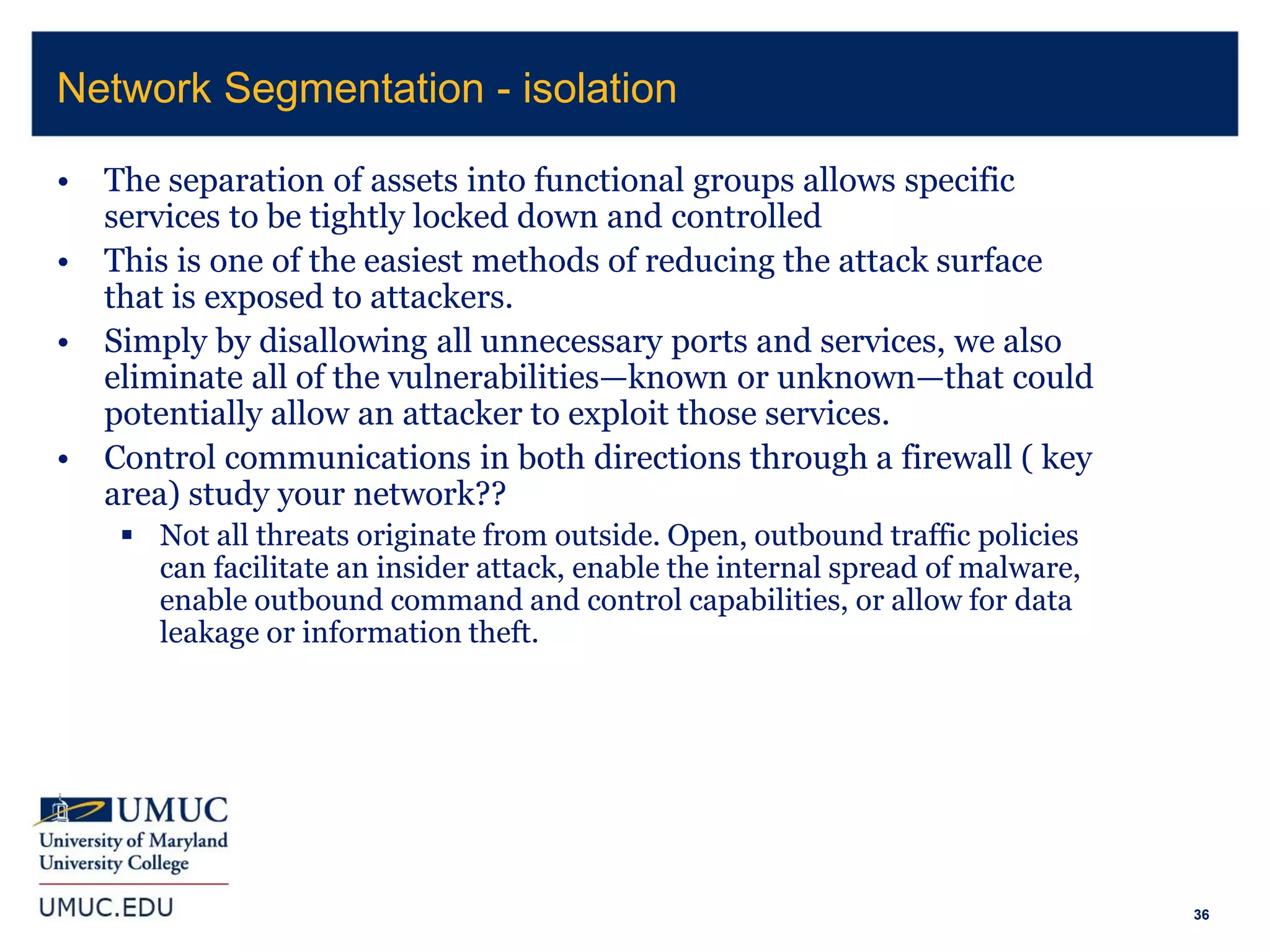
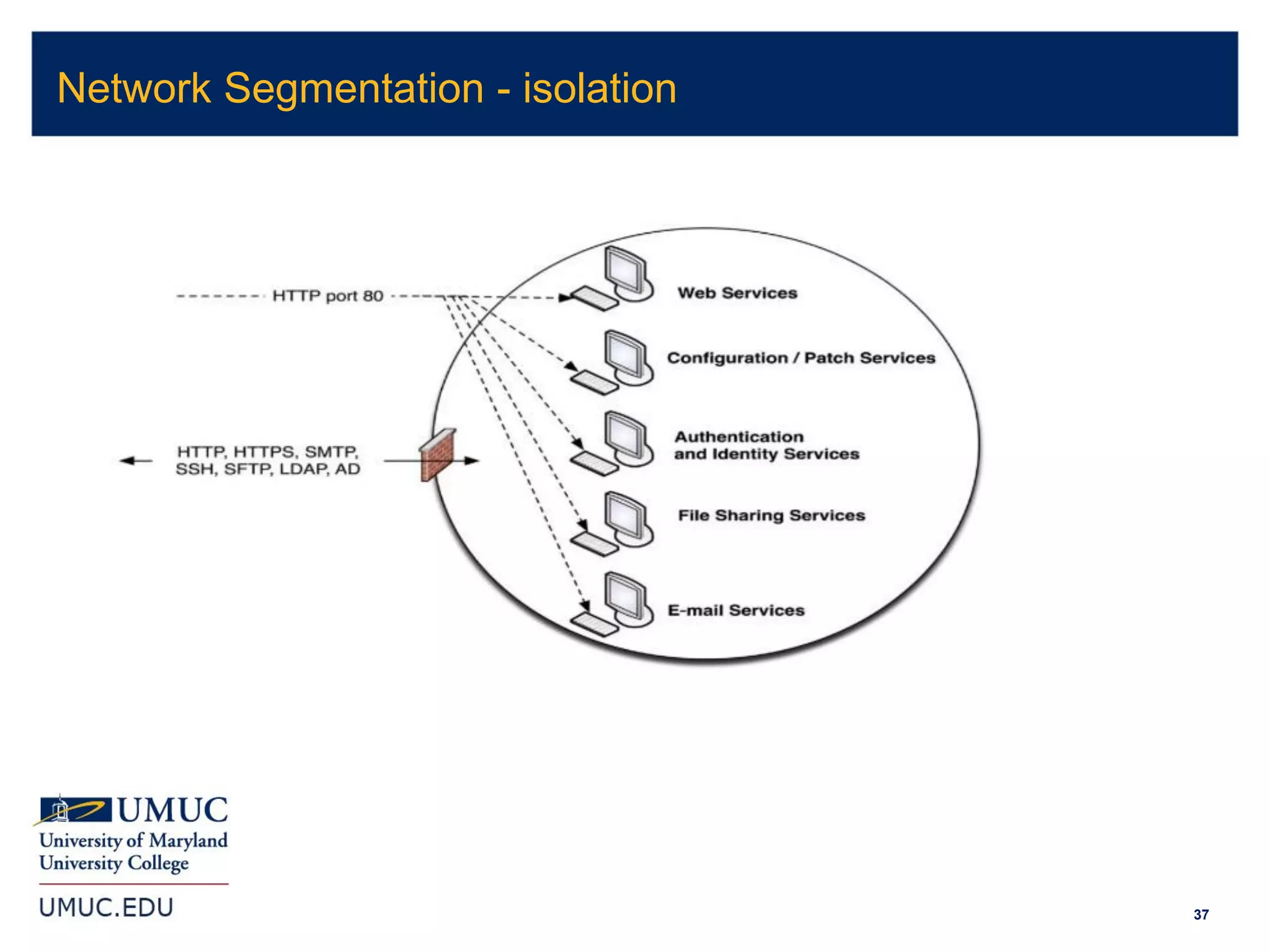
