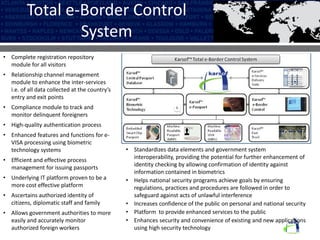
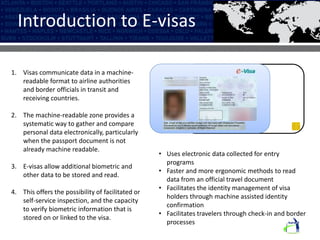
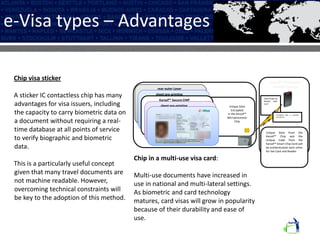
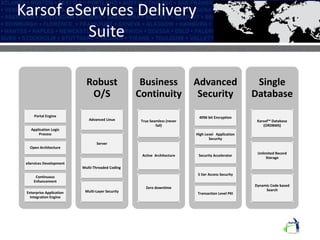
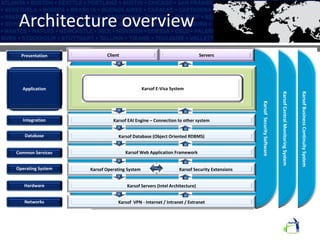
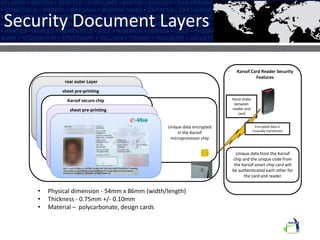
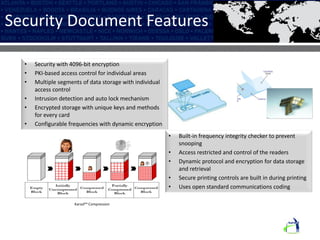
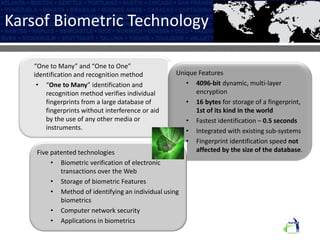
The Karsof eVisa Solution provides a comprehensive e-border control system with modules for visitor registration, relationship management between government services, compliance monitoring of foreigners, and enhanced e-VISA processing using biometric technology. The system features secure authentication, standardized data sharing between government systems, and helps ensure national security regulations are followed while increasing public confidence. Key components include an encrypted biometric chip for visas, biometric matching at fast track kiosks, an integrated manufacturing facility, and one-to-many biometric identification technology.