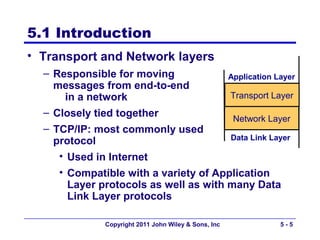
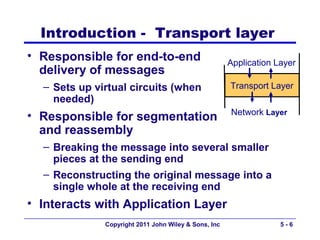
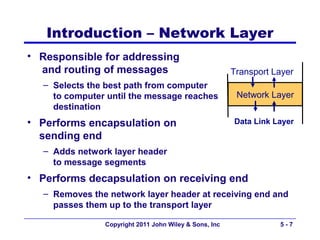
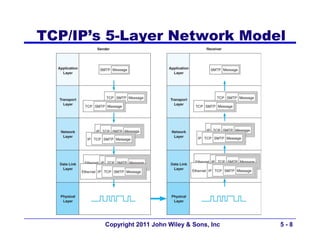
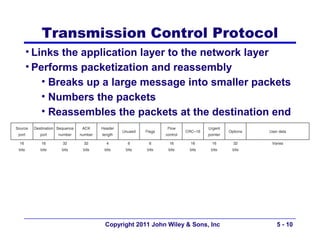
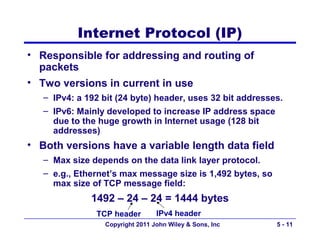
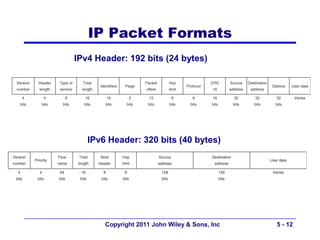
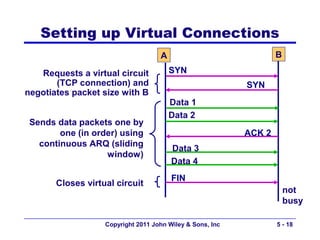
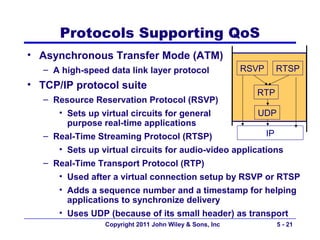
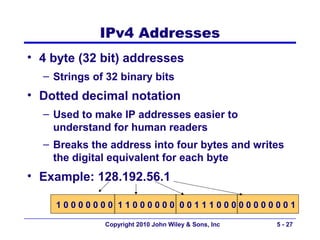
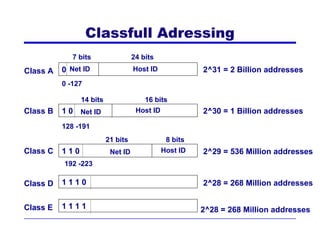
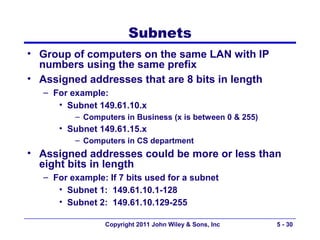
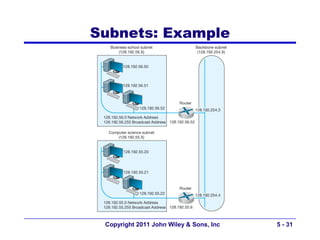
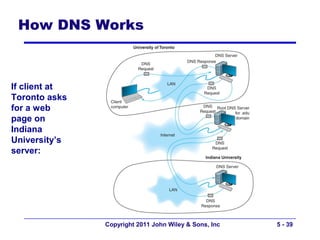
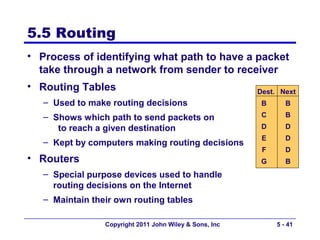
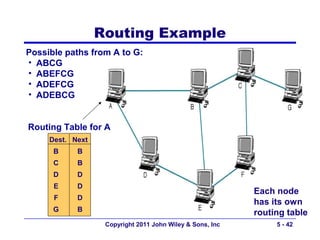
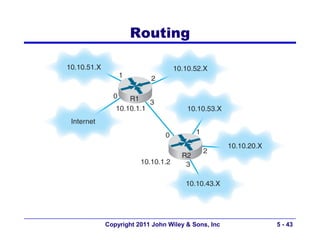
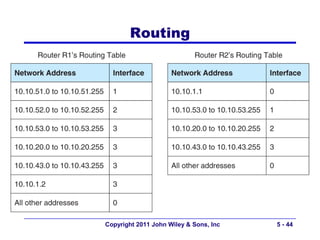
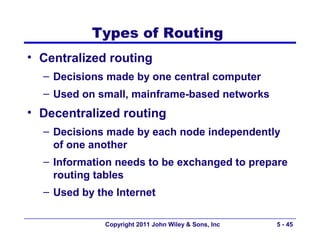
