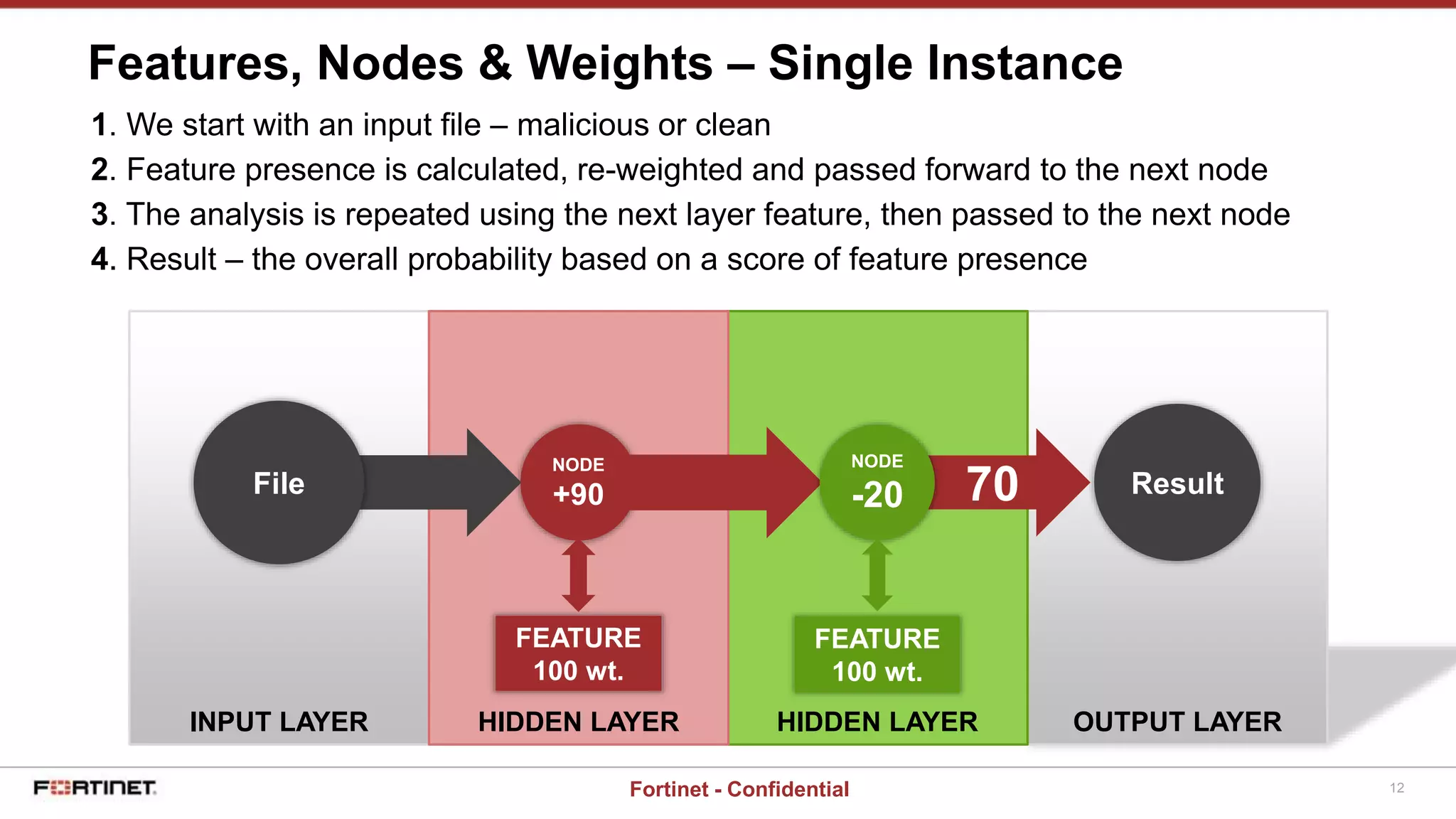
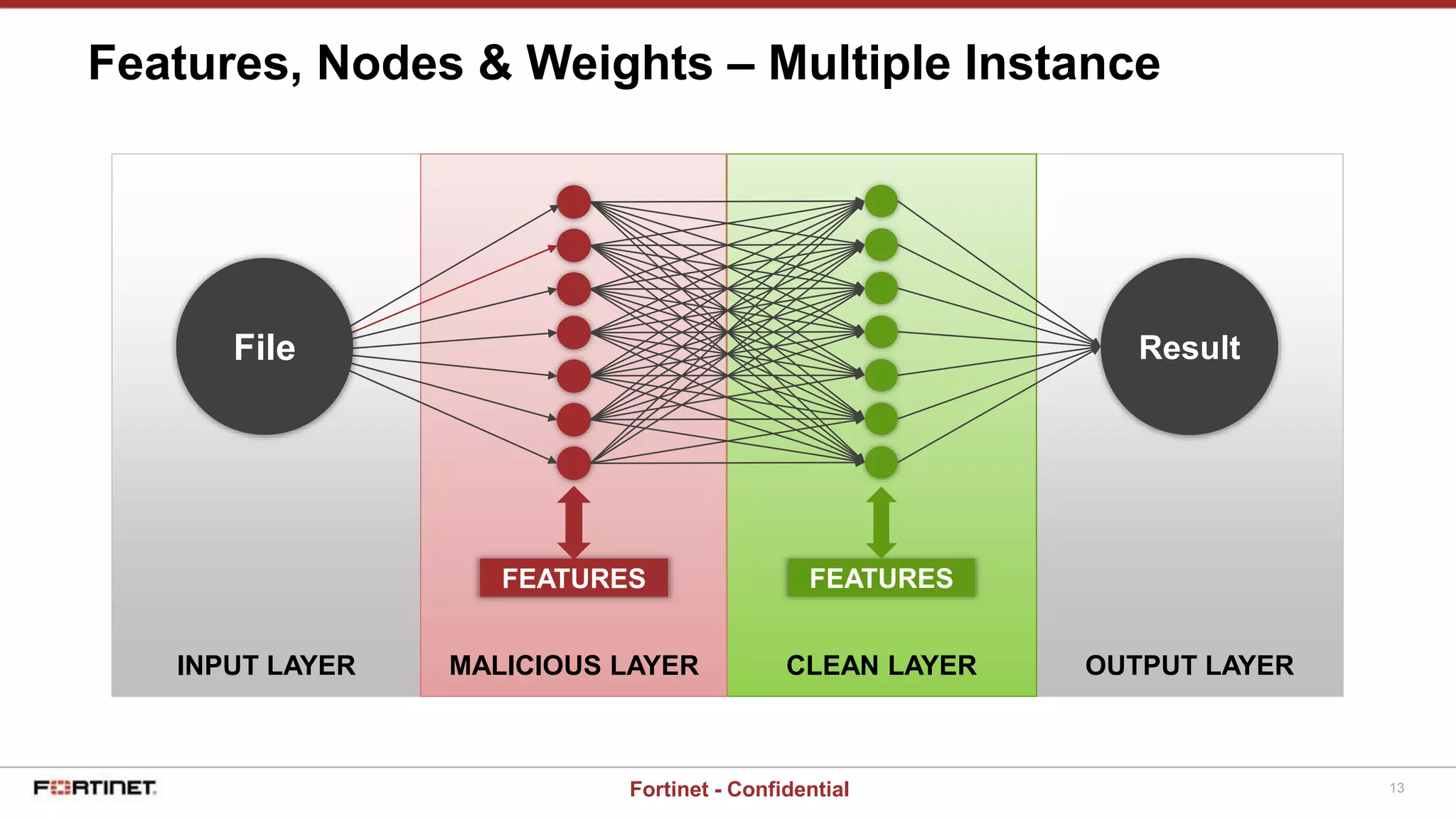
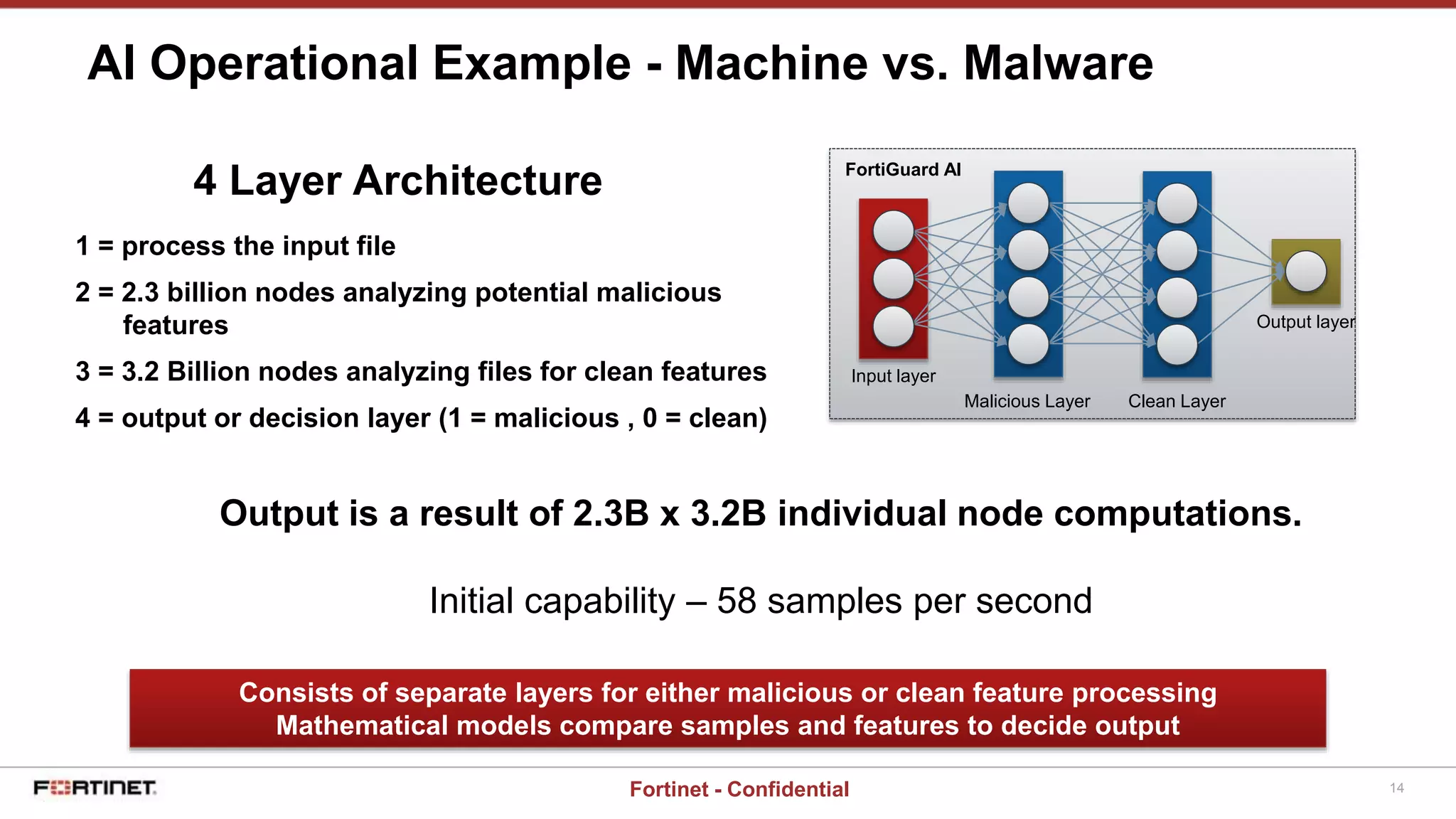
