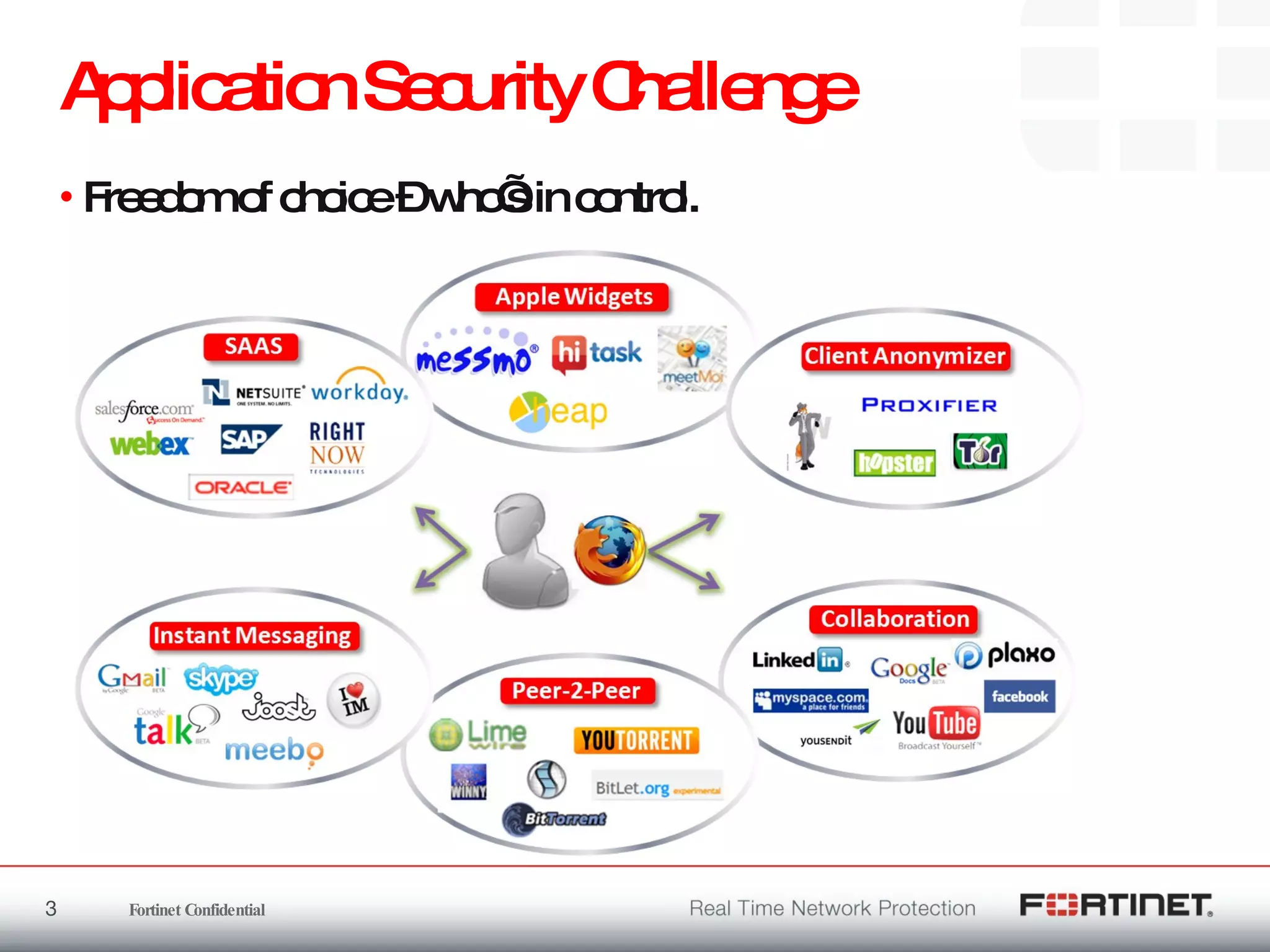
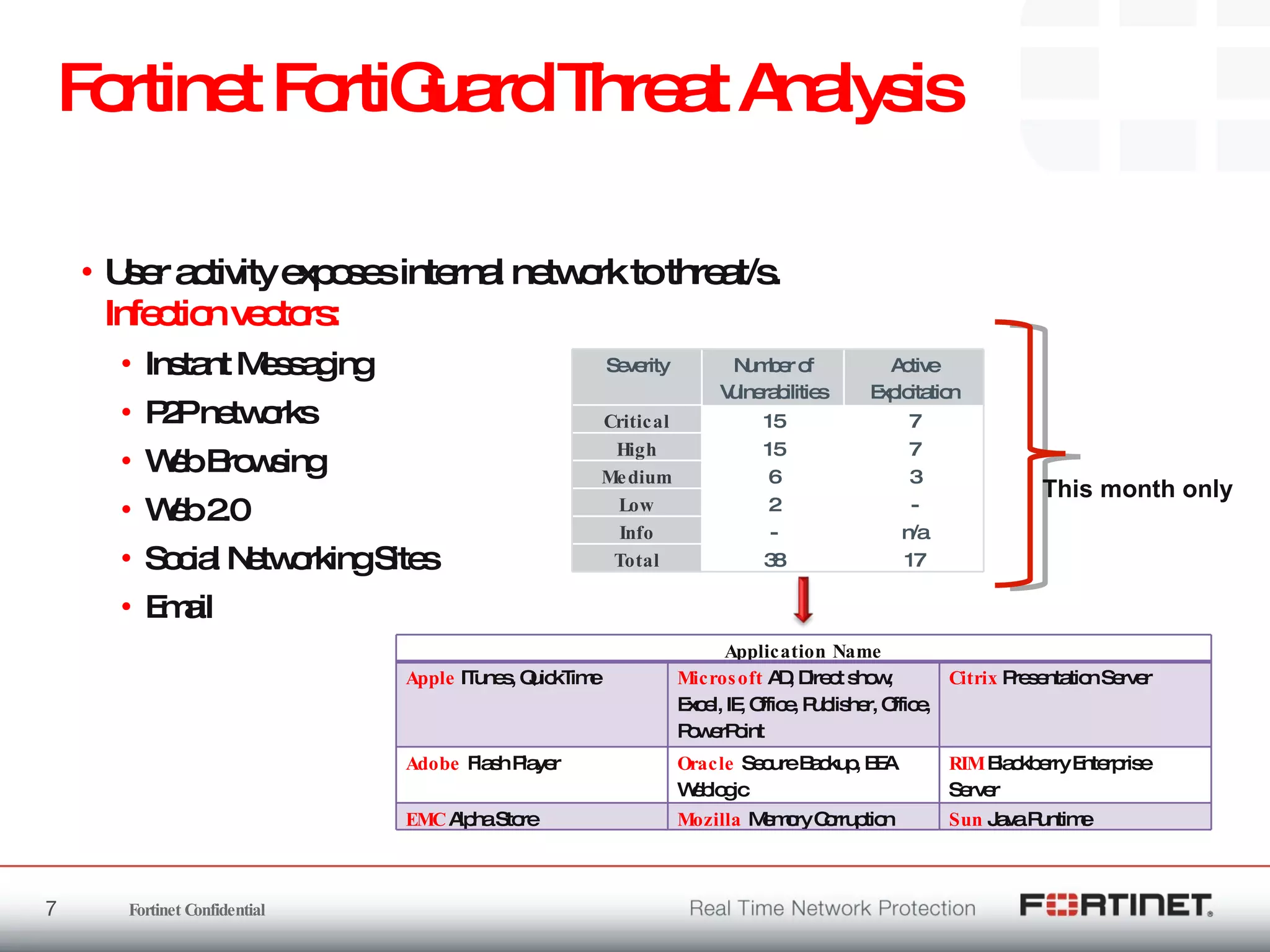
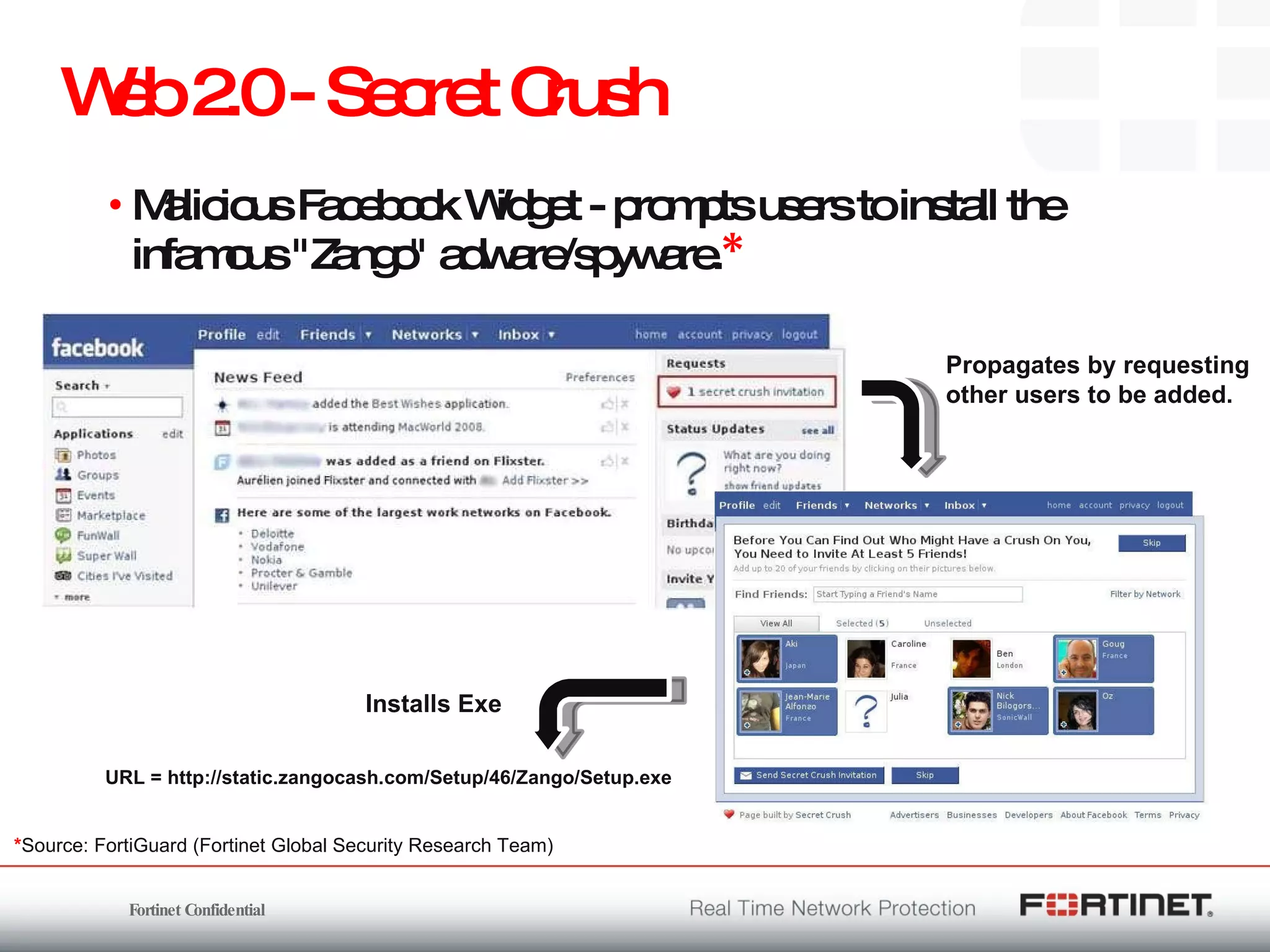
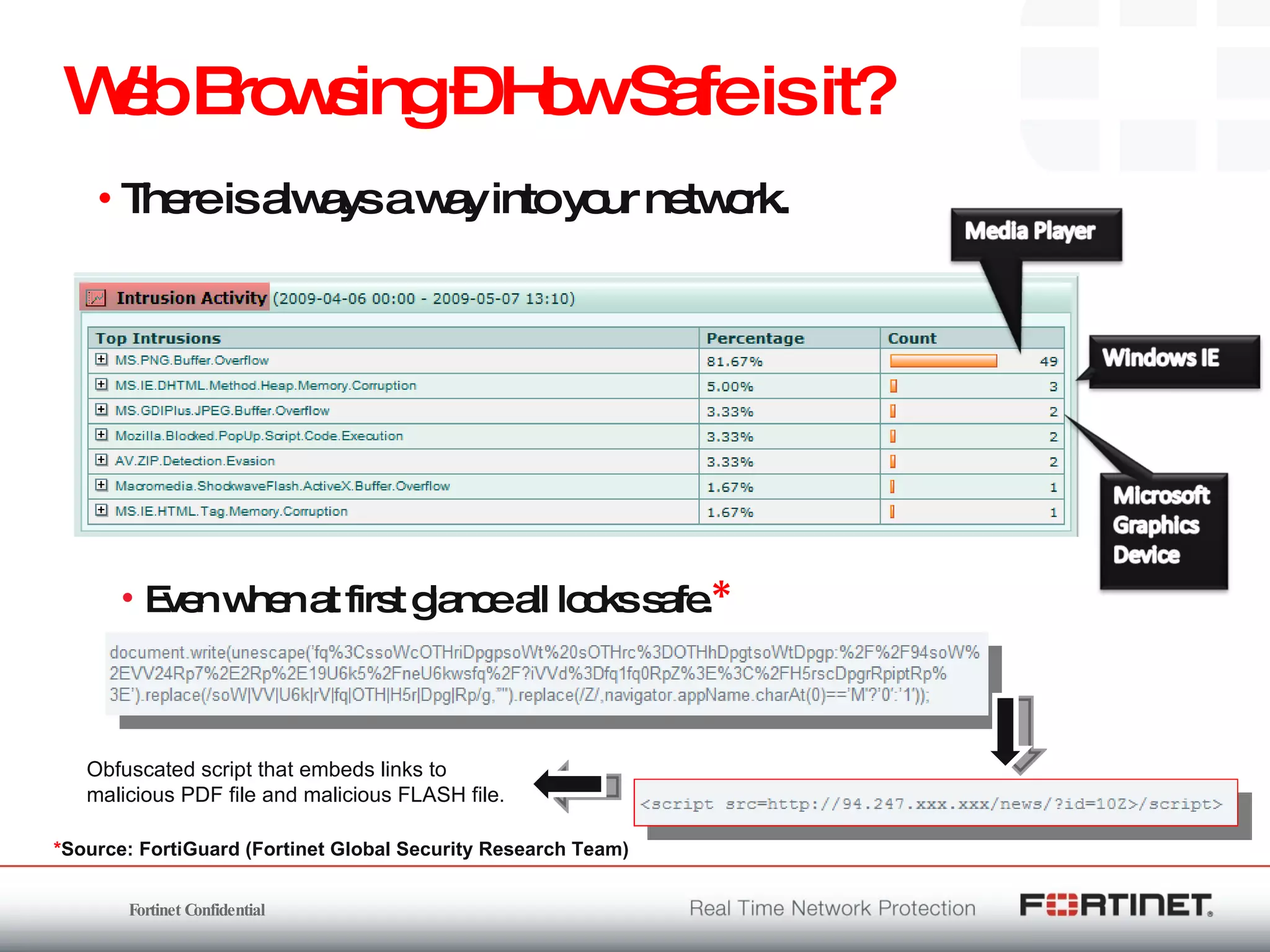
