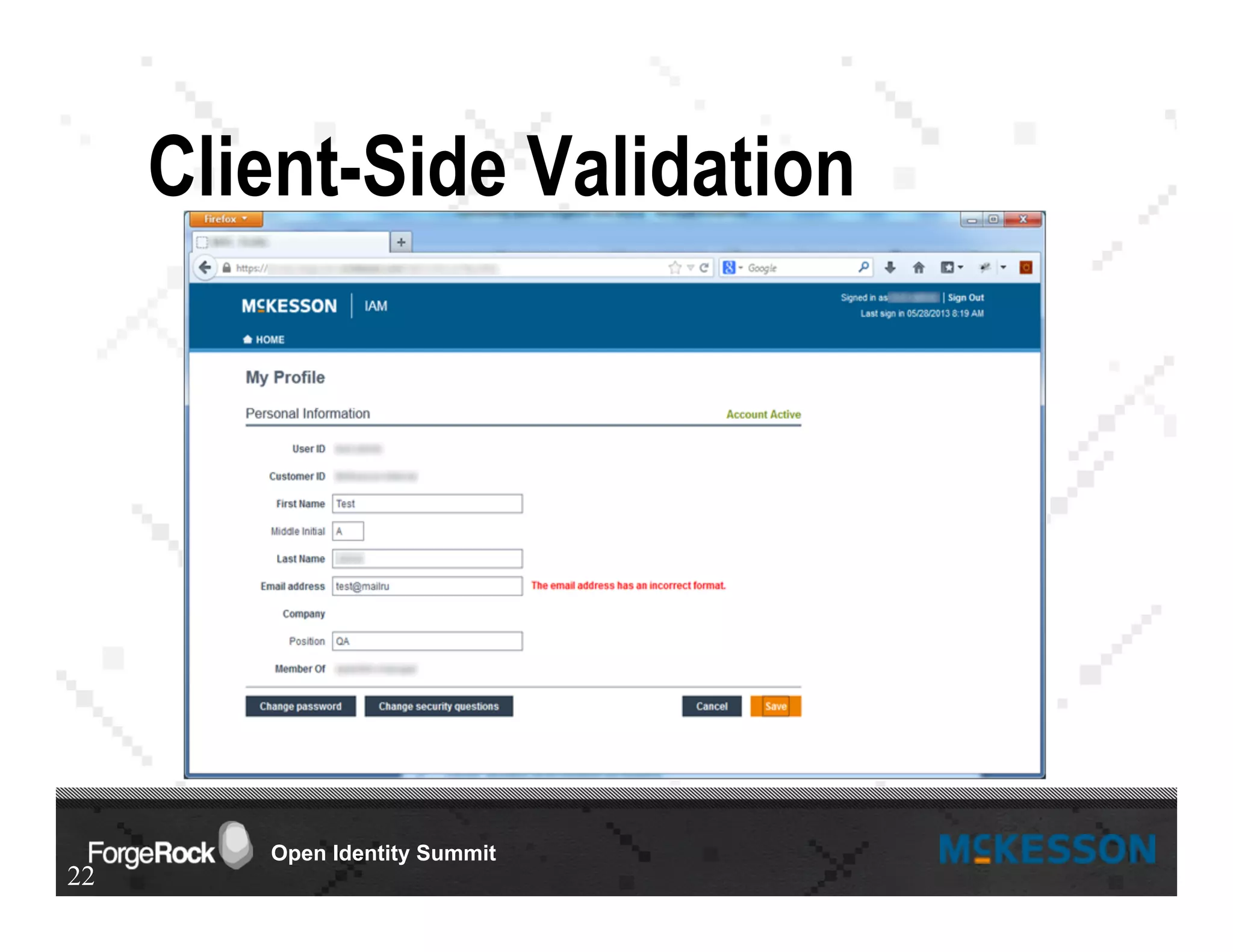
The document outlines a presentation at the Forgerock Open Identity Summit, detailing a partnership between McKesson Corporation and Exadel Inc. to deploy the Open Identity Stack. Key topics include the implementation of single sign-on solutions via Active Directory, user identity management use cases, and the architecture of the identity management user interface. The presentation emphasizes collaboration in creating a sustainable future for healthcare and provides contact information for further inquiries.