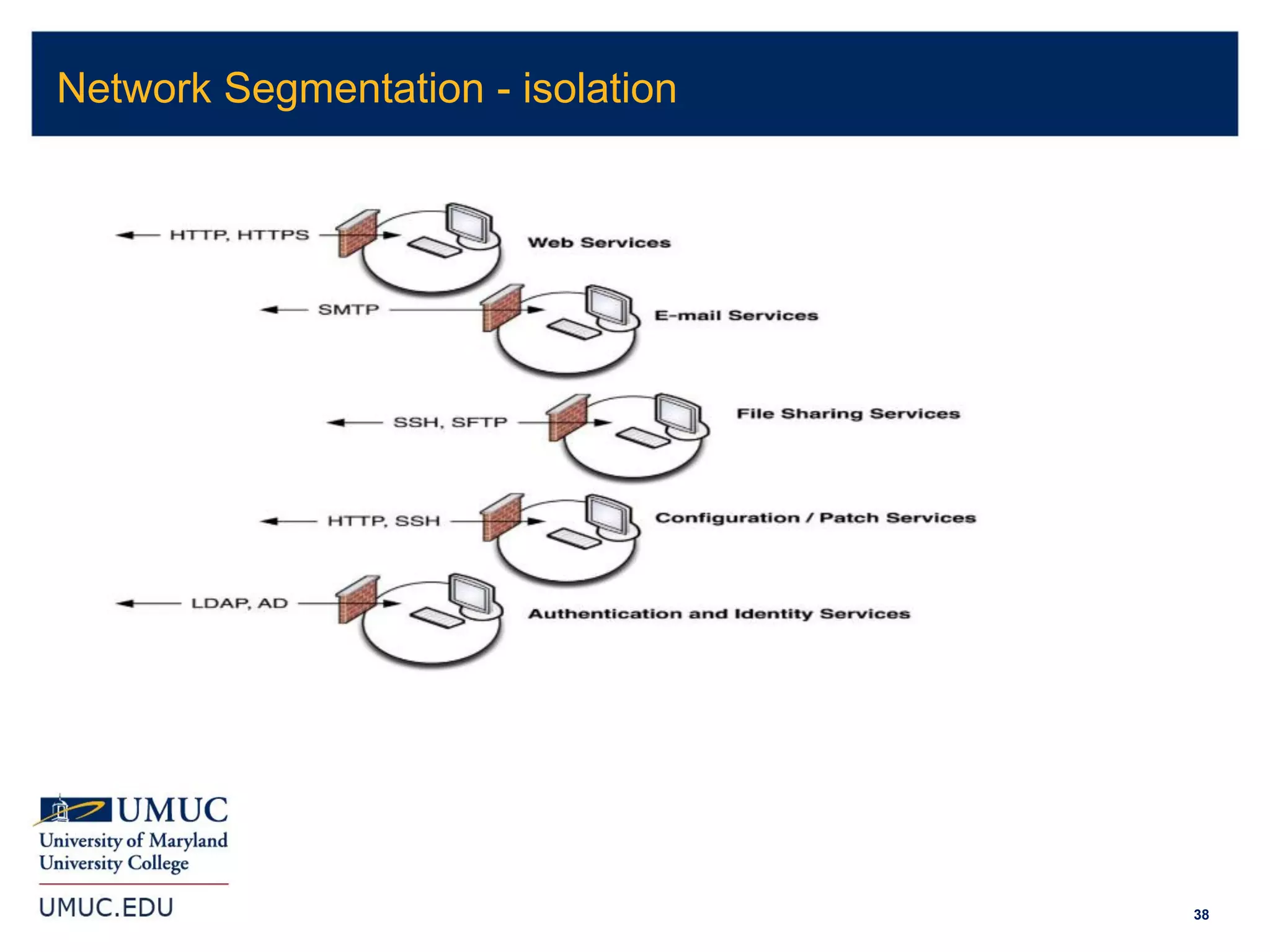
