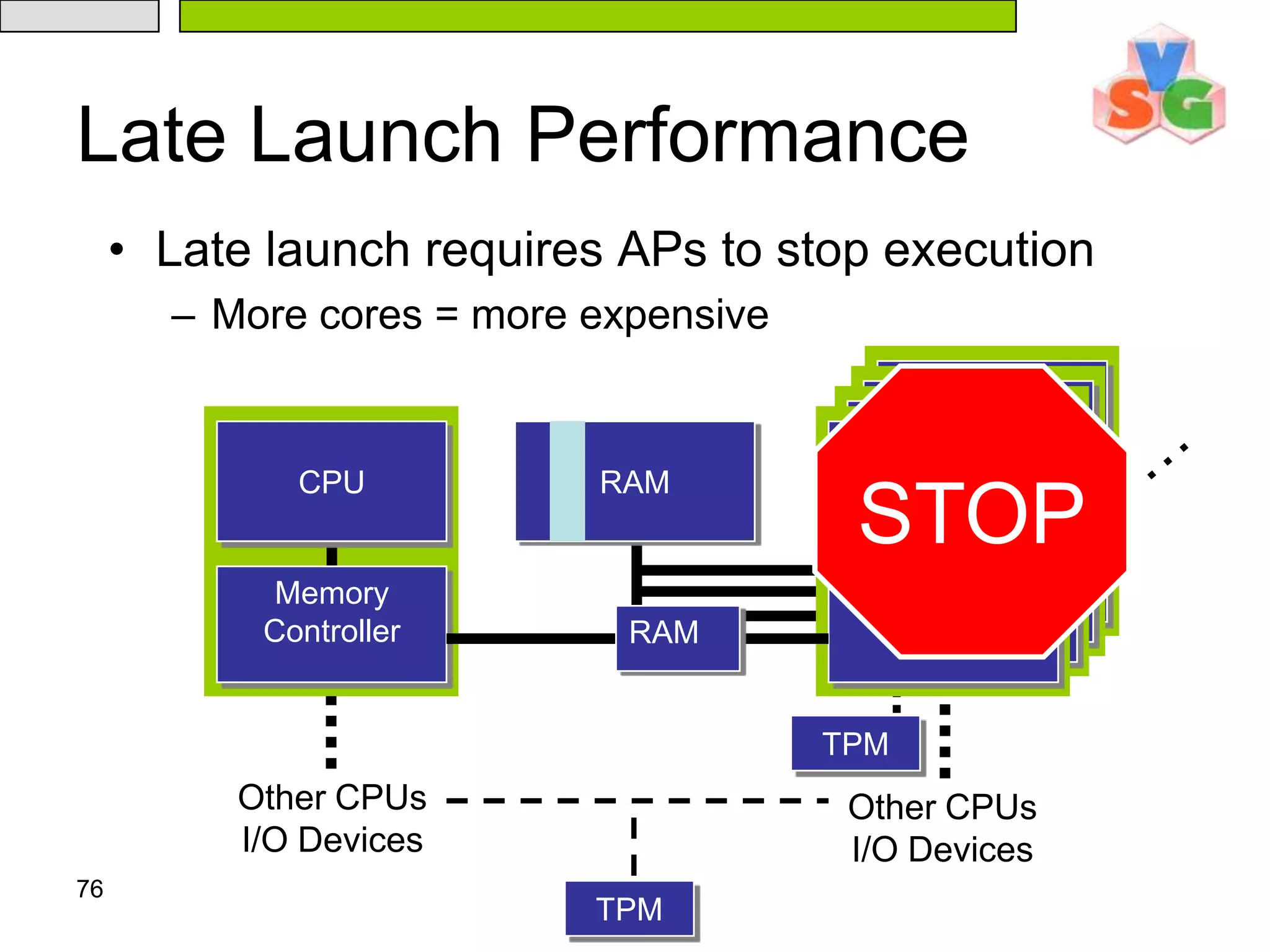
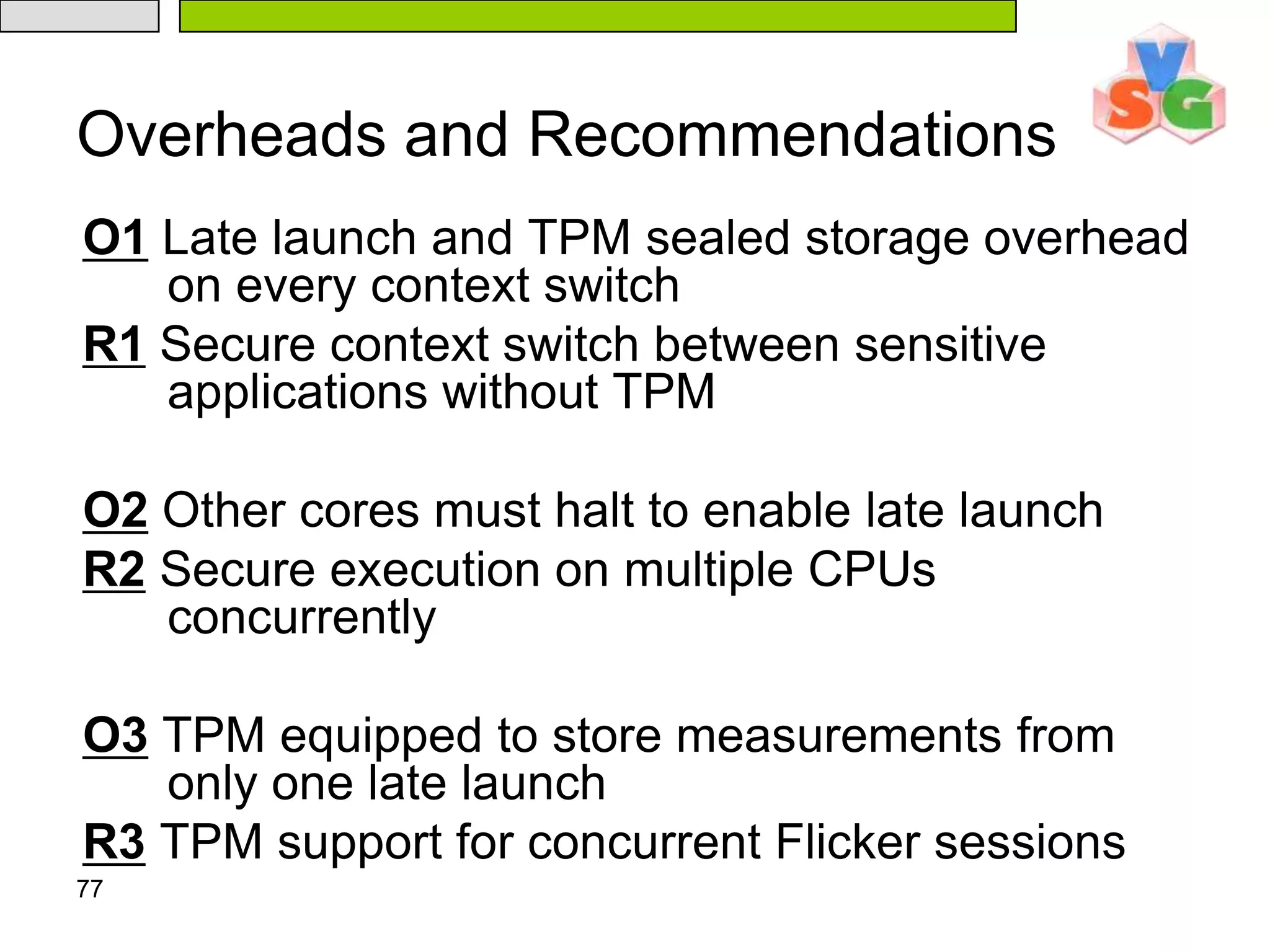
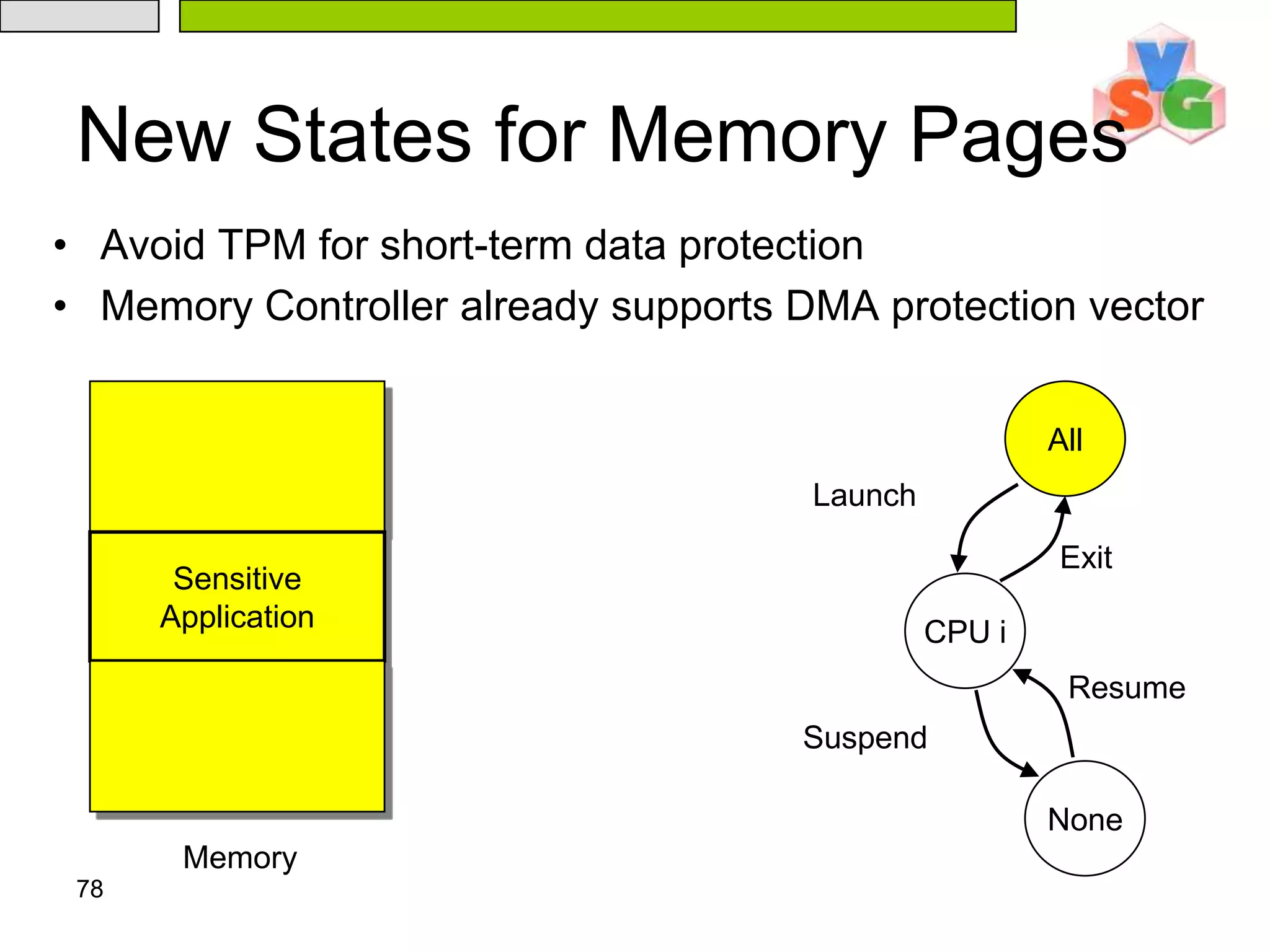
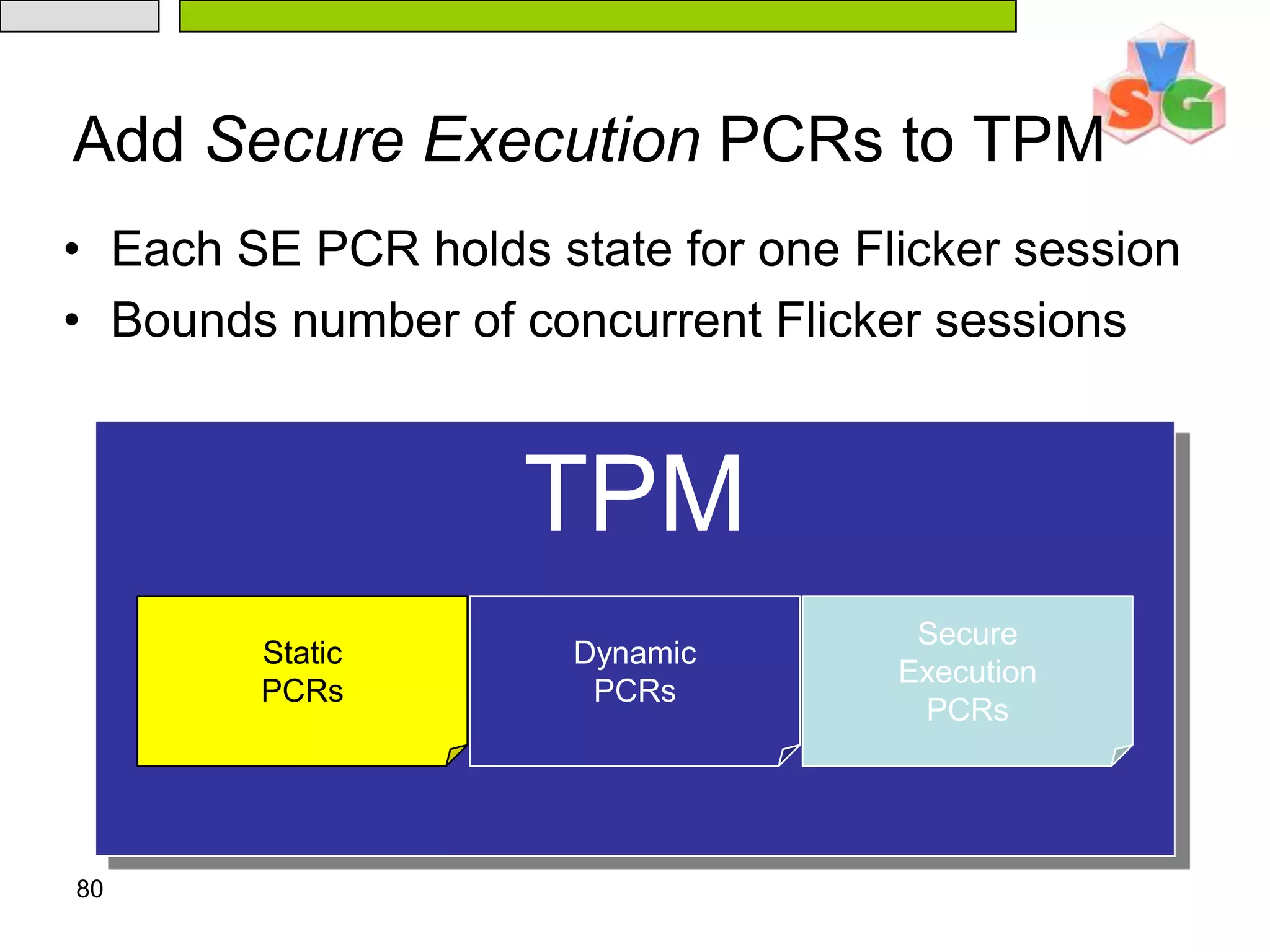
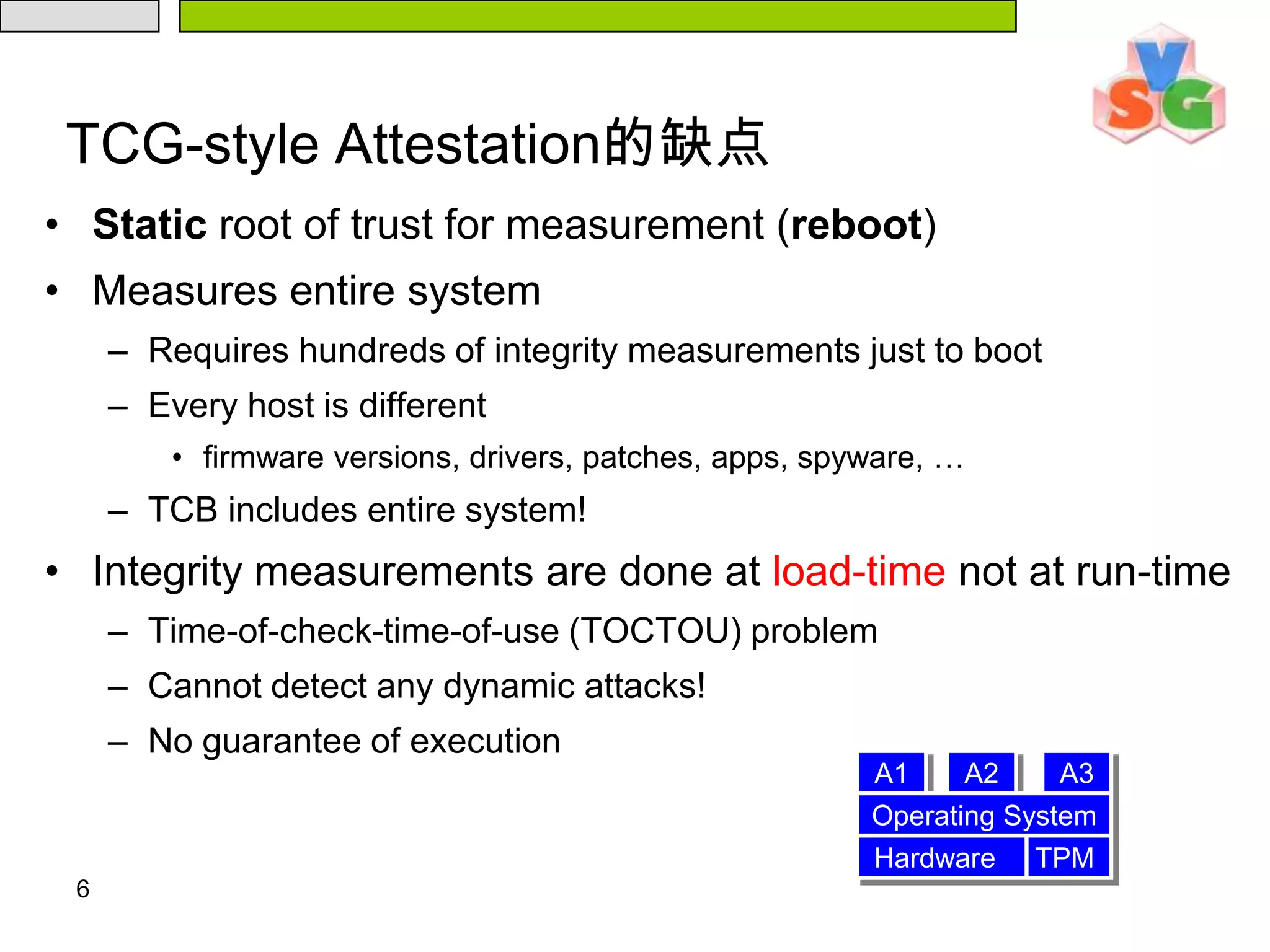
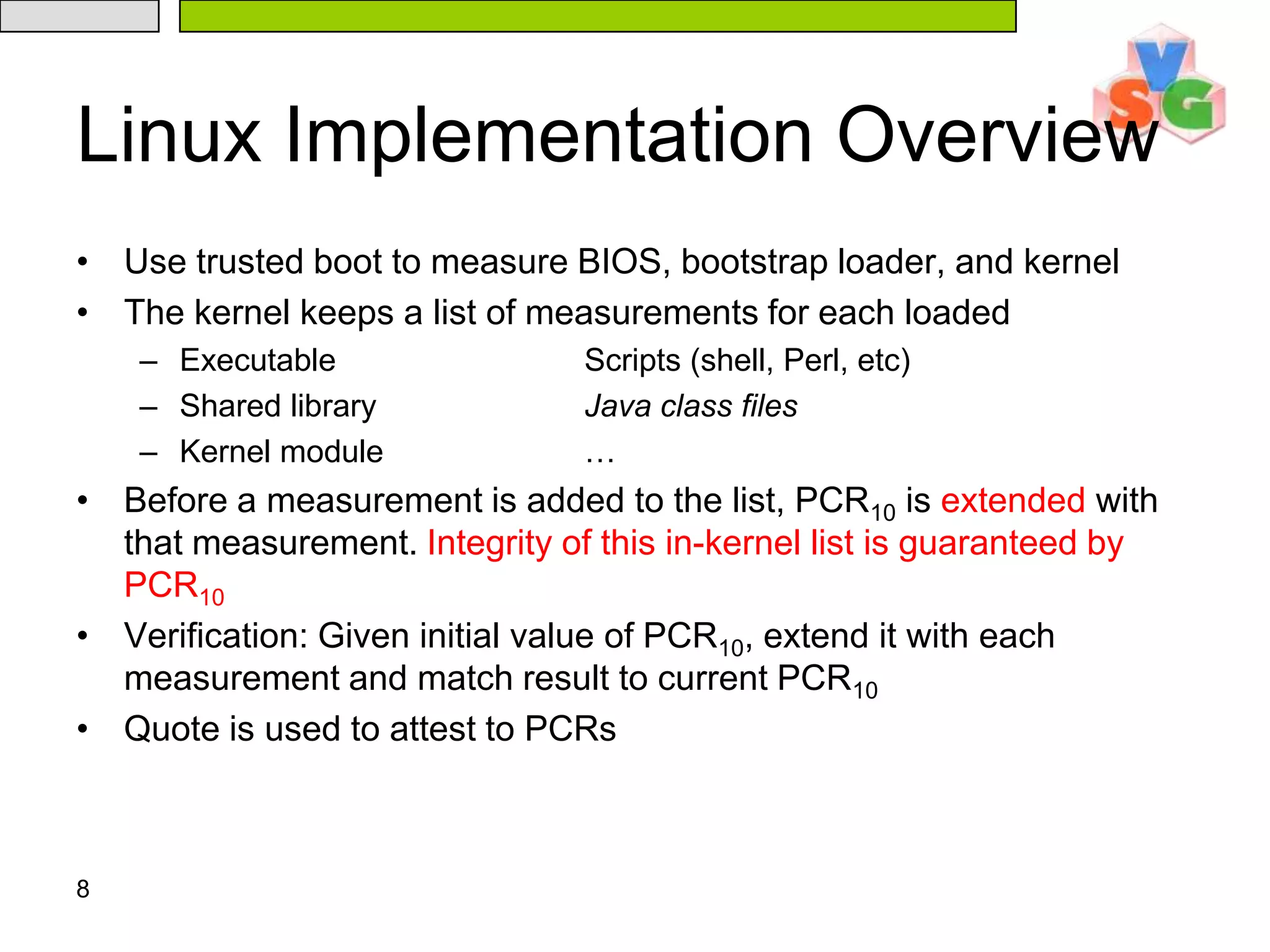
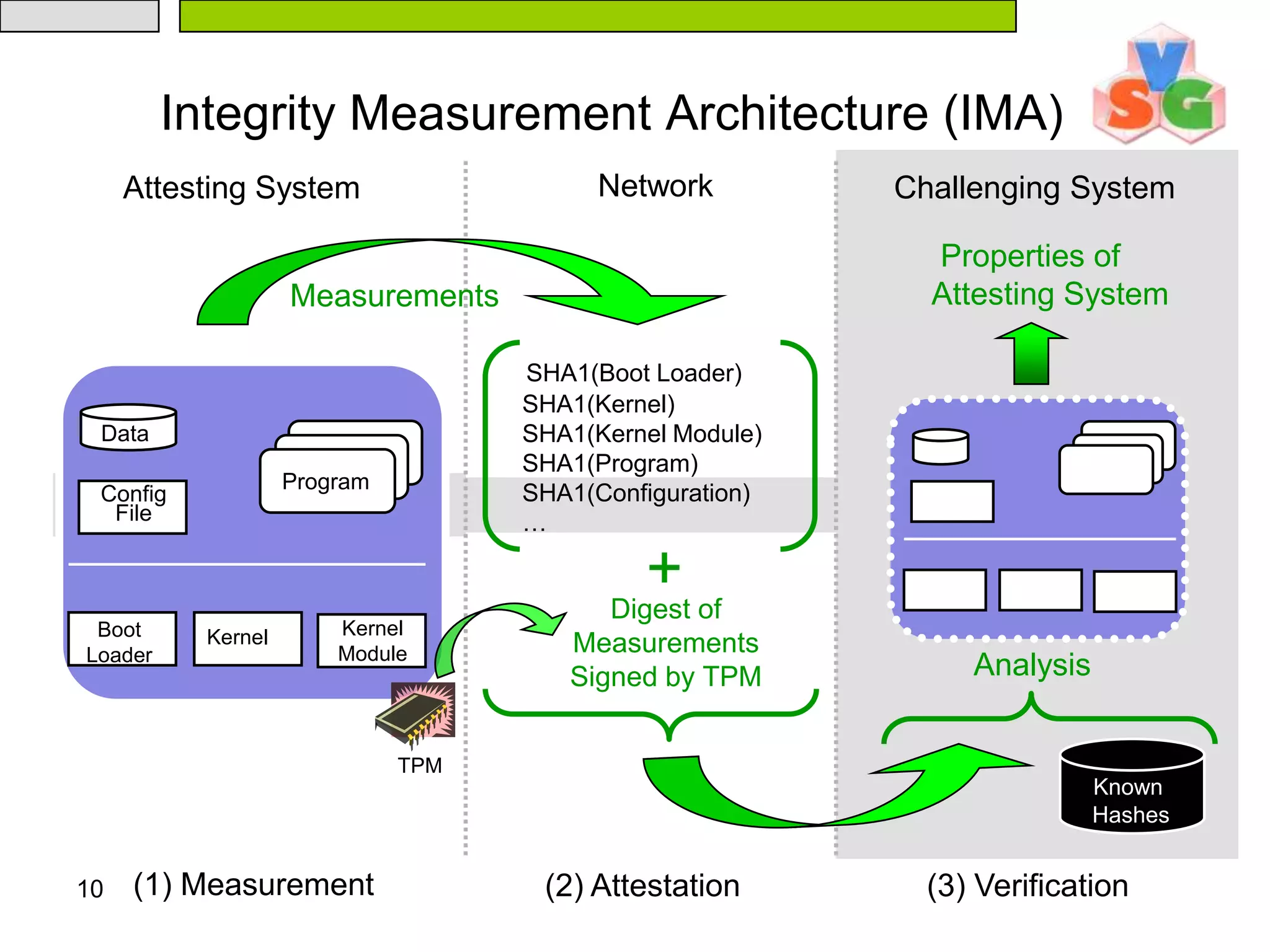
