The document outlines project checklists for a cybersecurity course, detailing the required deliverables for multiple projects, including security assessments, incident reports, and strategic plans. Each project specifies components such as executive summaries, lab reports, and executive briefing slides, emphasizing the need for in-depth analysis and documentation related to cybersecurity measures and protocols. The checklists aim to guide students in completing their assignments while also providing an optional framework for professors to evaluate submissions.










![and data governance aspects of deploying new
technology.Address possible process changes.Address possible
personnel changes, hiring, training, retraining or users and
administrators.Finalize the ReportCompile, review, edit, and
proofreadAs you write the conclusions and summary statements,
address the following possible challenges:- Any key impacts to
the organization or network infrastructure- What will the
organization need to do in the future to meet goals and
objectives.- How will your organization ensure continuous
improvement?- What possible roadblocks could your
organization face?- How would you oversome these potential
roadblocks?*******Cybersecurity Technology Strategic Plan
Feedback*******2. Presentation (Complete Set of Team Slides
and Narration of a Portion)Title SlideUse of Readable Fonts and
ColorSummarizes Findings and Recommendations at High
LevelSlide Narration or In Class or Online Presentation (5-6
minutes or a portion of report)******Presentation
Feedback*******3. Lab Experience Report [Can Be Produced
by Designated Member(s) of Team]Summarizes the Lab
Experience and FindingsResponds to the QuestionsProvides
Screenshots of Key Results*******Lab Experience Report
Feedback******
functions/Functions Tasksheet.pdf
Sensitivity: Internal
Mathematical Software
Functio n s Tasksheet
https://uk.mathworks.com/help/matlab/matlab_prog/create-
functions-in-files.html](https://image.slidesharecdn.com/project1cst630projectcheckliststudentnamedatenotethische-220930045714-bc68e8b6/85/Project-1CST630-Project-ChecklistStudent-Name-DateNote-This-che-11-320.jpg)



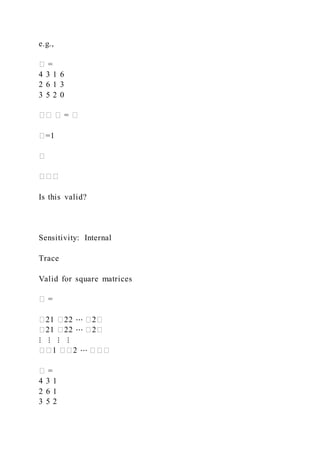

![It is adding up the main diagonal
Sensitivity: Internal
Trace
A = [1 2 3; 3 4 1; 4 3 4];
trace(A)
my_trace(A)
function t = my_trace(A)
t = 0
[m,n] = size(A)
for i=1:m
t = t + A(i,i)
end
end
Sensitivity: Internal
� × � Matrix
� =](https://image.slidesharecdn.com/project1cst630projectcheckliststudentnamedatenotethische-220930045714-bc68e8b6/85/Project-1CST630-Project-ChecklistStudent-Name-DateNote-This-che-17-320.jpg)

![⋮ ⋮ ⋮ ⋮
��1 ��2 ⋯ ���
�
�=1
�
�
�=1
�
��� = �
�=1
�
��1 + ��2 + ��3 …+ ���
First summing the rows, then summing these values.
It is adding all the elements of the matrix!
Sensitivity: Internal
Sum
A = [1 2 3; 3 4 1; 4 3 4];](https://image.slidesharecdn.com/project1cst630projectcheckliststudentnamedatenotethische-220930045714-bc68e8b6/85/Project-1CST630-Project-ChecklistStudent-Name-DateNote-This-che-19-320.jpg)
![sum(sum(A))
my_sum(A)
function s = my_sum(A)
s = 0
[m,n] = size(A)
for i=1:m
for j=1:n
s = s + A(i,j)
end
end
end
finite/1st Order ODES - annotated.pdf
Sensitivity: Internal
1st Order Ordinary
Differential Equations (ODES)
Sensitivity: Internal](https://image.slidesharecdn.com/project1cst630projectcheckliststudentnamedatenotethische-220930045714-bc68e8b6/85/Project-1CST630-Project-ChecklistStudent-Name-DateNote-This-che-20-320.jpg)

