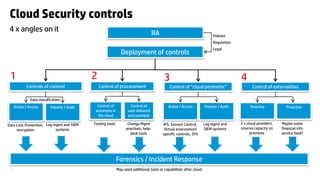
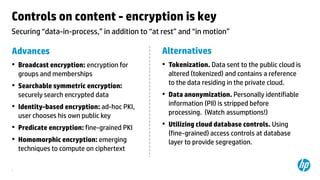
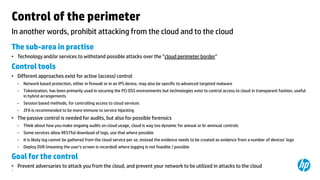
The document outlines necessary cloud security controls and the steps for successful cloud adoption, emphasizing the importance of risk assessments and defining specific controls for data handling, procurement, and perimeter management. It suggests implementing both active and passive controls to prevent data leakage and unauthorized use of cloud services, as well as ensuring compliance with legal standards. The author also discusses the need for continuous auditing and adapting controls to manage externalities like 'noisy neighbors' in a multitenant environment.