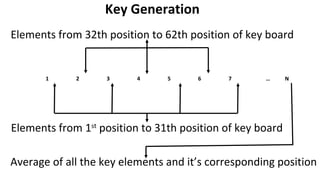
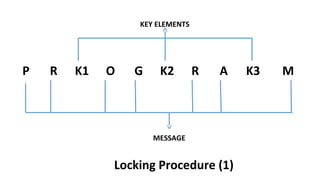
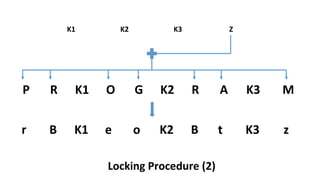
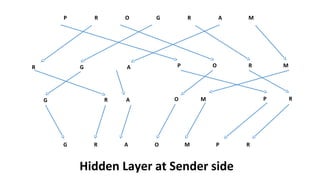
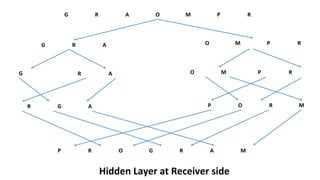
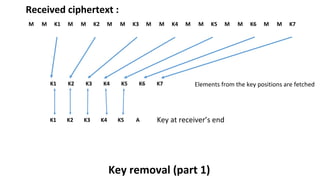
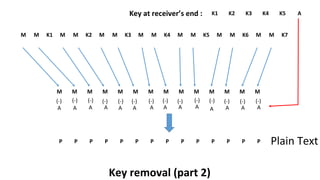
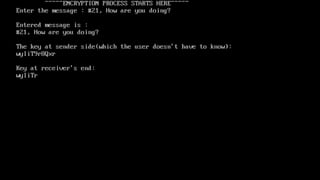
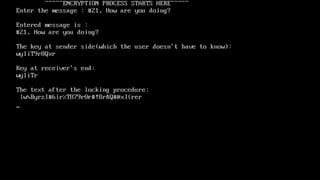
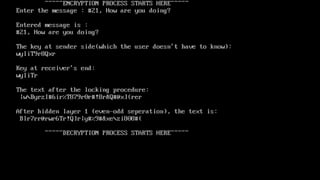
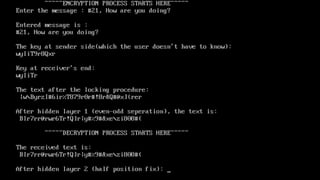
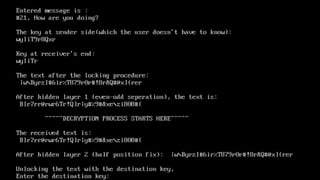
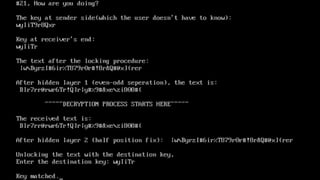
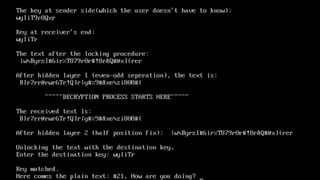
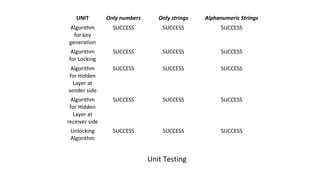
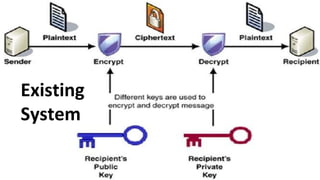
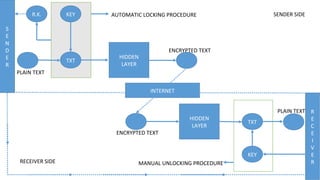
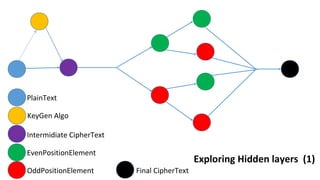
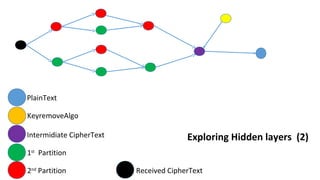
The document describes an encryption system utilizing dynamic key generation and asymmetric algorithms to secure plain text communication between sender and receiver. It outlines various procedures for locking and unlocking data, including the use of hidden layers for key management. Future enhancements could incorporate complex mathematical functions and additional hidden layers for improved security.



![Q W E R T Y U I O P
A S D F G H J K L Z
X C V B N M q w e r
t y u i o p a s d f
g h j k l z x c v b
n m 1 2 3 4 5 6 7 8
9 0 @ # $ % ^ & _ ~
` ! + - * / | { }
[ ] ( ) = : ; “ ‘ <
> , . ?](https://image.slidesharecdn.com/collegeprojectfinalcompatibleslideshare-170213115738/85/Dynamic-data-encryption-using-the-concepts-of-ANN-9-320.jpg)