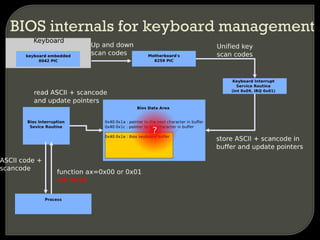
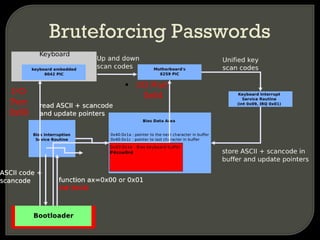
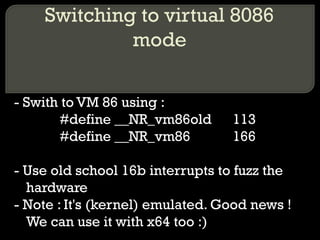
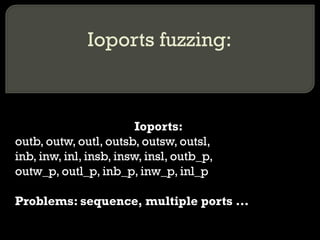
The document discusses various techniques for attacking virtualization systems and escalating privileges. It begins with an overview of virtualization definitions and market shares. It then covers methods such as privilege escalation on guest systems and the host, attacking isolation between guest operating systems, denial of service attacks targeting both the host and guests, and escaping the virtualized environment to the host system. Specific vulnerabilities and research are referenced to illustrate different attack vectors. The document concludes with a discussion of fuzzing the hypervisor or host operating system through techniques like virtual 8086 mode, I/O port fuzzing, and PCI device fuzzing to identify new ways to escalate privileges on the host system.