The document provides an overview of digital rights management (DRM), including its history, functional architecture, interested players, examples of implementation, relevant laws and controversies. DRM aims to protect digital content creators while enabling access, but is criticized for hindering fair use and progress. The future of DRM involves standardization to support applications like digital libraries and education.



![Conti…. It can also refer to restrictions associated with specific instances of digital works or devices. Digital rights management is used by companies such as Sony , Amazon , Apple Inc. , Microsoft , AOL and the BBC . The use of digital rights management is controversial. Proponents argue it is needed by copyright holders to prevent unauthorized duplication of their work, either to maintain artistic integrity [1] or to ensure continued revenue streams DRM technologies attempt to control use of digital media by preventing access, copying or conversion to other formats by end users .](https://image.slidesharecdn.com/drm-muruli-110616044645-phpapp02/75/Digital-Rights-Management-5-2048.jpg)
![Conti… DRM technologies have enabled publishers to enforce access policies that not only disallow copyright infringements , but also prevent lawful fair use of copyrighted works, or even implement use constraints on non-copyrighted works that they distribute DRM is most commonly used by the entertainment industry (e.g., film and recording ). [6] Many online music stores , such as Apple Inc. 's iTunes Store , as well as many e-book publishers have implemented DRM. In recent years, a number of television producers have implemented DRM on consumer electronic devices to control access to the freely-broadcast content of their shows, in response to the rising popularity of time-shifting