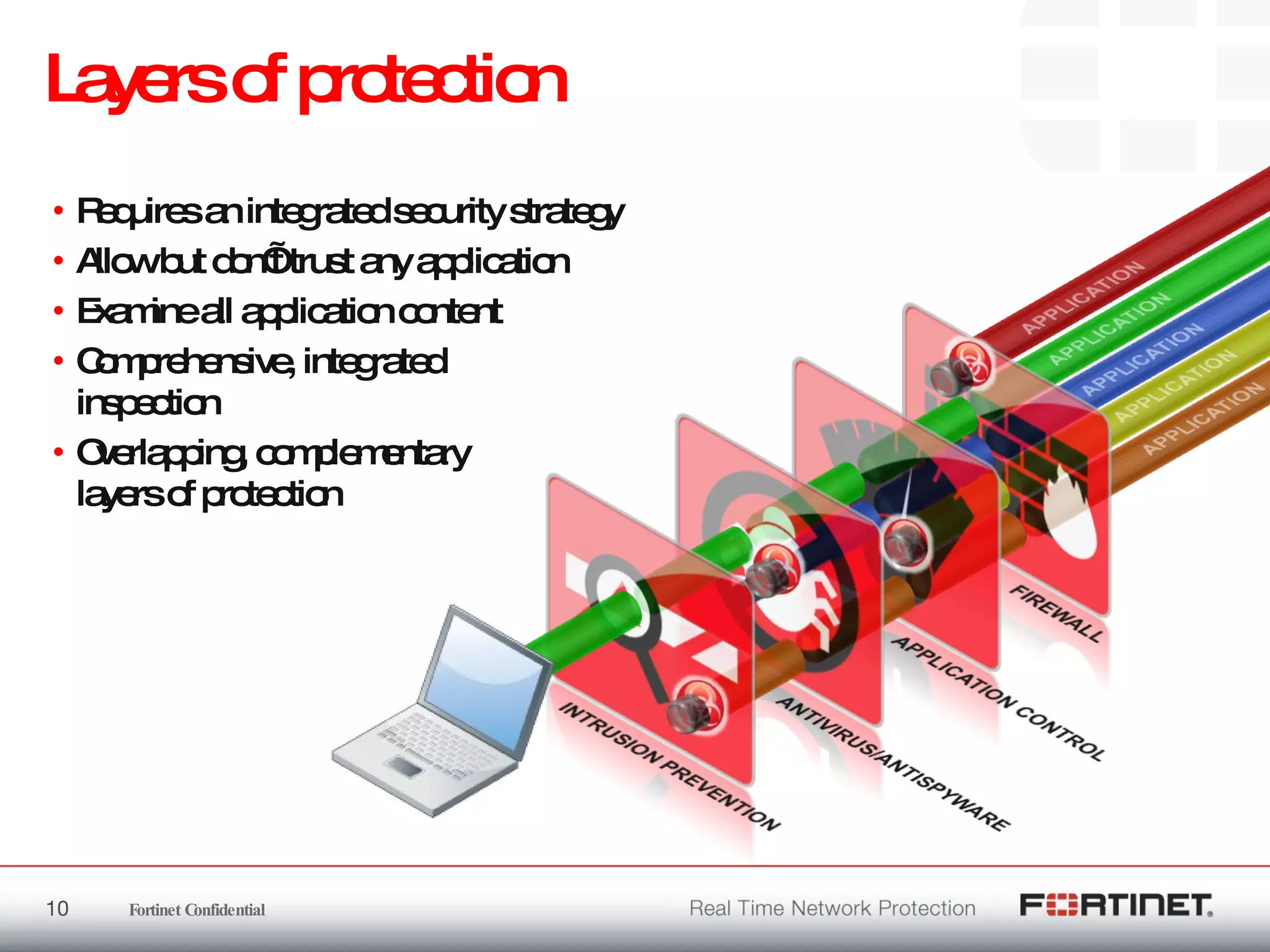
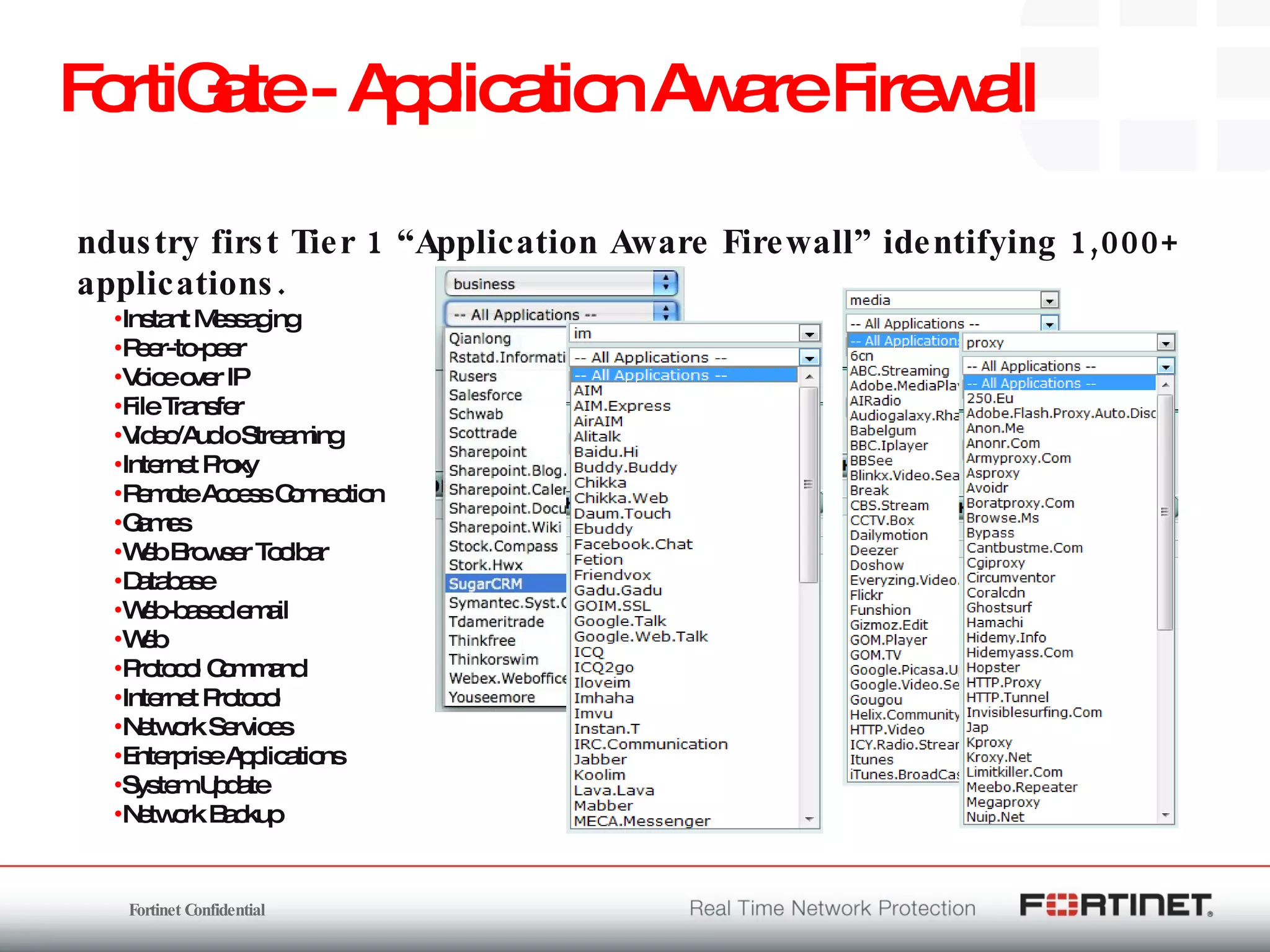
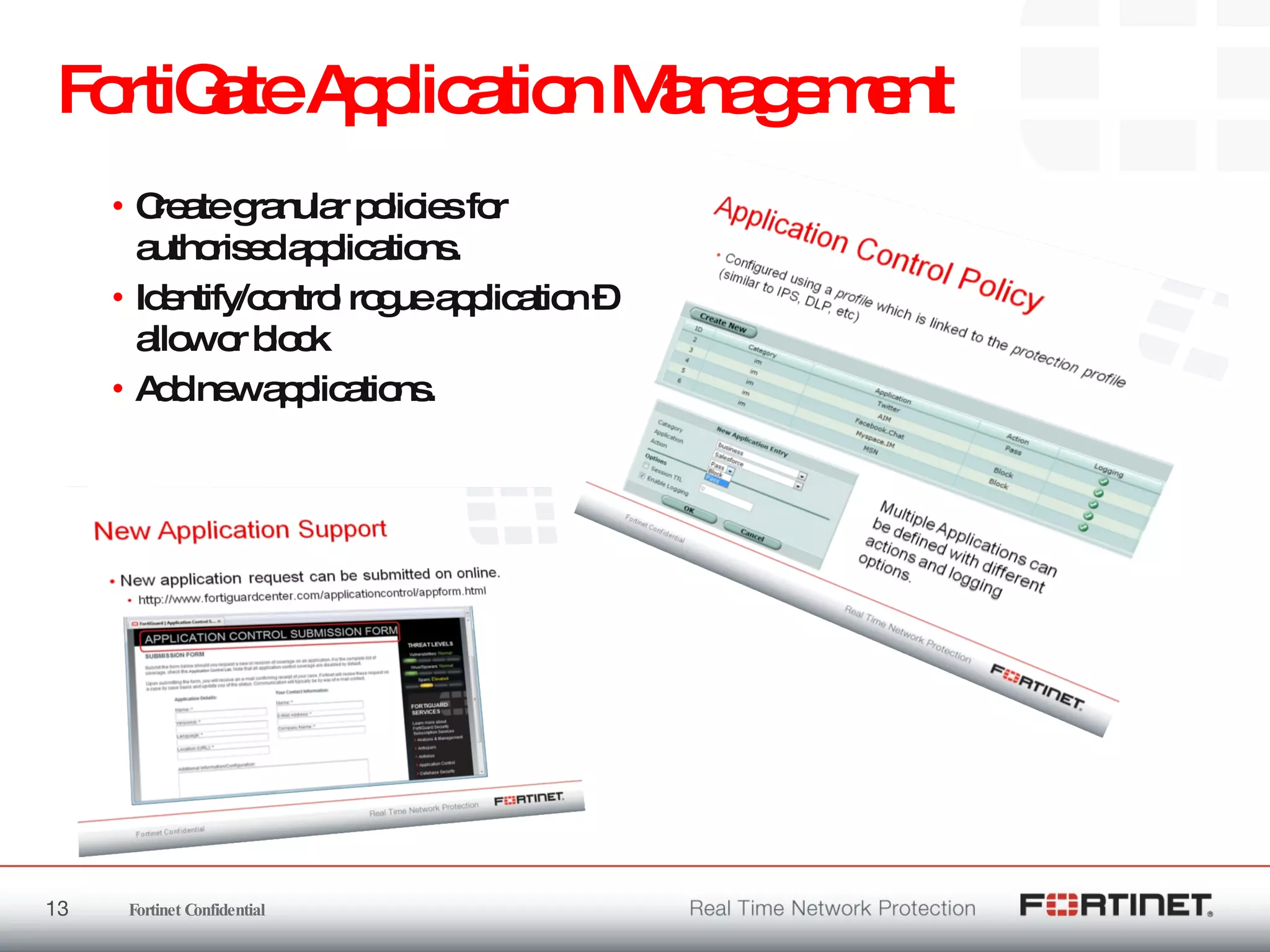
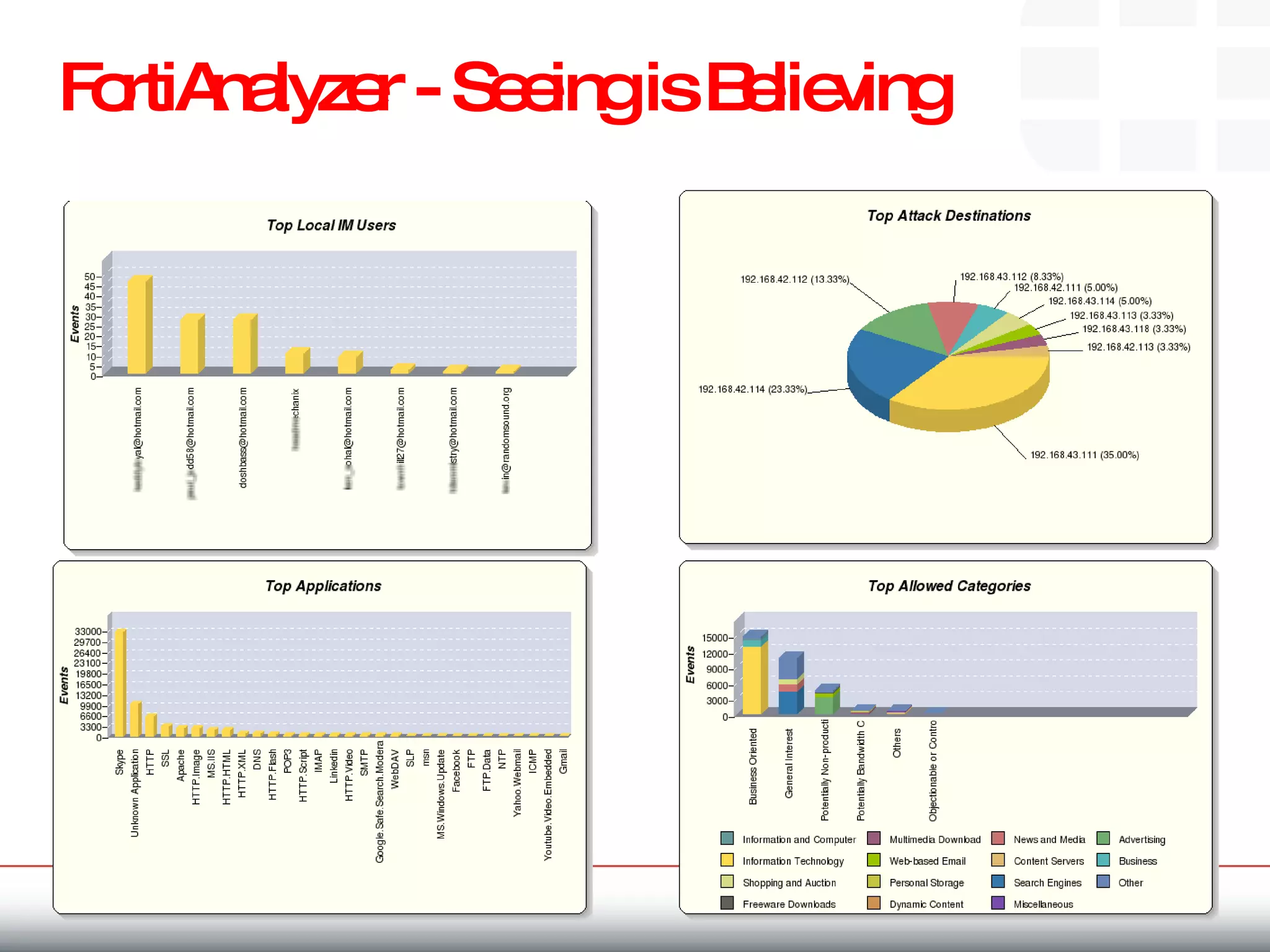
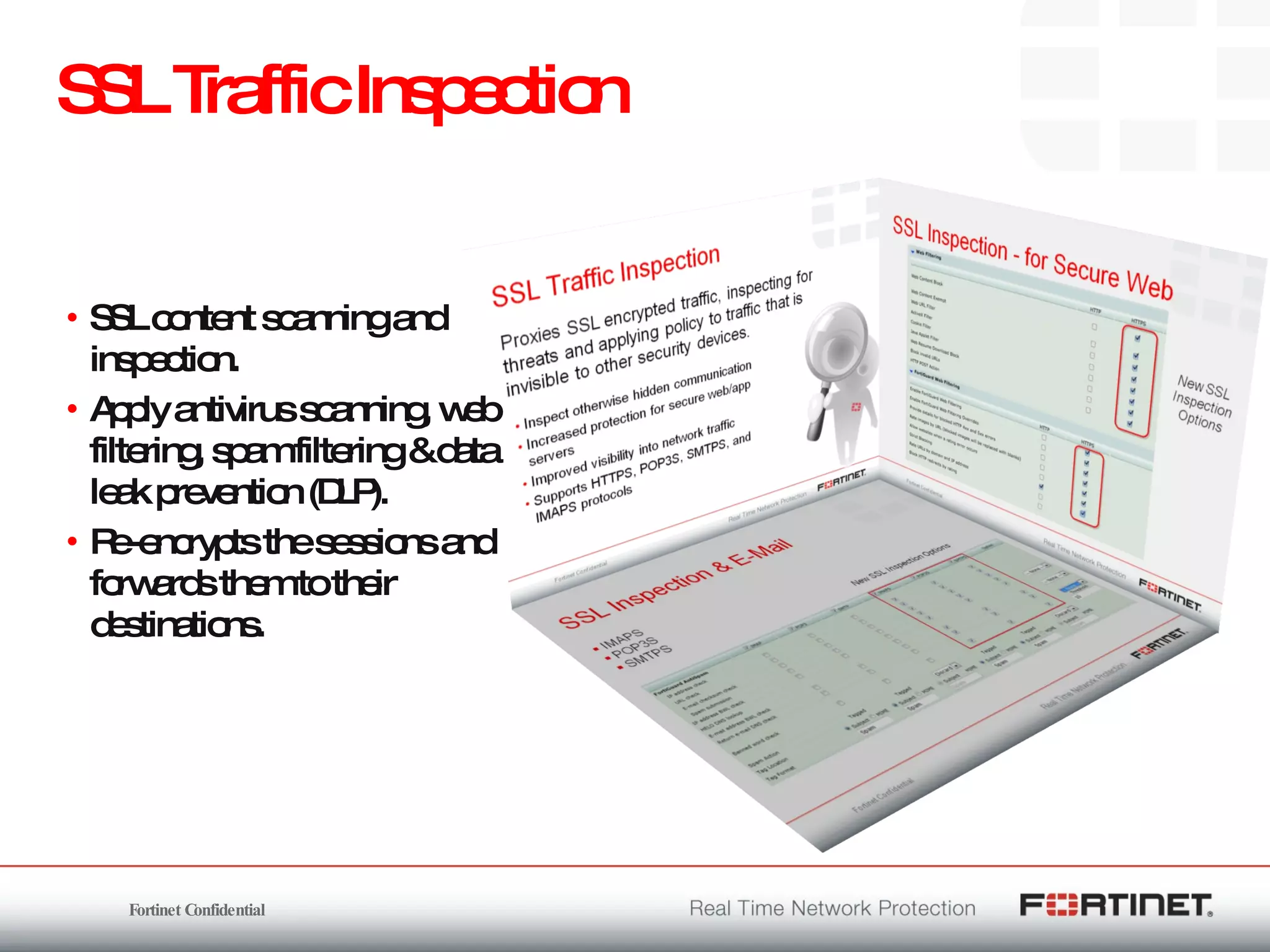