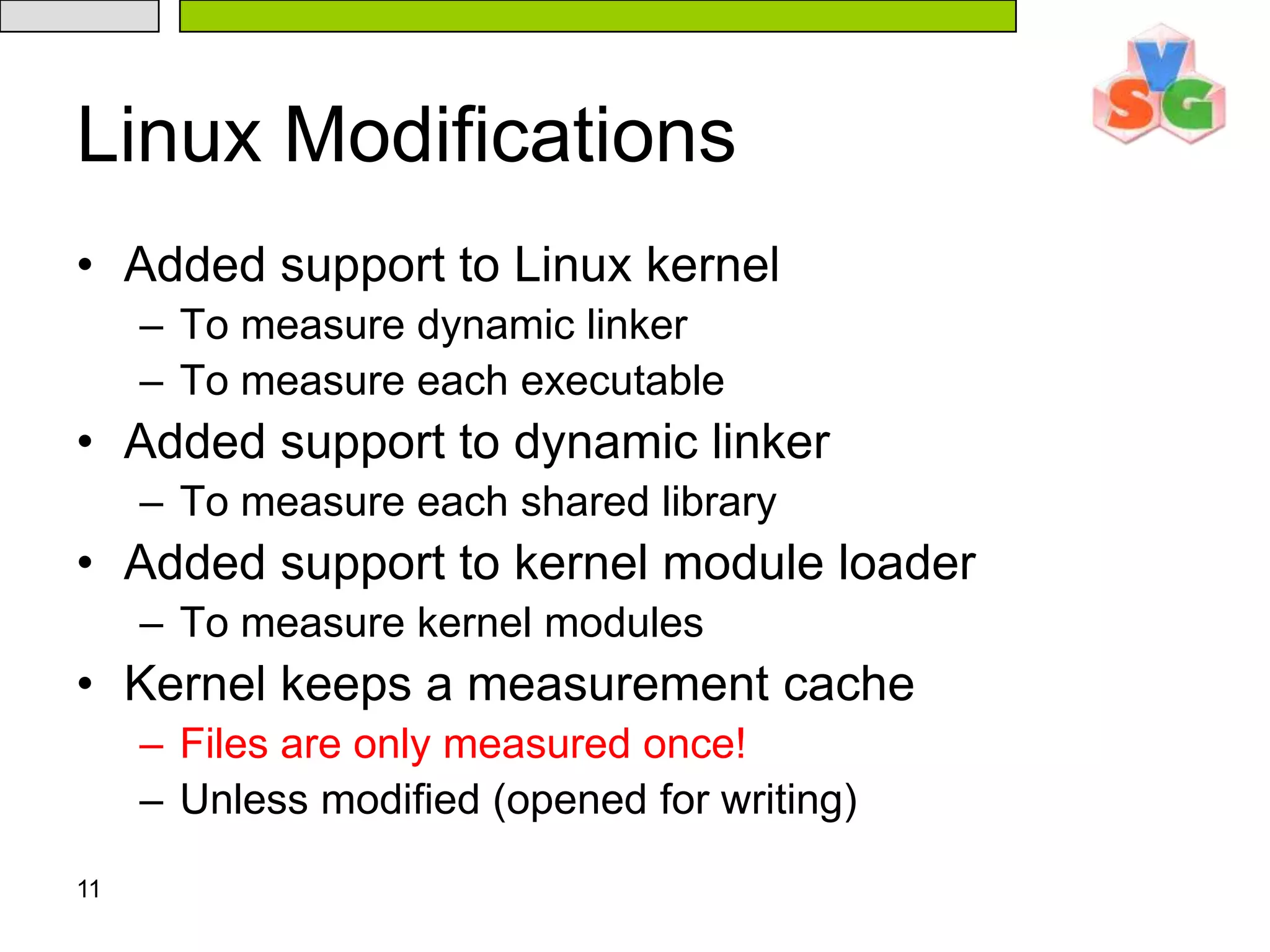
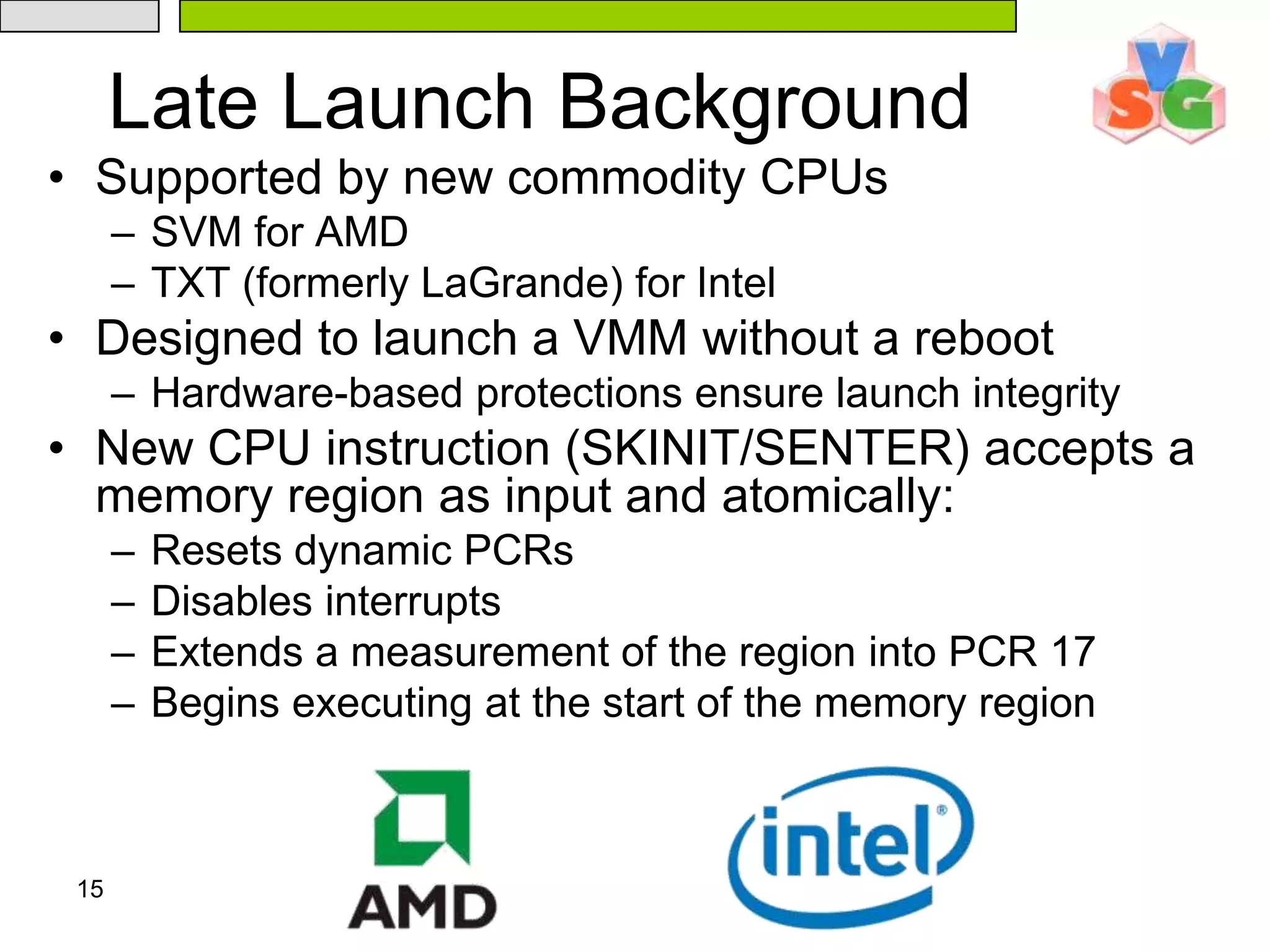
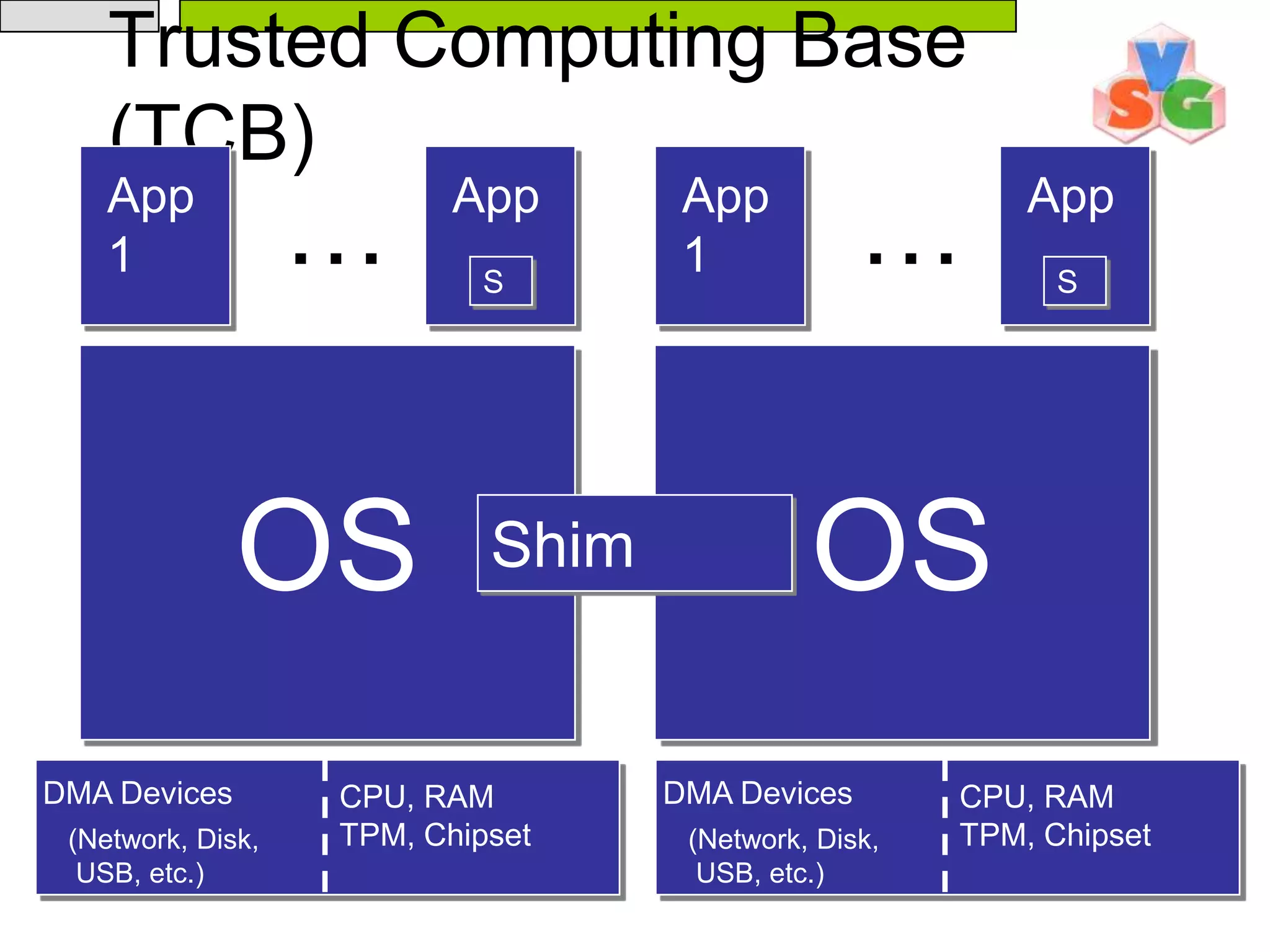
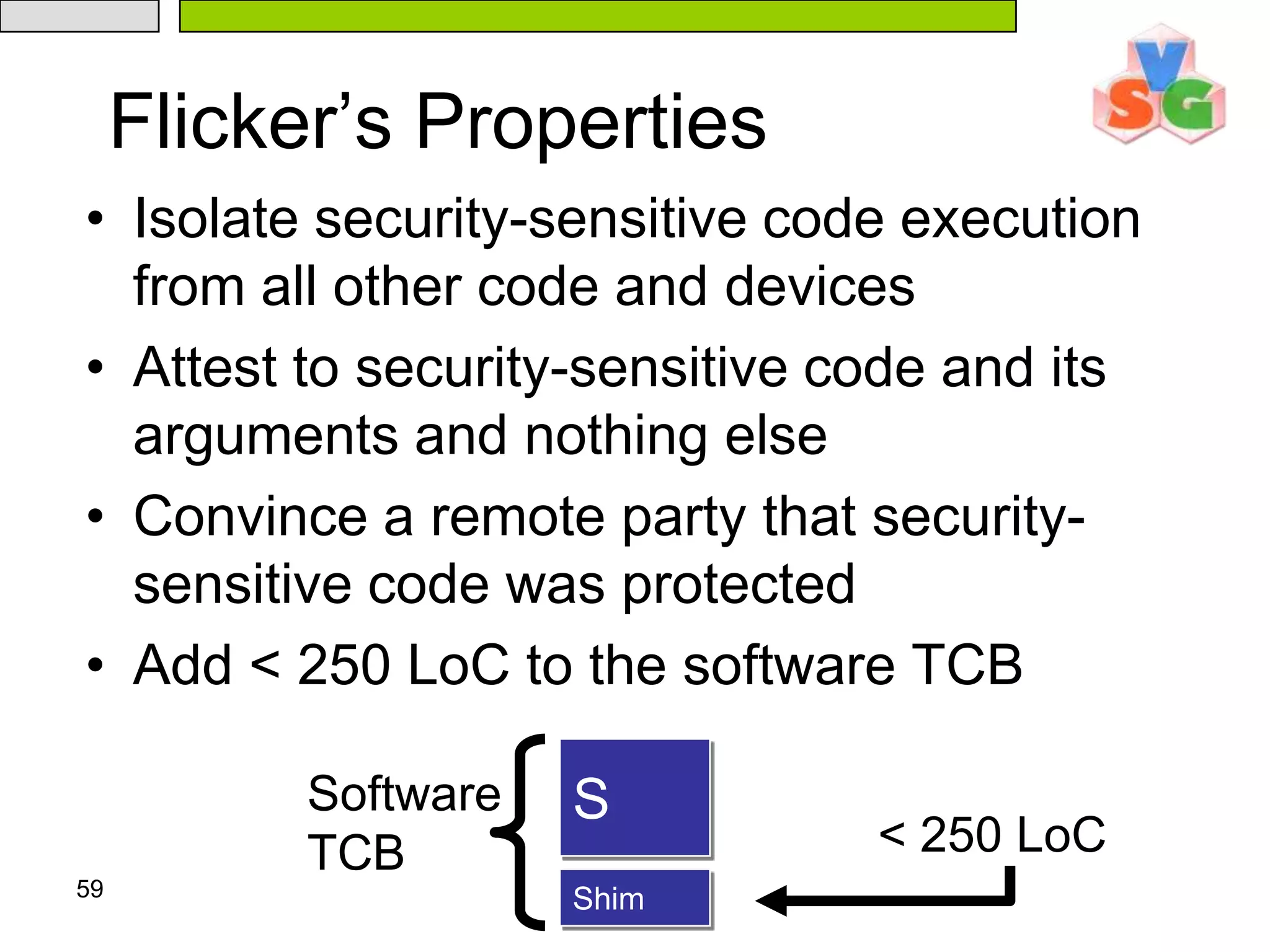
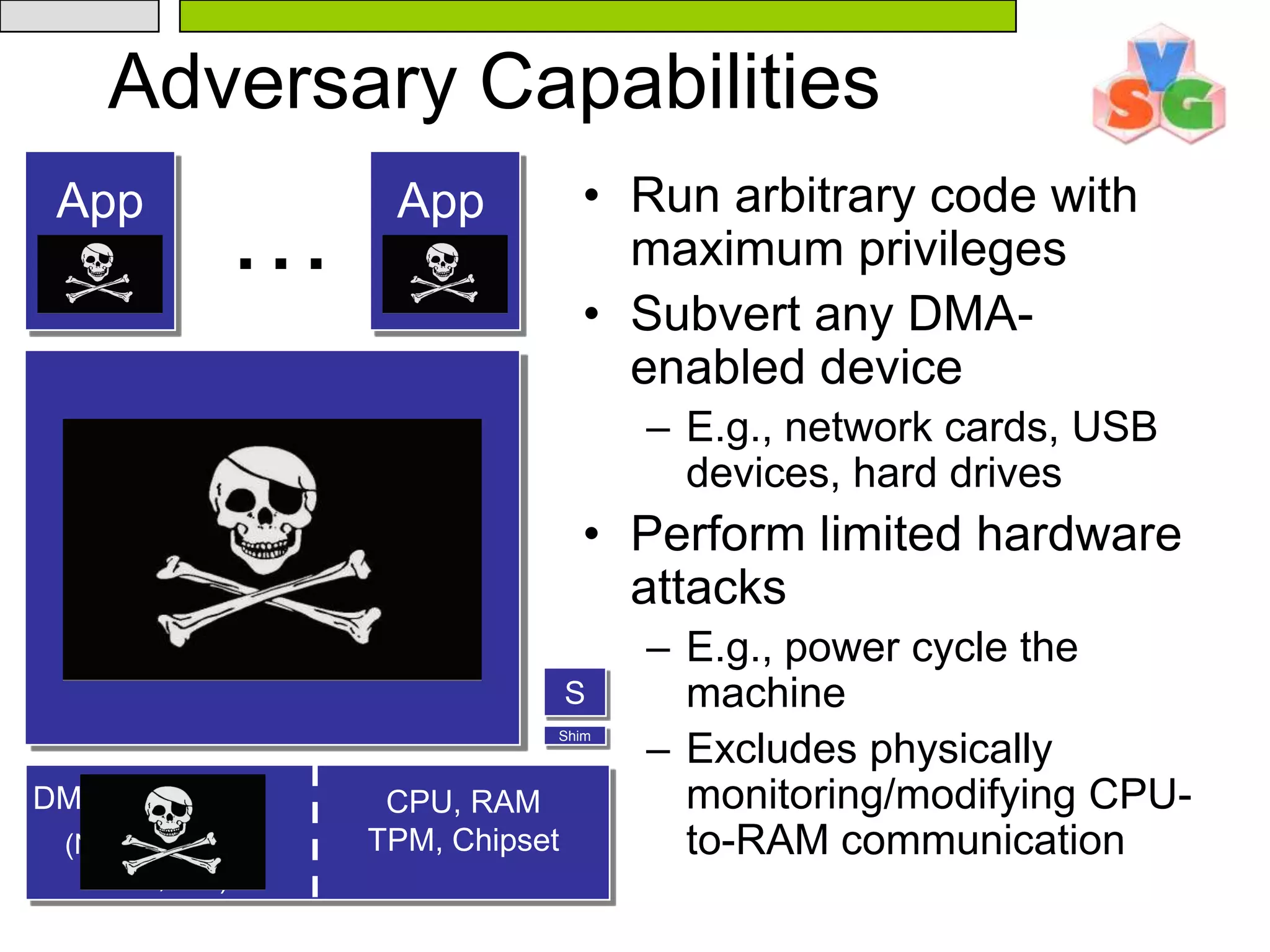
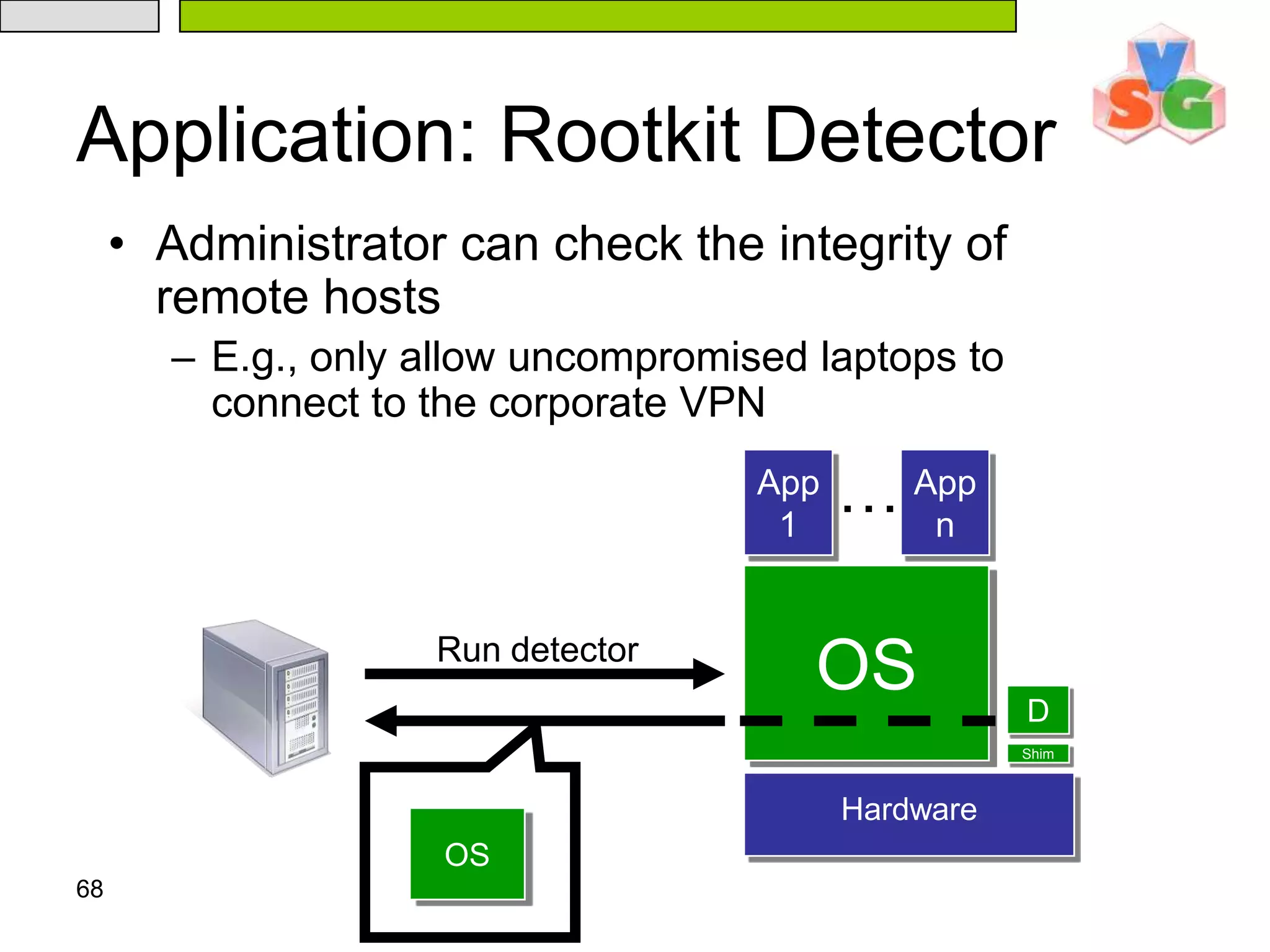
The document discusses Intel's Trusted Execution Technology (TXT) and its mechanisms for establishing a secure environment by creating a dynamic root of trust for measurement. It outlines how measurements are taken and verified to ensure the integrity of the operating system and applications, detailing the role of the Trusted Platform Module (TPM) and various technical specifications like the use of Secure Kernel Initialization (SKINIT). Additionally, it highlights both AMD and Intel's approaches to late launch configurations and their implications for security and system integrity.

