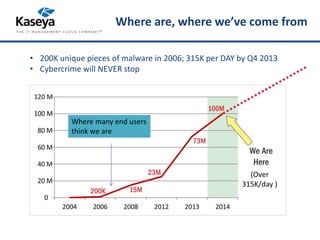
The webinar discusses the rising threat of cybercrime, particularly focusing on data breaches and ransomware, including a detailed overview of the current landscape and the primary causes of breaches. It highlights the importance of breaches reporting, legislation, and best practices for prevention, such as encryption and employee education. The discussion also provides insights into significant data breaches in healthcare and education in 2014, emphasizing the need for organizations to adopt robust security measures.