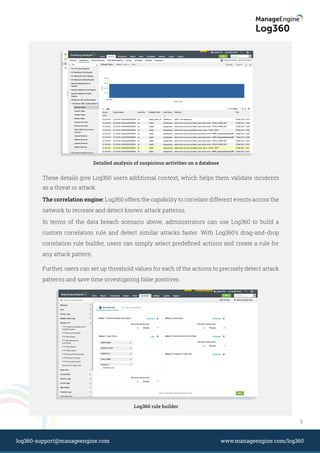
This document discusses the rising threat of security attacks and the importance of indicators of compromise (IOCs) and indicators of attack (IOAs) in detecting and mitigating these threats. It emphasizes the need for organizations to configure their SIEM solutions to monitor both IOCs and IOAs in order to effectively manage security risks. Additionally, the document provides guidance on implementing custom correlation rules and leveraging tools like Log360 for real-time event response and analysis.