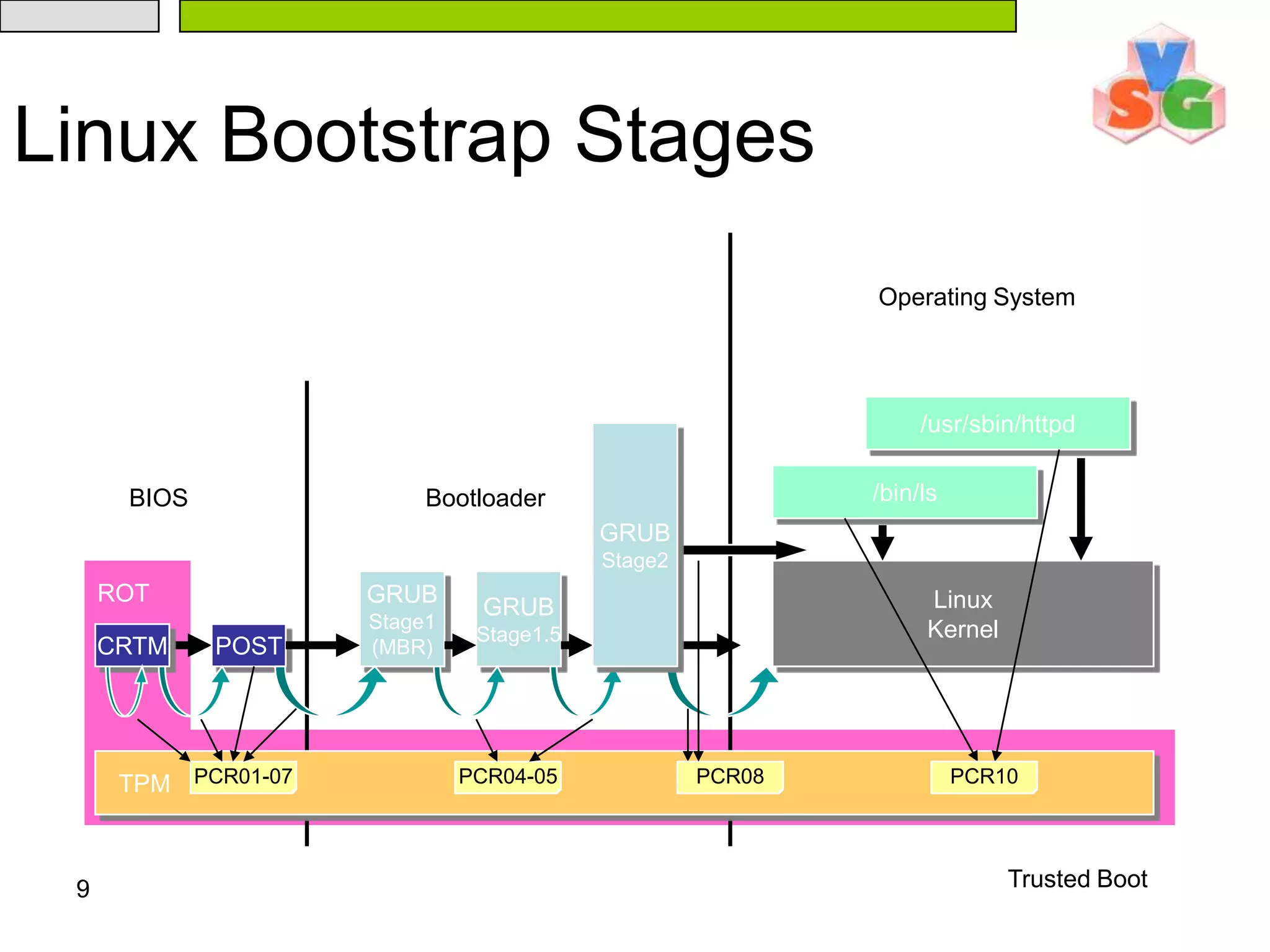
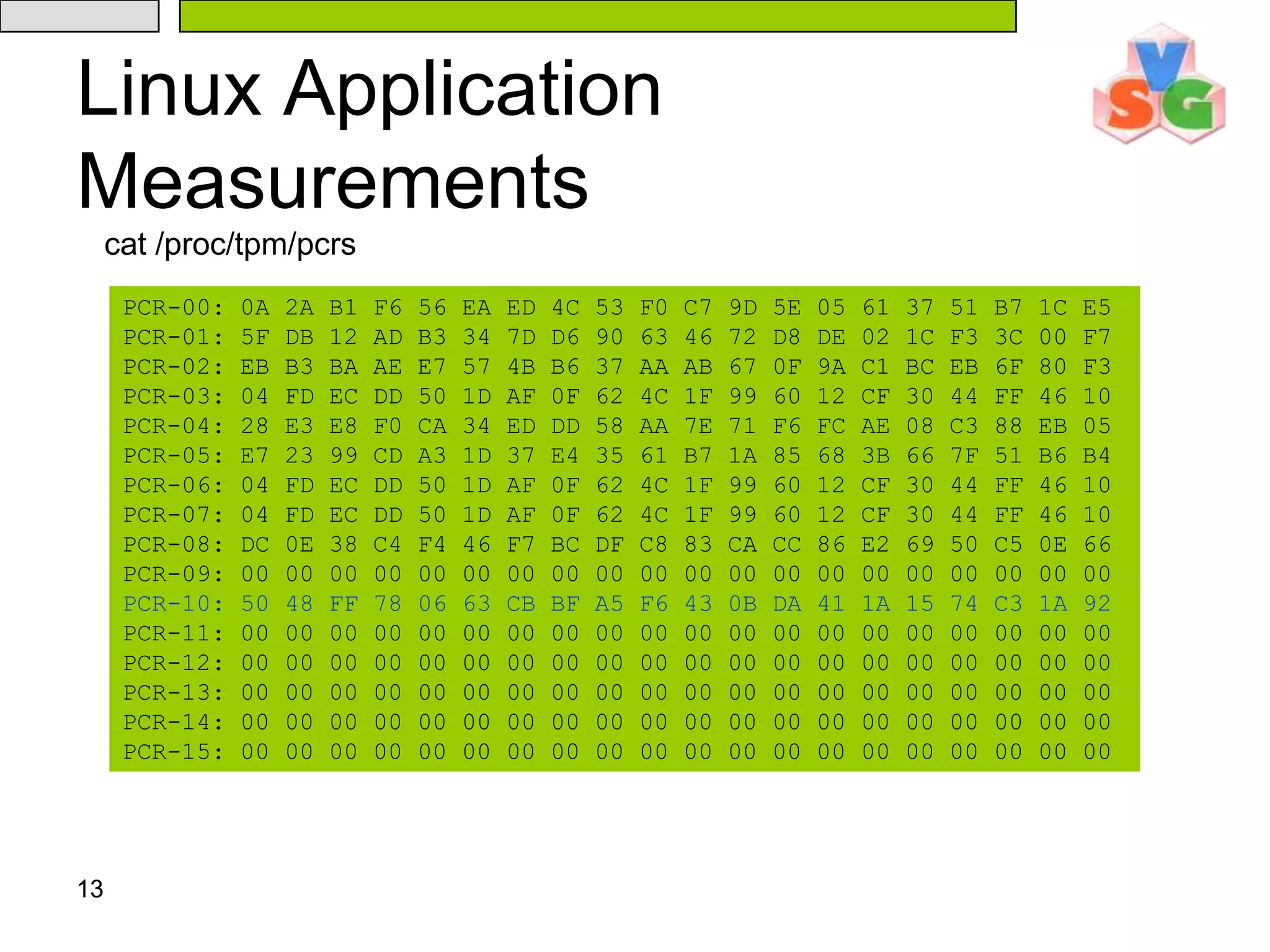
![12Linux Application Measurementscat /proc/tcg/measurements#000: 276249898F406BE176E3D86EDD5A3D20D03EEB11 [remeasure] linuxrc#001: 9F860256709F1CD35037563DCDF798054F878705 [remeasure] nash#002: 4CC52A8F7584A750303CB2A41DEA637917DB0310 [clean] insmod#003: 84ABD2960414CA4A448E0D2C9364B4E1725BDA4F [clean] init#004: 194D956F288B36FB46E46A124E59D466DE7C73B6 [clean] ld-2.3.2.so#005: 7DF33561E2A467A87CDD4BB8F68880517D3CAECB [clean] libc-2.3.2.so#006: 93A0BBC35FD4CA0300AA008F02441B6EAA425643 [clean] rc.sysinit#007: 66F445E31575CA1ABEA49F0AF0497E3C074AD9CE [clean] bash#008: F4F6CB0ACC2F1BEE13D60330011DF926D24E5688 [clean] libtermcap.so.2.0.8#009: 346443AAD8E7089B64B2B67F1A527F7E2CA2D1E5 [clean] libdl-2.3.2.so#010: 02385033F849A2A4BFB85FD52BCEA27B45497C6C [clean] libnss_files-2.3.2.so#011: 6CB3437EC500767328F2570C0F1D9AA9C5FEF2F6 [clean] initlog#012: FD1BCAEF339EAE065C4369798ACAADFF44302C23 [clean] hostname#013: F6E44B04811CC6F53C58EEBA4EACA3FE9FF91A2E [clean] consoletype#014: 12A5A9B6657EFEE7FD619A68DA653E02A7D8C661 [clean] grep#015: 3AF36F2916E574884850373A6E344E4F2C51DD60 [clean] sed#016: CE516DE1DF0CD230F4A1D34EFC89491CAF3D50E4 [clean] libpcre.so.0.0.1#017: 5EE8CD72AAD26191879E01221F5E051CE5AAE95F [clean] setsysfont#018: 8B15F3556E892176B03D775E590F8ADF9DA727C5 [clean] unicode_start#019: F948CF91C7AF0C2AB6AD650186A80960F5A0DAB1 [clean] kbd_mode#020: FF02DD8E56F0B2DCFB3D9BF392F2FCE045EFE0BC [clean] dumpkeys#021: C00804432DFBC924B867FC708CB77F2821B4D320 [clean] loadkeys#022: DE3AC70601B9BA797774E59BEC164C0DDF11982D [clean] setfont#023: 7334B75FDF47213FF94708D2862978D0FF36D682 [clean] gzip#024: AEC13AA4FF01F425ACACF0782F178CDFE3D17282 [clean] minilogd#025: 09410DDC5FE2D6E7D8A7C3CF5BB4D51ED6C4C817 [clean] sleep……………PCR10](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-12-2048.jpg)


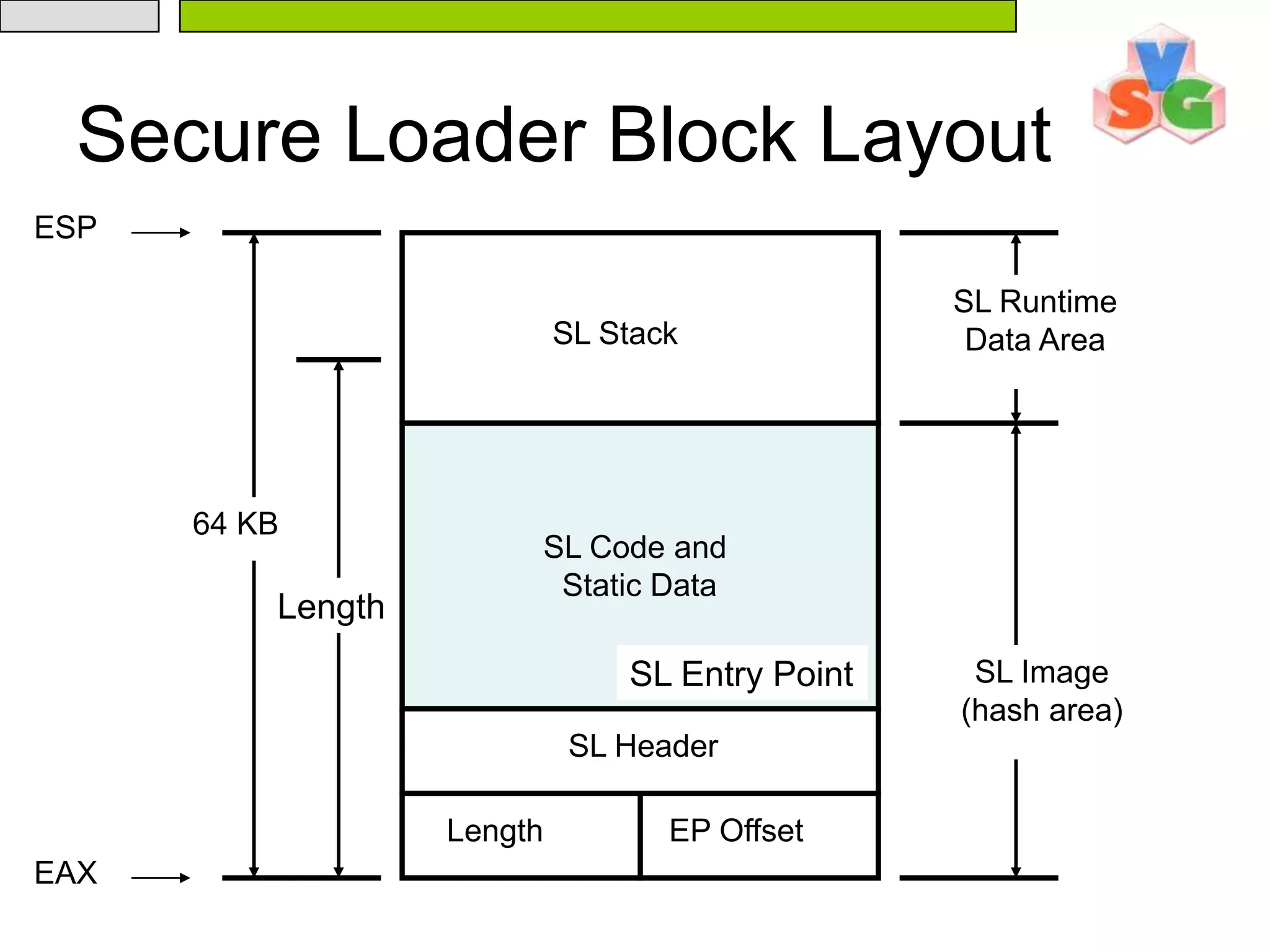
![24Intel Trusted eXecution TechnologySafer Mode Extensions (SMX) and Virtual Machine Extensions (VMX)SMX introduces Authenticated Code capabilitiesAC module loaded into CPU-internal RAMAC module contains a digital signatureProcessor calculates hash and verifies signatureExecution isolated from external memory and busSMX introduces a GETSEC “leaf” instructionGETSEC[CAPABILITIES] - get available capabilities](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-24-2048.jpg)

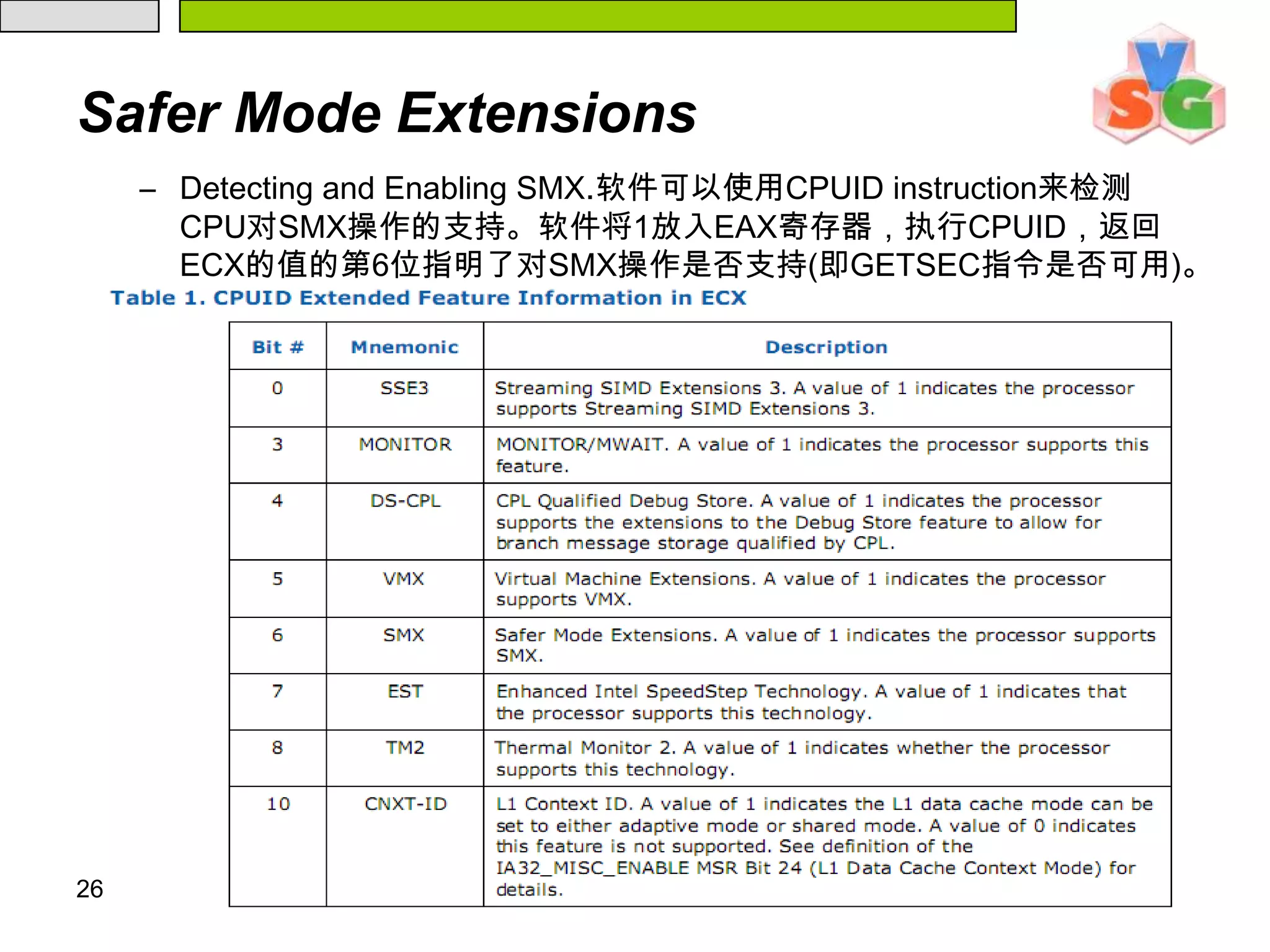