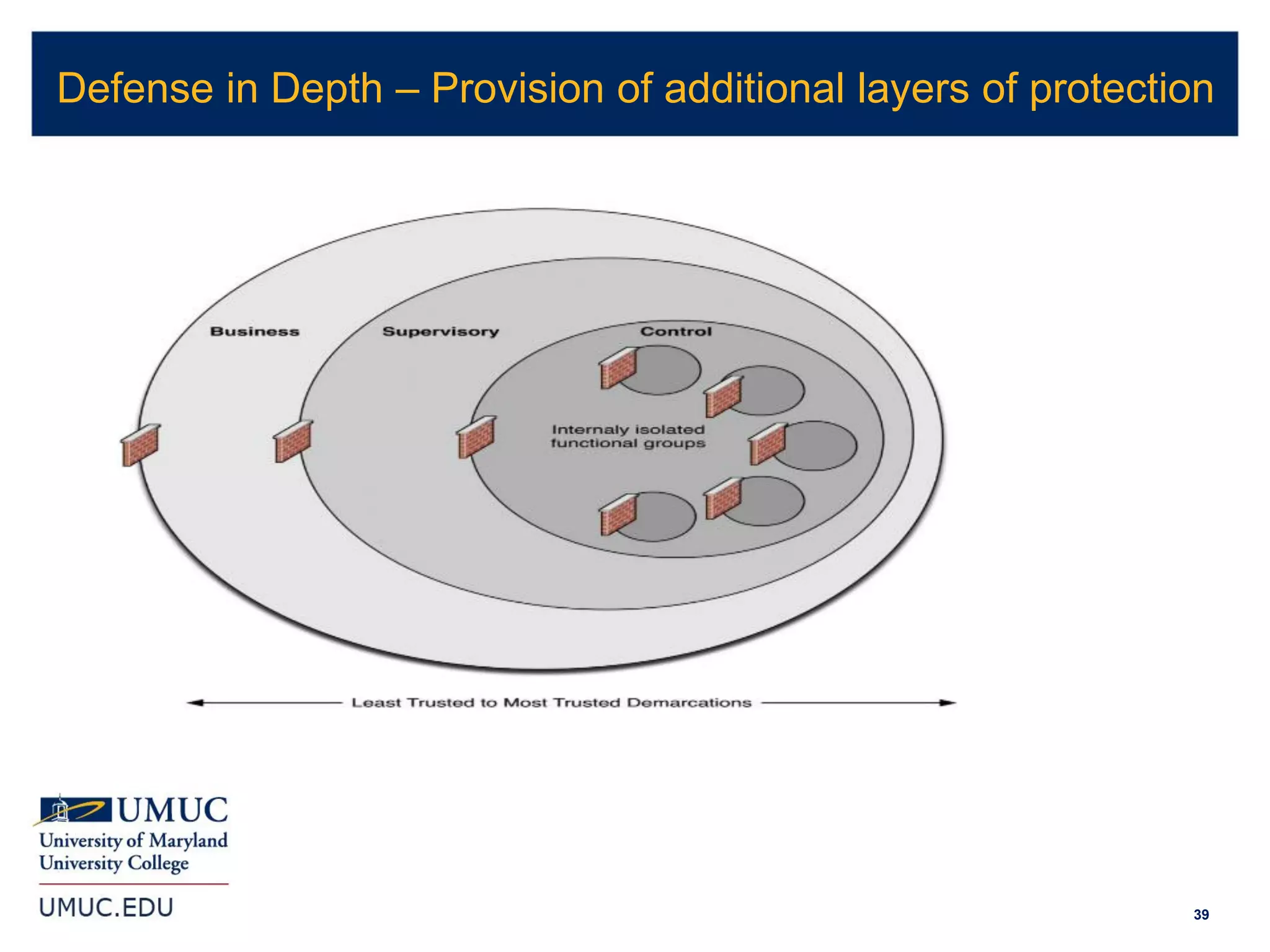
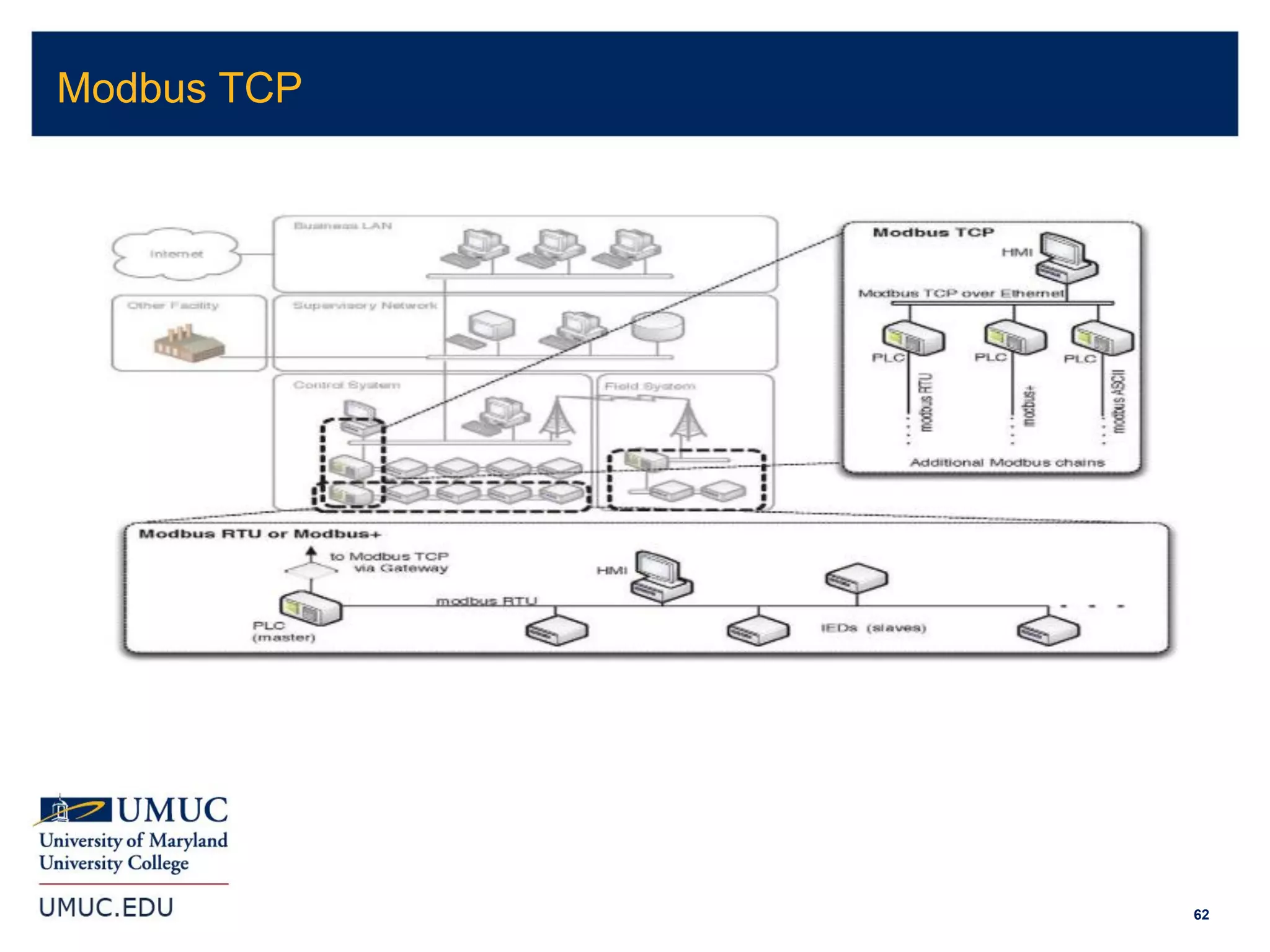
1. The document discusses implications of cybersecurity for small and medium manufacturers, including risk management and compliance requirements.
