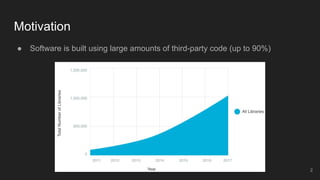
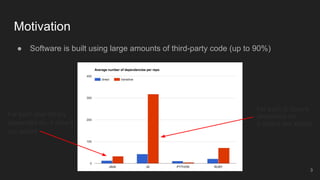
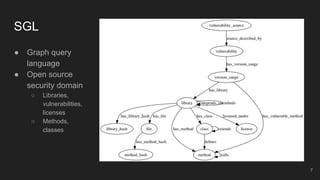
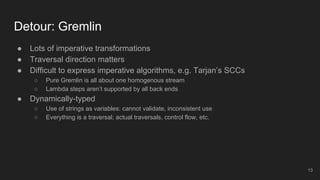
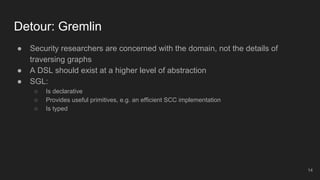
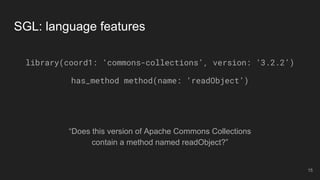
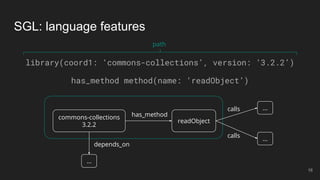
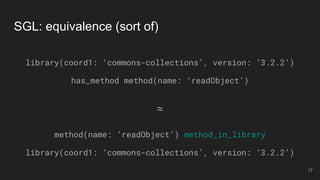
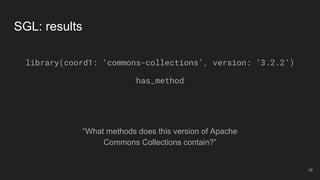
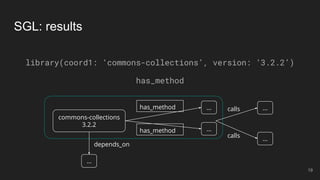
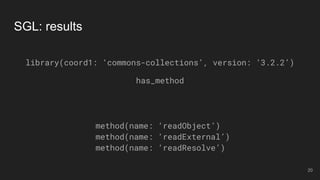
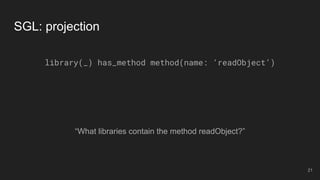
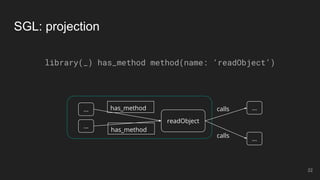
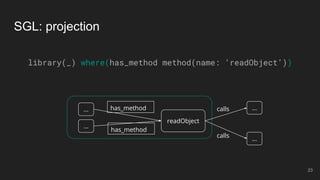
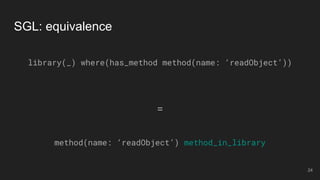
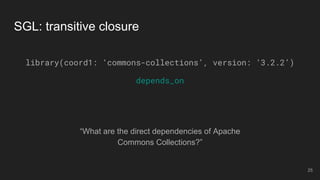
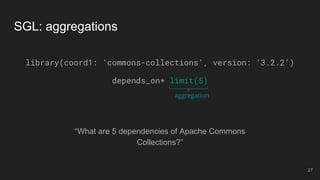
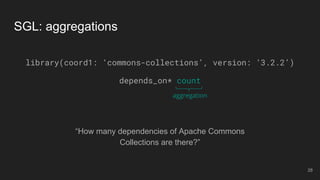
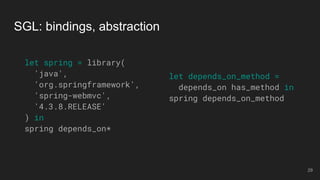
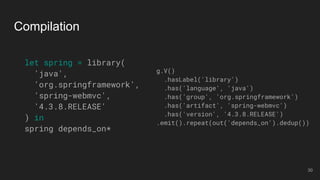
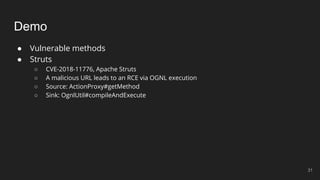
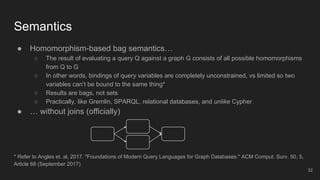
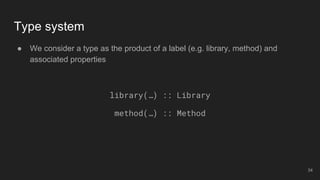
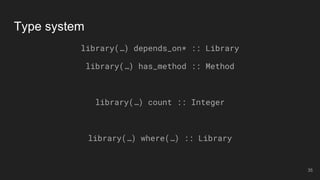
