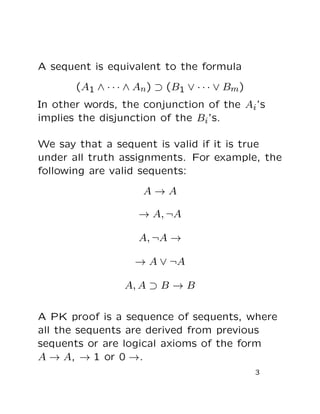
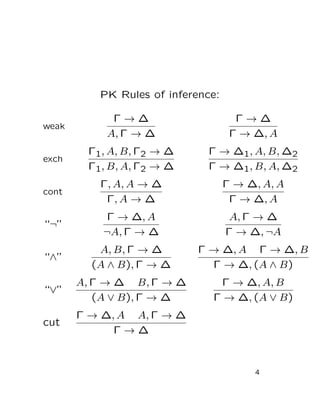
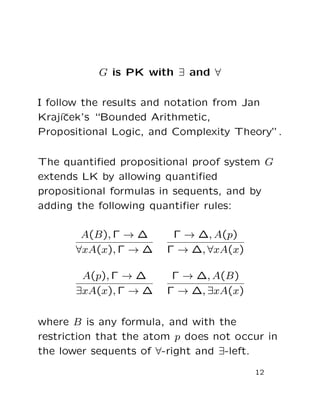
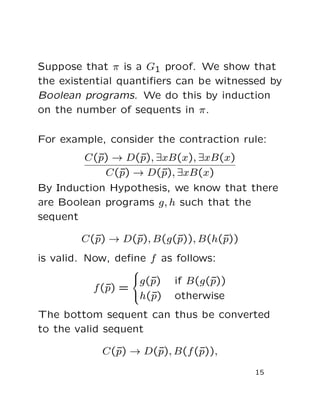
This document summarizes a paper on Boolean programs and quantified propositional proof systems. It introduces quantified propositional proof systems that extend propositional proof systems with propositional quantifiers. The main ideas are that quantified propositional proofs can be witnessed by Boolean programs, and that evaluating these programs is PSPACE-complete if the proofs are not tree-like, showing a connection between quantified propositional proof complexity and computational complexity classes.