Embed presentation
Downloaded 16 times



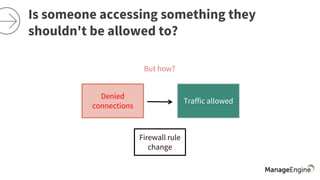

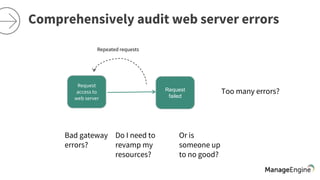

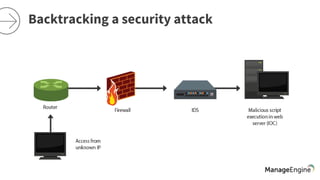


The document discusses the importance of security and auditing in network management, emphasizing the need for a comprehensive SIEM solution. It raises concerns about unauthorized access, auditing network devices, and the necessity of analyzing web server errors. Additionally, it suggests that preventive security measures alone may not suffice in protecting business-critical applications from potential attacks.