![271 SMX Functionality在处理器中通过GETSEC指令来提供对SMX的功能的支持。这条指令支持多个子功能。在GETSEC指令执行时由EAX中的值来决定执行哪个子功能(这些子功能共享同一个操作码,0F 37)。282 Enabling SMX Capabilities系统软件通过设置CR4.SMXE[Bit 15]=1去打开SMX功能。如果没有打开就去执行会返回一个非法操作码异常(#UD)。](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-27-2048.jpg)
![如果CPUID的SMX标志位是0(CPUID.01H.ECX[Bit 6] = 0),那么设置CR4.SMXE[Bit 15]位的操作将返回一个general protection异常。](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-28-2048.jpg)
![IA32_FEATURE_CONTROL MSR(在地址03AH)提供了配置VMX和SMX操作的控制位。293 SMX Instruction Summary系统软件首先通过执行GETSEC[CAPABILITIES]指令来查询可用的GETSEC子功能。](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-29-2048.jpg)
![303 SMX Instruction Summary1 GETSEC[PARAMETERS] 返回SMX的相关参数信息报告SMX操作的attributes, options and limitations。软件使用它来辨识操作限制或附加选项。The parameters index is input in EBX with the result returned in EAX, EBX, and ECX.](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-30-2048.jpg)









![Performing a measured launch.371.1 Intel® TXT detection and processor preparation Intel® Trusted Execution Technology Detection and Processor Preparation This action is only performed by the ILP. CPUID(EAX=1); IF (SMX not supported) OR (VMX not supported) { Fail measured environment startup; } // Enable SMX on ILP & check for Intel® TXT chipset CR4.SMXE = 1; GETSEC[CAPABILITIES]; IF (Intel® TXT chipset NOT present) { Fail measured environment startup; }](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-42-2048.jpg)

![401.3 Loading the MLE and processor rendezvous(2)Intel® Trusted Execution Technology Heap Initialization Information can be passed from system software to the SINIT AC module and from system software to the MLE using the Intel® TXT Heap. The SINIT AC module will also use this region to pass data to the MLE. The system software launching the measured environment is responsible for initializing the following in the Intel® TXT Heap memory (this initialization must be completed before executing GETSEC[SENTER]):(1)Initialize contents of the Intel® TXT Heap Memory(2)Initialize contents of the OsMleData and OsMleDataSize (with the size of the OsMleData field + 8H) fields. (3)Initialize contents of the OsSinitData and OsSinitDataSize (with the size of the OsSinitData field + 8H) fields. The OsMleData structure has fields for specifying regions of memory to protect from DMA (PMR Low/High Base/Size) using VT-d.](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-45-2048.jpg)