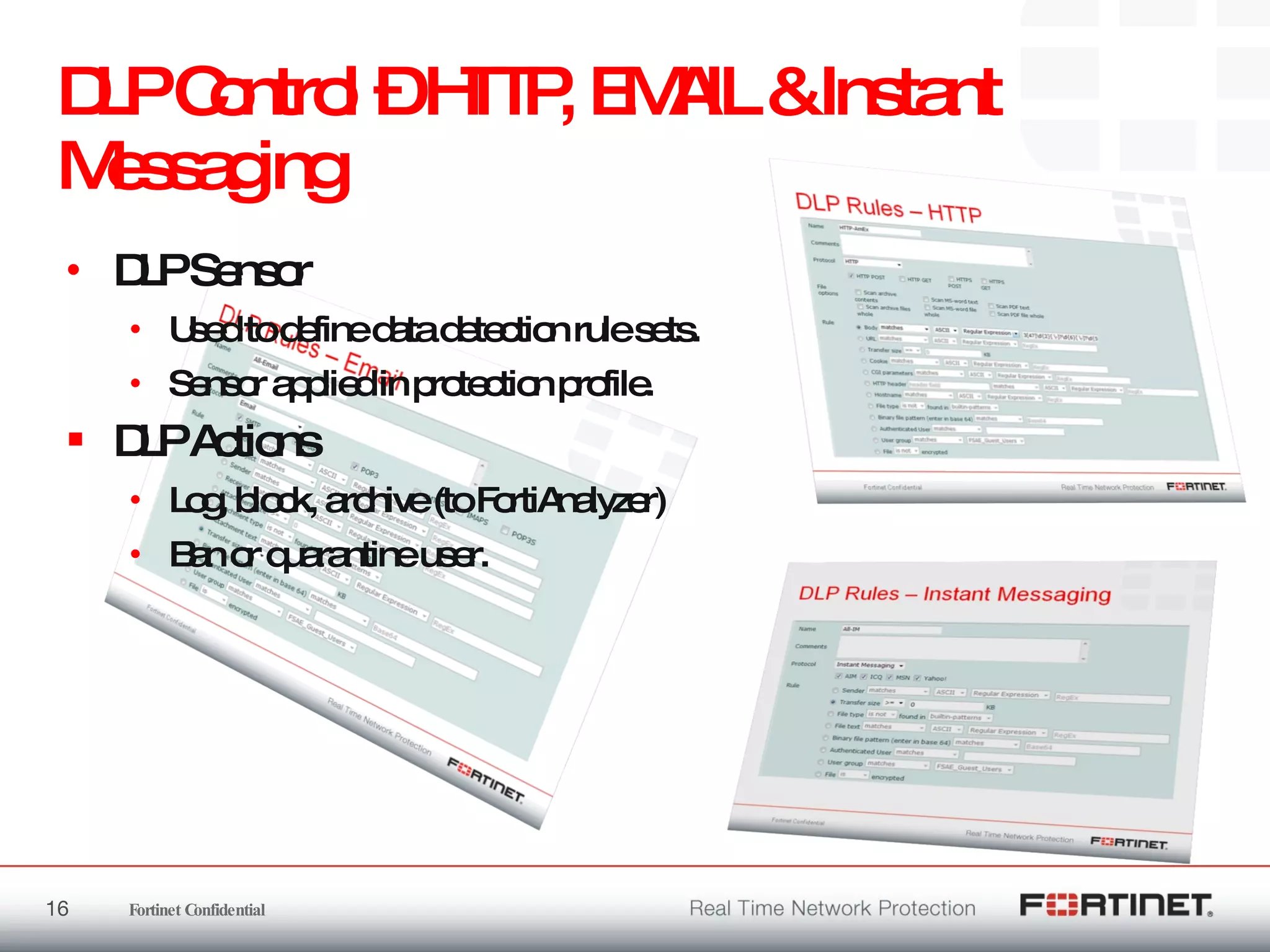
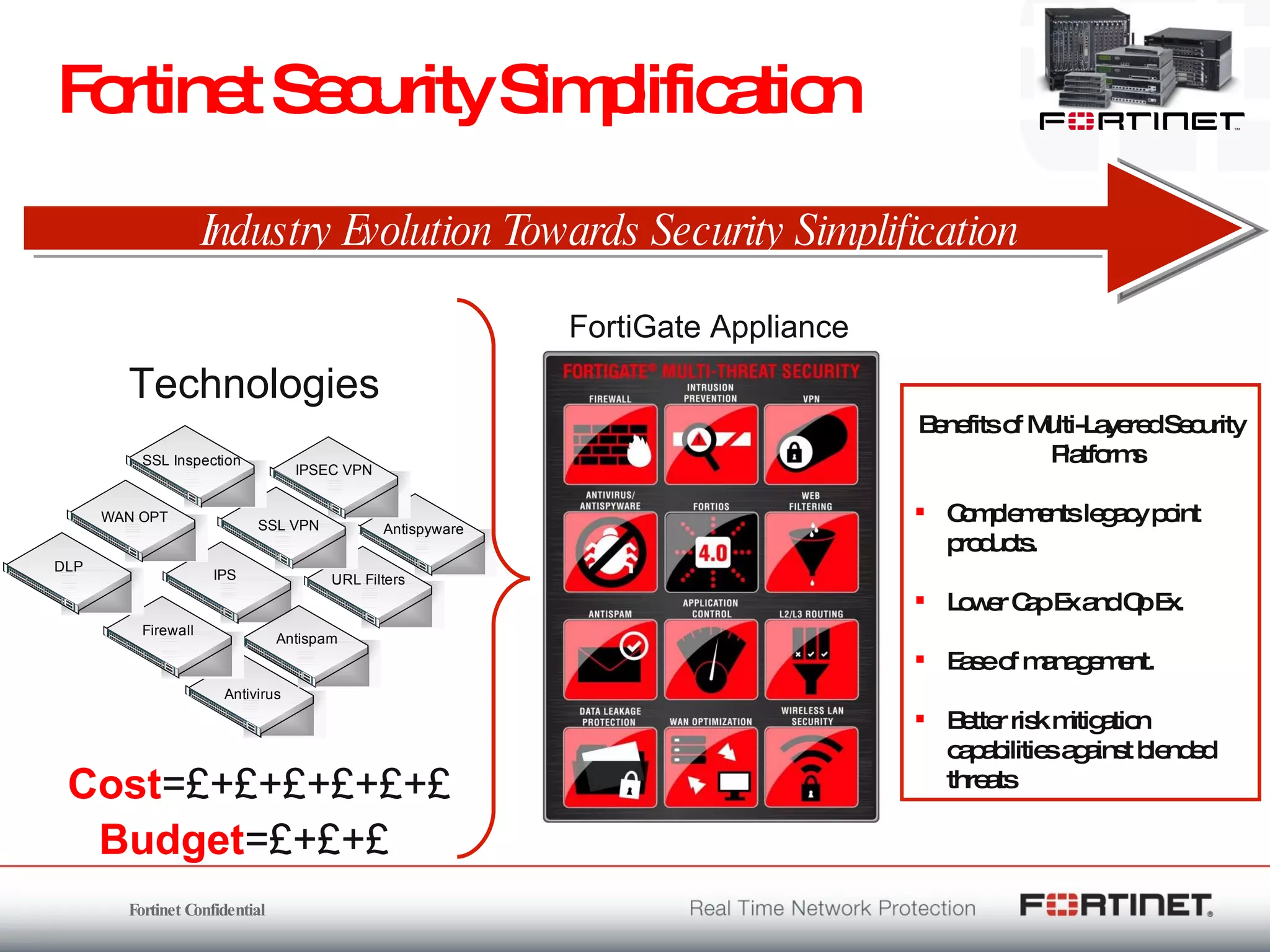
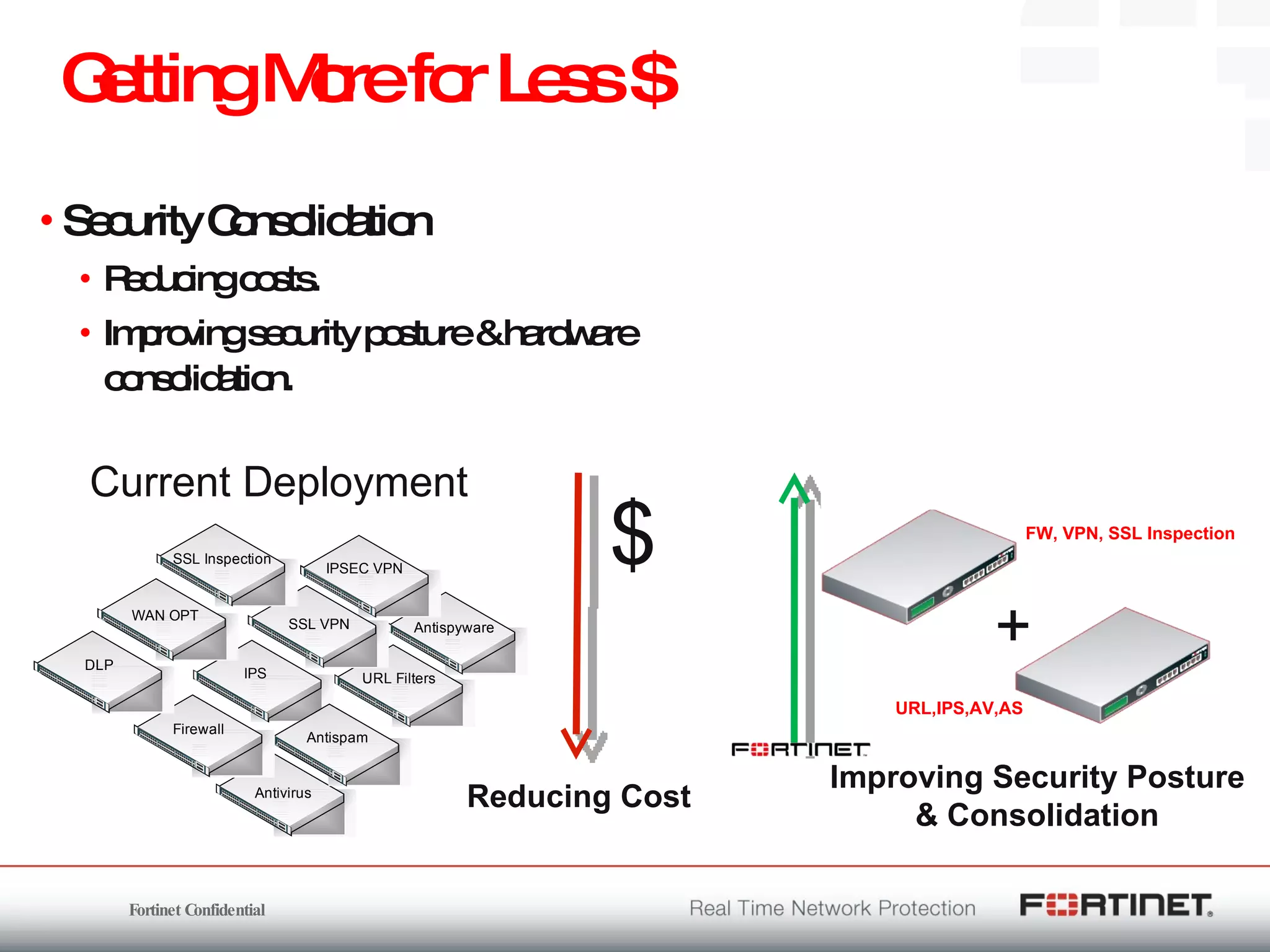
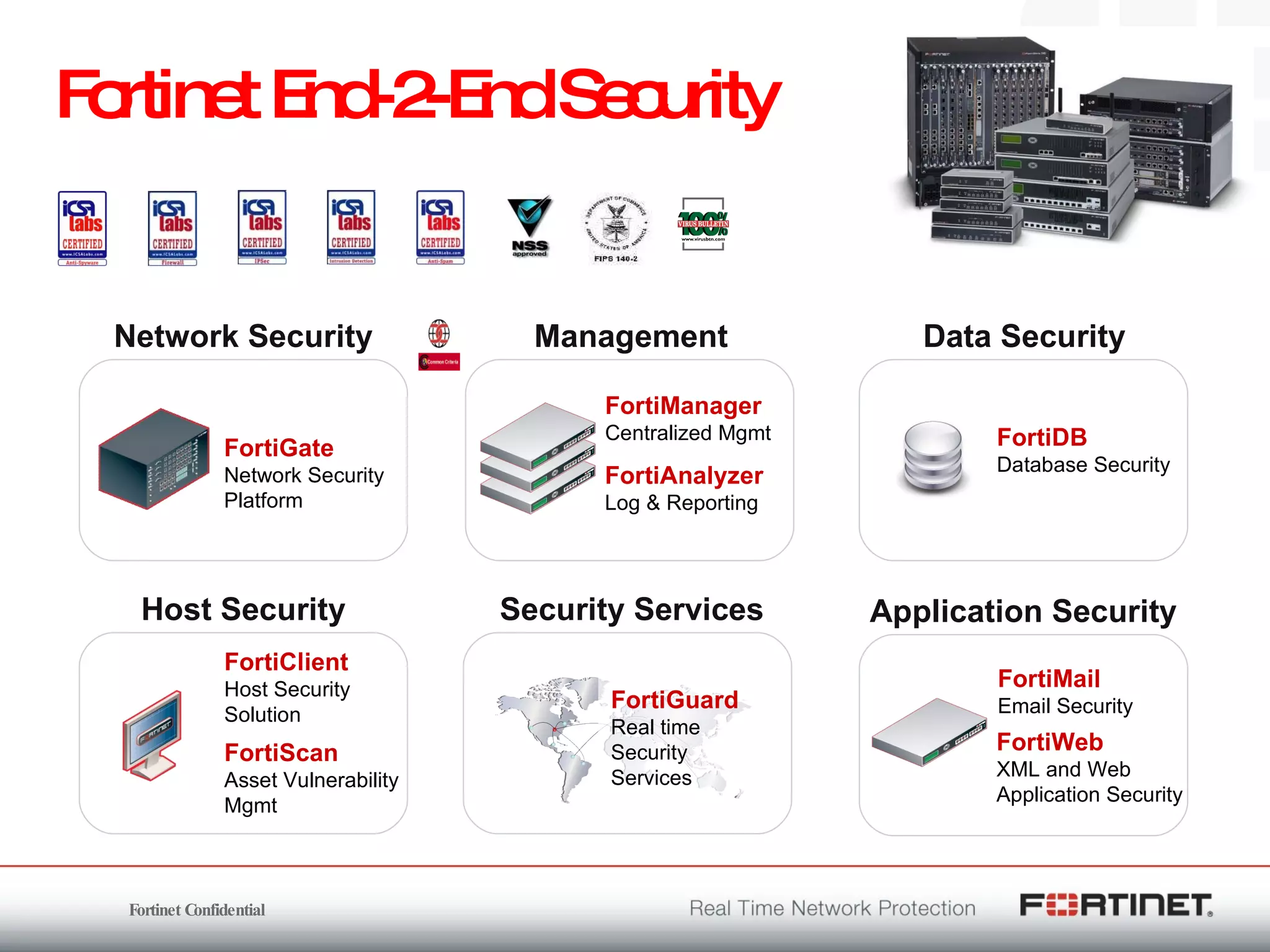
