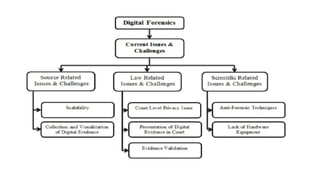
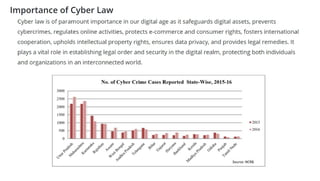
The document provides an overview of cybercrime, including its definition, origin, and the evolution of threats such as ransomware and advanced persistent threats, emphasizing the increasing sophistication of cyber attacks. It covers key topics from cyber security courses, including social engineering, mobile device security, computer forensics, and the importance of security policies and cyber laws. Additionally, it mentions a rise in security breaches and outlines the significance of understanding various cybercrime methods and prevention measures.