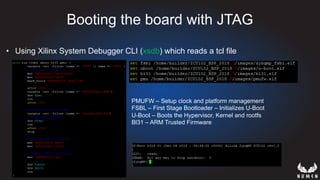
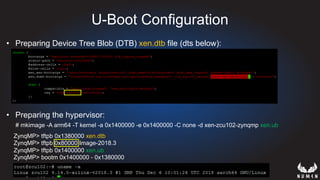
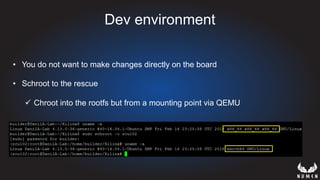
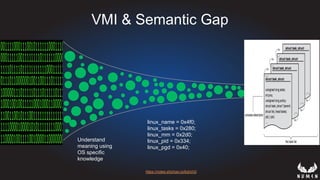
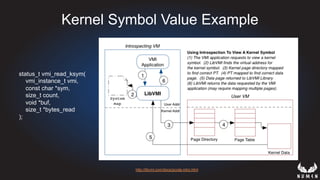
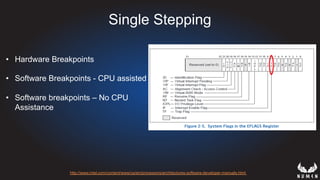
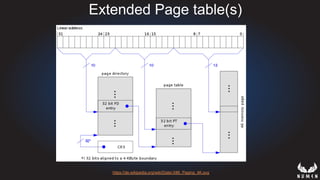
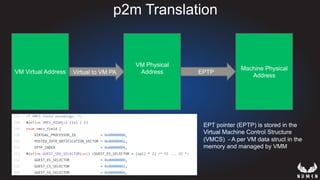
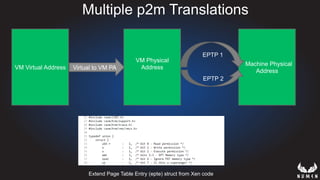
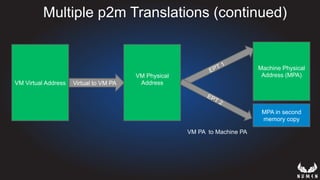
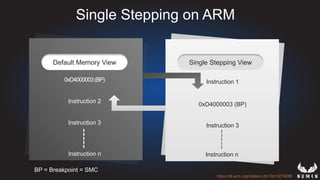
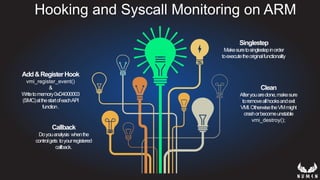
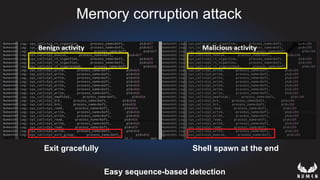
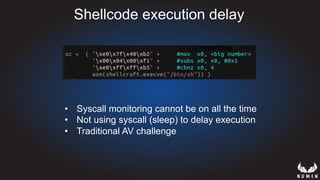
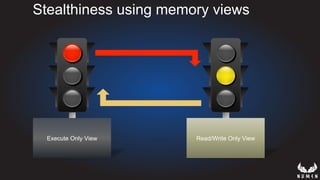
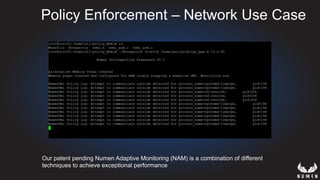
This document discusses using hypervisors to monitor devices for cyber attacks. It begins with discussing agent-less vs agent monitoring and then demonstrates setting up a development environment using a Zynq UltraScale+ MPSoC board with Xen hypervisor. It shows building a root filesystem, getting ARM syscalls, and using virtual machine introspection to monitor syscalls and memory. Various attack scenarios are demonstrated like shellcode execution and malware awareness. It concludes with recommendations for an end-to-end monitoring system and releasing the tools developed.