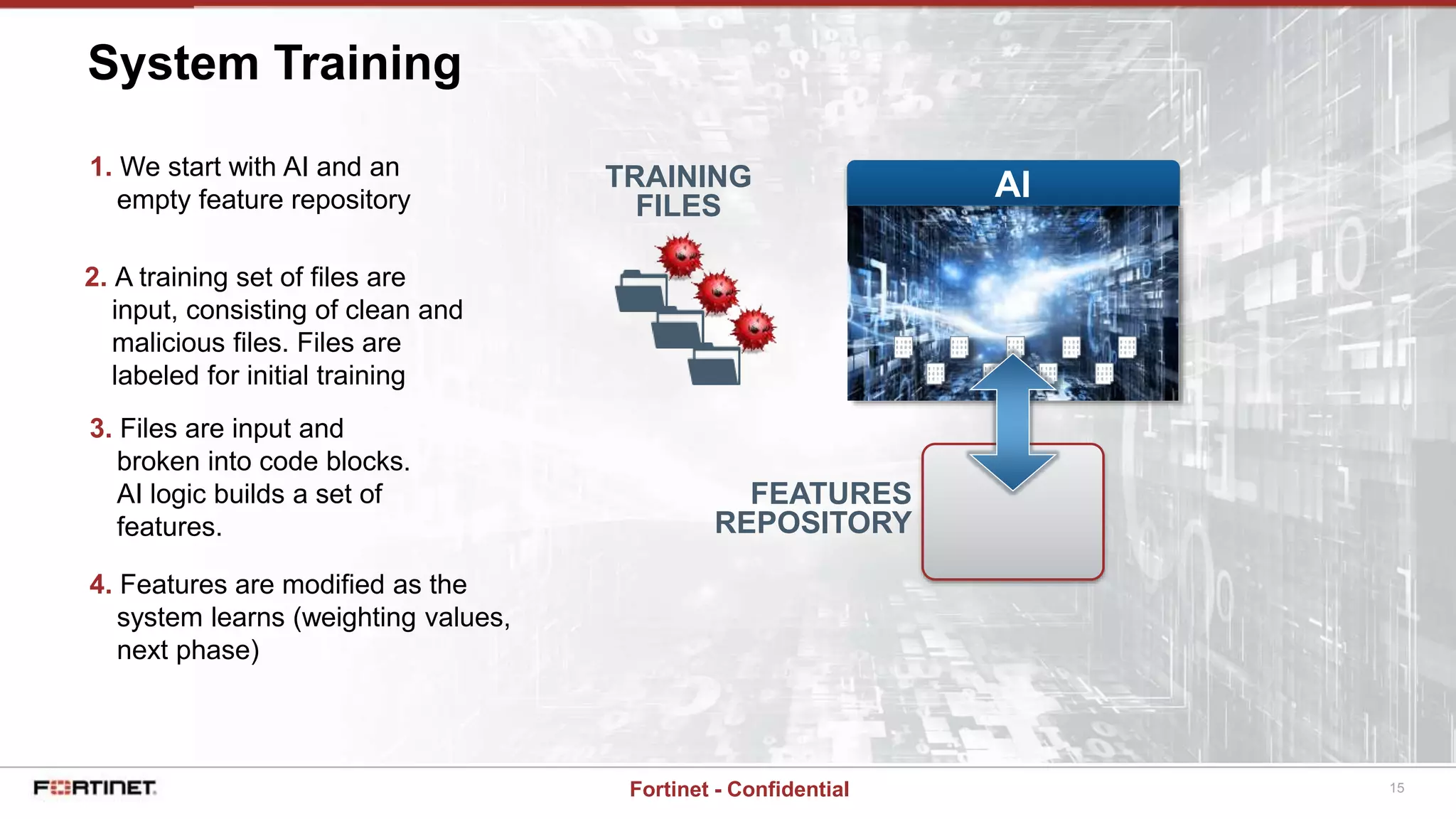
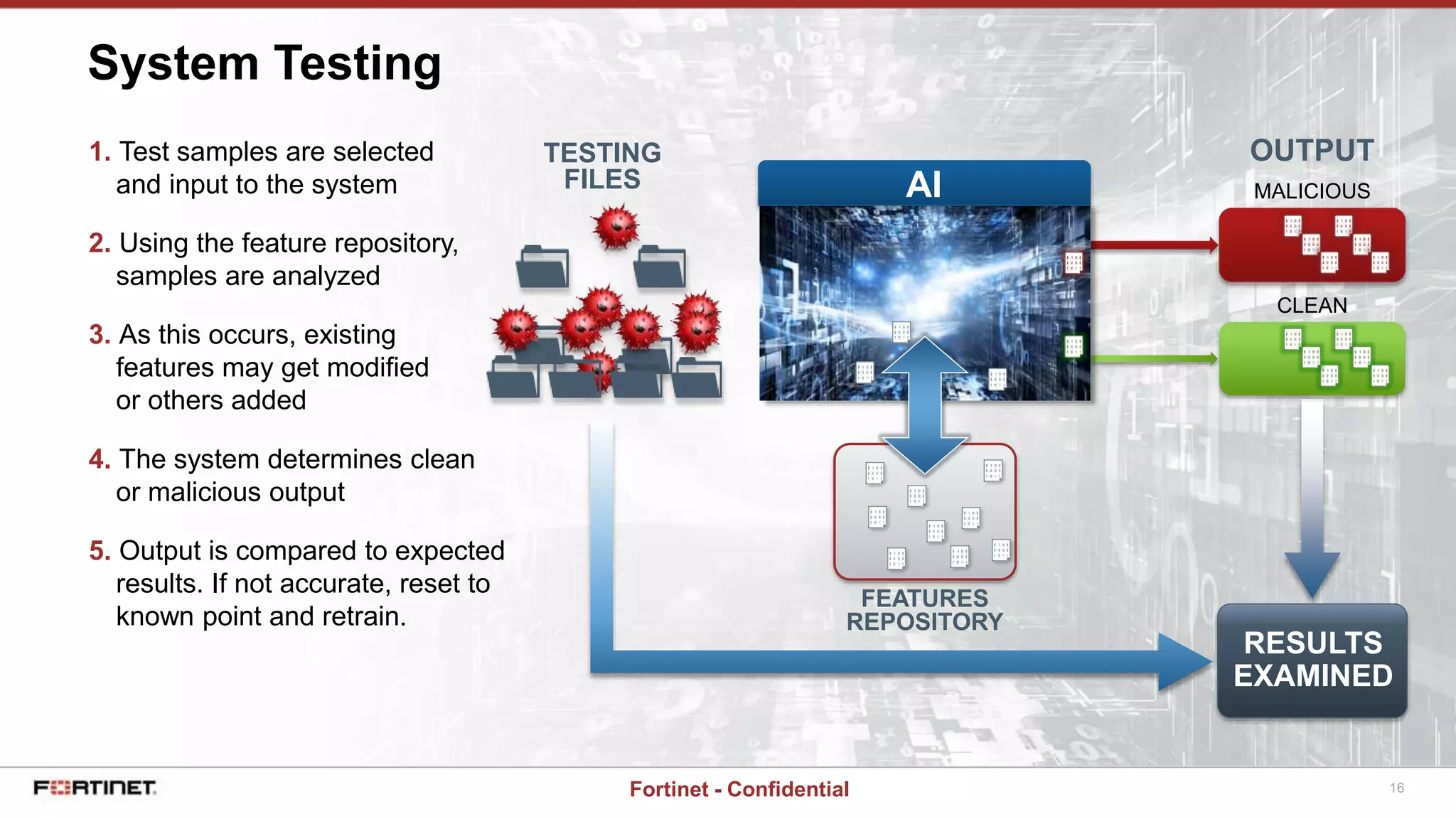
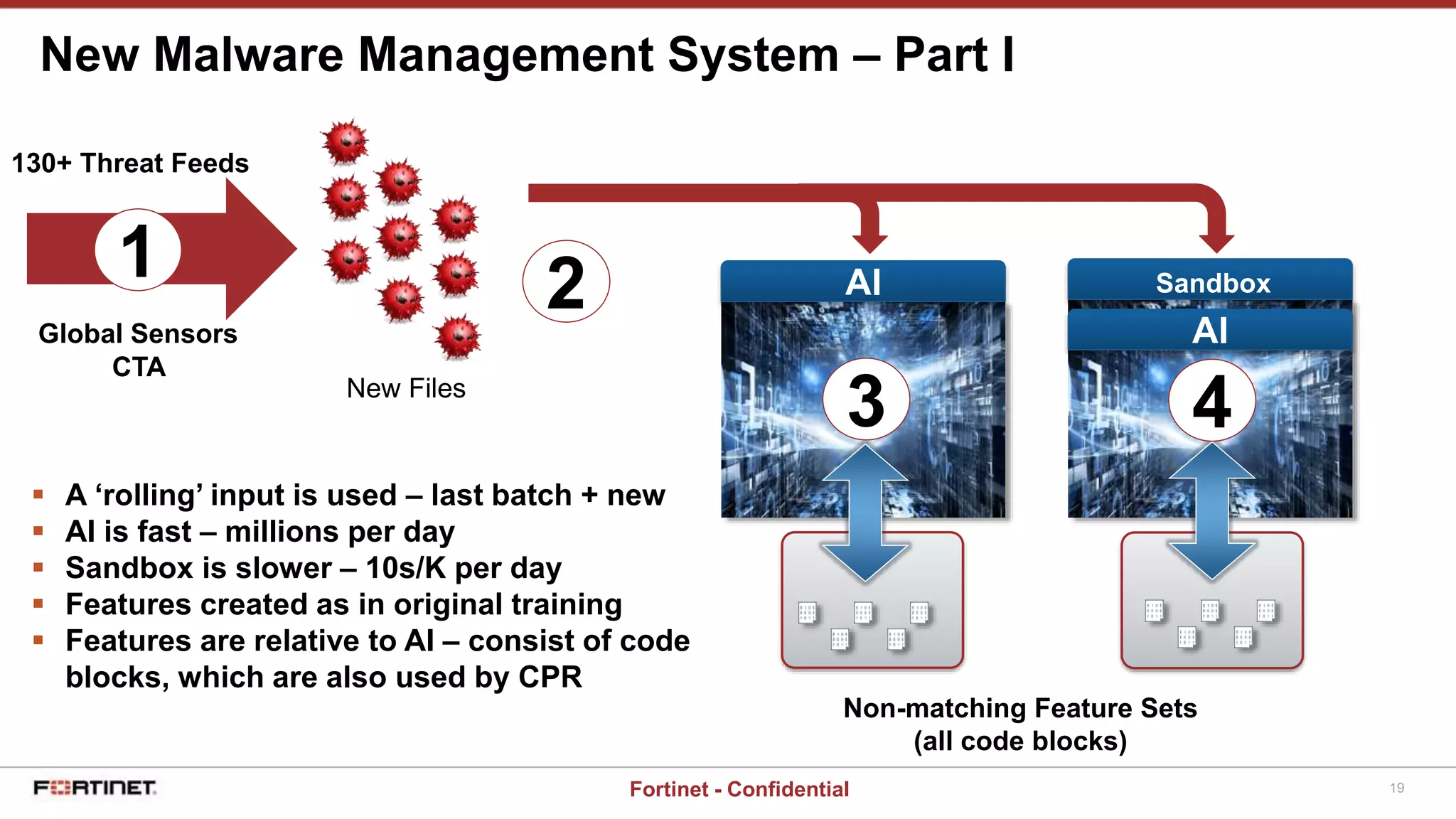