![411.3 Loading the MLE and processor rendezvous(3)Rendezvousing Processors and Saving State 如果是在OS启动后launching the measured environment 那么all processors should be brought to a rendezvous point before executing GETSEC[SENTER]. At the rendezvous point each processor will set up for GETSEC[SENTER] and save any state needed to resume after the measured launch. If processors are not rendezvoused before executing SENTER then the processors will loose their current operating state including possibly the fact that an in-service interrupt has not been acknowledged.Clear Machine Check Status Registers; Ensure CR0.CD=0, CR0.NW=0, and CR0.NE=1; // Save current system software state in Intel® TXT Heap Allocate memory for OsMleData; Fill in OsMleData with system software state (including MTRR and IA32_MISC_ENABLE MSR states);](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-46-2048.jpg)
![421.4 Performing a Measured Launch(1)MTRR Setup Prior to GETSEC[SENTER] Execution System software must set up the variable range MTRRs (memory type range register)to map all of memory (except the region containing the SINIT AC module) to one of the supported memory types as returned by GETSEC[PARAMETERS]. After MTRR setup is complete, the RLPs mask interrupts (by executing CLI), signal the ILP that they have interrupts masked, and execute halt. Before executing GETSEC[SENTER], the ILP waits for all RLPs to indicate that they have disabled their interrupts. If the ILP executed a GETSEC[SENTER] while an RLP was servicing an interrupt, the interrupt servicing would not complete, possibly leaving the interrupting device unable to generate further interrupts.](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-47-2048.jpg)
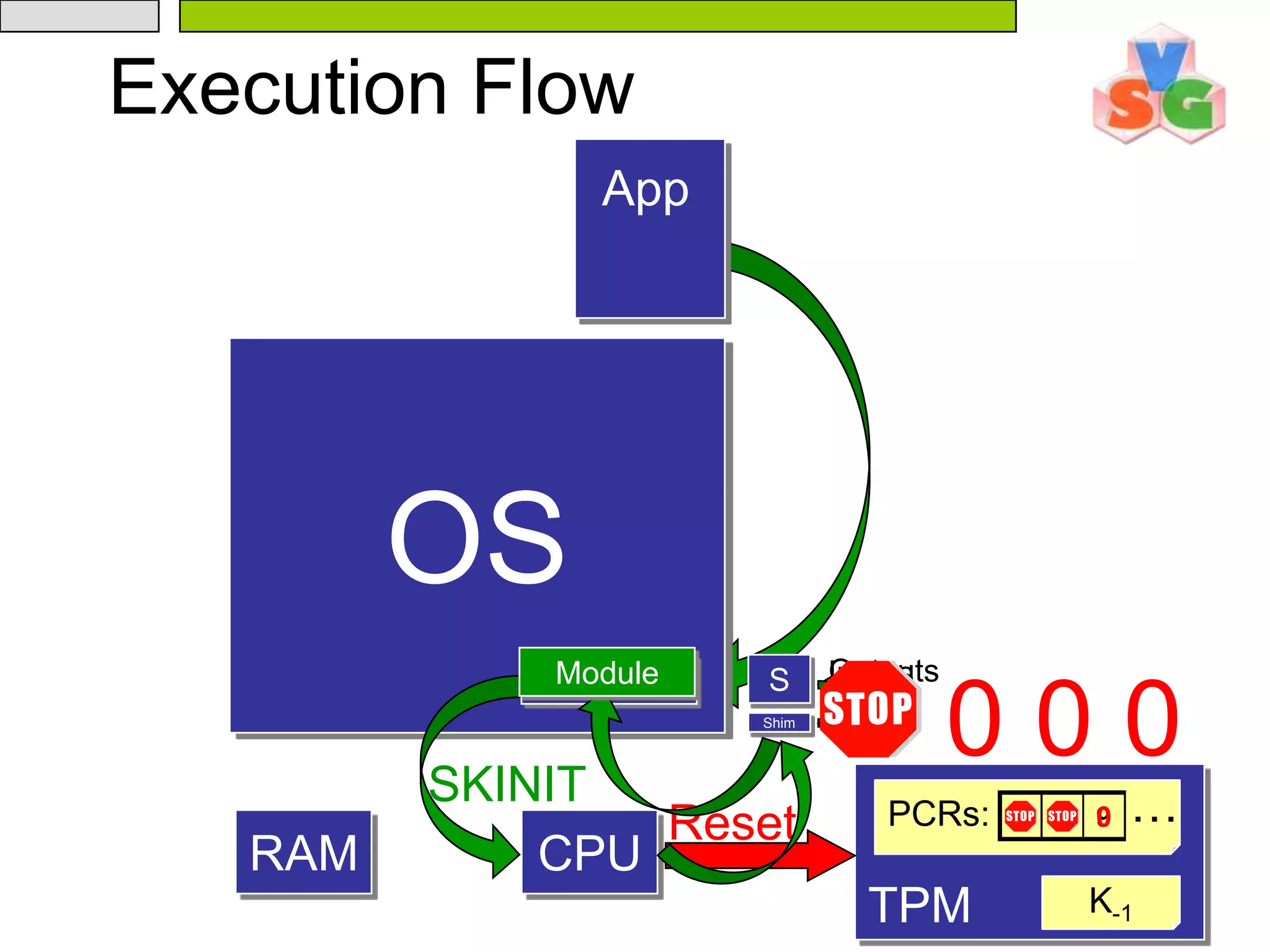
![431.4 Performing a Measured Launch(2)TPM Preparation System software must ensure that the TPM is ready to accept commands and that the TPM.ACCESS_0.activeLocality bit is clear before executing the GETSEC[SENTER] instruction. Intel® Trusted Execution Technology Launch The ILP is now ready to launch the measuring process. System software executes the GETSEC[SENTER] instruction.](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-48-2048.jpg)
![44Measured Launched EnvironmentAny Measured Launched Environment (MLE) will generally consist of three main sections of code: the initialization, the dispatch routine, and the shutdown. The initialization code is run each time the Intel® TXT environment is launched. This code includes code to setup the MLE on the ILP and join code to initialize the RLPs. After initialization, the MLE behaves like the unmeasured version would have; in the case of a VMM, this is trapping various guest operations and virtualizing certain processor states.Finally the MLE prepares for shutdown by again synchronizing the processors, clearing any state and executing the GETSEC[SEXIT] instruction.](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-49-2048.jpg)