digital video recorder systems](https://image.slidesharecdn.com/drm-muruli-110616044645-phpapp02/75/Digital-Rights-Management-6-2048.jpg)



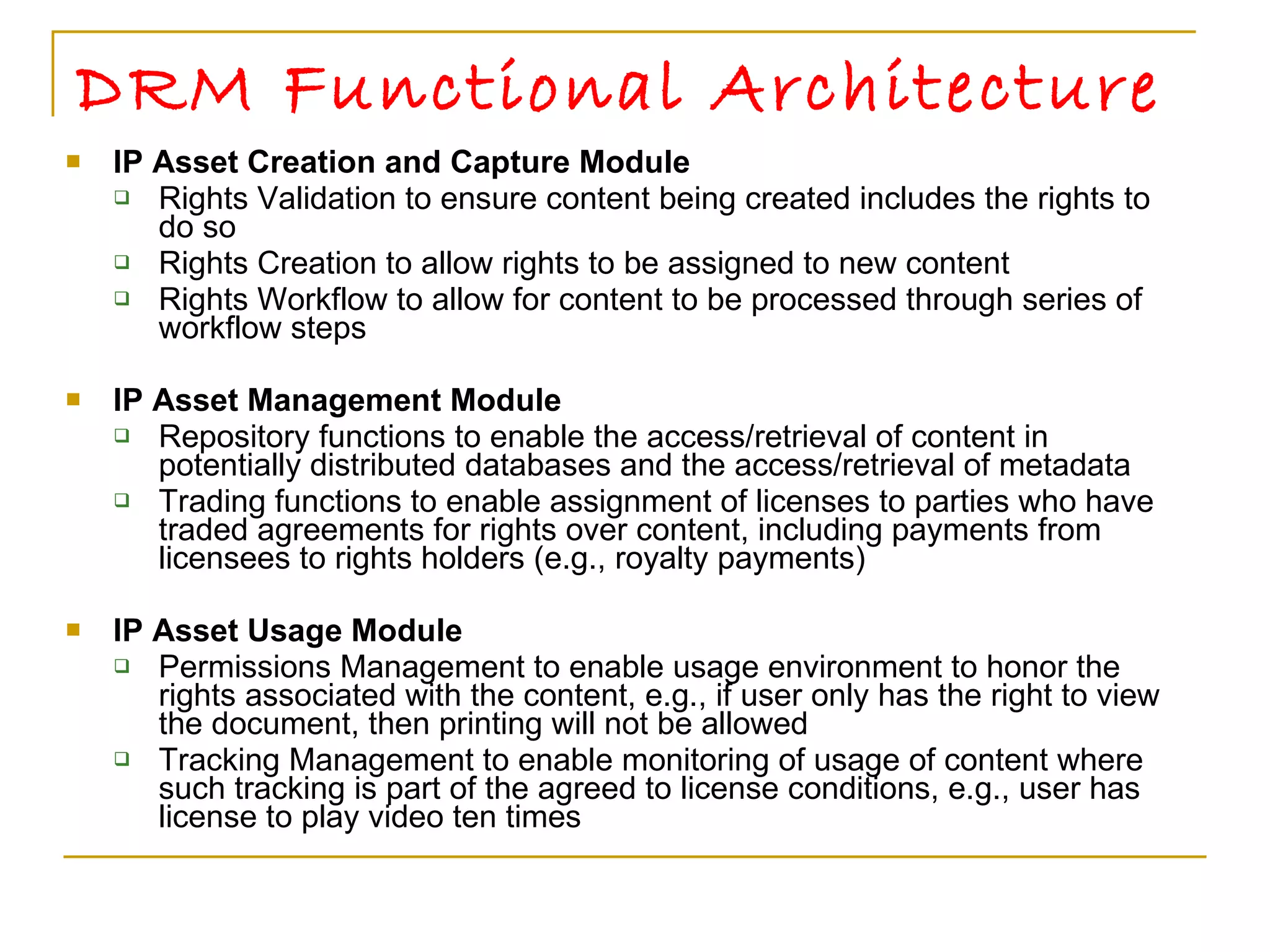
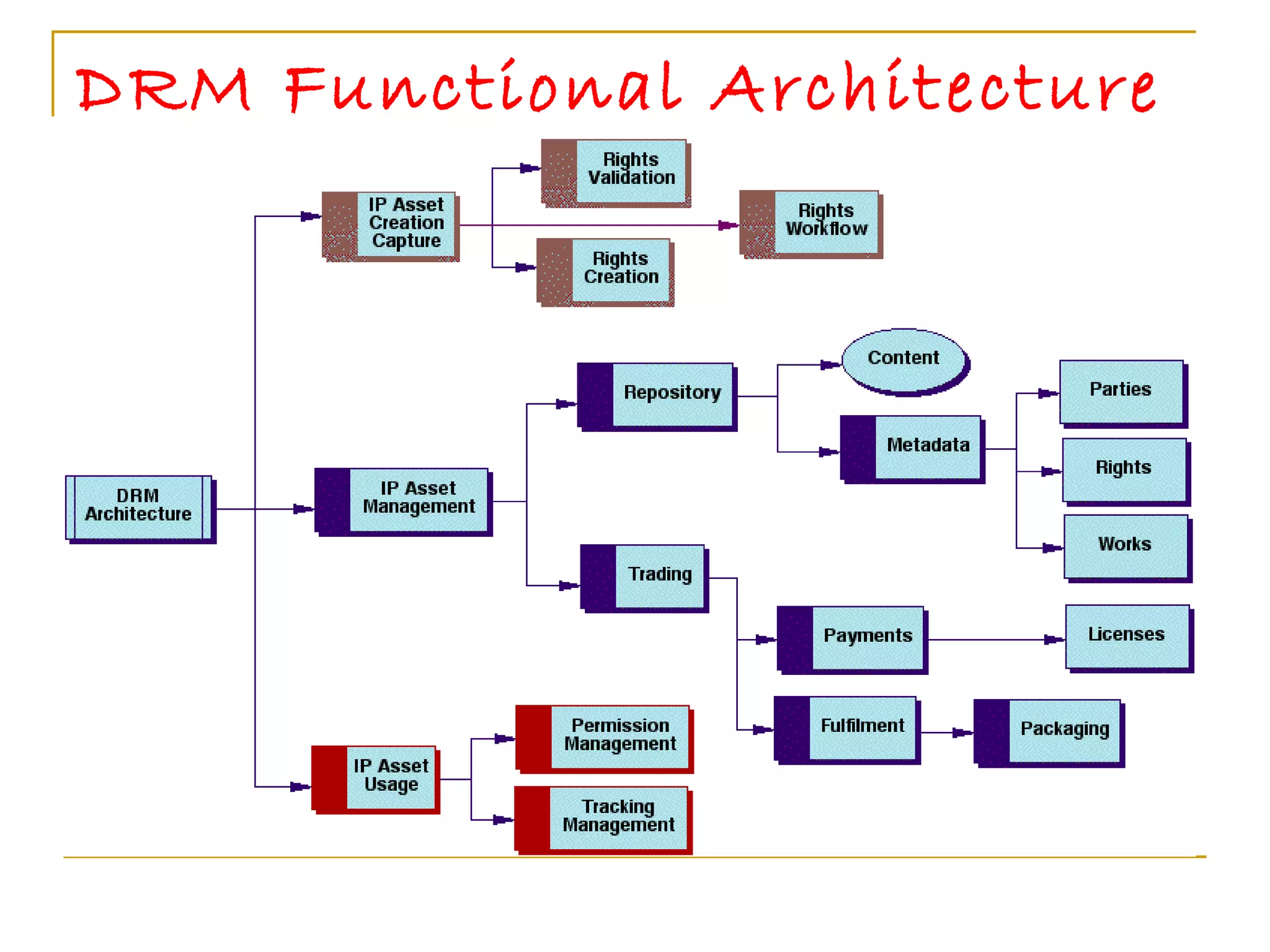



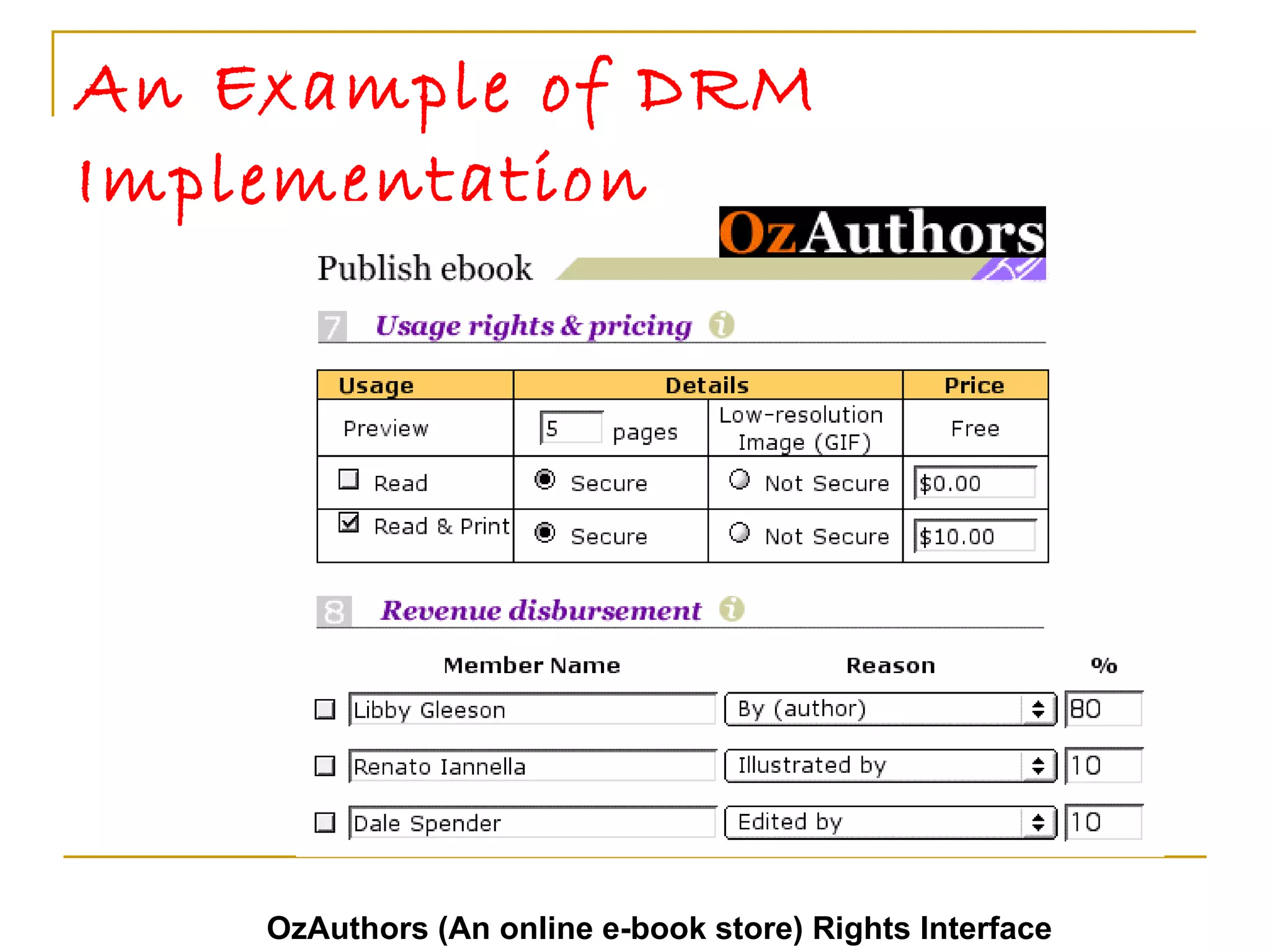




![The Future of DRM DRM standardization is occurring in a number of open organizations. The Open EBook Forum [OEBF] and the MPEG group [MPEG] are leading the charge for the eBook and multimedia sectors. The Internet Engineering Task Force [IETF] and the World Wide Web Consortium [W3C] have also commenced work on DRM issues. Their work will be important for the entire DRM sector, and it is also important that all communities be heard during these standardization processes in industry and sector-neutral standards organizations.](https://image.slidesharecdn.com/drm-muruli-110616044645-phpapp02/75/Digital-Rights-Management-23-2048.jpg)