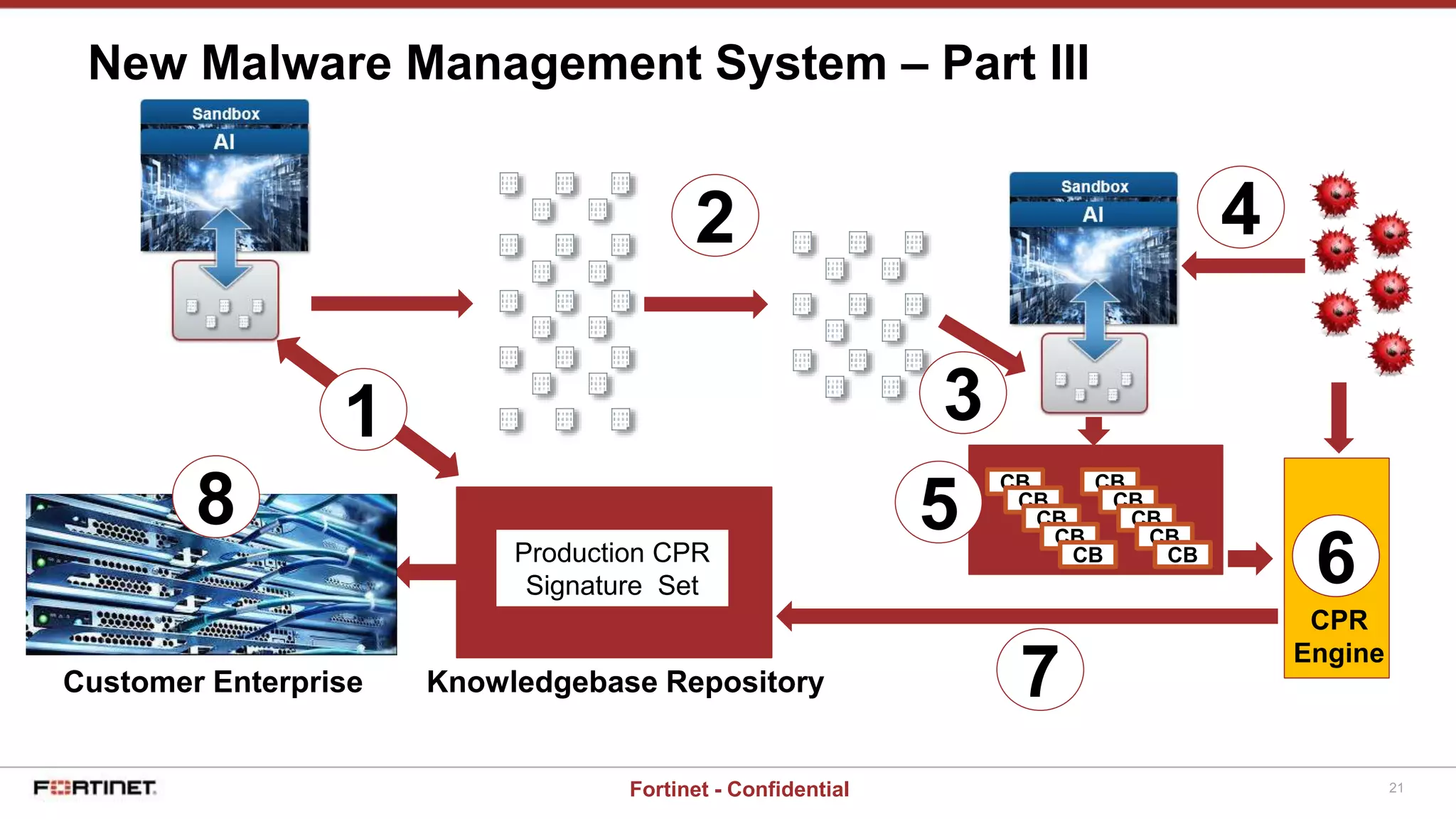
This document provides a high-level overview of an AI-based malware detection system. The system uses a multilayer perceptron neural network with over 5 billion nodes that analyzes files and extracts features to determine if files are malicious or clean. It continuously trains and improves itself by processing large volumes of known malware and benign files. The system also has a separate process for introducing new unknown malware samples in a controlled way to generate new features without disrupting the existing network.