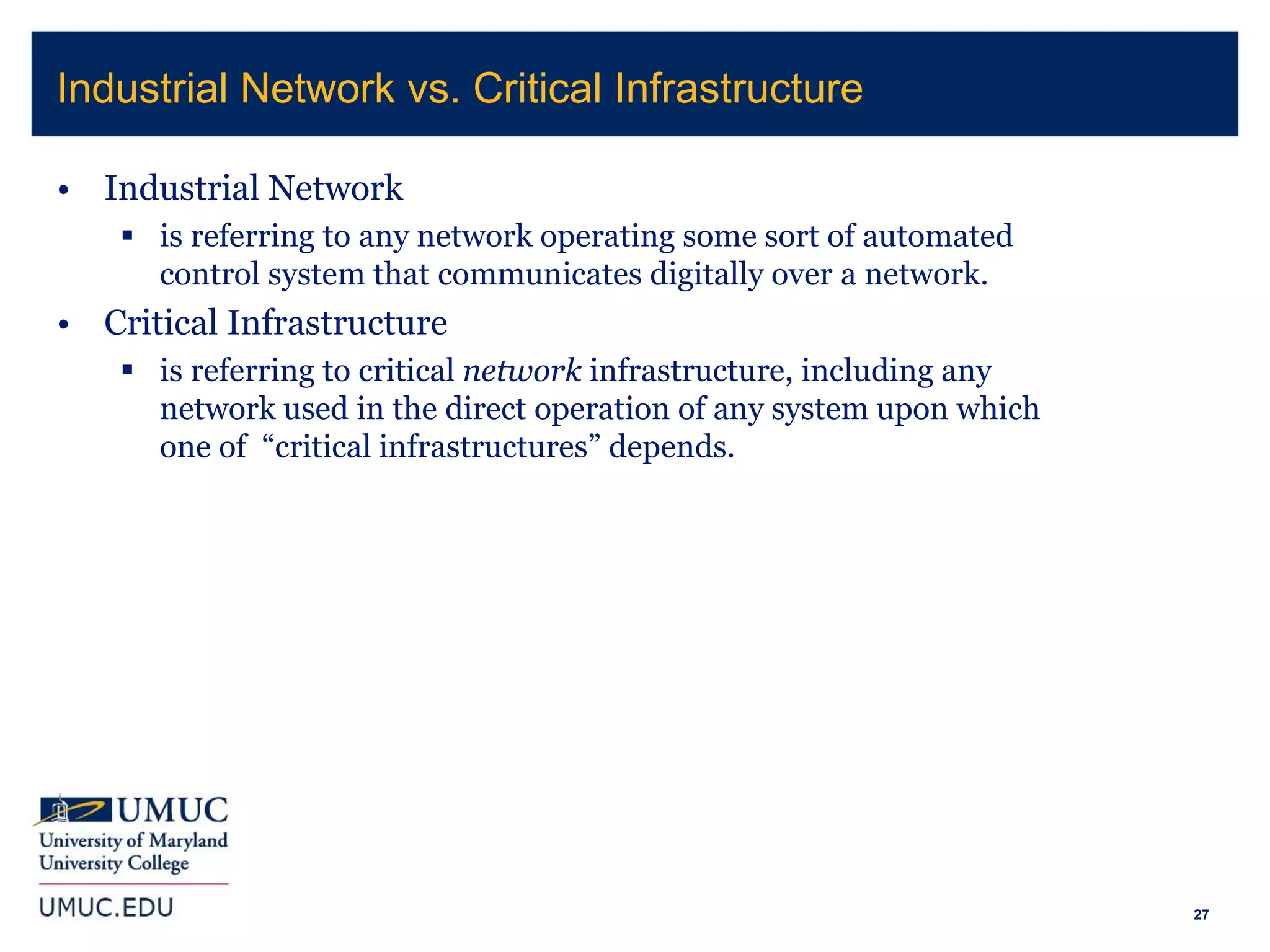
2. It covers topics like being compliant with certifications but still being breached, cybersecurity for industrial control systems, and Department of Defense Federal Acquisition Regulation Supplement (DFARS) requirements.