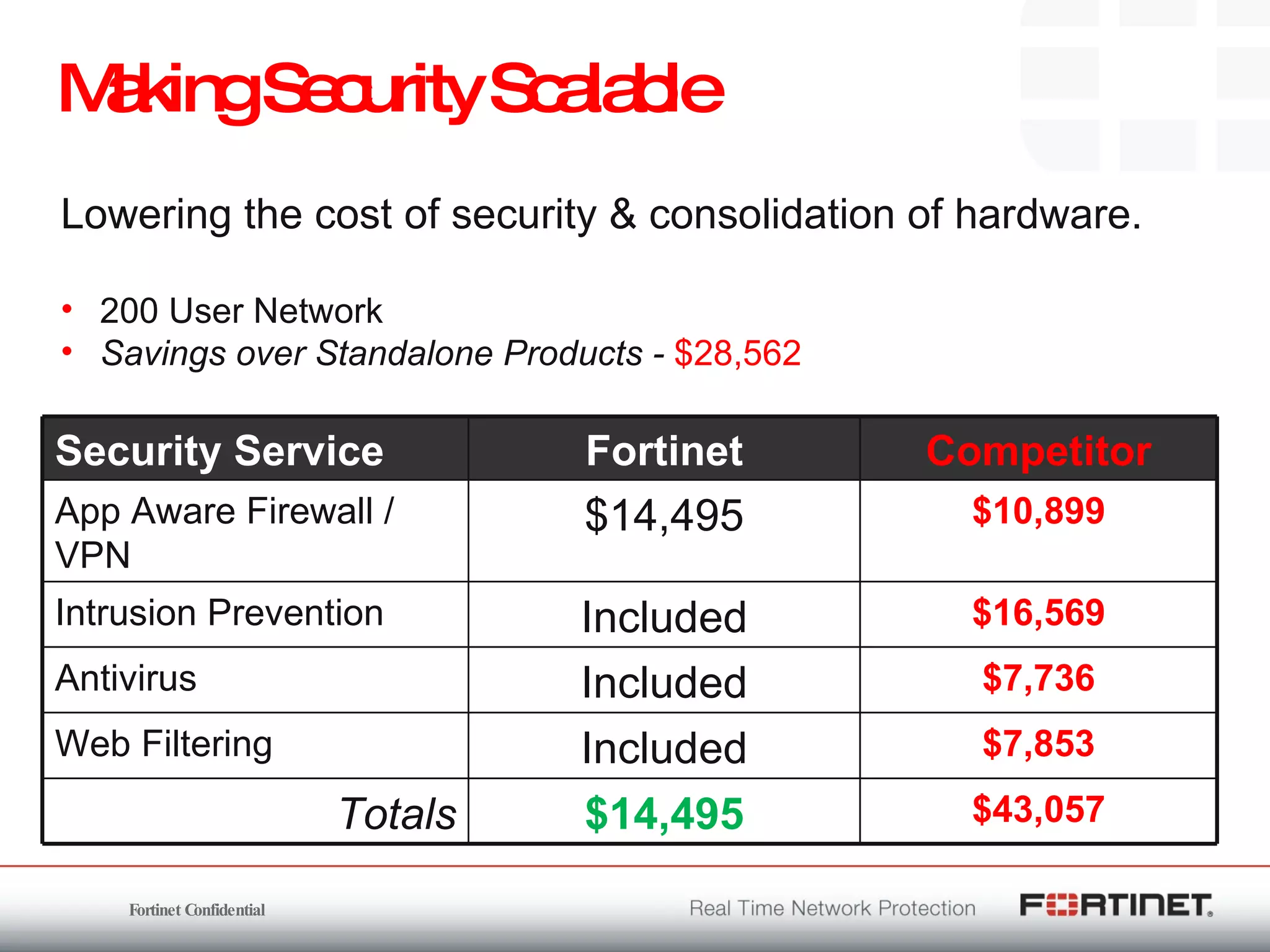
The document outlines the challenges and threats related to application security in the context of Web 2.0 and the growing sophistication of cyber threats. It emphasizes the need for an integrated security strategy, leveraging Fortinet's solutions, such as application-aware firewalls and threat analysis tools to enhance security posture and reduce complexity. The document also highlights the financial aspect of security management, advocating for cost-effective solutions that consolidate security measures while improving overall protection against threats.
![Kanwal Sohal – SE Manager UK&I [email_address] Richard Holmes – Technical Director [email_address] WEB 2.0 & APPLICATION SECURITY CHALLENGE](https://image.slidesharecdn.com/partnerwebexseminarv10september-100119093621-phpapp02/75/Partner-Zymbian-Fortinet-webinar-on-Web2-0-security-1-2048.jpg)