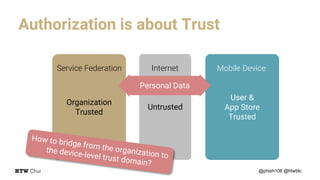
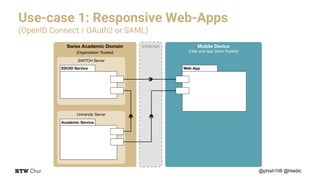
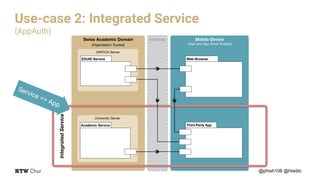
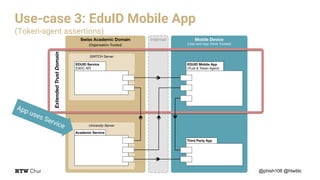
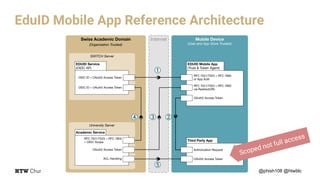
The document outlines the implementation and architecture of the eduid mobile app designed for smart environments in the Swiss academic domain, detailing three main use cases involving responsive web apps, integrated services, and a token-agent for enhanced security. It emphasizes the importance of trust among users, mobile devices, and app stores within a federated service structure utilizing open standards like OpenID Connect and OAuth2. Additionally, it highlights the full-stack integration of the app with various technologies, ensuring robust user management and strong encryption.