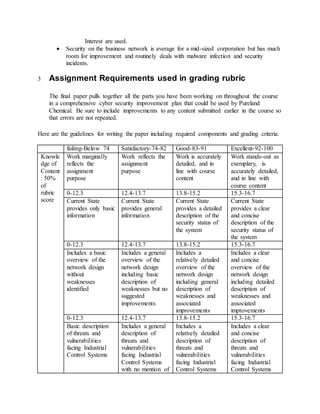
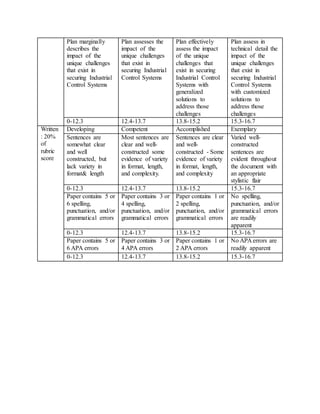
The document outlines a cybersecurity improvement plan for industrial control systems (ICS) based on a risk assessment, focusing on communication, network design, threats, and compliance with regulations. It includes specific learning objectives, assumptions for plan development, and a grading rubric emphasizing the quality of content, critical thinking, and writing. The plan aims to enhance ICS security while minimizing operational impact, addressing unique security challenges faced in industrial environments.