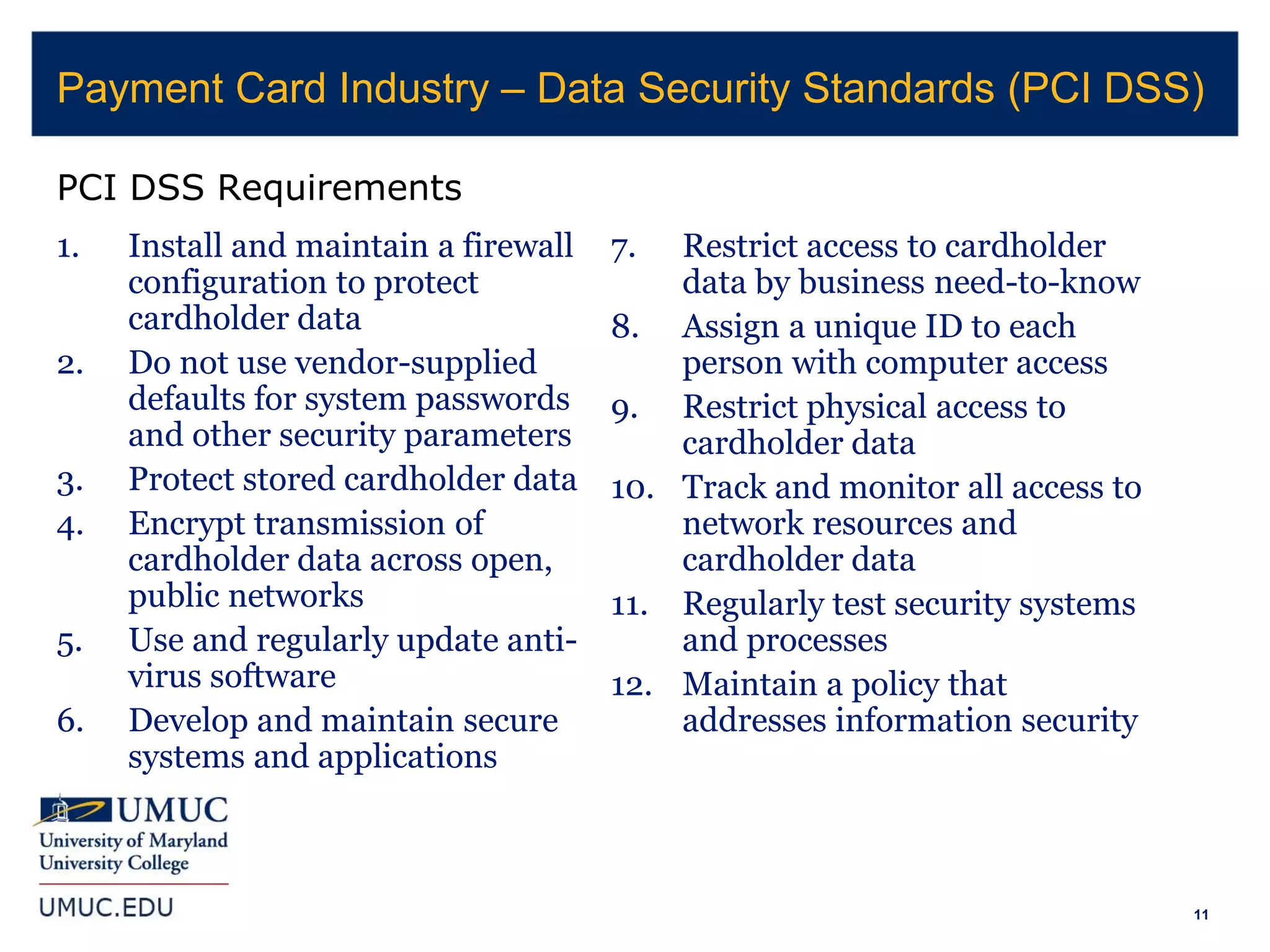
3. The document provides an overview of various laws and standards around data security, including the Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), Gramm-Leach-Bliley Act (GLBA), Sarbanes-Oxley Act (SOX), and Family Educational Rights and Privacy Act (FERPA).



























![34
• NIST Special Publications (800 Series)
NIST’s 800 series documents provide best practices and
information of general interest to information security.
All 800 series documents concern information security
It should be used as references where applicable.
Particular relevance to industrial network security is
SP 800-53 (“Recommended Security Controls for Federal Information
Systems”)
SP 800-82 (“Guide to Supervisory Control and Data Acquisition
[SCADA] and Industrial Control Systems Security”)
Standards and Organizations - continued](https://image.slidesharecdn.com/cybersecurityformanufacturersumuc-cadf-ronmcfarland-180912170838/75/Cyber-security-for-manufacturers-umuc-cadf-ron-mcfarland-34-2048.jpg)