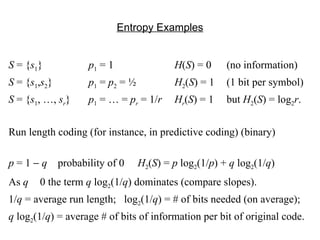
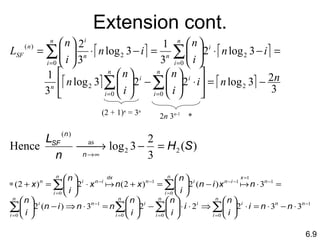The document discusses entropy and Shannon's first theorem. It defines entropy as the average amount of information received per symbol from a source where symbols have different probabilities. Entropy measures the uncertainty in the probability distribution of the source. The entropy of a source is equal to the minimum expected code length needed to encode symbols from that source.





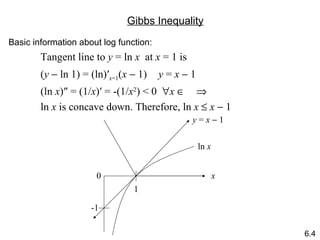




![Recall: The n th extension of a source S = { s 1 , …, s q } with probabilities p 1 , …, p q is the set of symbols T = S n = { s i 1 ∙∙∙ s i n | s i j S 1 j n } where t i = s i 1 ∙∙∙ s i n has probability p i 1 ∙∙∙ p i n = Q i assuming independent probabilities. The entropy is: [Letting i = ( i 1 , …, i n ) q , an n -digit number base q ] The Entropy of Code Extensions concatenation multiplication 6.8](https://image.slidesharecdn.com/datacompression1-100208231029-phpapp02/85/Datacompression1-12-320.jpg)