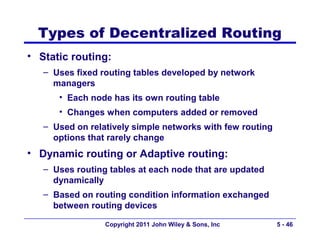
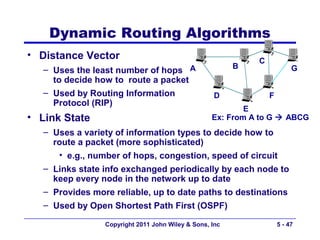
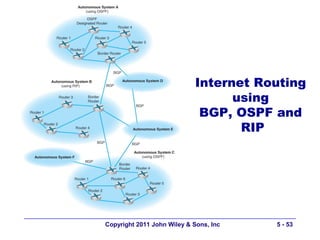
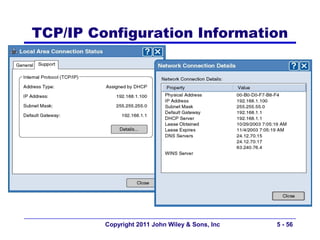
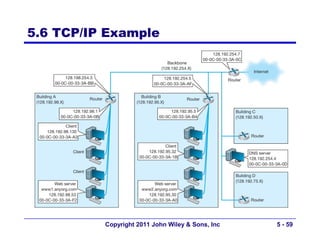
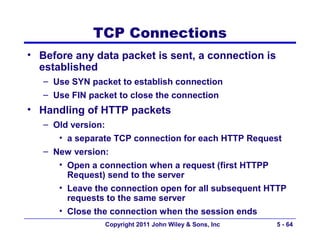
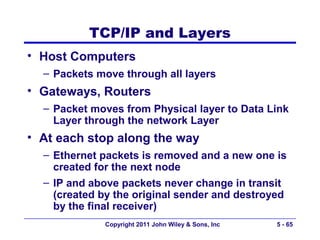
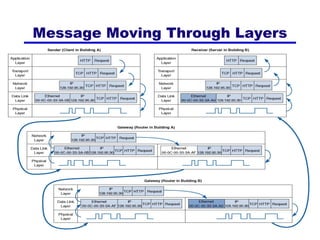
The document discusses TCP/IP networking protocols. It describes how TCP/IP is used to transport data across network and transport layers through packetization, addressing, and routing. TCP/IP uses IP addresses and port numbers to link applications to the network, and employs protocols like TCP, UDP, and IP to ensure reliable and unreliable delivery of packets. Dynamic addressing protocols like DHCP allow devices to obtain IP addresses automatically.