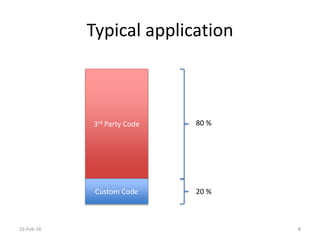
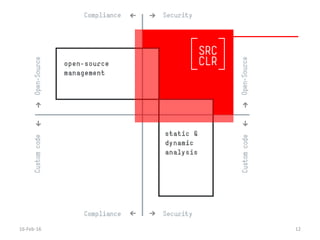
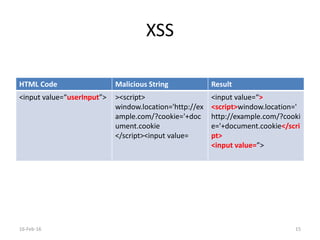
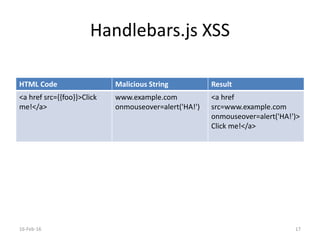
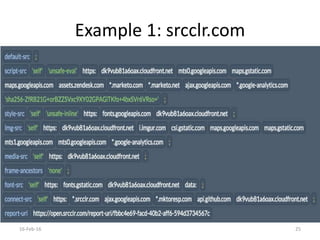
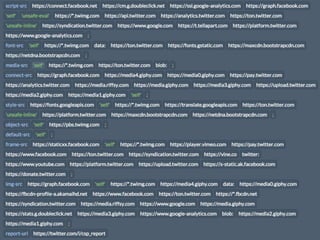
The document discusses the importance of software security, emphasizing the need to address vulnerabilities in third-party libraries often used by developers. It highlights the risks associated with open-source components, particularly how vulnerabilities can affect multiple applications. Recommendations include auditing library usage and implementing content security policies to enhance protection against attacks like cross-site scripting.