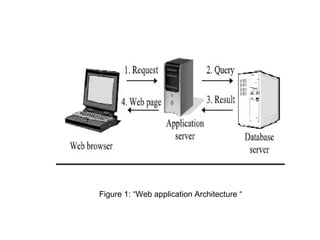
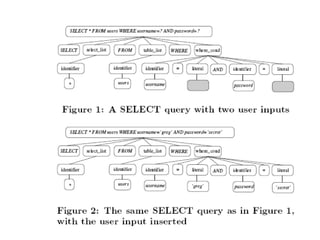
This presentation discusses database security and SQL injection. It introduces SQL injection and deploying an IDS to monitor for SQL injection signatures. It then summarizes the types of intrusion detection systems, including network-based, host-based, and distributed systems. The presentation also outlines the detection mechanisms for signature-based, anomaly-based, and hybrid intrusion detection systems. It concludes with a thank you and list of references.