![462.MLE Initialization//3. Wake RLPs Initialize memory protection and other data structures; Build JOIN structure; LT.MLE.JOIN = physical address of JOIN structure; IF RLP exist GETSEC[WAKEUP]; Wait for all processors to reach this point; 在processors间做一致性检测;// 4.Enable VMX CR4.VMXE = 1; // 5.Start VMX operation Allocate and setup the root controlling VMCS, execute VMXON(root controlling VMCS);](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-51-2048.jpg)

![483.MLE OperationThe dispatch routine is responsible for handling all VMExitsfrom the guest. The guest VMExits are caused by various situations, operations or events occurring in the guest. The dispatch routine must handle each VMExit appropriately to maintain the measured environment. In addition, the dispatch routine may need to save and restore some of processor state not automatically saved or restored during VM transitions. The MLE must also ensure that it has an accurate view of the address space and that it restricts access to certain of the memory regions that the GETSEC[SENTER] process will have enabled. The following subsections describe various key components of the MLE dispatch routine.493.1 Address Space CorrectnessIt is likely that most MLEs will rely on the e820 memory map to determine which regions of the address space are physical RAM and which of those are usable (e.g. not reserved by BIOS). However, as this table is created by BIOS it is not protected from tampering prior to a measured launch. An MLE, therefore, cannot rely on it to contain an accurate view of physical memory.](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-53-2048.jpg)





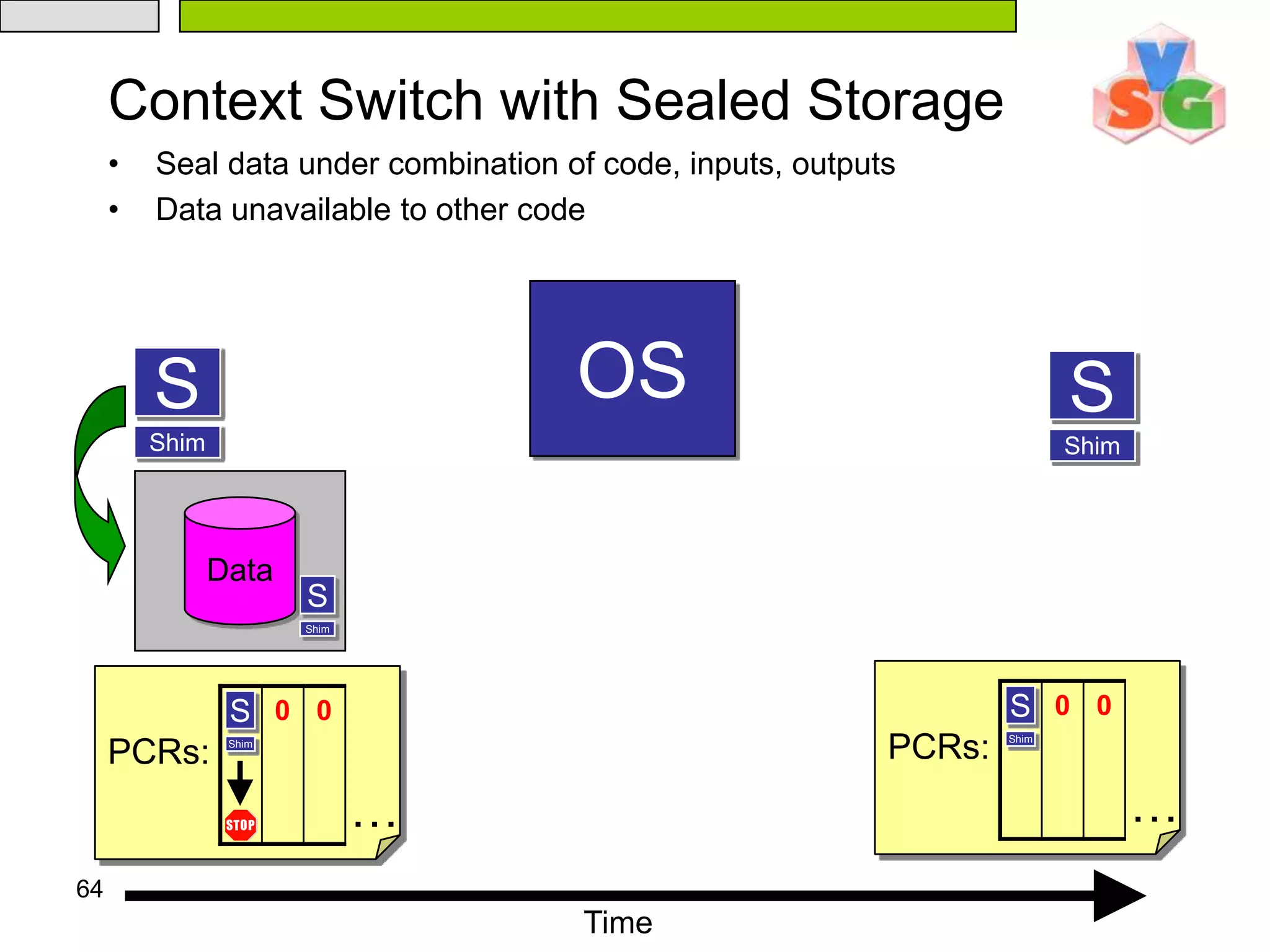
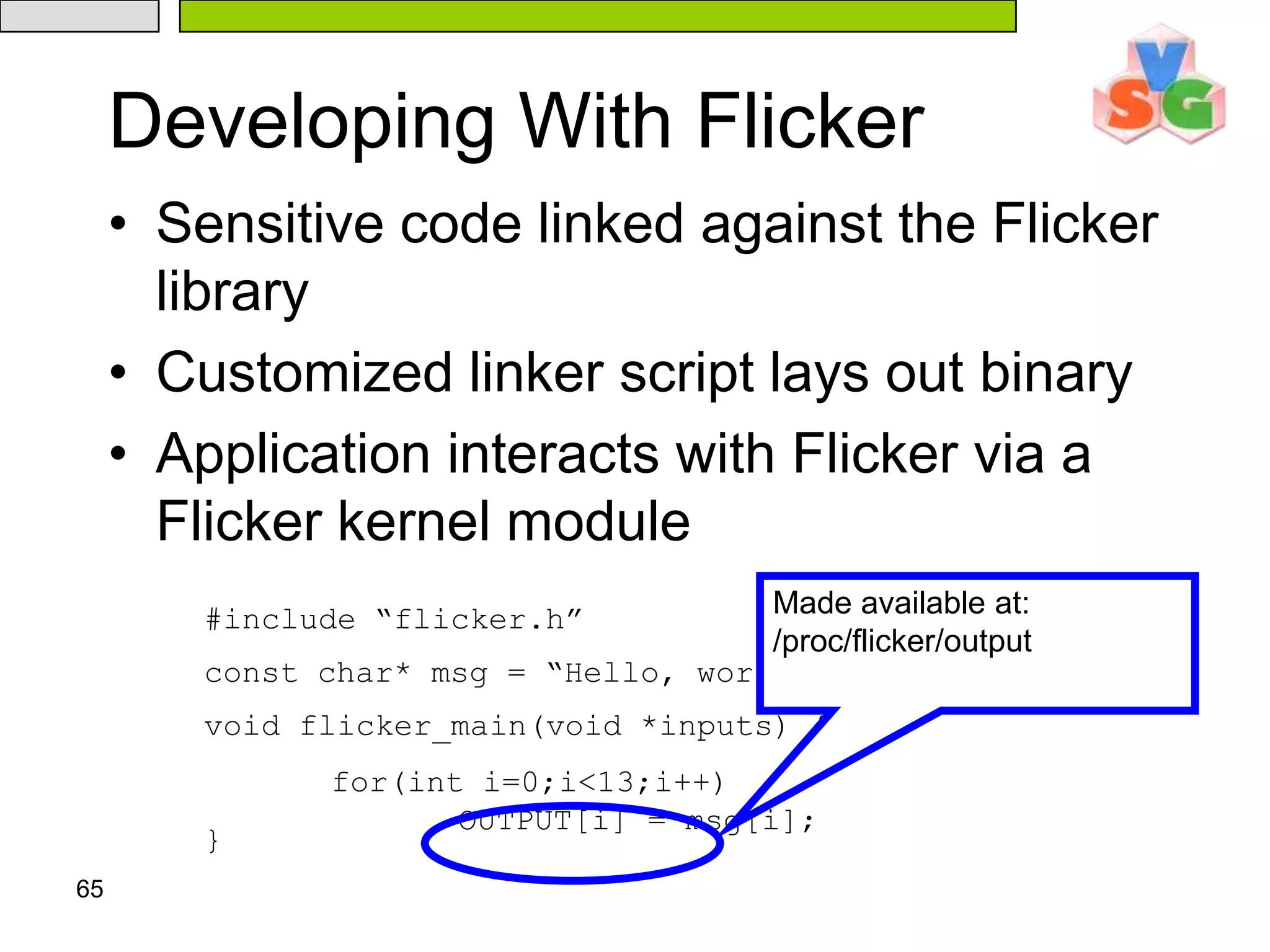
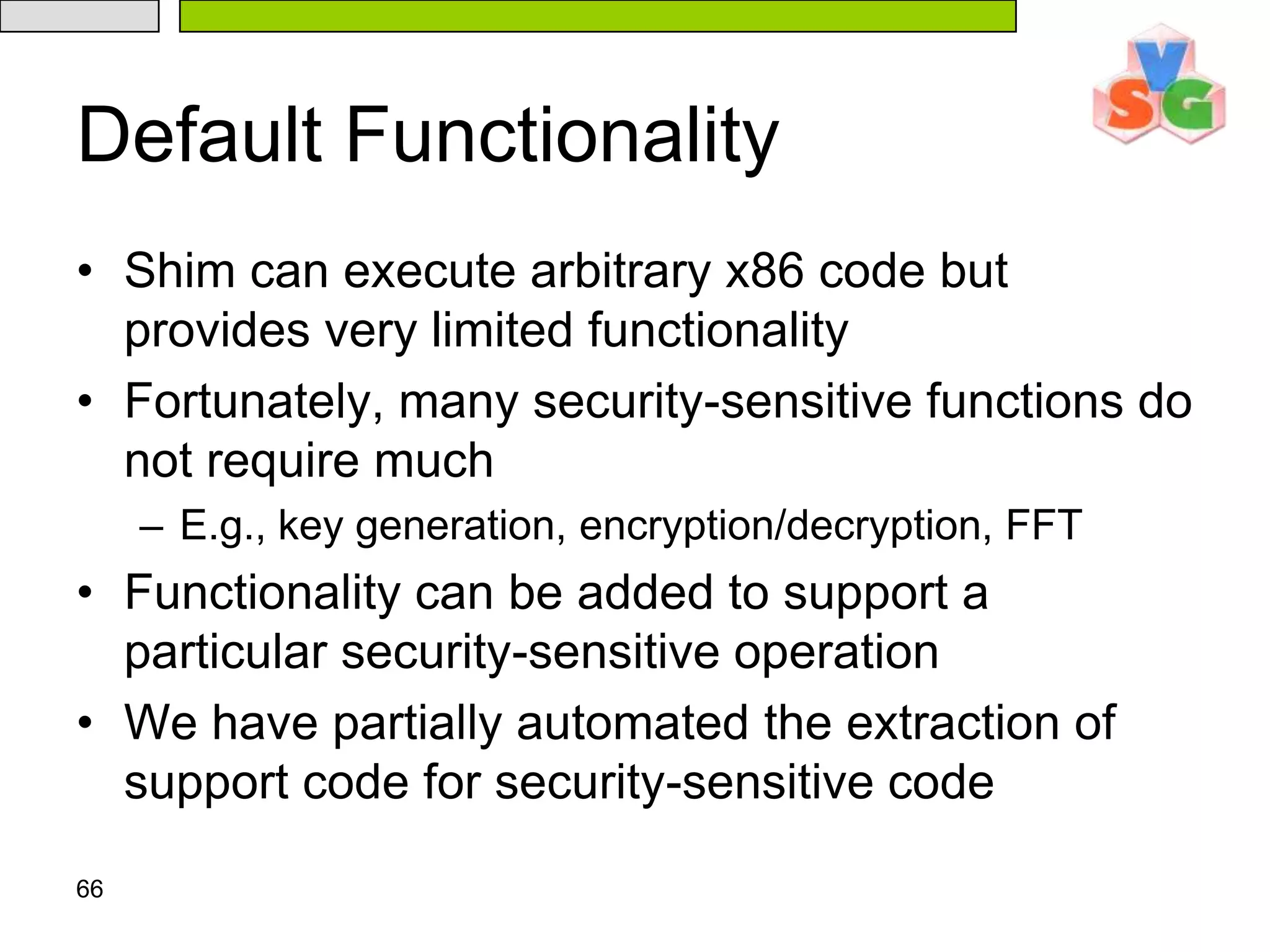
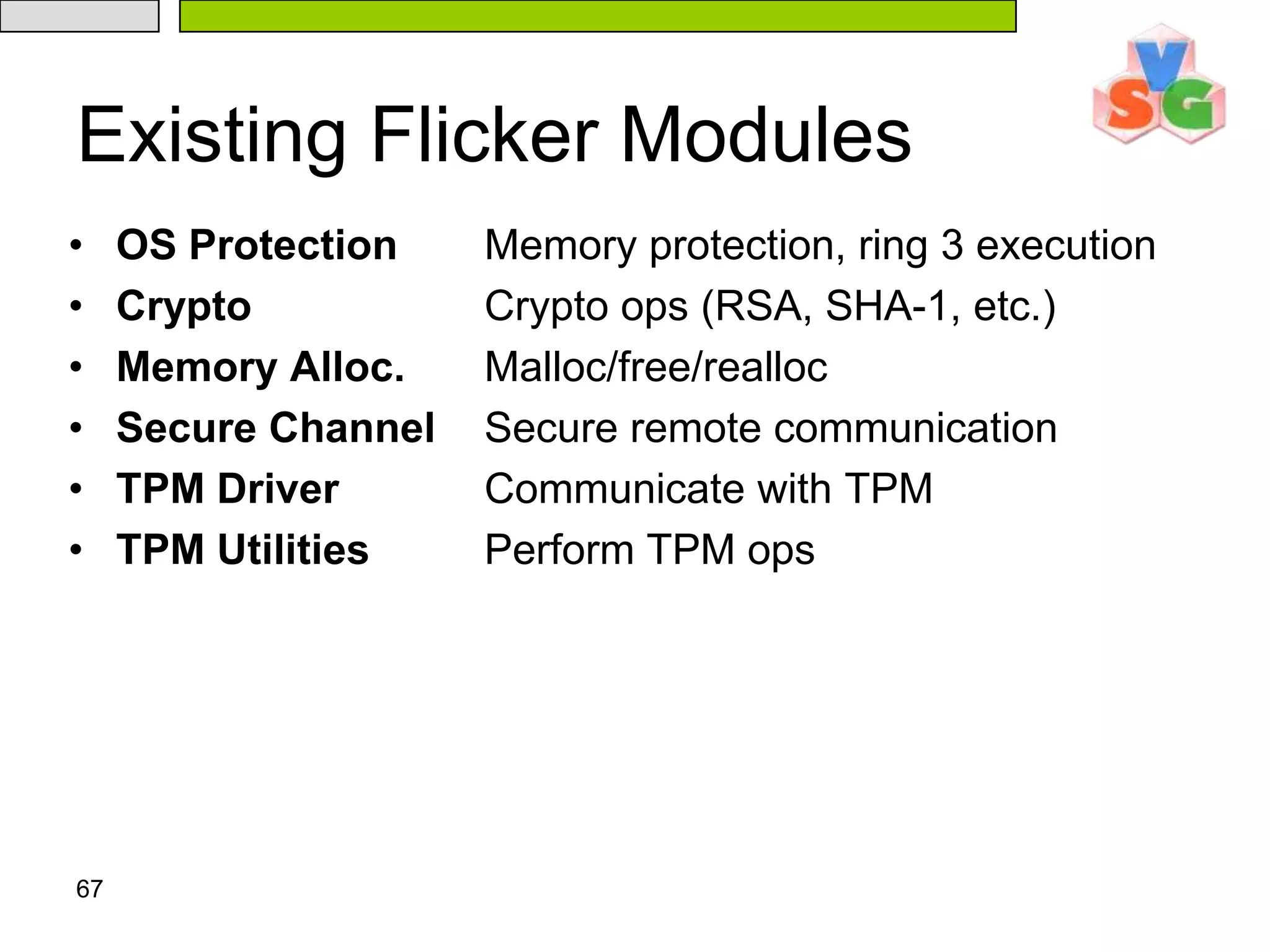
![65Developing With Flicker Sensitive code linked against the Flicker libraryCustomized linker script lays out binaryApplication interacts with Flicker via a Flicker kernel moduleMade available at:/proc/flicker/output#include “flicker.h”const char* msg = “Hello, world”; void flicker_main(void *inputs) { } for(int i=0;i<13;i++) OUTPUT[i] = msg[i];](https://image.slidesharecdn.com/txt-100215152710-phpapp02/75/Txt-Introduction-69-2048.jpg)