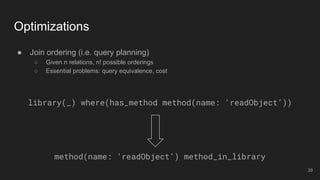
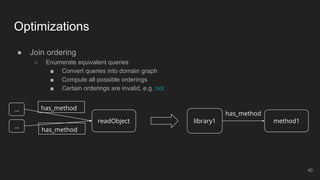
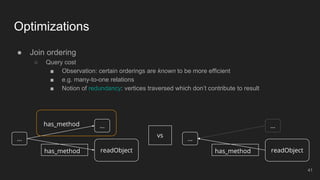
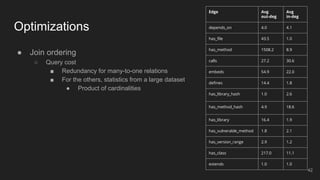
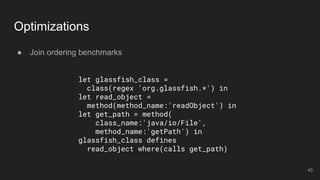
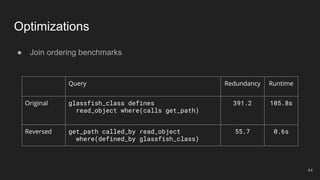
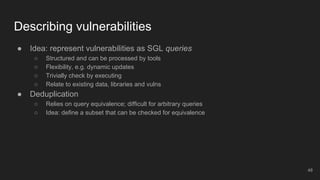
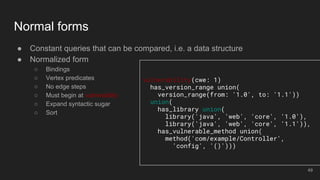
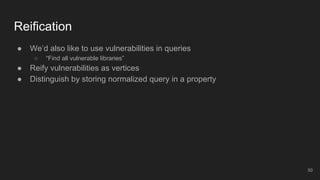
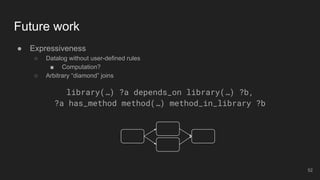
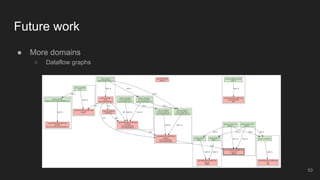
The document outlines the design and implementation of a Security Graph Language (SGL) to automate the auditing of third-party code dependencies in software, addressing the challenges posed by vulnerabilities in external libraries. It discusses the limitations of existing tools and presents SGL as a declarative language that enables structured querying of security-related data. The document also highlights various use cases, optimizations, and future work related to the application of SGL in identifying and managing security vulnerabilities.